If you develop and publish themes, it’s important to keep a few things in mind that must ensure the security of your customers. However, most of the time, theme authors rush to deploy their themes and its elements without integrating adequate security checks & protections into their code – inviting their customers to become prey to the wide range of cyberattacks.
As the world currently brawls with the disruption brought about by the COVID-19 pandemic, businesses are pivoting and modernizing their digital footprints for their customers.
A recent example of a critical vulnerability in Divi WordPress theme that affected more than 700,000 of its users showcased how an improperly developed theme can invite hackers to exploit a simple vulnerability and take over the entire site access.
Building a Security Mindset
Just like you add functionality to your themes, it is also important to implement security measures that will make the theme more secure for your users. You can follow these principles as you begin your theme development efforts:
- Always keep your theme up to date: As technology evolves, so does the potential security risks to your themes. Pushing periodic updates and managing your code could reduce these risks and make your theme more trustworthy for your customers.
- Don’t trust any data inputs: Data can come in many forms as user input. Always make sure to verify such inputs and sanitize the data before entering it in your theme’s database.
- Use only the trusted APIs: Many APIs could pose a potential security threat to your customers. It is always recommended that you should only use trusted APIs that offer a secure transaction.
Taking this into consideration, you can now set up the right development environment for your theme that offers feasibility and provides you options to integrate security at the same time.
Top security risks to website themes
Theme vulnerabilities have aggravated since last year. We are seeing more and more websites/web applications being targeted by theme vulnerabilities and it continues to worsen. Here are some CMS-wise hacking statistics (2019) to consolidate this statement:
- WordPress Hacking Statistics: According to CVE Details, XSS (38.1%) remains the biggest threat in WordPress, followed by code execution (15.3%), and bypassing something, gain info (12.7%) tying for the third spot.
- Magento Hacking Statistics: According to the CVE details of Magento. Again XSS (53.1%) came out to be the elephant in the room followed by code execution (12.5%) & Gain information (12.5%).
- OpenCart Hacking Statistics: The biggest threat that OpenCart faces is Remote code execution with a 45.5% share of all attacks. Other than that directory traversal and SQL injection equally threatens OpenCart with a share of 20% each.
- Prestashop Hacking Statistics: Most attacks on PrestaShop happen via Cross-Site Scripting (40.1%).
- Joomla Hacking Statistics: Known Joomla CVEs show that XSS is the most common vulnerability exploited by attackers.
You can also see this list for the variety of vulnerabilities found in WordPress themes.
The Open Web Application Security Project (OWASP) Foundation has a comprehensive list of risks in web applications and APIs, you should check it out. Here are a few of them:
- Weak backend access controls
- Data leaks and exposure
- Using components with known vulnerabilities
- Security misconfiguration
- Broken authentication and authorization
- Insufficient logging and monitoring
- Unsecure deserialization
- Cross-site scripting (XSS)
It is important that as a theme developer you are aware of the mentioned security risks, specifically the ones that usually result from an unsecured code.
Do-it-yourself list to perform a theme security audit
The serious risks posed by unsecured themes highlight the necessity for an in-depth theme security audit that includes, the process of finding, fixing, and enhancing the security of themes within the design, development, and post-deployment phase.
Here is a DIY list to perform a security audit for your theme:
1. Performing a data validation & sanitization test
Data validation is the process of analyzing the input data against a predefined pattern (or patterns) and sanitization is used for cleaning or filtering that input data.
Data validation and sanitization usually applies to external data such as incoming user input and calls to web services via API.
It is important to verify and clean the data before performing any actions.
A data validation & sanitization test will ensure that it is implemented correctly and doesn’t open doors to the most common security vulnerability exploits that can easily allow any threat actor to bypass your theme security.
There are various tools available for data validation & sanitization testing such as QuerySurge, DbFit, iCEDQ, Datagaps ETL validator, etc.
2. Checking data escaping/secure output
“Escaping is the process of securing output by stripping out unwanted data, like malformed HTML or script tags, preventing this data from being seen as code”. (Source: WordPress)
It is important to properly escape whenever you’re outputting data. Checking if the data escaping is implemented correctly will help you secure your data prior to rendering it for the end-user and prevent XSS (Cross-site scripting) attacks.
It will also make sure the SQL queries are SQL-escaped before it is executed, it will prevent any SQL injection attacks.
3. Analyze and scan your ‘container’
If you are using container technology to run multiple development environments, then you should scan it to be able to secure your development processes.
Analyzing your container images and scanning it for known vulnerabilities, secrets keys, compliance checklists, and malware variants during your SDLC will provide complete visibility of security concerns for your container. This will help your development team for pushing your theme into the production environment securely.
To further reduce the risks to containers, dev teams can make less third-party software integrations or use only the trusted ones to ensure that software doesn’t penetrate your container environment.
4. Perform Static Application Security Testing (SAST)
Doing Static Application Security testing (also called security code review / white-box testing) can help you test and analyse your code from inside and search vulnerabilities and other security issues early in your software development cycle (SDLC).
Discovering security issues in your code at this stage can help you save money and remediate the code faster.
5. Use a Software Composition Analysis (SCA) tool
“A software composition analysis (SCA) tool can detect publicly disclosed vulnerabilities contained within a project’s dependencies”.
If you have imported/sourced any code from outside the organization and embedded it to run inside your current DevOps environment, it is possible that it is not checked during the static analysis phase.
You can use this OWASP dependency-check tool to check for any vulnerable or outdated libraries in your code.
6. Perform Dynamic Application Security Testing (DAST)
Also known as “black box security testing”, DAST can help you test the resilience of your theme VAPT application, containers, and clusters when subjected to hacking techniques that threat actors use to find out potential vulnerabilities in your application.
You can also use a DAST scanner/tool to scan your theme application.
DAST is performed when an application is running, where you or the scanner try to hack or find exposed vulnerabilities/weaknesses in your theme just like an attacker would.
7. Interactive Application Security Testing (IAST)
IAST (also known as gray-box testing) is a combination of SAST (white-box testing) & DAST (black-box testing) methodologies, allowing it to cover more code and perform tests that provide more accurate results and verify a wider set of security rules.
It basically fulfills the bases that SAST and DAST don’t cover such as hidden inputs, hidden files, and configuration information, etc.
IAST tools/scanners can scan the application in real-time, in the development process, QA, or even in production.
Finding it difficult to do-it-yourself? Get professional help from Astra Security’ engineers.
While the core developers have a dedicated team focused on securing the core platform, as a theme developer you should be aware that there is potentially much that is outside the core that can be vulnerable. It’s easy to miss out on vulnerabilities while auditing your theme manually. Hence, for better-optimized and thorough testing, you can get a professional to do it for you.
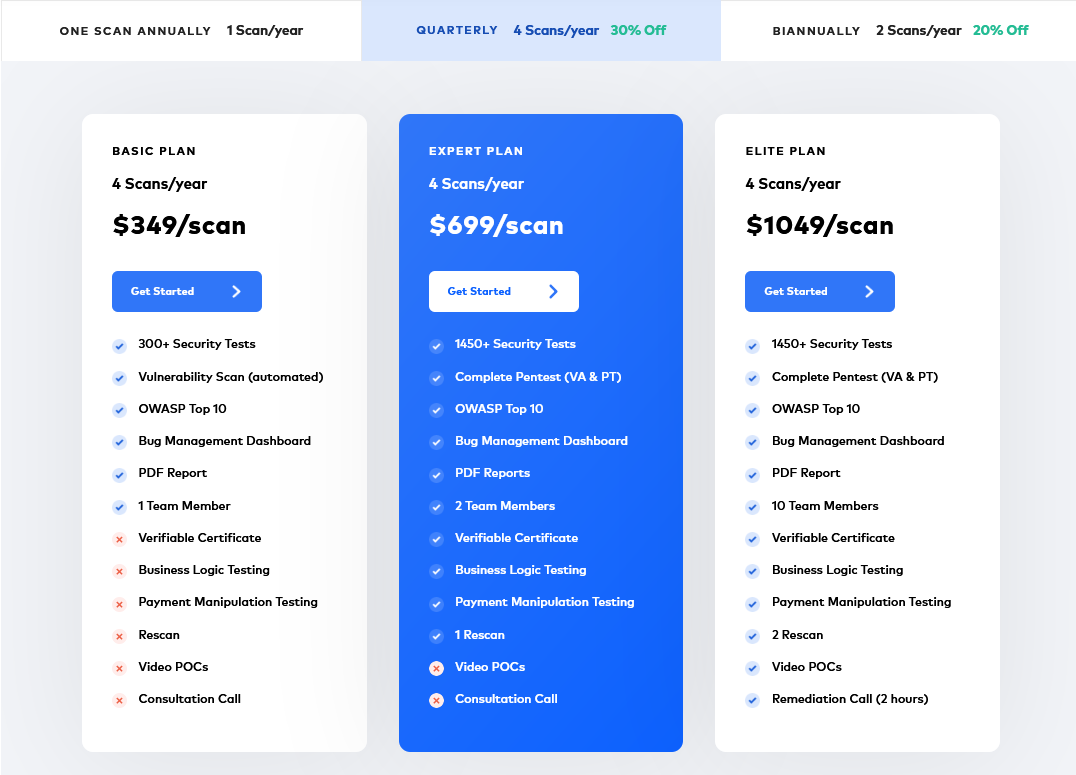
At Astra Security, we offer comprehensive VAPT plans to assess your application with advanced professional tools and an expert eye. Astra’s VAPT plans are available in three different packages — Basic, Elite, and Expert. The pricing details of which are as follows:
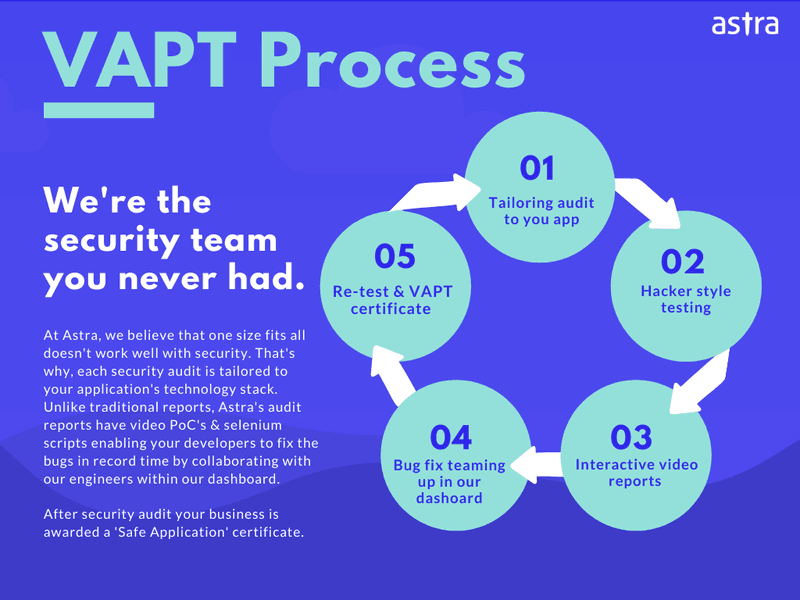
Astra’s VAPT process is straight-forward and can be summed up in these 5 steps:
Don’t wait for an attack to tell you that your theme has vulnerabilities. Test your application today and be secure.
















