With the increasing frequency and sophistication of cybercrimes, businesses are facing ever-mounting risks to their data and operations. In 2021 alone, there were over 4,100 publicly disclosed data breaches, exposing billions of records to potential compromise. To safeguard against such threats and instil trust in their services, organizations are turning to SOC audits.
In this article, we will cover the basics of SOC 2 auditors and audits, who need a SOC 2 certification and why. We will also look at 8 SOC 2 vendors that can help you achieve SOC 2 compliance.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Top 8 SOC 2 Auditors in 2024
What is a SOC 2 Audit?
A SOC 2 audit is a comprehensive examination and certification process developed by the American Institute of Certified Public Accountants (AICPA). It assesses the effectiveness and reliability of your company’s internal controls related to the 5 Trust Service Criteria namely, data security, confidentiality, privacy, processing integrity, and availability.
During the audit, AICPA approved SOC 2 auditors to evaluate your internal control measures to ensure they align with industry standards and best practices. Upon successful completion, your organization receives a SOC 2 report, which can be shared with clients and stakeholders to demonstrate their commitment to maintaining high standards of data protection and operational excellence.
Who needs SOC 2 compliance?
SOC 2 primarily applies to service organizations that handle sensitive customer data or provide critical services to other businesses. The following are different service organizations that need SOC 2 certification, including but not limited to:
- Software as a Service (SaaS) companies
- Business intelligence and analytics companies
- Financial consultancy and accounting services
- Customer management services
- Managed IT and security service providers
5 Reasons why you need SOC 2 compliance
- Building trust: Businesses are naturally keener to work with service providers that have SOC 2 compliance rather than those that don’t. Showing your SOC 2 compliance letter to a potential client gives you a significantly better shot at acquiring business.
- Competitive edge: You establish a discernible advantage over your competitors that do not have SOC 2 compliance.
- Security awareness: You conduct vulnerability scans and penetration testing as parts of your SOC 2 prep. These proactive security procedures help you get a grip on your company’s security posture at a point in time. You can use the insights to close the gaps and build a more secure organization.
- Compliance readiness: The security controls and measures prescribed for SOC 2 overlap with other security compliance regulations like ISO 27001 and HIPAA. By preparing for a SOC 2 audit, you build a foundation for other compliance audits as well.
- Peace of mind: It’s difficult to assign a value to peace of mind in terms of measuring the ROI for SOC 2 certification, but if you are responsible for the security of your organization and your clients, you surely understand how important it is to rest assured that your security controls are all in good shape.
The Top 8 SOC 2 Auditors at a Glance
| Name of the SOC2 vendor | Services/Products Offered | Feature Highlights |
|---|---|---|
| Sprinto | SOC2 compliance preparation, evidence management | Use of automation, compliance readiness in 14 days, employee onboarding and offboarding workflows |
| Drata | Evidence collection, cyber-asset inventory, | Continuous monitoring and alerts, automated evidence collection, MDM integration for endpoint evaluation |
| Secureframe | Compliance preparation, vulnerability management | Free cyber security training, vendor onboarding workflow, evidence collection, and monitoring |
| Tugboat Logic | Audit preparedness module | Templated questionnaires for vendors, continuous monitoring of security controls |
| Vanta | Compliance automation platform | Dashboard to monitor security practices, single platform to gather employee information |
| LogicGate | Risk management platform | Risk assessment, risk mitigation |
| JupiterOne | Cyber asset management | Automated evidence collection, automated asset discovery for cloud providers |
| ZenGrc | Compliance monitoring platform | Risk scoring system, easy shift from one compliance framework to another |
As you can imagine obtaining a SOC 2 certification is time-consuming and resource-intensive. Vendors like Sprinto, who offer compliance automation, can expedite the process and minimize your efforts.
1. Sprinto
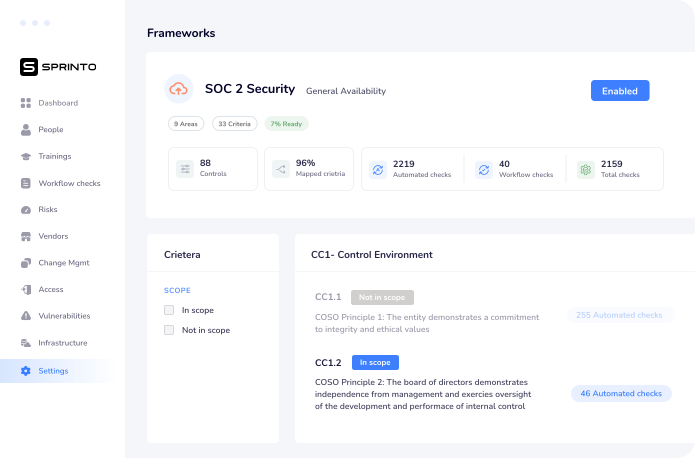
Sprinto offers an automation-driven SOC 2 compliance program that helps cloud-hosted companies to become audit-ready in a fast, error-free, and well-organized way. It automates all the busy work related to SOC 2 compliance and handles 100% of the requirements prior to you facing the best SOC 2 auditors.
Key Features:
- Automation: Sprinto automates controls and policies, reducing audit-ready time from months to weeks.
- Editable security policies: Sprinto offers 20+ editable security policy templates for easy adoption.
- Easy evidence collection: Sprinto automates evidence collection, saving hundreds of hours of audit prep time.
- Auditor-friendly: Sprinto provides a custom Auditor’s Dashboard for easy access to information.
- Continuous monitoring: Sprinto flags compliance lapses and vulnerabilities for ongoing compliance.
Pros:
- Setting up security policies that help deliver a seamless auditing experience
- Facilitates employee onboarding and offboarding
- Helps in mapping your business and creating an auditable catalogue of evidence
- Becoming compliance-ready within weeks, investing just 10-14 hours of your time
The following are some figures that show you the advantages of using Sprinto.
| Area of Expenditure | Without Sprinto | With Sprinto |
|---|---|---|
| Consulting/Gap assessment cost | ~$10k to $30k | 0 |
| Additional cost of software | ~$30k p.a. | ~$3k p.a. |
| Auditor | ~$15k to $50k | Starting at $5k per audit |
| People bandwidth | 3-6 months | ~14 sessions (60-90 minutes each) |
| Total | $50k to $100k + 3 months + uncertainty of audit | ~$8k + Sprinto cost + 14 sessions + zero touch audit |
Cons
- The provided information may be insufficient for users requiring more detailed guidance on SOC 2 compliance
2. Drata
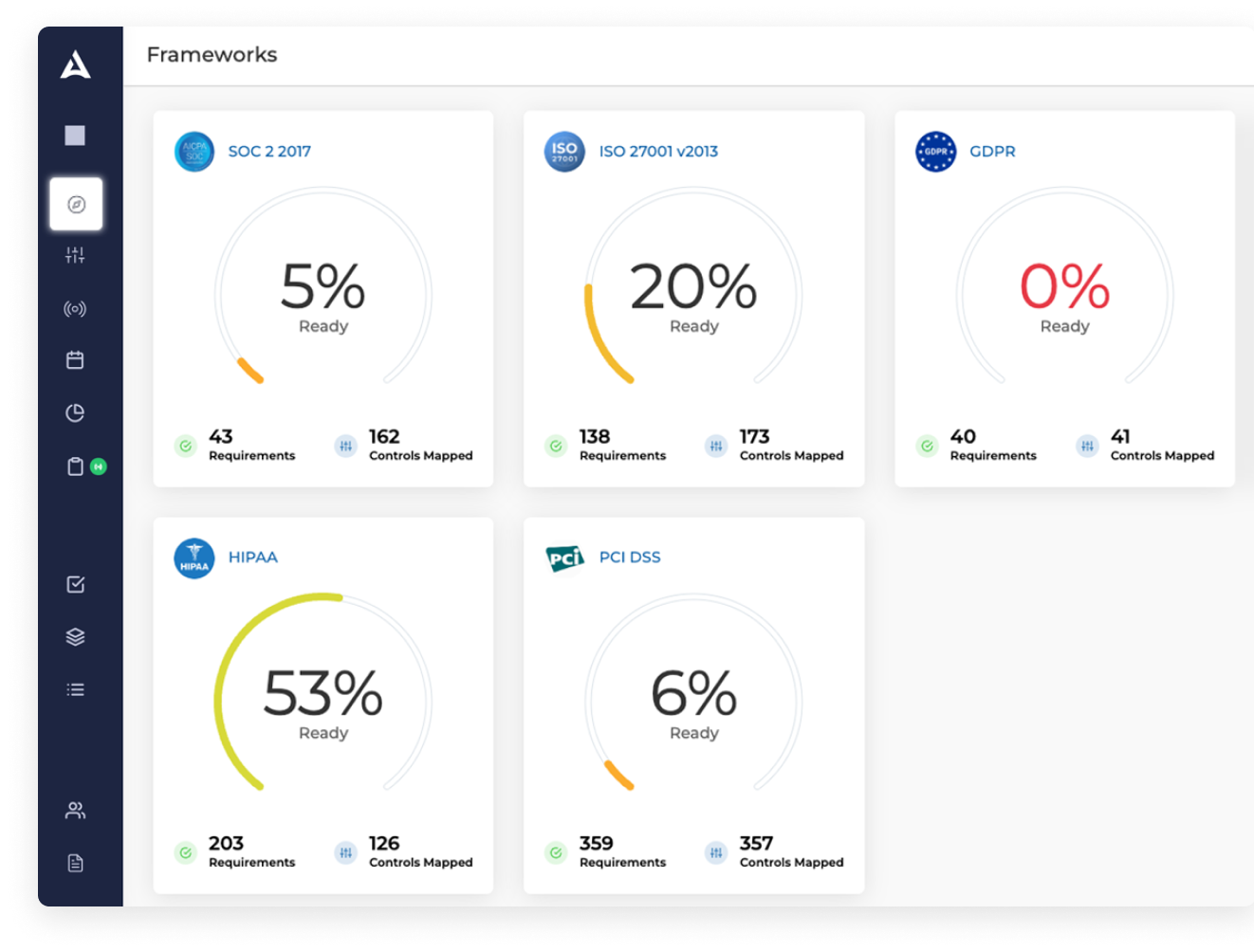
Drata specializes in automated evidence collection for the SOC 2 compliance audit. They help you generate an inventory of cyber assets used by your organization. You also get a significant amount of vendor integration.
Key Features:
- Automation: Automated inventory creation through its asset and personnel tracking feature.
- Continuous monitoring capabilities: Its continuous automated monitoring feature alerts you when a system falls out of compliance.
- Mapped security controls: You can enable specific security controls for only the SOC 2 trust criteria you want to follow.
- MDM integration for endpoint evaluation: It allows for seamless data integration with Master Data Management (MDM) hub to facilitate endpoint evaluations
Pros:
- Automates evidence collection and cataloguing, saving businesses time and effort
- Seamless integration with various tools and platforms simplifying compliance management
- Streamlined the SOC 2 audit process, with user-friendly interface
- Customised policies help cater to your unique needs
Cons:
- Lacks risk assessment features
- Limited reporting capabilities compared to other SOC 2 audit companies
3. Secureframe
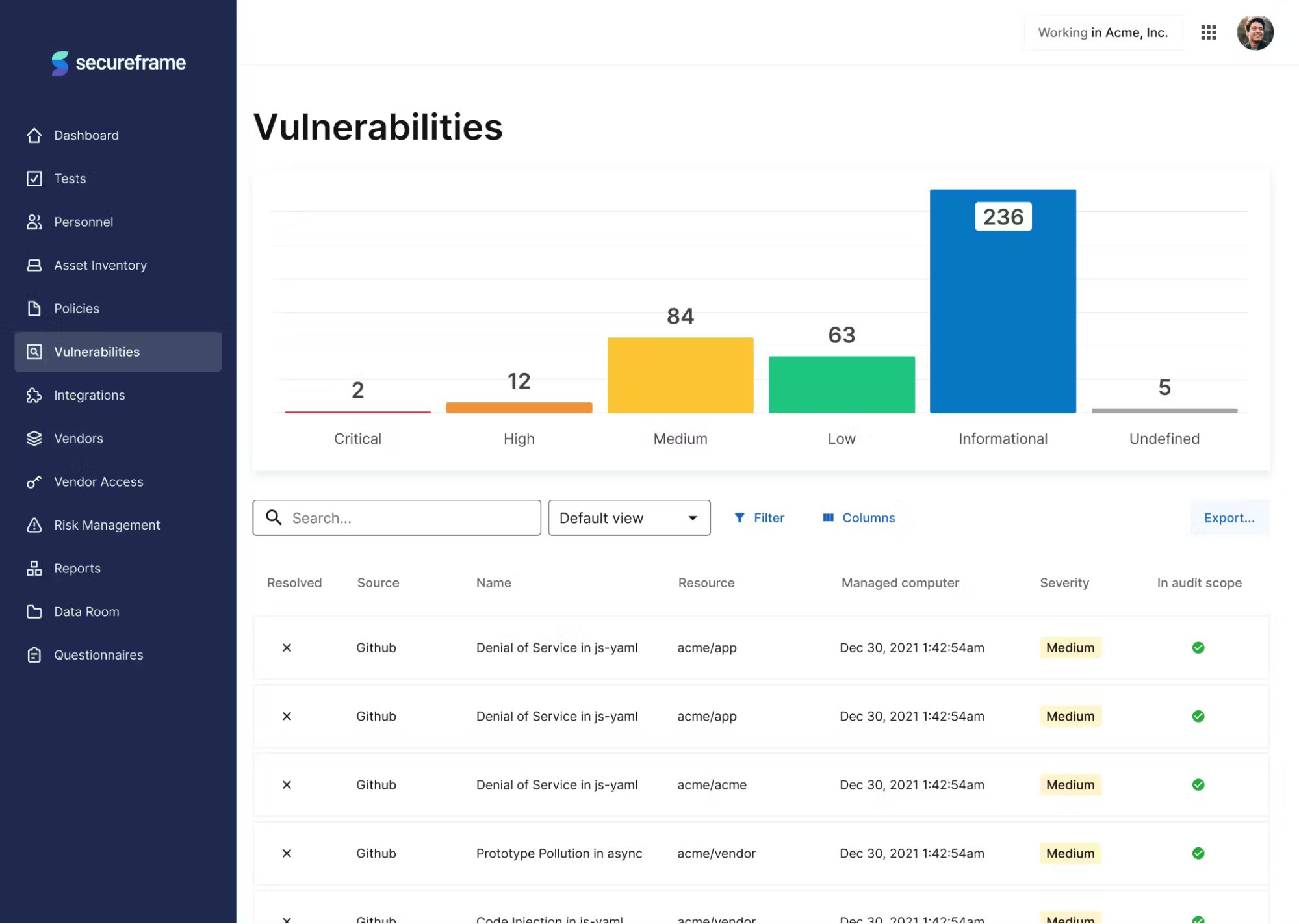
Secureframe is a well-managed compliance preparation platform. Once you signup for a program with Secureframe, they connect all your digital and human resources to the platform and look for vulnerabilities. After identifying vulnerabilities that can block SOC 2 compliance, they create a list of things to be done to mitigate the same.
Secureframe, as one of the leading SOC 2 audit companies, focuses on streamlining the compliance process. They provide you with a customer success manager who helps you put everything in its place.
Key Features:
- Evidence collection: Automates evidence collection and centralized storage to ease access and sharing with auditors
- Vendor workflow: Streamlines vendor onboarding and compliance by managing workflows, assessing vendors for SOC 2 compliance, and centralizing vendor documentation.
- SOC 2 preparedness report: Identifies compliance gaps, offers detailed analysis, and recommends improvements for audits.
- Free cyber-security training: Offers free cybersecurity training to help businesses improve their security posture & SOC 2 Complaince.
- Continuous monitoring: Ensures ongoing SOC 2 compliance by tracking security controls and alerting businesses of changes or risks.
Pros:
- The audit interface simplifies access to information for AICPA approved soc 2 auditors.
- Easy access to information helps avoid the back-and-forth with auditors
- Saves time and effort.
- Reports facilitate easy analysis and remediation
Cons:
- May involve a potential learning curve
4. Tugboat Logic
Tugboat Logic excels in the areas of audit readiness, risk assessment, setting up security policies, and vendor integrations.
Tugboat Logic has a SOC 2 audit preparedness module that helps businesses prepare for SOC 2 attestation. They have pre-built security policies and a central system to keep track of the various security-related tasks assigned to the members of the organization.
Key Features:
- Continuous monitoring of security controls: Ensures compliance by continuously monitoring security controls, proactively identifying and addressing potential issues.
- Vendor-security questionnaires: Provides templated questionnaires for vendor assessments, ensuring vendors meet SOC 2 compliance requirements.
- Mapped security controls: Maps security controls to the SOC 2 framework, facilitating alignment with trust services criteria for compliance.
- Auto-answer RFP management: Machine learning-based module automates security-related RFP responses, saving time and effort.
Pros:
- Automates and simplifies the SOC 2 compliance process
- Central system helps keep track of the various security-related tasks
- Saves time and effort
- Helps you align your controls with the trust services criteria
Cons:
- Pre-made templates may limit options for customization
5. Vanta
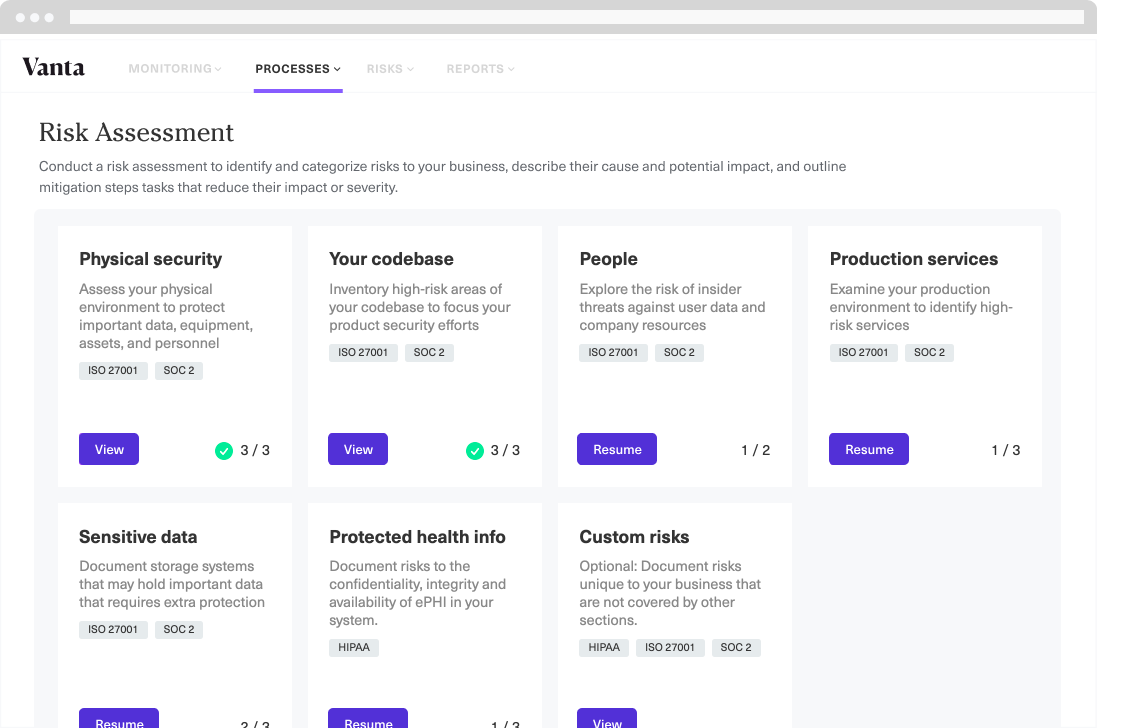
Vanta offers a host of compliance risk assessment products for SOC 2, HIPAA, ISO27001, GDPR, and PCI DSS. We will focus on their offerings as a SOC 2 service auditor.
Vanta helps you prepare for a SOC 2 audit by automating 90% of the tasks around it. The following are some features that help you with the process.
Key Features:
- Tailored security controls: Customize security controls based on your company’s maturity and AICPA guidance, facilitating SOC 2 compliance.
- Unified employee information management: Track employee information, background checks, and security tasks in one place.
- Centralized dashboard: Help monitor security practices, aiding businesses in tracking compliance efforts and identifying areas for improvement
- Continuous testing: Automates evidence collection from various cloud services, with hourly checks and faster annual renewals
Pros:
- Tailored security controls based on AICPA guidance
- Continuous testing for security and compliance verification
- Faster audit report generation
- Simplified compliance management
Cons:
- Limited information on SOC 2 reporting capabilities
- Involves potential learning curve
6. LogicGate
LogicGate offers a risk management platform that is specifically designed for cloud-hosted companies. Apart from various risk management programs, LogicGate has a regulatory compliance program that acts as a SOC 2 service provider and helps companies with overall security compliance preparedness.
Key Features:
- Inventory of regulatory controls: Creates an inventory of relevant regulatory controls, ensuring awareness and compliance with industry-specific regulations
- Risk assessment: Assesses major risks and penalties related to non-compliance
- Up-to-Date regulatory guidance: Integrated guidance on changing regulations, enabling businesses to stay updated with industry-specific changes.
- Regulatory change management: Aids in planning the change management process for regulatory updates.
- Corrective action plans: Mitigate current and future risks of non-compliance, ensuring effective gap resolution and reduced risk.
Pros:
- Helps businesses fix security gaps and remain compliant.
- Helps you stay updated and comply with industry-specific changes.
- Helps you understand and mitigate potential consequences.
Cons:
- May not cover all relevant controls for SOC 2 Compliance
7. JupiterOne
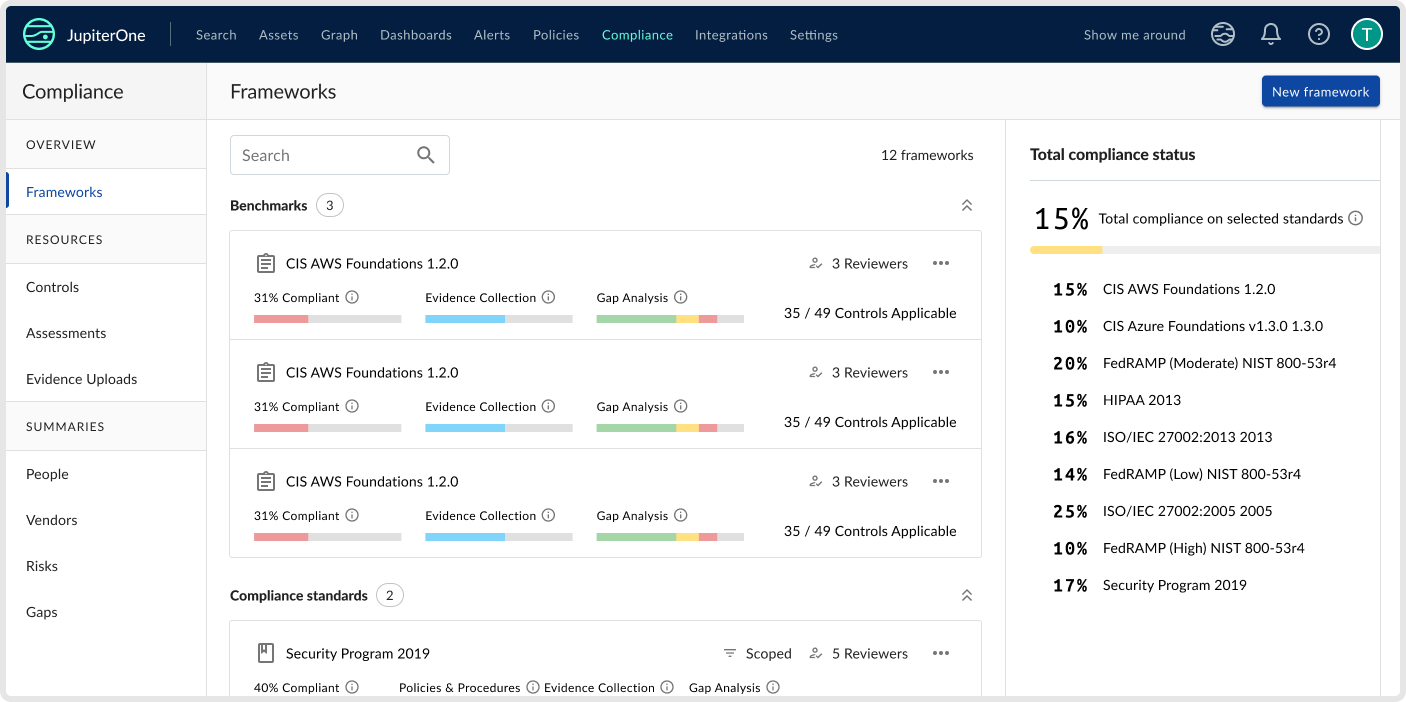
JupiterOne is not specifically a SOC 2 vendor. The company is marketed more as a cyber asset management firm. However, it has some qualities that can help businesses in their compliance journey.
JupiterOne scans your systems and creates a graph representing the connections between different assets. It also has a powerful tool for evidence collection. Between these two features, JupiterOne can help you prepare for a SOC 2 audit.
Key Features:
- Automation: Automates evidence collection, aiding SOC 2 audits and reducing back-and-forth with auditors.
- Thorough inventory of assets: Comprehensive inventory of assets, ensuring businesses identify and protect assets
- Automated asset discovery: Automates cloud asset discovery, helping businesses manage cloud assets effectively
- Detailed view of security environments: Offers a detailed view of security environments, enabling risk identification
- Supports many compliance frameworks: Supports multiple compliance frameworks, such as SOC 2, ISO 27001, PCI DSS, and HIPAA
Pros:
- Central storage of evidence of security controls aids easy access for sharing with AICPA-approved soc 2 auditors
- Helps meet SOC 2 compliance requirements.
- Enables risk identification & mitigation
- Enables you to manage compliance efforts across various standards
Cons:
- Pre-made templates may not meet specific business needs, limiting customization options
8. ZenGrc
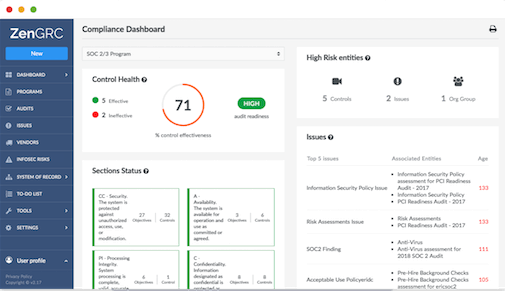
ZenGRC is a compliance monitoring platform by Reciprocity. Instead of being solely a SOC 2 service provider, it is a center for multiple compliance frameworks and it makes it very easy for its clients to shift from one framework to another. While its evidence-collection tool does not come with a lot of integration options, you can use an open API to integrate the tool with other vendors.
Key Features
- Customizable risk assessment and scoring: Allows businesses to tailor risk assessment and scoring systems to meet your specific needs.
- Risk monitoring and alerts: Offers a system for monitoring and alerting potential risks
- Mature evidence collection tool: Provides a robust tool for collecting and storing security control evidence
- Seamless compliance framework: Facilitates easy management of compliance efforts across multiple frameworks, like SOC 2, ISO 27001, and PCI DSS
Pros:
- Facilitates internal audits and provides a streamlined process
- Enable multiple compliance frameworks
- Helps with cybersecurity controls and vendor risk management
Cons:
- Limited integration capabilities
What are the aspects considered for selecting these SOC 2 vendors?
The two fronts on which a good SOC 2 vendor can make a huge difference, Evidence Management and Risk Management.
What is evidence management?
Evidence in the context of cyber security refers to any information of value held by an organization that has investigative value.
The AICPA approved SOC 2 auditors need to access a certain level of evidence gathered from all digital resources used by the organization under investigation and its employees. These resources would include a workspace like Microsoft 365 to cloud providers like AWS.
A tool that automates most of the process of evidence collection and ensures that no stone is unturned is the one you should look for.
What is risk management?
Risk management is concerned with assessing the security risk faced by an organization and finding ways to mitigate that risk. Many SOC 2 service auditors help their clients with pre-built security policies, cyber-security training, and security control monitoring to help them achieve compliance.
6 steps leading to a SOC 2 Compliance audit
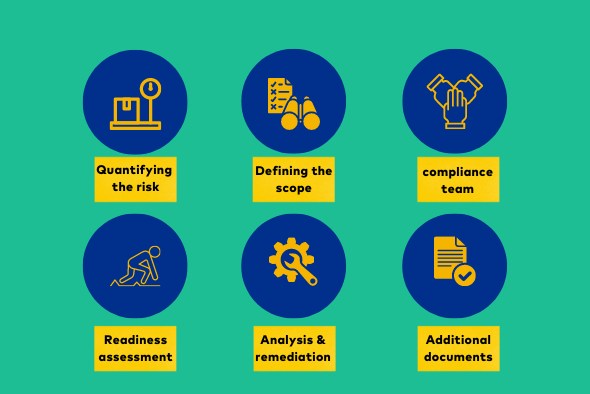
We will not discuss these steps in too much detail, we’ll just brush up on your knowledge so that you can relate these steps to the offerings of the SOC 2 audit firms on the list and make an educated decision.
Step 1. Quantifying the risk
Identifying the business assets that come under the SOC 2 audit, and the financial impact of securing those assets.
Step 2. Defining the scope
The SOC 2 audits are focused on one or multiple trust service criteria as you already know. Depending on what TSCs you are targeting, the industry you are in, and the kind of results you are looking for, the scope of the SOC 2 audit is determined.
Step 3. Building a compliance team
Security compliance is not a one-time event, it is like a marathon that you need to run for the entirety of the existence of your business. It is very important to create and distribute ownership of various aspects related to the SOC 2 compliance process.
Step 4. Readiness assessment
This is the process of identifying areas that need work before the SOC 2 auditor is invited. This is the area where the best SOC 2 auditors can make a huge difference.
Step 5. Gap analysis and remediation
This is an extension of the previous step where the gaps are mitigated and the risks are taken care of. Security controls are placed, and evidence is collected to support that.
Step 6. Gathering additional documentation
The SOC 2 auditor will require a lot of documentation related to security controls in place, checklists, records of employee and vendor onboarding and offboarding, and whatnot. You will receive a list of these documents and the SOC 2 vendor will help you gather them.
As a part of your SOC 2 compliance-readiness campaign, you will need a reliable pentest partner that can help you identify critical vulnerabilities and fix them. You can run compliance-specific scans with Astra’s vulnerability scanner. Getting a manual pentest done to get rid of business logic errors is also highly recommended.
Conclusion
A SOC 2 audit can be a challenge for any organization but getting the right SOC 2 auditor can really ease things up. When you automate a major part of the grunt work around compliance preparation, you can save a lot of time and resources. We have introduced you to the best in the business. Go ahead, check them out, and find out what works for you.
FAQ
1. Are SOC 2 auditors and SOC 2 vendors the same?
Not necessarily. The primary objective of SOC to vendors is to help you prepare for a compliance audit. It may happen that a SOC 2 vendor helps you find an auditor.
2. How much time does a SOC 2 audit take?
The timeline for a SOC 2 audit is largely variable. After you have prepared for the audit, the audit may take up to a couple of months. The preparation leading to the audit is where you can save a lot of time by choosing the right vendor.
3. How much does a SOC 2 audit cost?
So, the cost of a SOC 2 audit can vary depending on factors like the size of the company and the scope of the audit. For small to midsize companies, it’s usually between $12,000 to $20,000 on average but can go up to $100,000 for the whole process.
4. How long is a SOC 2 report valid?
SOC 2 reports are valid for 12 months from the issue date. Conduct annual audits to stay compliant. Type I covers a specific time, and Type II assesses control effectiveness over 3-12 months; AICPA suggests a minimum 6-month reporting period for Type II.
5. Who can perform a SOC 2 audit?
So, a SOC 2 audit, is conducted by an external auditor from a third-party audit firm. These auditors are usually certified public accountants (CPAs) who specialize in SOC 2 compliance.
















