If you’re a SaaS vendor in healthcare, finance, or any industry, the value of solid foolproof security cannot be overstated. The data generated by your business is always a prime target for malicious entities. Add to this, the healthy growth of your business also depends on good security. The current digital landscape necessitates invaluable attention to security for any business with an online presence.
This is where security compliance comes in. Adherence to industry-relevant security standards automatically raises your business security and its persona. One such popular security compliance standard is System and Organization Controls Type 2 or SOC2.
SOC 2 is a globally recognized security auditing standard. It requires your business to meet certain criteria known as SOC2 security compliance requirements for a SOC 2 certificate to be issued. This article will discuss the SOC 2 compliance requirements in detail and how they will help your business.
Action Points
- SOC 2 compliance requirements are criteria set by the AICPA for companies to achieve in order to attain SOC2 compliance.
- The SOC 2 compliance requirements are based on the five trust services criteria (TSC) which include security, privacy, confidentiality, availability, and processing integrity.
- SOC2 compliance security requirements comprise 9 common criteria series that are concerned with controls, communications, risk assessments, and monitoring.
- SOC requirements for privacy and confidentiality include guidelines for securely maintaining and disposing of personally identifiable information or PII and any information deemed sensitive.
- Availability SOC compliance requirements ensure that data and systems are accessible to concerned parties.
- SOC2 processing integrity requirements are placed to ensure that systems and data processing are accurate and complete.
What Are SOC 2 Compliance Requirements?
SOC 2 compliance requirements refer to the criteria put forward by AICPA (Association of International Certified Professional Accountants). These criteria have to be met by all companies looking to attain SOC2 compliance certification and pass an audit from an independent auditor.
If you’re a company within the healthcare or finance sector, or a SaaS vendor, having SOC2 compliance adds remarkable value to your company’s services and security. Similarly, other businesses include data centers, cloud platform providers, and ultimately any company that places importance on cybersecurity.
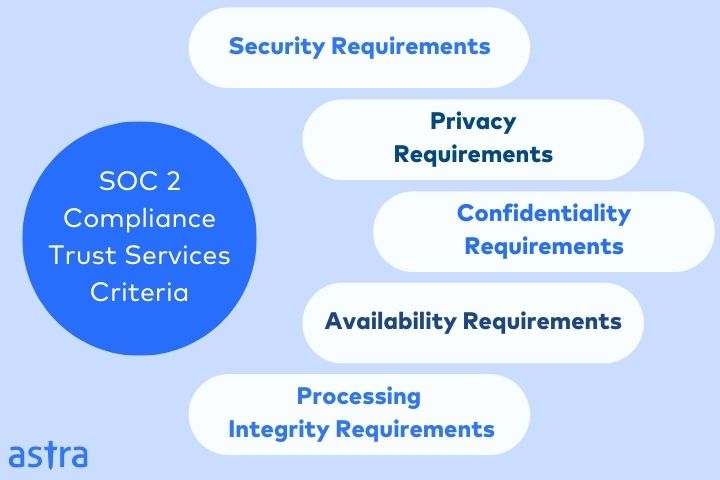
The AICPA categorizes these requirements into five categories known as the Trust Services Criteria. It includes:
- Security: SOC 2 security requirements protect data systems from any system damages, unauthorized access, and disclosure of information that could tamper with the other SOC2 trust services or your company’s ability to meet its compliance objectives.
- Privacy: SOC2 privacy requirements ensure company’s data is collected, used, retained, and disposed of per SOC2.
- Confidentiality: This set of requirements is designated to protect information that is marked as confidential.
- Processing Integrity: These requirements ensure that your company’s systems processing is complete, valid, accurate, and authorized to meet the objectives of your SOC2 audit.
- Availability: Ensures that the systems and data are available for processing and use as a part of meeting the SOC 2 objectives.
What Are SOC 2 Requirements?
As mentioned previously, the SOC 2 compliance requirements are categorized based on the five different trust services criteria (TSC). Let’s take a look at them.
1. Security Requirements
The security criteria are called common criteria since a lot of them overlap with the other Trust Services Criteria for evaluating systems. The first 5 SOC 2 criteria are mandatory while the rest are optional.
CC1 Series – Control Environment
These requirements assess your company’s control environment. It checks for accountability, staff training, and more. How your company shows its commitment to ethical values, development, and retention of good team members, and demonstration of an accountable culture are assessed and evaluated. Your company’s leadership and clear structuring of responsibilities and reporting are also assessed.
CC2 Series – Communication and Data
These series of security requirements check how well your company demonstrates the right data management measures to check how they are collected and shared. Using relevant data to support IC, and having clear communication of controls and objectives with external parties are some controls mentioned in this series of requirements.
CC3 Series – Risk Assessment
This set of requirements assesses whether your business follows the current and relevant risk assessment techniques. It mainly focuses on technical vulnerabilities and financial flaws.
The risk assessment controls require your business to have clear a scope that allows regular risk assessments such as vulnerabilities assessments or penetration tests.
It also requires you to show the identification and analysis of all business risks that could damper your business and SOC 2 compliance objectives. Such identification and assessment of risks should also be done if and when there are major changes within your assets.
CC4: Monitoring of Controls
This set of criteria focuses on your company’s compliance monitoring capacities such as regular evaluations of internal policies, and accurate communication of identified deficiencies in them. It also determines and evaluates your company’s reporting processes.
CC5: Design and Implementation of Controls
Your company’s effectiveness in the execution of compliance initiatives is checked to ensure that it can adopt various compliance measures into different tech stacks within the organization. It checks for adequate development of risk mitigation controls, & other tech controls based on pre-defined policies to meet SOC 2 objectives.
CC6: Controls over Logical and Physical Access in SOC 2
Requirements in CC6 relate to your company’s compliance measures and its security capacities with regard to data access, handling, and deletion practices.
CC7: Systems and Operational Controls for SOC 2
Having the right systems and operational controls is important in achieving SOC 2 compliance. The major focus of CC7 is on your company’s incident response plans and capacities.
CC8: Controls for SOC 2 Change Management
This assesses how your company navigates through changes in management and shifts in policies and what processes are implemented for the same.
CC9: SOC 2 Risk Mitigation Controls
SOC2 assessments involve checking the measures your company has in place to identify and mitigate risks. This includes internal risks as well as vendor, third-party, and partner risks.
2. Privacy Requirements
SOC 2 privacy requirements are guidelines placed to help protect any PII or personally identifiable information from unauthorized access or any breaches of security within your company.
It is important to note that privacy only applies to personal data whereas confidentiality applies to any information deemed sensitive. SOC2 has eight privacy requirements that check various aspects of personal data security.
- Ensuring client understanding of how and why their personal data is stored by your company.
- Clearly communicate the choices parties have over their data to establish proper personal data authority.
- Ensure your company’s PII collection processes match its stated aims.
- Ensure your company has proper safeguards for the use, retention, and proper disposal of PII such as using data encryption, MFA, and access controls.
- The PII stored by your application or business should allow customers access to their PII for any corrections, updations, and reviews.
- Ensure your company has proper PII breach or disclosure notification policies that cover essentials on post-breach communication to clients.
- Make sure your company’s data storage is current, accurate, and up-to-date in terms of security to ensure the integrity of the stored PII.
- Ensure the effectiveness of your company’s response processes for any PII-related queries including its monitoring.
3. Confidentiality Requirements
Confidentiality requirements under SOC2 help guard any data that is deemed confidential by your company. This is mostly done by limiting access to only a section of authorized personnel.
Major controls mentioned under confidentiality requirements include:
- Identification and maintenance of confidential information by your company to prevent its compromise.
- Having proper processes for the disposal of confidential information to meet your company’s SOC2 confidentiality objectives.
4. Processing Integrity Requirements
This set of requirements is used to evaluate your cloud environment, data processing, and storage to see if it matches the needs of your business. This series of SOC 2 compliance requirements is mostly concerned with how data is managed and not the data or its security as such. It comprises five criteria:
- The efficacy with which your company understands its data processing goals from data metrics to company goals.
- Placing policies and procedures for system inputs that aid in better accuracy and meet company aims.
- Maintaining data processing quality by placing effective measures and policies.
- Placing policies and procedures to allow data output for internal or external demands.
- Maintaining adequate data storage systems with policies and procedures that cover the company’s specifications.
5. Availability Requirements
This refers to how accessible the information stored and the services provided by your company are. The SOC 2 compliance requirements for availability essentially help data accessibility through monitoring and maintenance. The controls mentioned under this trust services criteria include:
- Ensuring your company’s technical capacities allows it to meet your business objectives and also monitors and manages processing.
- Address how your company would recover from disruption by having proper data backup processes and recovery measures.
- Test out your company’s recovery plan and its real-world viability.
How Can Astra Security Help With SOC 2 Compliance Requirements?
Astra Security’s round-the-clock vulnerability assessment and SOC2 penetration testing assess your company’s internet-facing assets as quickly and efficiently as possible to detect vulnerabilities that require mitigation.
Astra does this by providing risk assessments in the form of automated and manual vulnerability scans, assessments, and comprehensive pentest. Along with this, Astra also provides SOC 2 compliance to help you identify where your assets’ SOC2 compliance is hindered.

Our VAPT offerings help with:
- Maintenance of compliance with regulatory requirements like SOC2, HIPAA, PCI-DSS, ISO 27001, and GDPR.
- Better security coverage for web and mobile applications, cloud infrastructure, networks, and APIs.
- Detection and remediation of vulnerabilities and security gaps of varying criticality.
- Shifting from DevOps to DevSecOps giving due priority to security testing applications in SDLC.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Conclusion
SOC2 compliance is standard compliance for any company wanting to showcase its strong data security and privacy measures. The best way to increase your reliability and trustworthiness in the services provided by your company is to obtain a SOC2 certification.
Achieving SOC2 compliance comes after an audit that determines how successfully your assets are compliant with the controls mentioned in the SOC 2 compliance requirements. Compliance scans and risk assessments with Astra Pentest help further your quest to achieve SOC2 compliance.
FAQs
Why do companies need SOC2 compliance?
Companies need SOC2 compliance as it helps demonstrate the high level of information security that is maintained. SOC2 compliance requirements are rigorous and meeting them automatically makes the company and its services more reliable and trustworthy for potential customers.
What is SOC2 compliance vs ISO 27001?
ISO 27001 is compliance that provides a scope for data management and information security management systems whereas SOC2 is much more focused on showing that a company has in fact placed essential data security controls.
Is SOC2 compliance mandatory for companies?
SOC2 compliance is not a mandatory requirement for companies. However, more customers are requiring vendors to show a SOC2 certificate or report to continue with deals. This is important because having SOC2 compliance implies the standards of your company’s security measures.
















