Article Summary
This article discusses all aspects surrounding top SaaS security tools. From the features to look for, the top SaaS security companies and their details to the best practices that can optimize SaaS security, this article mentions it all, so keep reading folks!
Businesses nowadays find it tedious to have huge data centers to store and maintain software and this is where Software-as-a-Service or SaaS found its niche. By allowing the applications to be accessed over the internet, companies can save a lot on software and hardware management cost, physical security, and storage space.
But as with every new niche, SaaS also comes with areas that need continued focus and improvement. With SaaS, this comes in the form of security. Since all the software details and customer information are stored within the SaaS provider’s servers, like candies in a pinata, it definitely comes with the risk of attackers attempting to hack into the servers, similar to how kids whack at a pinata.
However, unlike breaking open a pinata, breaking into SaaS servers is illegal and punishable as it puts the data of all its customers at risk. Therefore it becomes a top priority to protect SaaS applications and the servers they are hosted on. This is where SaaS Security Tools provide the ultimate protection against all security threats.
SaaS Security Tools are the single-stop destination for all your SaaS security requirements. Making use of SaaS or cloud penetration testing tools makes maintenance of SaaS servers and application security a hassle-free process. These tools provide compliance checks, and monitoring of assets and employ the best security practices to ensure the safety of your SaaS application.
This article will provide further clarity on all things SaaS security tools related for you to understand including its importance, features to look out for in good SaaS security tools, and the best tools in the arena currently. Finally, it walks you through some of the best practices to opt to enhance the safety of your SaaS applications.
Why Is SaaS Security Important?
Below mentioned are some of the major reasons why SaaS security is so vital:
- Compliance
Securing SaaS forms an important part of maintaining compliance with regulatory standards and laws like ISO 27001, HIPAA, or PCI-DSS. Compliance is becoming stringently important for all companies globally. SaaS security ensures the continued compliance of the SaaS server and application thus reducing the risk of non-compliance and subsequent penalties or other charges. It also makes the SaaS or cloud service providers an attractive candidate for potential customers owing to their compliant nature.
- Data Security
One of the major reasons to implement Saas or cloud security solution concerns the safety of data, this can be client data or software-related information all of which are extremely confidential in nature and as such requires continuous monitoring, vulnerability assessments, and regular patch updates to ensure their continued safety. Continuous assessments form the crux of maintaining the safety and security of data in SaaS.
Also Read: A Complete Guide to Cloud Security Testing | Continuous Penetration Testing: The Best Tool You’ll Find in 2022
- Reliability
Having SaaS security and the best measures for it implemented makes the cloud service provider seem more reliable and trustworthy. It raises the bar for confidence in customers due to increased vigilance in place to protect their applications and data throughout.
- Something for the Sales Team Boast About
Having good SaaS security tools in place is a vital component for companies that are looking for a SaaS provider. Here, cloud services that already have a great SaaS security system in place with continuous scans, monitoring, and safety measures in place have the upper hand. This is because the sales team can use this as an attribute that appeals to potential customers.
Also Read: 5 SaaS Security Certifications to Wrap Your Head Around
Comparison Table of Top SaaS Security Tools
| SaaS Security Tools | Products | Pros | Cons |
|---|---|---|---|
| Astra Security | Vulnerability Scanning, VAPT services, Malware Scanner, Firewall | 8000+ tests conducted. Zero false positives assured. Affordable prices. Supportive security team. Interactive dashboard. | Does not provide free-trials. |
| Intruder | Internal and External Vulnerability Scanning, Continuous Penetration Testing | Pro-active scanning with real-time alerts. Applies latest security patches for safety. | Does not provide manual penetration testing. |
| Cloudflare | Web Application Firewall, Encryption, DDoS Protection | Largest server networks. Scalable services. Provides security to anything from servers to domains and installations. | The main focus is on protecting public-facing applications like websites and APIs. |
| Orca Security | Shift Left Security, Identity Access, Management, Malware Detection. | Aids in compliance enforcement. Provides protection for high-risk data like PII. Provides alert on Slack or other mediums when configured. | Quote available on contact. |
| Rubrik | Cloud Security, Secure backups, Ransomware Protection | Provides security for hybrid, virtual and physical platforms. Unified cloud backups with precise data recovery. | Pricing is only available on demand. |
| TOPIA | Patchless Protection, Network Scanners, 0-Day Detection | Emphasis on vulnerability management. Assured cloud security over multiple vendors. | Much more applicable for larger enterprises. |
| Zscaler | Ransomware Protection, Cloud Security, SSL Inspection, Zero Trust Exchange | Offers services like file recovery and integrity monitoring. Inspection of SSL traffic for malicious activity. User-friendly interface. | Pricing options are available only on contact. |
Features to Look for in SaaS Security Tools
- Data Security
Ensure that the SaaS security tools you have shortlisted have good measures in place to ensure data safety. This can include enabling data encryption like Transport Layer Security (TLS) to protect data that is in transit. It can also be enabled for data at rest along with enabling multiple levels of security.
Another method is to allow the encryption keys to remain with SaaS customers thus ensuring that server-side employees can not gain access to confidential data. Continuous vulnerability assessments are also crucial in ensuring that the data remains safe since the discovered vulnerabilities will immediately be fixed.
- Continuous Assessments
Continued vulnerability assessments help assess the security system for any vulnerabilities. If such vulnerabilities are discovered, they are mentioned in a detailed report with measures that can be taken for remediation. Vulnerability assessments are much easier to carry out on a frequent basis.
A good vulnerability scanner should be able to detect any known vulnerabilities, OWASP 10 and SANS 25. Vulnerability assessments should also be done every time a feature is updated or introduced into the platform as it could have hidden vulnerabilities. These are also relevant to maintaining compliance.
- Security Audits
This is a systemic analysis of the security protocols in place to protect your organization. Cloud security tools that provide audits analyze every aspect of the security measure unlike a vulnerability assessment or a penetration test which works to find vulnerabilities and exploit them. It generally focuses on hardware and software configurations, physical security measures, devices used, and so on.
SaaS security audits are crucial for achieving and maintaining compliance with regulations like SOC2, ISO 27001, and standard laws like HIPAA and PCI-DSS. Audits must be done at least once a year or preferably twice a year to ensure maximum safety. Doing so increases the level of client trust in your SaaS server.
Also Read: Cloud Security Audit: Everything You Need to Know
- Compliance
As mentioned earlier, compliance is an important aspect of SaaS, and therefore when choosing a SaaS security tool it is crucial to assess what all compliances they adhere to and whether it aligns with the regulatory compliances that your organization needs to meet. The most important compliance standards are HIPAA, GDPR, PCI-DSS, SOC2, and ISO 27001.
With each regulatory body, the standards that need to be met may vary. SOC2 is a certification that focuses more on cloud security solutions and continuous monitoring of the safety protocols implemented for the same. Therefore, ensure that the SaaS security tool you choose provides continuous compliance checks to ensure that your organization is compliant throughout.
- Integration
Make sure that the SaaS security tools you are considering provide integrative possibilities thus enabling you to integrate the SaaS security tool and its testing features into your CI/CD pipeline. This ensures that every code update is scanned for vulnerabilities automatically before hitting the production phase. You get security without compromising on the speed of delivery.
This essentially allows your organization to make the move from DevOps to DevSecOps a methodology where security is also given prime importance. The integrative capacities of a SaaS security tool allow it to provide security and testing to your projects across multiple platforms.
Read also: 8 SaaS Security Solutions You Can Count On
Top SaaS Security Tools
In this section, some of the top SaaS security tools and their features have also been mentioned. Additionally, a table showing the pros and cons of each tool is also featured.
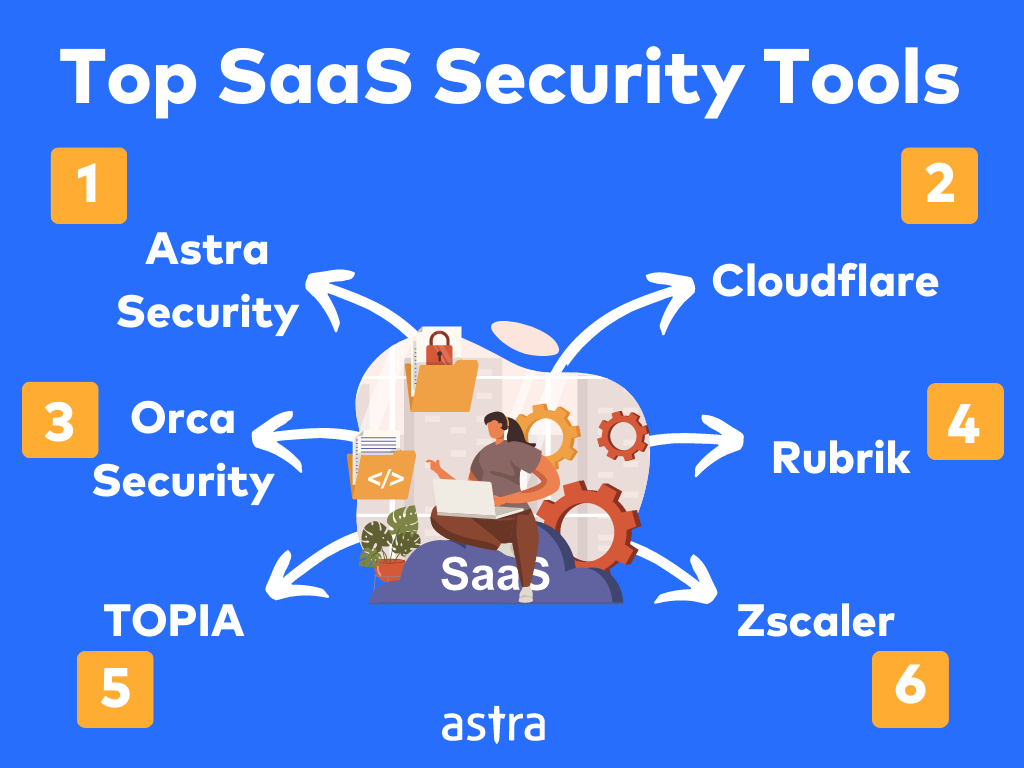
- Astra Security
One of the topmost SaaS security tools, Astra provides protection for SaaS applications, websites, cloud infrastructure, and APIs with a well-established security tool- Astra Pentest Suite.
Features:
- Powerful vulnerability scanner that can detect vulnerabilities from known CVEs, OWASP Top 10, SANS 25, and based on intel. Based on this detailed fixing measures are provided through video POCs and detailed reports.
- Provides VAPT services and regular audits to ensure that the SaaS is regulation-compliant and free of any vulnerabilities. This service can also be integrated into an organization’s CI/CD pipeline ensuring the security of projects from the get-go.
- Provides website protection with a powerful firewall and malware detection. Unlike other SaaS security tools, Astra also provides publicly verifiable certificates that boost the trustworthiness and clientele of one’s organization.
2. Intruder
This vulnerability management software helps provide SaaS security to companies with finite resources and helps run efficient and effective vulnerability management.
Features:
- Offers internal and external vulnerability scanning as well as continuous penetration testing.
- Asset discovery and tagging options.
- Risks and patch management services are offered for the SaaS services.
3. Cloudflare
This popular online protection service offers reliable protection for SaaS services, websites, APIs, and all things in connection with the internet.
Features:
- Provides optimized, high-speed connectivity between devices.
- Network protectivity against external attacks.
- Secures resources like cloud applications, web services, and applications.
Also Read: Penetration Testing Quotes to Look out for in 2022
4. Orca Security
This agentless SaaS security tool ensures targeted visibility to AWS, GCP, and Azure. It works through immediate identification of assets which are then scanned for any resolution requirements or other security ambiguities.
Features:
- Provides behavioral analytics of the SaaS applications and other public cloud platforms.
- Other features like data encryption, antivirus, potential intrusion, and threat detection are also provided.
- Involves a simple 3-step process that included discovery, monitoring, and assessing the SaaS application assets.
5. Rubrik
This tool is perfect for SaaS applications with complex architectures as it provides extremely secure backups with pin-pointed restoration facilities.
Features:
- It provides centralized data management to gain full accessibility regardless of the environment leading to simplified control.
- Ultimate and impregnable data backup security which helps in easy recovery in case of any disastrous events.
- Provides data safety even when it is stored as a backup with the help of immutable storage.
6. TOPIA
This innovative SaaS security tool collects relevant data on assets across the digital infrastructure to analyze them for threats and rank them based on severity so that they can be fixed quickly.
Features:
- SaaS applications are scanned in real-time to ensure the identification of any threats and appropriate patch management to fix them.
- Amazing GUI that makes it easy for users to navigate through with regards to vulnerability identification and effective response.
- Provides patchless protection feature on applications by securing it with a force field with the aid of binary instrumentation that gives in-memory protection.
7. Zscaler
Yet another leading cybersecurity provider, Zscaler provides the users with a tight zero-trust security posture that can be managed at all aspects, thus making navigation easy and the security posture more secure.
Features:
- Distributed cloud-based security for web, email, and mobile computing regardless of client locations.
- Identifies SaaS application misconfigurations and improper access authentication to provide remediation measures.
- Provides secure access to the SaaS application with alerts for any anomalies or threats found.
Also Read: 11 Top Penetration Testing Tools/Software of 2022 [Reviewed]
Best SaaS Security Practices To Follow
- SaaS Security Checklist
It is an essential practice for every SaaS vendor to maintain a SaaS security checklist. This can provide easy access to the requirements that need to be met by the SaaS providers and customers equally. It also ensures a smooth transition from one stage of assessment or implementation to the next without making any mistakes in the process.
Each and every organization will have different priorities and processes for building a checklist. However, the general areas that need to be monitored and mentioned in the SaaS security checklist are the security protocols implemented, the status of compliance, ensuring data encryption both during rest and in transit, authentication procedures, and automated backups.
- Access Management
Identity access management is a system used to verify each user’s identity and determine whether the user has the right to use or download data from a SaaS application. In short, the system works to authenticate, authorize and screen users for activities on a SaaS platform that they may or may not perform.
This form of authentication and authorization also enables role-based access control and multi-factor authentication, requiring users to present at least two pieces of proof of identity to be able to gain access. This provides a high level of scrutinized security that reduces the chances of identity theft or malicious actors trying to gain access.
- Regular Penetration Tests
Penetration testing is the process of finding vulnerabilities within a security system and trying to gain access through hacker-style exploitation. These tests are extremely beneficial in analyzing the damaging impact a vulnerability could have on the security system thoroughly. This can be done for networks, web applications, APIs, and cloud infrastructure.
Regular penetration testing and its integration into your organization’s CI/CD pipeline can make application development go much smoother, faster, and more efficiently. Doing such penetration tests allows you to be ahead of any hackers who may find and exploit their vulnerabilities. The detailed reports provided at the end of a test can help the developers in patching the issues found.
Also read: Astra Pentest Suite’s VAPT Guide
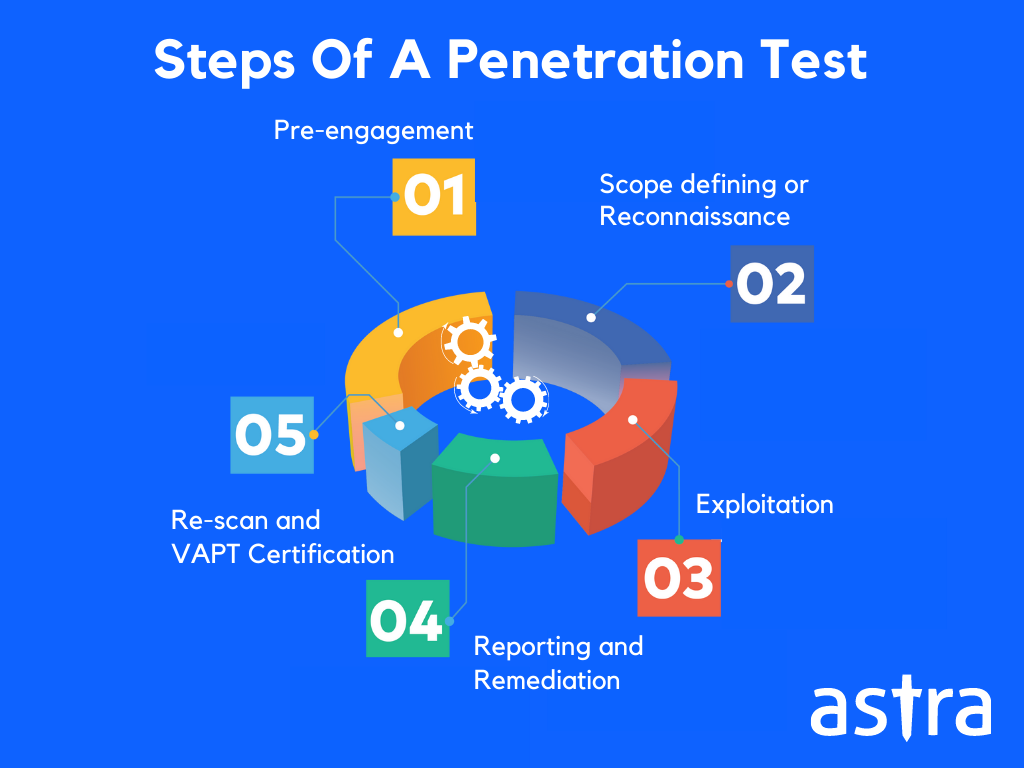
- Incident Response Planning
Backing up all the relevant data must be done periodically to ensure that the original data can be retrieved without any major complications if any disaster strikes or a breach takes place. This makes it an important part of disaster recovery and incident response plans.
Enabling a data retention policy is also a must to ensure that only relevant data is stored on servers and other superficial, yet important data is deleted from them after a certain period of time. This provides an additional layer of security in SaaS security management as the client-side information isn’t available for extended periods of time without due cause.
Conclusion
This article has provided detailed information on various aspects of SaaS security tools, right from their importance, and factors influencing the choice of a tool to the best practices for SaaS security. Additionally, this article has also mentioned some of the best SaaS security tools available along with the features that make them the best in the field as well as a table of pros and cons for each tool. All the information made available in this article will make choosing the right SaaS security tool an easy decision for you.
FAQs
1. Why is SaaS more secure?
Software as a Service or SaaS is more secure since it most often employs Transport Layer Security to protect data in transit while encryption is also offered for data at rest.
2. Who does the responsibility of SaaS security fall on?
Generally, the responsibility of SaaS security falls on the SaaS vendors who have to ensure that their cloud servers, physical infrastructure, and application security are top-notch. However, SaaS customers must also do their due diligence before opting for a SaaS vendor to ensure the maximum safety of sensitive data.
3. What is the relevance of SaaS security?
SaaS security is relevant as it ensures compliance of applications, and security of data and helps in incident recovery if good policies are implemented. It also makes the applications less vulnerable to external attacks.
















