A penetration test report is a comprehensive security analysis report of a computer system, network, cloud, web, mobile application, and even human weaknesses that could lead to a security failure. A pentest report includes insights into the vulnerabilities discovered, their impact, severity, affected components, steps for re-creation, and remediation.
Simply put, a penetration testing or VAPT report is your roadmap to strengthening your cybersecurity posture, winning customers’ trust, and securing critical data. Moreover, it helps mitigate legal ramifications, such as avoiding the non-compliance fees associated with mandatory industrial standards like GDPR, HIPAA, etc.
Let’s deep-dive on why a Pentest report is crucial for an organization to improve its security posture!
Benefits of Penetration Testing Report
The pentest report is equally important to stakeholders, including company executives, developers, customers, vendors, and compliance regulatory bodies.
Since security analysts prepare the pentest report for companies undergoing a pentest, we’ve listed a few benefits that a company and security analyst derive from the same:
| Feature | Benefits for the Company | Benefits for the Security Analyst |
|---|---|---|
| Leverage Comprehensive Evaluation | Prioritize security risks based on potential impact, severity, and actionable remediation steps. | Identify key focus areas and design targeted remediation strategies. |
| Foster Secure Code Writing Practices | Ensure the engineering team indulges in writing secure code proactively. | Proactively reduce debugging and recoding workload by avoiding repeated vulnerabilities in future iterations. |
| Track Year-on-Year Progress | Identify recurring issues, prioritize continuous monitoring, and improve overall security posture. | Measure the effectiveness of implemented security measures and identify areas requiring further attention. |
| Adhere to Security Benchmarks | Achieve compliance with industry and international standards by identifying vulnerabilities and providing evidence of remediation. | Refine in-house testing procedures and remediation patches to prioritize vulnerabilities penalized by specific standards. |
| Build Trust with Customers | Demonstrate commitment to transparency and customer data safety through rescan reports and verifiable certificates. | Help companies build a transparent narrative by communicating report findings clearly. |
1. Leverage Comprehensive Evaluation
VAPT reports offer a comprehensive analysis of vulnerabilities across your network, applications, and websites, detailing potential impact, severity, risk factors, and actionable remediation steps to help CTOs and CXOs prioritize security risks.
Moreover, a detailed analysis helps engineering teams identify key focus areas and design targeted remediation strategies.
2. Foster Secure Code Writing Practices
Pentest reports guide iterative secure coding, revealing exploitable flaws and prioritizing critical fixes. This helps strengthen the trust of existing customers in your business and encourages word-of-mouth referrals.
Likewise, such reports not only help remediate but also help developers avoid repeating the same in future iterations, thus proactively reducing the debugging and re-coding workload.
3. Track Year-on-Year Progress
The pen testing report provides a baseline for your security posture. It allows you to track your progress over time, identify recurring issues, prioritize continuous monitoring, and improve your overall security posture.
Furthermore, by providing a historical reference point, the report also enables analysts to measure the effectiveness of implemented security measures and identify areas requiring further attention.
4. Adhere to Security Benchmarks
Every business must adhere to specific industrial and international benchmarks such as HIPAA, PCI-DSS, GDPR, etc. Regular pentests with subsequent reports help firms achieve compliance with the above by identifying vulnerabilities and providing evidence of remediation for audits.
Similarly, such compliance reports also help security analysts tailor their in-house testing procedures and remediation patches to prioritize vulnerabilities penalized by specific standards.
5. Build Trust with Customers
While the pentest report might not directly interact with your customers, a well-crafted rescan report and publicly verifiable certificate provide concrete proof of your company’s commitment to transparency and customer data safety.
Key Components of a Penetration Testing Report (VAPT Report)

1. Executive Summary:
The executive summary briefly summarizes the systems/applications tested, the pentest’s objectives, the timeline, and any limitations the pentesting experts encountered.
A. About the Pentester
This section briefly explains the security analyst and reviewer assigned to the penetration test, including their credentials, number of pentests performed, CVEs found, and achievements.
B. Overview
It provides a condensed overview of the identified vulnerabilities, highlighting the number, range of risk scores, severity, and resolution statistics, along with an assessment of the organization’s current risk posture.
Pro Tip: Since the summary deals primarily with C-suite executives, it should be short, crisp, drafted in layman’s language, and well-formatted.
2. Methodology and Scope:
This section of the vulnerability assessment and penetration testing report describes the various methodologies used, including tools, techniques, scan authentication, and scope of the assessment.
A. Tools and Techniques
Such details usually include a rundown of every paid and open-source tool used for the pentest. They also outline the techniques employed, such as web application scanning, network penetration testing, social engineering, etc.
B. Scope
The report defines the systems and applications included and excluded from the testing scope and the timeframe allocated for the pentest. It also mentions any limitations related to testing hours or data availability.
3. Findings and Vulnerabilities
This section categorizes and lists all the vulnerabilities identified with specific details like type, severity (e.g., critical, high, medium, low), CWE, risk scores such as CVSS, and CVE identifiers, if applicable.
Since the primary audience of this section is engineers and developers, it often includes technical jargon and references to facilitate better understanding and reduce fillers. Each individual vulnerability report includes the following:
A. Description:
This sub-section briefly explains the vulnerability, including how it works and how it can be exploited. This also includes detailing the severity of the impact and potential consequences, such as unauthorized access to data and user role manipulation.
B. Affected Components
This provides a comprehensive list of the affected components, i.e., the specific software, hardware, or configuration, such as the URL, user, or IP ports vulnerable to the identified weakness. It pinpoints the exact locations where the vulnerability exists.
C. Severity
This indicates the potential impact of the vulnerability on your system. It’s usually categorized as critical, high, medium, low, or informational, with ‘critical’ signifying the most severe impact.
On the other hand, ‘informational’ refers to a potential issue that usually doesn’t directly affect your security posture but is an industrial best practice.
D. Status
This often describes the vulnerability’s current state. Common statuses include unsolved, meaning it is unaddressed; solved, indicating it has been patched and vetted; or help wanted, indicating clarification is required from the pentesting team.
Some other statuses also include under review for vulnerabilities that have been patched but not vetted and accepted risk that reflects the customer’s decision not to address or resolve the reported issue or vulnerability.
E. Risk Score
This represents a numerical value assigned to the vulnerability based on a combination of factors like severity, exploitability, and potential business impact. Higher scores indicate a greater risk and require prioritization.
For example, CVSS or Common Vulnerability Scoring System is a popular standardized risk scoring model ranging from 0.0 (no severity) to 10.0 (critical severity).
F. CWE (Common Weakness Enumeration)
This assigns a unique identifier to the vulnerability based on its type and classification. CWE provides a standardized classification system for software weaknesses, allowing easy comparison and analysis across different reports and vendors.
G. Compliance Labels:
This section pinpoints any industry or regulatory standards the vulnerability may violate to help organizations understand their compliance posture and prioritize remediation efforts based on potential legal or financial ramifications.
H. Proof of Concept
It includes sanitized screenshots or video recordings for critical vulnerabilities, as applicable, to demonstrate the fatal nature of a risk discovered in an external or internal penetration test.
I. Steps to Reproduce
This part of the penetration testing report template provides a step-by-step guide on recreating the vulnerability to help developers better understand the flaws and test fixes in sandbox environments.
J. Suggested Fixes & Remediation:
As the name suggests, it offers specific remediation recommendations. These could include code-level changes, configuration updates, application of patches, or implementation of security controls tailored to the technology or system involved.
K. Additional Resources
This section includes links to external sources, such as vendor advisories, CVE (Common Vulnerabilities and Exposures) entries, detailed technical write-ups, or relevant research papers, to provide context and additional information for those who want to dig deeper.
5. Appendices:
Lastly, an appendix typically contains supplementary information crucial to understanding the report without cluttering the main body of the report. Some components include measurement scales, various statuses, risk scores, OWASP Top 10, SANS 25 & a list of any other test cases.
Here’s a simple penetration report preparation checklist to help you tick off all the essentials while preparing your report as a security analyst or vetting your vendor as a company.
What Makes Astra the Best VAPT Solution?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- The Astra Vulnerability Scanner Runs 8000+ tests to uncover every single vulnerability
- Vetted scans to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities
- Astra pentest detects business logic errors and payment gateway hacks
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Various Compliance Standards for Pentest & VAPT Reports
While most industry standards share common core elements in pentest reports, individual compliances and standards have specific nuances necessitated by their drafting legalese. The key differences in the penetration testing report formats for some common standards include:
| Standard | Key Reporting Elements |
|---|---|
| PCI-DSS | Detailed vulnerability analysis, Evidence of testing process, Recommendations for risk mitigation, PCI violation detected in each vulnerability |
| CREST | Executive summary, Detailed findings, Risk ratings, Remediation advice |
| CERT | Incident disclosure policy, Vulnerability assessment, Recommendations |
| FEDRAMP | Security requirements, Assessment results, Remediation plan |
| CHECK | Detailed test plan, Vulnerability findings, Remediation steps |
Best Practices to Write a Penetrating Testing Report Efficiently

1. Know Your Audience:
Tailor the report’s language and technical depth to your audience. For example, executives prefer a high-level overview of risks and remediation strategies, while technical remediation teams require detailed vulnerability descriptions.
2. Prioritize Vulnerabilities:
Don’t overwhelm your audience with a laundry list of vulnerabilities. Prioritize findings based on severity, exploitability, and potential impact. Use a risk assessment framework like CVSS to categorize vulnerabilities per their potential risk.
3. Leverage Consistent Structure and Formatting:
Maintain a consistent and logical structure that executives and engineers can follow throughout the pentest report template. Use clear headings, subheadings, and bullet points to improve readability.
Pro Tip: Reference any tools, frameworks, or external resources used during the penetration test as footnotes or in the appendix.
4. Include Visuals:
Use screenshots, tables, and diagrams to enhance understanding and highlight key findings. Add video-based walkthroughs for proof of concepts and especially challenging steps to recreation and remediation. Ensure visuals are well-labeled and easy to interpret.
5. Provide Actionable Recommendations:
Don’t just identify vulnerabilities but also offer actionable recommendations for remediation. This includes specific steps to mitigate risks tailored to individual assets and suggest resources for further action as required.
6. Proofread and Edit:
Ensure the report is free of grammatical errors and typos to avoid any scope of misinterpretations of critical security information. For example, a typo in a CVSS score of 9.5 to 8.5 can undermine the risk and prioritization of a critical CVE.
How Can Astra Pentest Help?
Astra is a leading SaaS company that specializes in delivering innovative penetration testing reporting solutions. Our VAPT techniques blend automation, AI, and manual expertise to run 9300+ tests to deliver penetration testing reports tailored to your needs.
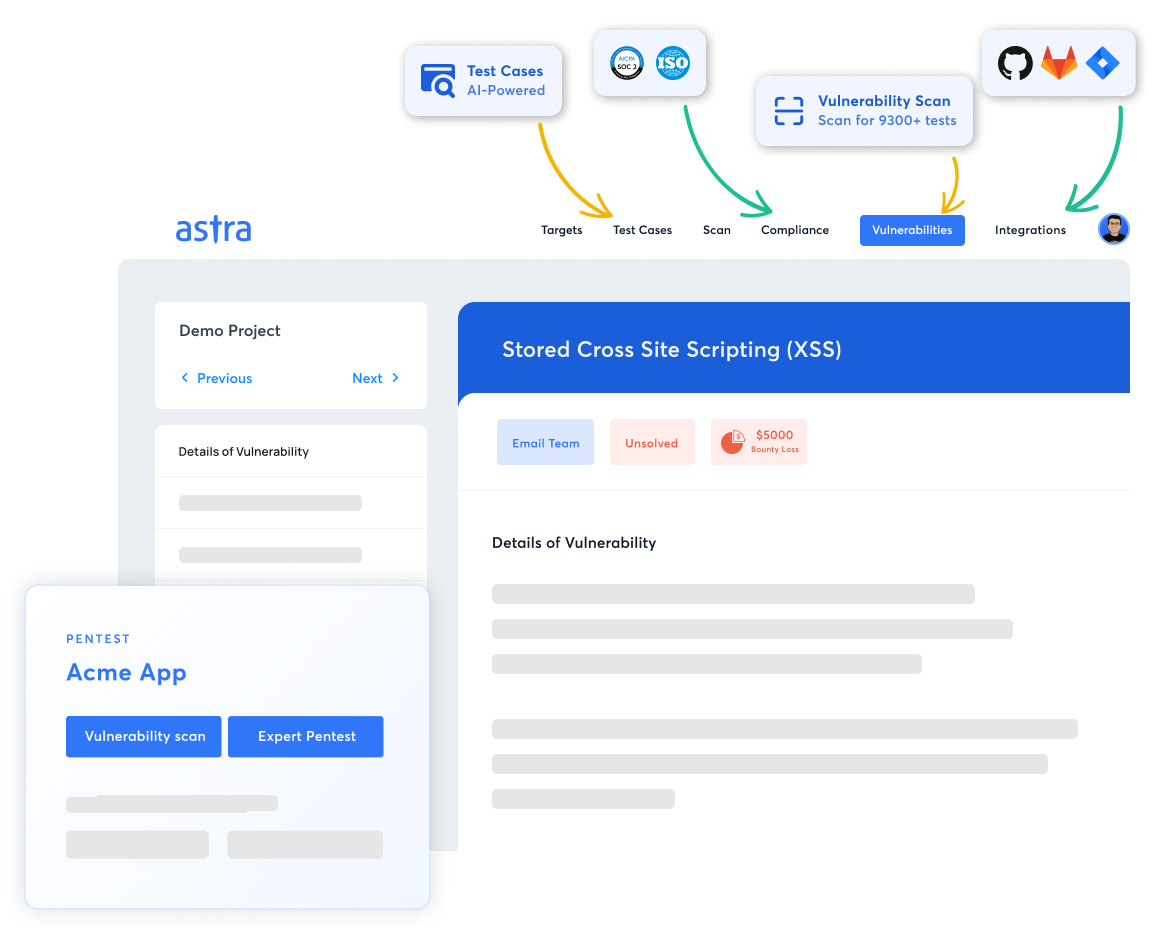
Moreover, our AI-powered test cases help our engineers run additional business logic test cases based on your asset’s digital infrastructure and existing tech stack to ensure complete safety.
Lastly, zero false positives, deep CI/CD integrations, and customizable reports guarantee a smooth experience while saving you millions of dollars proactively. We strive to make pentesting simple, effective, and hassle-free.

Final Thoughts
To conclude, these penetration testing reports are not just simple lists of vulnerabilities but defined plans for mitigating business risk for your data and assets.
They help identify weaknesses, provide actionable insights, facilitate compliance certification processes, and, most importantly, help establish trust with your stakeholders.
Simply put, well-drafted pentesting reports such as Astra’s act as the true north stars in cybersecurity.
FAQs
1. What do you expect from a penetration testing report as a security professional?
A penetration testing report should include an executive summary outlining issue impacts, comprehensive insights into evaluation methodologies and tools, detailed technical breakdowns of vulnerabilities, and actionable recommendations for mitigation.
2. How much does penetration testing cost?
The cost for penetration testing ranges between $349 and $1499 per scan for websites. For SaaS or web applications, it ranges between $700 and $4999 per scan, depending on your requirements.
3. What are the three 3 types of penetration test?
The three main types of penetration tests are:
Black box: No prior knowledge of the system, simulating an external attacker.
White box: Complete knowledge of the system, allowing for deeper testing.
Gray box: Partial knowledge, offering a balance between the two extremes.
This post is part of a series on penetration testing, you can also check out other articles below.
Chapter 1. What is Penetration Testing
Chapter 2. Different Types of Penetration Testing?
Chapter 3. Top 5 Penetration Testing Methodology to Follow in 2024
Chapter 4. Ten Best Penetration Testing Companies and Providers
Chapter 5. Best Penetration Testing Tools Pros Use – Top List
Chapter 6. A Super Easy Guide on Penetration Testing Compliance
Chapter 7. Average Penetration Testing Cost in 2024
Chapter 8. Penetration Testing Services – Top Rated
Chapter 9. Penetration Testing Report

















Easy to understand!! Nice Article!! Pen-test or penetration testing is a security process where a skilled cyber-security professional endeavor to locate and exploit vulnerabilities in a computer system.
Nice information around Penetration testing report and what things to mention in it during the Pentest.
The sample report that you have shared justifies the total process.
Thanks
Thank you for this article. Very nicely explained article with a easily understandable sample pentest pdf report.