A recently discovered unpatched vulnerability has rendered WordPress. the most popular CMS in the world in peril of user credential exposure. The vulnerability could allow hackers to compromise targeted admin passwords. What’s more perturbing is that it renders all versions of WordPress as vulnerable.
The wordpress vulnerability (CVE-2017-8295) had been brought to light by Dawid Golunski, a Polish security researcher who reported the vulnerability long back to the WordPress team in July 2016, but was subsequently ignored by the team. Till present, the vulnerability remains unfixed as even the latest version of WordPress 4.7.4 goes unpatched.
Hence users are advised to resort to the preventive measures discussed further in the article, for more details one may refer to the advisory published by the discoverer.
Dawid believes that “WordPress has a password reset feature that contains a vulnerability which might in some cases allow attackers to get hold of the password reset link without previous authentication. Such attack could lead to an attacker gaining unauthorized access to a victim’s WordPress account.”
What’s the vulnerability?
Dawid uncovers that this vulnerability arises because the password reset function uses untrusted data by default when creating an email that is supposed to be delivered to the owner’s account.
WordPress uses a variable SERVER_NAME to get the hostname of the server to build a From and Return-header of the email.
Some major servers allow the client to manipulate the value of the of SERVER_NAME variable using the hostname supplied. Since the variable SERVER_NAME can be modified it enables an attacker to choose it to be any arbitrary domain of their choice, this makes an attacker’s web server being set as the from the path in the password reset email.
This enables any attacker to send an email to the victim with malicious From/Return-path. Below is the example which shows an example request made by the attacker.
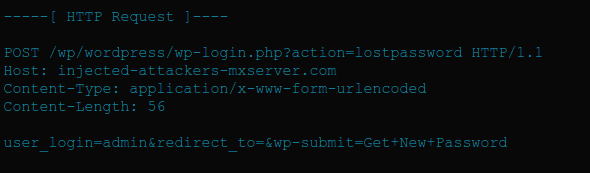
Golumski states that “Upon a successful exploitation, the attacker may be able to reset user’s password and gain unauthorized access to their WordPress account.”
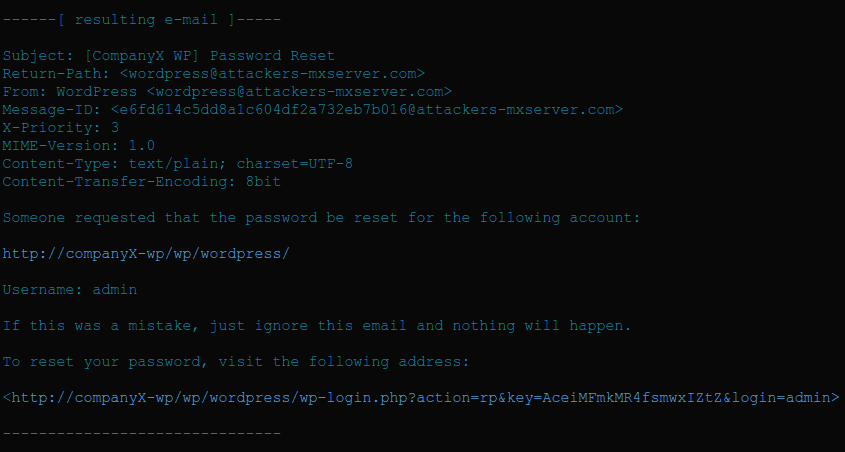
An example of the email sent to the victim shows how the attacker was able to inject malicious From/Return path.
Solution
As mentioned by the researcher Dawid, this issue has been reported to the WordPress team but there had been no fix for the same whatsoever. The temporary fix suggested is to enable UseCanonicalName to enforce static SERVER_NAME.
Besides, Astra advises you to take some time and go through this detailed guide on how to keep WordPress sites secure.
















