PHP Based Website Hacked – PHP Vulnerabilities & Fixing
PHP is the backbone of almost every popular CMS today. Thanks to its simplicity and license-free nature, PHP is the preferred choice for dynamic website development. However, due to poor coding standards, compromising PHP sites has become relatively easy. The internet is full of help threads where users complain about custom PHP website hacked or PHP website redirects hack. This has led to a lot of negative publicity for PHP itself which is nowhere to be blamed for this.
Therefore, if PHP is not to be blamed then what causes PHP website redirect hack? This article shall explain the security flaws that compromise a PHP website and how to prevent them.
Custom PHP Website Hacked: Examples
Most of the site owners focus only on the development part and not on the security aspects. Therefore, when websites, designed using PHP are hacked, site owners have nowhere to go as they paid the developers only for the development. Troubled users can be found looking for help on the online forums and reading articles like this one. Here are a few such examples.



Custom PHP Website Hacked: Symptoms
- Phishing pages appear on your PHP site which tries to trick users into entering sensitive info.
- Users click on certain links on your site and end up on another domain. Which is most likely caused due to a misconfiguration or PHP website redirect hack.
- Adblockers label and block certain elements of your site for cryptocurrency mining.
- Unknown PHP file managers appear on the site and the PHP site shows malicious adverts.
- PHP files have been modified with unknown code causing redirects or creating backlinks for fishy sites.
- Gibberish content appears on the custom PHP website which is likely to be caused by Japanese Keyword Hack or Pharma Hack etc.
- Warning messages of account suspension appear while using third-party hosting for custom PHP sites.
- The custom PHP site shows warning messages for being blacklisted by Google and other search engines for malware spam etc.
- phpMyAdmin shows some new and unknown database administrators.
- Emails sent from your PHP website’s domain have been labeled as spam.
- Unexpected error messages on the site and the PHP site becomes slow and unresponsive.
Custom PHP Website Hacked: 13 Reasons Why
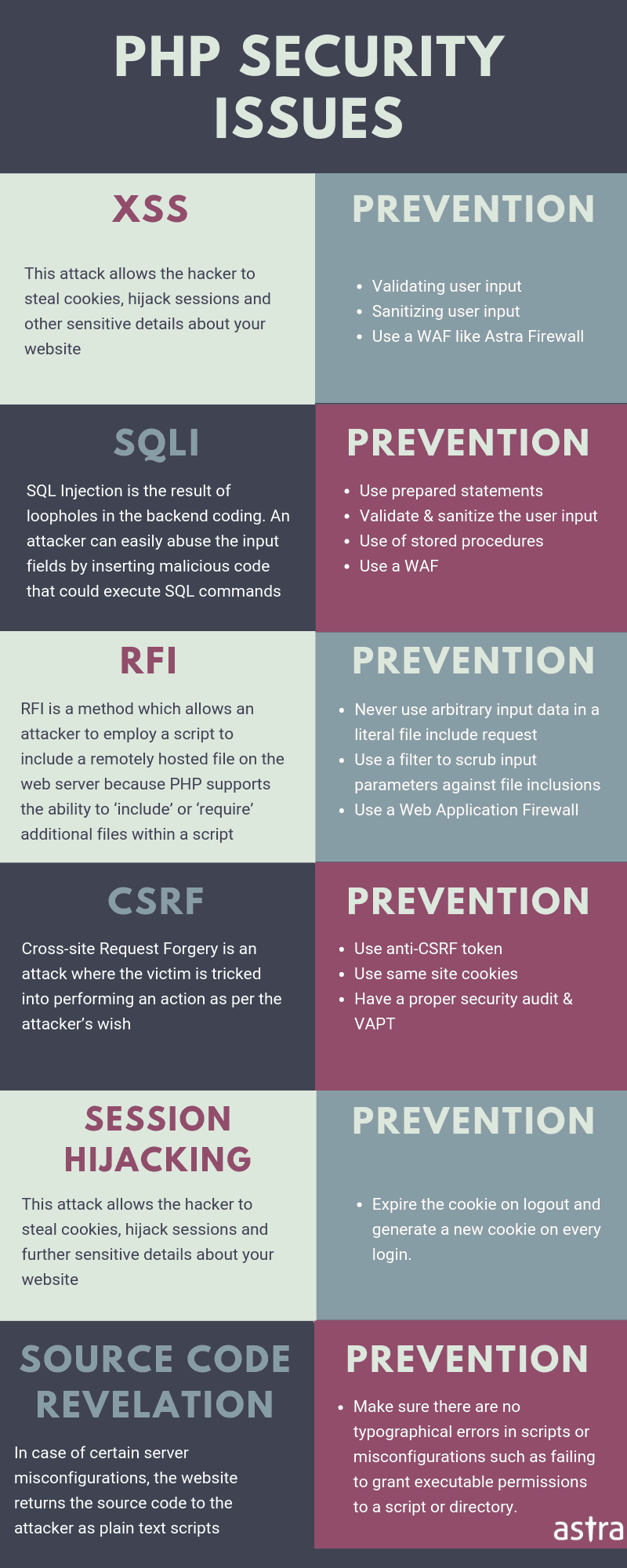
Server Mis-configuration
1. Weak File Permissions
File permission grants the privileges of modifying a particular PHP file to a certain type of user. Therefore, if the PHP file permissions are not set properly, it can allow attackers to inject your PHP files with malware spam, etc.
2. Default Passwords
Using weak or commonly used passwords is a common reason for the custom PHP website hacked. A Customized dictionary can be used to try all possible combinations of passwords. Once compromised, depending on the attack vector i.e. FTP brute force or cPanel brute force; the attacker can access the admin area of a custom PHP site. The attacker can then upload a PHP malware or backdoor.
Related article – How to remove the WordPress Backdoor?
3. Directory Indexing Enabled
Enabling directory indexing can allow attackers to read sensitive PHP files. This can give away sensitive information regarding the server to the attackers. The attackers can use this info to conduct cyber attacks on your custom PHP site.
4. Open Ports
Open ports may be causing a custom PHP website hacked. Moreover, open ports can be used by attackers to fingerprint backend services of your PHP site. By using that info the attacker can either compromise the backend services or the open ports themselves using exploits.
5. Poor Hosting
Generally, cheap PHP hosting comes with a heavy price for security. Poor hostings cut down on security operations to make the service cheaper. So, once the infections start spreading on such servers, it can compromise multiple sites including your PHP site, although, it was not directly targeted.
Vulnerable PHP Code
6. PHP SQL Injection
SQL injection in PHP is primarily caused due to lack of unsanitized user input. Due to poor coding standards, the unsanitized input reached directly to the database server and gets executed. Some main causes of SQLi in custom PHP pages are:
- Lack of filtering for space characters.
- Using the quotation marks to delimit strings.
- Passing unsanitized user input to the Database.
- Improper implementation of Unicode encoding.
- Inter-mixing of code with the data.
- Improper Type handling.
7. PHP Cross-Site Scripting
XSS is another commonly found cause of Custom PHP sites hacked after SQL injection. Both of these attacks are so prevalent on the web that they feature every year in the OWASP top 10. XSS is also caused due to a lack of user input sanitization. In PHP sites and in general, XSS attacks are mainly of three types:
- Stored XSS: This kind of XSS relies on the web admin to click on a particular link which then loads a malicious script to steal cookies.
- Reflected XSS: This is a pretty serious XSS and can be generally found in PHP sites with forums, discussion, etc. Malicious code from this type of XSS is stored on the server and gets executed every time a user visits that PHP page.
- DOM Based XSS: This kind of XSS may be either of the two given above. But, the detection of this type of XSS is pretty hard and may even escape after a code audit.
Sites vulnerable to XSS are generally targeted for PHP website redirect hack or to steal admin cookies.
8. PHP Cross-Site Request Forgery
CSRF attacks are intended to trick PHP site users to perform unwanted actions. If your custom PHP sites allow signups, a CSRF can allow people to delete random accounts or perform other actions. While the implications of actions are not directly visible to the attacker, CSRF can delete the users of PHP sites thereby reducing the site traffic.
9. PHP Local File Inclusion
File inclusion vulnerability occurs when an attacker can access files outside the root ‘www‘ directory. The main culprits for this vulnerability are the poorly coded scripts that take filenames as parameters. This vulnerability allows an attacker to read sensitive configuration and password files of your custom PHP site. The info obtained from these files can be used by the attackers to log in with admin rights thereby leading to a PHP website hacked.
Zero-Day Flaws in PHP
10. Buggy Plugins or Themes
Poorly coded plugins or themes in PHP are vulnerabilities sitting right on your server just waiting to be exploited. There have been instances when attackers have specifically targeted buggy plugins to conduct mass attacks on PHP sites. If you have your PHP website hacked, it is likely to be a poorly coded plugin or theme.
11. Compromised PHP Package
There is also a possibility that PHP libraries and packages are vulnerable. The same could happen with any other language. Recently, the PHP PEAR package manager was compromised by the attackers. The attackers had replaced the original one with their injected code which was downloaded by unsuspecting users. This package was then used by them on their sites for searching and downloading free libraries written in PHP programming language. Although such instances are rare the possibility of custom PHP website hacked due to zero-day flaws cannot be completely neglected.
Social Engineering Attacks
12. Phishing
Did the admin of your custom PHP site recently receive a mail from the Nigerian prince?. Attacks like this are designed to trick web admins into giving away sensitive info of the PHP website leading to a PHP website hacked. Therefore, to stay secure from phishing filter emails to the PHP site domain!
13. Tailgating
Tailgating is just another variant of phishing attacks. Under this attack, an attacker first compromises a low-level user account and then uses it to escalate privileges. Tailgating was seen in one of the case studies by our researchers and is commonly used to evade detection. The consequences of tailgating can vary from info stealing to a PHP site hacked.
Custom PHP Website Hacked: Securing the Site
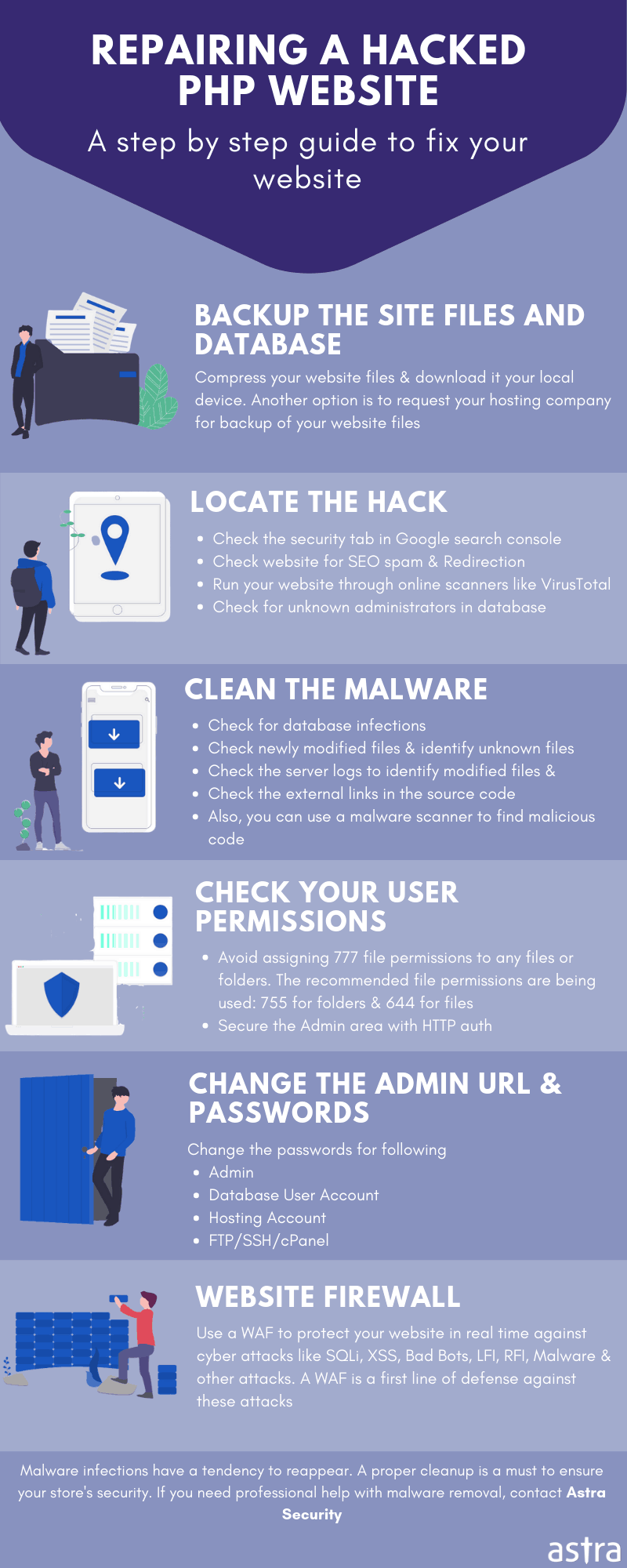
Set Correct Permissions
PHP has the following three functions to check file permissions:
- is_readable(): This function returns a boolean value of true if the user is allowed to read a PHP file.
- is_writable(): This function returns a boolean value of true if the user is allowed to write to a PHP file.
- is_executable(): This function returns a boolean value of true if the user is allowed to execute a PHP file.
Similarly, the chmod() function of PHP can be used to edit file permissions. Simply, input the name of a file along with the permission. i.e. “chmod($RandomFile, 0644);”. In the image given below is a complete list of file permission and what it does. Moreover, make sure to append ‘0’ before the file permission to specify the PHP interpreter that the input is octal.

Set A Secure Password
Ensure that your password to your custom PHP site is a secure one. Make it a good mix of numbers, alphabets, and symbols. Also, before setting a password it is a precautionary step to go through popular password dictionaries like Rockyou.txt and check if the password you are setting is not present there. In the case of Linux users, the Grep command can come in handy to search in such large files. Simply search, grep -i ‘*YourNewpass*’ rockyou.txt. Also, to avoid the hassle of making a new password, other online tools can also be used to get a secure, long, and random password.
Disable Directory Indexing
To disable indexing in a particular directory, append the following code to its .htaccess file(in case .htaccess is not present, create one):
Options -Indexes
Use Secure Hosting
Generally while looking for a hosting service, ensure that it provides a firewall or security solution as Astra Security does with its integrated hosting partners. Moreover, ensure subnetting to isolate your site from other sites running on the same server.
PHP Code Audit
Once, the custom PHP site has been created, building another one from scratch would not be economically feasible. Therefore, code auditing is the best way to catch vulnerabilities in the PHP website before the attackers do. Astra Security has a great community of hackers to audit and pentest the security of your site.

















A well written blog for PHP which in detail talks about the functions required and also explains the concept in depth for even the beginners to understand. The blog is rich in content and the detailed explanation makes it interesting.