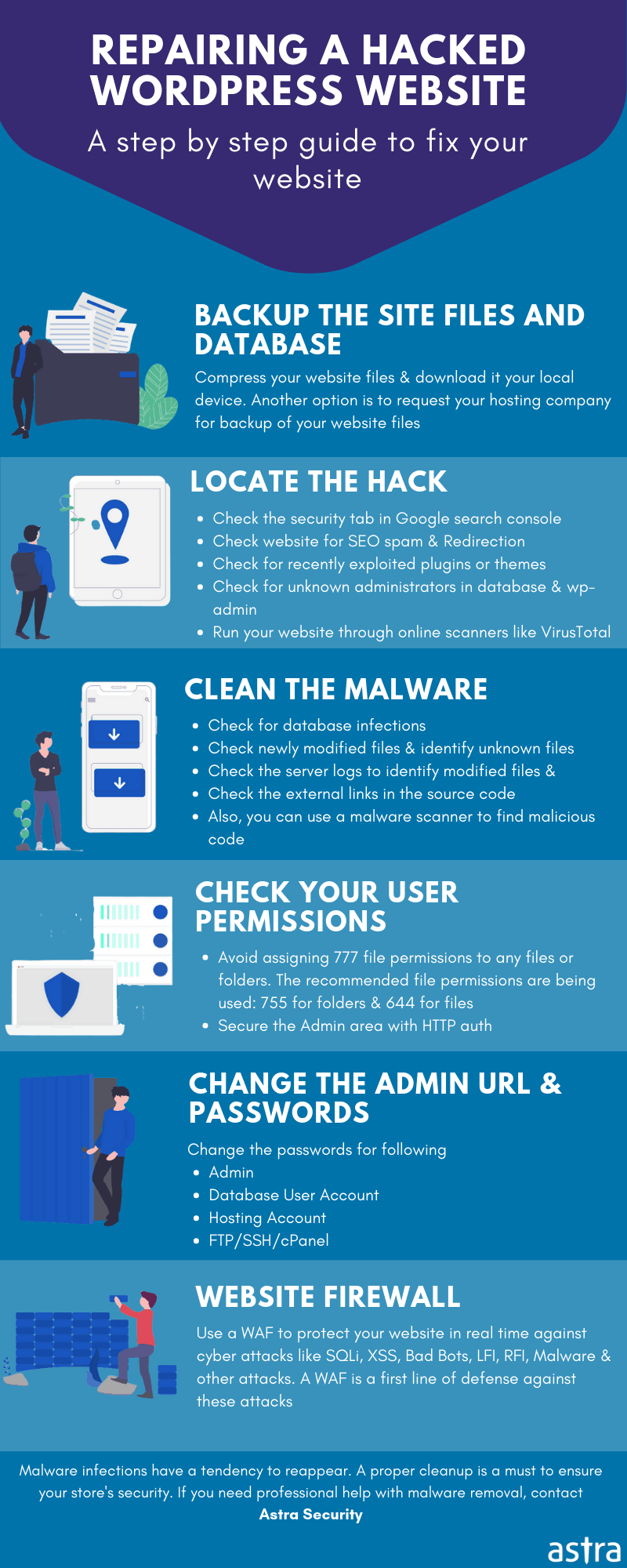
WordPress sites have always been targets for internet fraudsters owing to its large user base and a wide range of functionalities. Using vulnerable Plugins, not timely updating to the latest versions, not applying patches regularly, and carelessness in security measures are the major reasons for a large number of attacks on WordPress Sites.
Unfinished WordPress installations have rendered the world’s most popular CMS WordPress is vulnerable to PHP Code Injection attack with more than 7.2 million attacks in June 2017. The WordPress code injection campaign particularly peaked during May and June when attackers targeted WordPress installations which were recently installed, but not configured. This PHP code execution attack provides attacker admin access, thereby gaining full control of the website in no time.
Related Guide – Complete Guide to WordPress Security (Reduce the risk of Hacking by 90%)
Why WordPress?
WordPress hosts some of the world’s most famous websites like BBC America, TechCrunch, Sony Music etc. As a result, its popularity invites both the good and the bad. Just as the Windows OS is a primary target for malware and Android OS for mobile malware, WordPress (WP) CMS is one of the most sought-after platforms, holding about 59 percent of market share. The sheer quantity of WordPress-based sites makes them natural targets for spammers and cybercriminals who compromise legitimate looking WordPress sites to house their own malware for free.
Code Injection: How are WordPress Sites attacked?
Most WordPress users install the platform by either unzipping the archive into a directory on their hosting account or by using a one-click installer from a hosting provider. But this leaves the process incomplete until the user creates a configuration file. This becomes a major reason for WordPress site owners who fail to complete installation become vulnerable to attack.
To initiate the attack, the attacker would scan for the setup URL and identify WordPress instances where the configuration part of the installation has been left incomplete. This leaves the site open to outside handling, thus allowing external parties to access and complete the installation on user’s behalf.
To take over your WordPress site, the attacker would pick up the unconfigured site from where you left, launch a theme and insert a PHP code, or create and upload a custom plug-in. Once an attacker gains admin access, he/she can easily implement PHP Code execution and launch a series of malicious activities. As the admin, the attacker can now access all files, websites and even databases on the hosting server.
Check our blog on best security practices to secure your WordPress.
An obvious way to mitigate this flaw is to ensure your WordPress configuration during installation is complete. Moreover, now more than ever, it becomes imperative for website admins to scan their sites for any unfinished installations. Regular monitoring and auditing can also protect your site from such attacks in the future.