Social media is a validation of the term ‘global village’. Much like nodes in a distributed network, social network gives a validation to the content. The more shares it has the more likely people are to believe it. Websites, therefore, felt the need to keep up with the times. So what better platform to count the social relevance of content than Twitter. Back in 2015 Twitter used to provide a Tweet Button. Its primary goal was to count the number of times a content has been tweeted. However, Twitter announced in late 2015 that this feature would be deprecated. This decision was based on many factors. The clarification Twitter gave for its actions was:
- The button was introduced back in the days when the internet had few buttons. So it’s usage was getting more complicated to handle.
- The original API (count API) was never meant to be public. It was intended for Twitter’s web widgets.
- Twitter was migrating to newer technology at that time. So the old tweet button could be a security issue.
- Costs of maintaining the security and updates for it were not profitable.
So naturally, the web owners had to look for alternate options. Then came the New Share Counts service. This service could be used via API, Apps or plugins in case of WordPress etc. The ease of use for this service made users migrate to it. A simple signup and you are good to go!
The signup process was pretty simple. This is what helped it to establish a user base. To register, firstly visit newsharecounts.com. Enter your domain whose tweets you wish to count. See the image below:
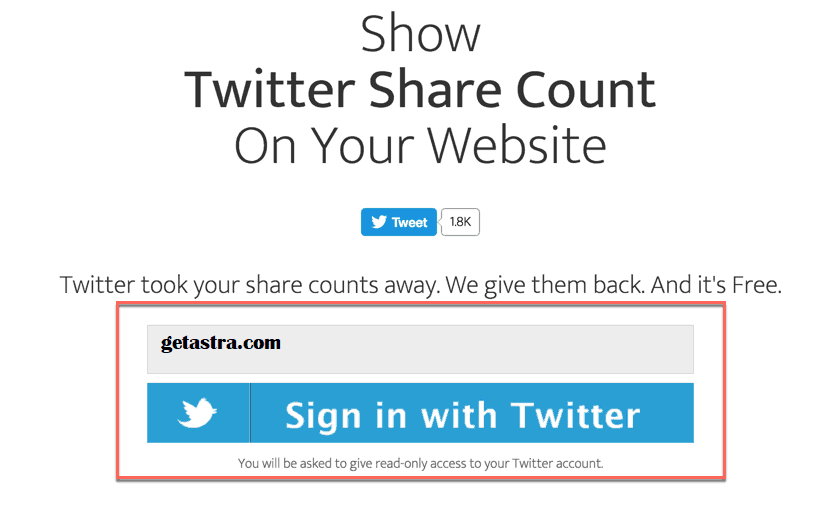
After signing up from this page all you needed was one more step. Just add the following code to the end of every page you wish to track.
<script type="text/javascript" src="//newsharecounts.s3-us-west-2.amazonaws.com/nsc.js"></script><script type="text/javascript">window.newShareCountsAuto="smart";</script>
This code loads a javascript from http://newsharecounts.s3-us-west-2.amazonaws.com/nsc.js on the page. The script was loaded from what looks like an Amazon web server of the company. So, it would then go on to track the tweets for the page.
What Went Wrong?
The issue grabbed attention when the service went defunct. WordPress forums reported the service dead. Even now if you visit http://newsharecounts.com the service is no longer available. The users on the forums suggested alternate options for the service. However, it raised an alarm among the security researchers. There was a sense of doubt that the service may have been removed because of malware. The service may be dead but the Amazon web server was still functional. The whole code snippet can be reviewed by merely visiting http://newsharecounts.s3-us-west-2.amazonaws.com/nsc.js. It was analyzed that the script had nothing to do with counting tweets. It was merely infecting innocent users. The users were redirected to spam campaign pages. So this script was used to serve spam to the users.
Facing some problem with your website? Drop us a message on the chat widget and we’d be happy to help you fix it. Secure my website now.
Code Analysis
The Amazon web server of newsharecounts.com serves a script that looks somewhat like this.
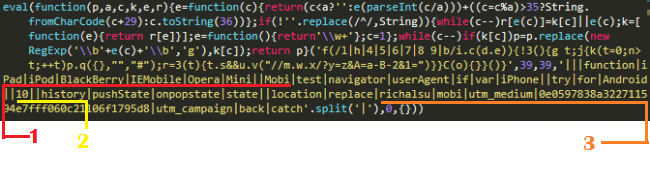
Clearly, some code obfuscation techniques have been implemented. We shall now break down the code step by step as to what it did. Once decoded the script would:
Code #1:
This piece of code checked the user agents of the visitors. It was then determined if a user was surfing on a mobile or Desktop. So mobile users were identified and precisely targeted. |iPad|iPod|BlackBerry|IEMobile|Opera|Mini||Mobi|test|navigator|userAgent|if|var|iPhone||try|for|Android This code here identifies Opera Mini, iPhone, Blackberry etc mobiles. However, it is noteworthy here that these mobile users will be infected only if they tap the Back button or try to navigate to the previous page. Mainly because of the presence of a malicious event handler.
Code#2:
Now once the users have been identified, they were targeted using the following code.
try|for|Android||10||history|pushState|onpopstate|state||location|replace|richalsu|mobi|utm_medium|0e0597838a322711594e7fff060c21106f1795d8|utm_campaign|back|catch These are the parameter values which goes into the obfuscated code.
Nicely packed between the try and catch statements this piece of code would first add 10 fake entries of the same page to the browser history. This was targeted at faking the page visits. Now when the page is loaded a malicious event handler gets at play. The event it is looking for is pressing the Back button. Once the back button was pressed it cause an Event to begin. The Event was redirecting visitors to a spam page.
Code#3:
Once the unsuspected user pressed the back button, comes the next step ‘The Redirect‘. Clear code obfuscation techniques have been used. The code("//m.w.x/?y=z&A=a-B-2&1=") can be decoded to a redirect URL. The redirect URL looks something like this: m.richalsu.mobi/?utm_medium=0e0597838a322711594e7fff060c21106f1795d8&utm_campaign=a-back-2&1=.
This URL then redirects the user to another and final Spam URL. Which would look something like this
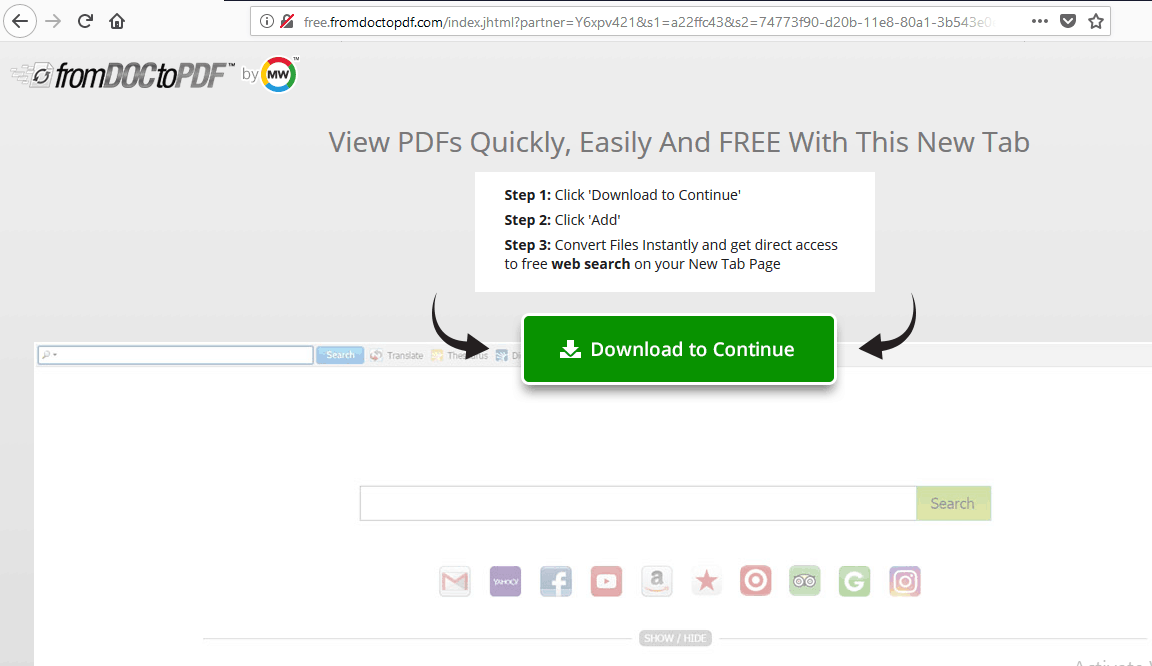
This is another spam page which asks unwary users to download a malware file. An audio file is played regarding the same. Pressing back button reloads the page because of the Event handler. This is a spam campaign targeting users visiting websites which used the infected tweets counter.
Lessons Learned
There were fair reasons why Twitter stopped counting the tweets and it was a lesson to learn. The bloggers and websites who wanted to measure their social presence have unexpectedly exposed their users to spam and malware. A source code search engine reveals that 1000+ websites are still serving this script to visitors. If your website has been infected with this redirect malware you should:
- Remove the infected script form your website.
- Look for other alternate options. Use WordPress help forums to find alternate options.
- Inspect third-party scripts and elements regularly.
- Manual inspection is not easy. You may be no expert in the security field. So hire the experts!
- Use a firewall or security solution. The one at Astra can detect such malicious third-party scripts and block them.
Facing some problem with your website? Drop us a message on the chat widget and we’d be happy to help you fix it. Secure my website now.
















Thank you for breaking down the twitter counter security hole here. Much appreciated.