Article Summary
The article provides a detailed definition and a step-by-step guide to web services pentest. Along with this the two types of web services, REST and SOAP are also explained at length. So keep reading to know more!
Web services are simply defined as software that supports communication between devices. This XML-based information can be exchanged between, systems, programs, messages, documents, applications, and more through internet or computer servers that are listening for web requests on a particular system, serving relevant documents. Web services are a type of API or Application Programming Interface.
Websites were generally given more prominence when it came to matters of security, making website penetration testing quite popular. However, web services that were once considered secondary attack vectors have now emerged as popular targets for attackers to exploit.
Safeguarding is made possible by carrying out regular web services pentest. Wondering what exactly a web services pentest is? Well, look no further. This article will talk about all web services pentest, the types of web services, the need for web services penetration testing, common vulnerabilities and threats to it, as well as the steps for the same. So let’s dive in!
What is A Web Services Pentest?
Pentesting Web services refer to the authorized hacking attempt to identify and exploit vulnerabilities within the infrastructure of a web service. This can provide a unique perspective into how hackers could exploit the vulnerabilities present and gain access to confidential data. The vulnerabilities found during a web services pentest can be remedied quickly to avoid such malicious activities. But before we explore this further, let us get a better understanding of the different types of web services there are.
Types Of Web Services
Web services are generally divided into two categories, REST (Representational State Transfer) and SOAP (Simple Object Access Protocol).
| S. No. | REST | SOAP |
|---|---|---|
| 1. | Representation State Transfer | Simple Object Access Protocol |
| 2. | REST is an architectural style for web services | SOAP is a protocol with specifications |
| 3. | It is only a RESTful service if it is stateless and cacheable | Requires a WSDL file that has the information on the web service |
| 4. | Uses uniform service locators like URI and URLs to access resources from the database | Uses service interface to reveal function and information of a web service to client |
1. REST Web Services
Defined by Roy Fielding in 2000, Representational State Transfer or REST is an architectural format followed by web services which are then known as RESTful web services. In order to be categorized as a RESTful web service, the request must be made by making use of HTTP methods. REST is mainly resource-oriented, unlike SOAP which will be explained in the next section.
REST web services can be built with both JSON and XML, with JSON (JavaScript Object Notation) being the more used format owing to its readability and web accessibility. The components of REST services can be split into two:
- Client Request
A client here refers to the person or program accessing a web service. A request by a client to access a service includes the following:
- URI (Uniform Resource Identifier): This includes both URL (Unique Resource Locator) and URN (Unique Resource Name). They help in the identification of a resource. Resources refer to specific information from a web service.
- Uniform Interface: These resources are then manipulated using the HTTP methods for reading (GET), creating (PUT), updates (POST), and deletion (DELETE) of web services.
- Self-description: This refers to additional information in the request added in by the client such as resource metadata to perform authentication of credentials.
- Server Response
Resources are stored on a server with specific URIs that make them easily identifiable. Once a request is put in, the server end makes a representation of the resource available to the client system. Here the important thing to notice is that the original resource isn’t sent over, rather a representation of it at a particular time point is. These responses are sent back in JSON or other formats like XML or HTML.
Also Read: API Penetration Testing: What You Need To Know
2. SOAP Web Services
Unlike REST which is essentially architectural guidelines for designing web services, SOAP or Simple Object Access Protocol refers to a certain set of protocols that define and restrict the XML format. It is important to note that SOAP and REST services aren’t comparable, rather they are different aspects of web services.
XML is used to transfer data between client and server through request and response while WDSL or Web Service Description Language is used to define the format and functionality of the web service. This includes the request and response structure, endpoint, and all operation definitions as well.
The established structure for SOAP web services includes:
- Envelope: Which is the initial root document that contains two parts, a header, and a body.
- Header: This includes the information that specifies the meta-information regarding which client the XML document is being sent to for authentication and authorization.
- Body: This is the actual XML content of the message.
Since REST web services can also be done in XML language the above SOAP web service protocol can be applied to it. However, the vice-versa is not applicable since SOAP is solely XML-based.
Also Read: 11 Best Penetration Testing Tools/Software of 2022 [Reviewed] | Top 6 Web Pentest Tools You Should Not Miss
Need Of Pentest for Web Services
The need for web services penetration testing stems from the vulnerabilities found in web services which can lead to a variety of threats and exploits. This section focuses on the common vulnerabilities and threats to web services and explains them in detail.
Common Vulnerabilities In Web Services
- Weak Authentication
Web services authentication is often extremely difficult to implement. This can lead to improper or weak authentication measures being enforced which can be easily exploited. This leads to authentication aspects like client/user identification and web service security in a system being heavily compromised.
- Lack of Encryption
Not securely encrypting the web services can lead to its exploitation. Encryption allows the scrambling of content thus safeguarding it from prying eyes. Improper encryption for services at rest or in transit increases the chances of sensitive data being leaked legibly.
- Insecure Endpoints
Web services often have exposed endpoints in object identifiers since developers often miss out on this. This can make them vulnerable to broken object-level authorization (BOLA). Object-level authorization controls the access users have to certain objects.
- Business Logic Error
These are errors that result from following a procedure that while legitimate produces negative results for the web services. It is difficult to test them for them since processes look normal and legitimate. Such undetected logic errors can lead to the web service being vulnerable.
Read more on Business Logic Errors
Common Threats To Web Services
- Injection Attacks
In this, an attack is staged by injecting malicious code into the application. The codes are commonly SQL or XSS. The former focuses on the server databases and stealing sensitive information from them while the latter targets clients by redirecting them to unprotected websites from where their data can be stolen. In the case of web services, these harmful codes can be used to manipulate or transfer malicious code into the API.
- DoS Attacks
A Denial of Service attack is accomplished by disrupting a web service by flooding it with ICMP (Internet Control Message Protocol) or SYN (synchronize) packets. When the system is overwhelmed with requests, information, and traffic it can’t handle, it eventually stops functioning and crashes.
- Broken Authentication
Weak or broken authentication which controls who can access certain objects leads to malicious attackers exploiting these vulnerabilities by completely surpassing them or obtaining control over them. With such an attack various aspects of a web service like passwords, API keys, and more may be accessed for ill gain.
- Data Exposure
Whenever data isn’t secured properly through stringent encryption at rest or in transit, it leaves confidential data unencrypted and exposed. This leads to data theft, manipulation, or deletion of highly sensitive client data or codes.
- Man-In-The-Middle Attack
In such an attack, the attacker is positioned between the user and a program while data transfer is taking place, thereby acquiring enough information to act or listen to either party while appearing legitimate and using the opportunity to intercept sensitive information from either client or system.
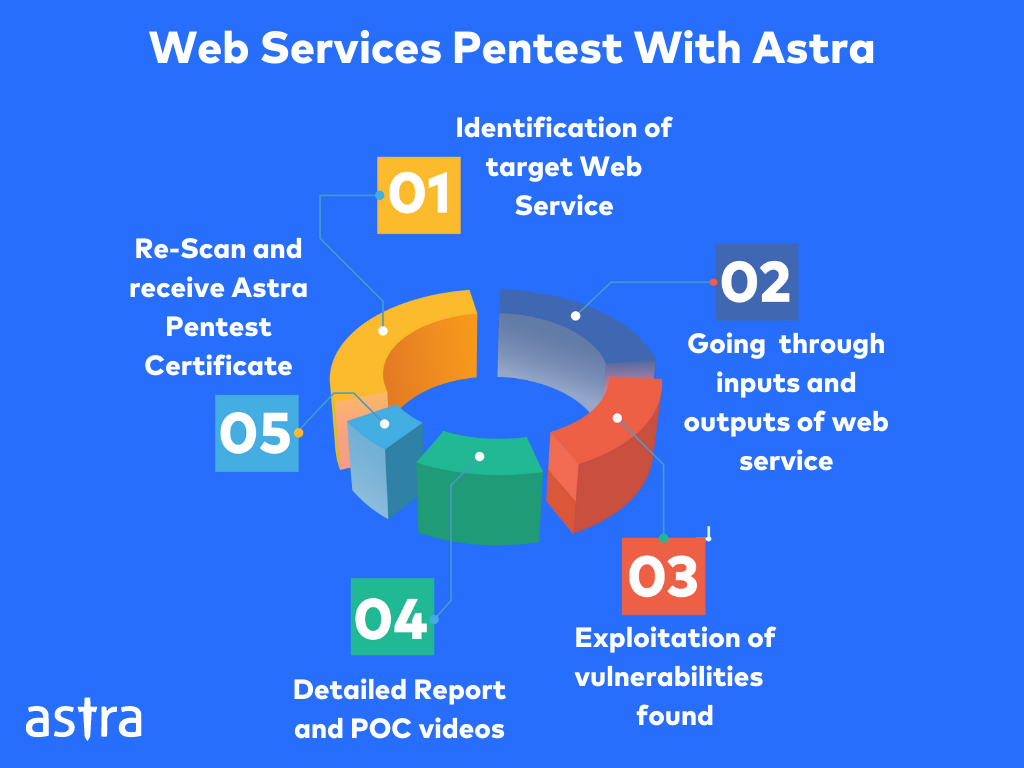
Step-By-Step Pentest For Web Services
1. Web Service Documentation
Going through the documentation of the target web service can help identify endpoints and parameters used to request a web service. Identifying these areas can also help understand the working of the API and its possible vulnerabilities.
2. Inputs And Outputs Of Web Service
By identifying the inputs and outputs of a web service you can determine the vulnerabilities within them as well. The most common inputs and outputs in a web service are the following:
- Web Service Requests refer to the communication from the client side to receive a response from a program or system to access a resource.
- URI parameters include both URNs and URLs which are essentially the address of the resource on the web.
- Headers in SOAP or RESTful web services have crucial meta-information regarding where the data is sent from and who/what it is received by.
- Web Responses are the HTTP replies from the server side to the requests made by clients. They vary depending on the client’s request.
- Authentication is the mechanism that helps identify the user and check their authorization for accessing a web service. It can be a password, token, or certificate.
- Cookies are small amounts of data from websites you visit on computers or mobiles. These allow the websites to recognize the user to shift to their preferred settings and collect data on browsing activities for targeted ads.
- Web service keys are specific codes that allow access to certain features on a website and protect them from being accessed by the general public.
These are the areas where there is a high chance of vulnerabilities to be found.
3. Identify and Exploit Vulnerabilities
Determine the vulnerabilities in the above aspects of a web service using a comprehensive vulnerability scanner. Once these vulnerabilities have been identified they can be exploited through various means:
- Fuzzing: This is a method of exploitation where random data is put into the web service API till a response like some information or an error message is received indicating that the random data has been processed by the API.
- Test For Injection Attacks: These are mostly SQL injection attacks in which malicious code is injected into the vulnerable part of a database through the website. Since every search field acts as a gateway to the database if a harmful code is put in and processed it could lead to access to sensitive data on the database.
- Parameter Manipulation: Parameters are set using HTTP methods which help read. Update, create and delete web services. To test for vulnerabilities with them, send a request that requires authentication. Once the request is processed, if it shows a “200 OK” message without authentication, it is indicative of a vulnerability.
4. Report Of Findings
Once all the vulnerabilities found are exploited to assess the level of damage they could produce, a detailed report is constructed with all the details mentioned in it. This includes everything from the scope of the pentest to the list of vulnerabilities found.
These vulnerabilities are explained in detail with their CVSS risk level and possible remediation measures to be taken to fix the vulnerability. Doing so can help safeguard the web services from any potential attack and exploitation of web service loopholes.
5. Re-Scan
Once the vulnerabilities mentioned in the detailed report are fixed with the help of POC videos and collaborative efforts of the pentesting team and the development team, ensure that a re-scan is done. This allows the identification of any further vulnerabilities with the patches placed. Once this is done the web service becomes eligible to receive a pentest certificate.
Related Read: API Security Testing
Choose Astra For Web Services Pentest
Astra’s Pentest Suite is the ideal solution for all your web services pentest requirements. Here are the features that make Astra’s Pentest the perfect penetration testing tool out there:
- Comprehensive Vulnerability Scanning: Astra’s Pentest provides a comprehensive vulnerability scanner capable of detecting vulnerabilities based on intel from hacks and CVEs, OWASP 10, and SANS 25.
- Zero False Positives: The provision of both manual and automated web services pentest ensures zero false positives.
- Detection Of Business Logic Errors: The tool can also test for business logic errors within your web service that could be making it dysfunctional.
- Quick Web Service Penetration Testing: The test is completed within a short span of 4-5 days but may vary slightly based on the scope of the test.
- CI/CD Integration: Provides opportunities for integrating web services pentest for projects in the CI/CD pipeline thus promoting the shift from DevOps to DevSecOps.
- Detailed Report: Upon the completion of the web services pentest, a detailed report explaining the vulnerabilities found, their CVSS risk level, and remediation steps are all mentioned in the report.
- Re-Scanning: Once the vulnerabilities mentioned in the report are fixed with the appropriate patches, a re-scanning feature is provided to ensure that there are no further vulnerabilities.
- Verifiable Certificate: Clients who successfully finish a web services pentest with Astra’s Pentest and do a re-scan upon fixing vulnerabilities are given a publicly verifiable Astra Pentest Certificate that is very beneficial to organizations.
- 24*7 Customer Support: At Astra, customer service is the number one priority with quick query clearance and additional support through POV videos to help fix vulnerabilities, Astra’s pentesting team is always available for the customer.
- Intuitive Dashboard: Astra’s Pentest tool has an easy-to-navigate, intuitive interface which makes it appealing to clients. Once the pentest begins, the vulnerabilities found till the completion are routinely updated and visible on the dashboard. It also offers a comment feature under each one for easy support. Additionally, members of the development team can be added in to fix vulnerabilities with the aid of the pentesters.
Conclusion
This article has highlighted various aspects of web services including the types of web services available, common vulnerabilities, and threats faced by web services. Along with this, a detailed analysis of what pentesting of web services are, and the steps for the same have also been mentioned. Opting for Astra’s Pentest Suite for all your penetration testing needs can make the process more streamlined and speedy owing to the variety of features it possesses.
FAQs
1. What is the difference between an API and a web service?
An API is a software intermediary that allows interaction between two applications while a web service refers to a set of guidelines and protocols used to exchange information between them. All web services are a type of API, however, all APIs are not a type of web service.
2. What are the common vulnerabilities in a web service?
The most common vulnerabilities in a web service include weak authentication, lack of proper data encryption, insecure endpoints, and business logic errors.
3. What is the importance of a web services pentest?
Web services pentest is important to identify and exploit any vulnerabilities within a web service to understand their severity level and fix them before an actual attack takes place.
















