API (Application Programming Interface) has been around for a very long time. Attributing to its wide usage, it became an easy vector for hackers. The vulnerabilities of API can lead to security failure, data breach, unauthenticated access, and so on. Further, a vulnerable API can cost a company millions of dollars if it goes unchecked. But you already know that for you’re here looking for API security testing pricing.
As you can see in the following bar graph, the number of vulnerabilities has constantly been increasing over the years. Imperva calculates a growth of 18.9% in the number of API vulnerabilities since 2018.

For a business, the need for an API Security Testing is getting direr with every passing day.
Why API Security Testing is necessary?
Besides the rising API vulnerabilities, the security of sensitive information handled by API is another big reason to get its security tested.
The following high-profile API data breaches show how catastrophic a vulnerable API can get:
- VENMO: Venmo’s API breach, allowed scraping of 200 million transaction details which left people stunned.
- Federation of Industries of the State of Sao Paulo: In 2018, FIESP (Brazil’s industrial body), exposed more than millions of data points.
- Airtel API: The Airtel API mishap risked the information of more than 325 million users, whose personal details could be extracted just by using their mobile numbers.
Also Read: API Penetration Testing: What You Need To Know
API Vulnerabilities
Further, security issues and Vulnerabilities in APIs typically fall into a few distinct categories. Which are:
1. Access controls
- Authorization: It involves proving that you are who you say are
- Authentication: It involves granting access to resources based on your identity
Access control schemes tend to follow a pattern. A client makes a request to something that requires authentication, the server processes authorization/authentication request and checks for things like:
- If the account exists
- Whether the requested resource is within access scope of the client
- If any previous cookies or tokens were used in the request, etc.
In case, the attempt is successful, the server returns a token, session id, or other identifiers to mark the session. Further authenticated requests will follow a similar pattern throughout the session.
2. Input Validation
It is a very important attack vector to consider when hunting for bugs. It is crucial to note that input is anything that server takes in, form the user, 3rd party apps, and other internal mechanisms. Common places to test in an API for input attack vectors:
- Within the requested header
- Parameters within the URL
- Parameters within the request
- File uploads(PUT/DELETE requests)
- Different request methods
3. Rate limiting
APIs are built for applications that typically expect a high load and a large number of arbitrary requests. This aspect can be abused to very quickly enumerate the endpoint in ways that are unintentional. Common ways to test Rate Limiting: It makes requests in varying states of authentication
- Pretending to be an unauthenticated user
- As a developer
- As a bot
- With a deactivated account
- With bogus credentials
An API with improperly implemented rate limiting can be used to make an abnormal amount of requests to enumerate the application and potentially cause other issues.
4. Restricting HTTP methods
APIs are built to support a number of HTTP methods. Determining what the application expects and what the application supports are very important when testing the API. Sometimes HTTP methods can lead a user to use PUT, POST, DELETE, etc; which are not generally allowed to be used. Even if these are not included in the application logic, if an application is lazy with this and has no logic to parse, weird things can happen.
5. XSS Attack
XSS stands for Cross-site scripting. This attack works when malicious code is injected into a website. These codes can make the user do anything varying from unauthorized access to data breaches. Its behavior will entirely depend on the intent of the attacker.
6. SQL Injection
In this vulnerability, instead of entering valid data, a user enters a SQL query that can change the behavior of your application.
What areas does API Security Testing cover?
Testing the authentication of an application to check how well the application is secured from unauthorized users is called API Security testing. These are some common areas that go into complete API security testing:
- Network security
- Client-side application security
- Server-side application security
- System software security
API Security Testing Pricing and Provider
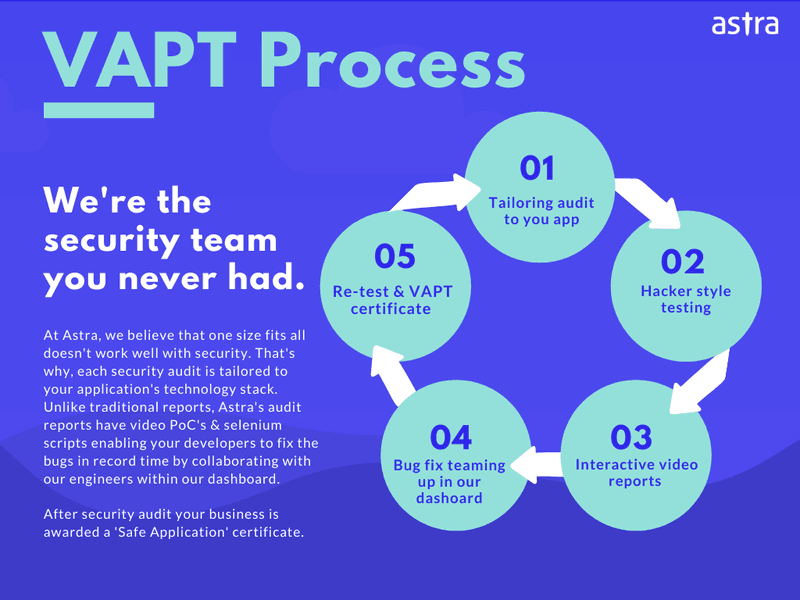
Choosing the right API security testing provider that detects all hidden vulnerabilities in your API is essential to having a secure website. Astra Security experts review your website corner to corner to uncover all vulnerable APIs under our VAPT (Vulnerability Assessment and Penetration Testing) plan.
It is one of the best VAPT service provider. It does not only tests your website for possible vulnerabilities but it also provides additional facilities.
Some of the features of ASTRA Security are:
- Vulnerability Assessment and Penetration Testing
- Static and Dynamic code analysis
- Network devises Configuration
- Payment Manipulation Testing
- Server Infrastructure Testing & DevOps
- Business Logic Testing
- Patch up Vulnerabilities
- Keep in the loop with an intuitive dashboard
- Test for known CVEs
Also Read: Penetration Testing Quote | Top 5 Software Security Testing Tools [2022 Reviewed]
API security testing pricing lies somewhere between $500 to $6000 per scan on the basis of scope and complexity. However, the Astra VAPT service comes in different plans – Scanner, Pentest, & Enterprise and starts only at $199.
You can also get a security audit with the Advanced & Business plan.
For more details, visit here: Plans & Pricing If you have further questions regarding API Security Testing Pricing, click on chat widget on your right-hand side and start a conversation with a security expert.
FAQs
What is the timeline for API Security testing?
API security testing ideally takes 4 to 5 days. You start seeing the vulnerabilities from the 2nd day on your dashboard. The timeline may differ a little depending upon the scope of the test.
How much does API security testing cost?
The cost of API testing is between $349 and $1499 per scan depending on the number of scans and the scope of the pentest.
Why choose Astra for Security Testing?
1250+ tests, adherence to global security standards, intuitive dashboard with dynamic visualization of vulnerabilities and their severity, security audit with simultaneous remediation assistance, multiple rescans, these are the features that give Astra an edge over all competitors.
Do I also get rescans after a vulnerability is fixed?
Yes, you get 2-3 rescans depending on the plan you are on. You can use the rescans within a period of 30 days from initial scan completion even after a vulnerability is fixed.
















