The process of protecting web API from attacks and ensuring only authorized access takes place is called API security. In the past six months attacks targeting APIs have increased by 400%. This has resulted in API security becoming a C-level discussion in many companies.
With such a drastic increase in API attacks, it is wise to strengthen your API security with the latest security measures in town. This article provides you with an API security checklist with all the latest list of top security measures to implement to truly safeguard your business’s APIs.
What is an API Security Checklist?
An API security checklist is a set of best practices and critical measures that heighten the security of your API assets and provide protection against any cyber threats. If APIs aren’t secure it can affect the communication and data transmission between systems.
Having and implementing an API security checklist allows you to
- Protect sensitive data transmitted API
- Enhance compliance and reliability in services
- Reduce vulnerabilities in API assets
- Preventing any disruption in business operations
If you are a business owner, security professional, part of a developing team, or an IT administrator, having and implementing an API security checklist is a must. API security checklist allows you to keep track of the security measures applied to your APIs.
Updated API Security Checklist for 2024
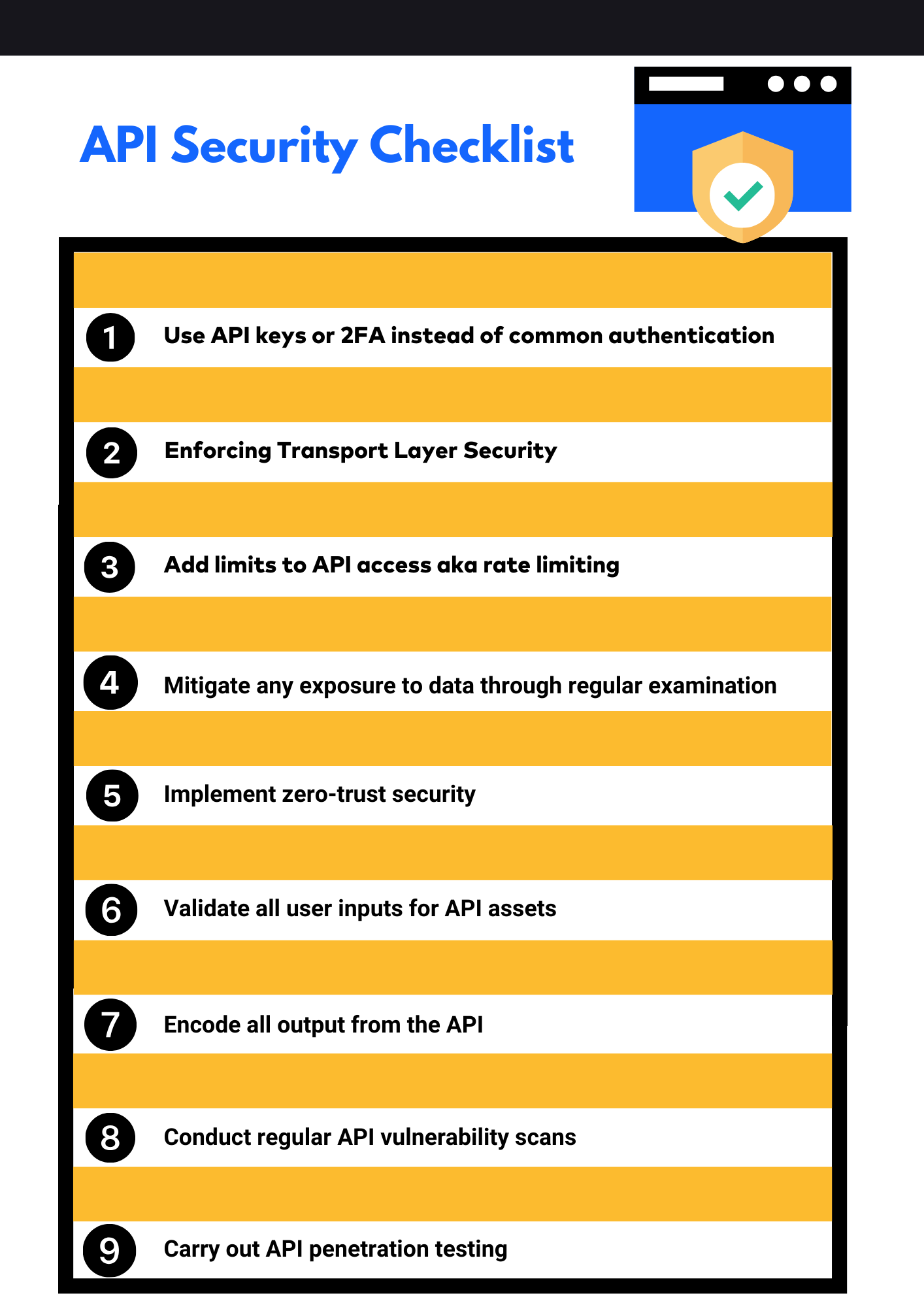
1. Use API keys or 2FA instead of common authentication
Number #1 in this API security testing checklist is important to avoid basic measures of authentication such as passwords as they offer limited or outdated security. Instead, employing two-factor authentication (2FA) the user trying to access the API needs to provide identity verification in two separate ways, usually a basic password and an OTP or even biometrics.
Another method of authentication that can be used is API keys. API keys are unique codes provided to authorize access to APIs. They essentially act as credentials that allow secure interactions with the API.
2. Enforcing Transport Layer Security
Implement TLS to encrypt data in transit. Transport layer security prevents unauthorized users from being able to hijack or modify the messages in transmission. It does this by protecting your APIs from a large number of vulnerabilities such as man-in-the-middle attacks, data tampering, and brute-force attacks.
TLS ensures that the message transmitted only reaches the intended party and cannot be tampered with in any way. An API asset without TLS is highly insecure and results in data exposure.
3. Add limits to API access aka rate limiting
Limiting access to API restricts the number of users that can access it. This is done since providing unlimited access can lead to a host of exploit attempts by malicious attackers. Limiting API access helps protect it from DDoS, and brute force attacks and also from it getting overloaded and crashing.
API rate limiting essentially means using certain measures to curb traffic directed to an API. These measures usually limit or restrict API access based on:
- Number of API access requests that can be sent over a period of time.
- The number of requests that your API can process in a certain period of time.
4. Mitigate any exposure to data
Data exposure is a vulnerability mentioned in the OWASP top vulnerabilities for APIs. This means the API would provide information outside the scope of the user query. A common scenario of data exposure is leaving login credentials in the URL string.
Such information can expose your systems to hackers who are equipped with more information and can find vulnerabilities faster for exploitation. To prevent such scenarios ensure that API elements such as error pages, transmitted data, data at rest, and URL strings are examined regularly.
5. Implement zero-trust security
Implementing a zero-trust model of security shifts your API security paradigm from placing a certain amount of trust to entirely eliminating the concept of trust in API governance. This means that no user, external or internal is trusted unless they pass the authentication and authorization measures.
Since each user is a potential threat, they and their activity are constantly monitored for malicious activity even after API verification. This approach to security means that even the chances of insider threats are significantly reduced.
6. Validate all user inputs for API
Treat user inputs as potential pathways for attacks to place. Hackers can use this to gain unauthorized and unauthenticated access to your API operations and the data within. It is therefore vital to validate all input regardless of the user privileges of the users.
Ideally, an invalid user input submission should trigger an error response and not be processed by the API for data retrieval. At the same time, a valid input will meet all the developer criteria to be able to access the API functionalities. Also, limit the fields to a bare minimum without scaling back on user experience.
7. Encode all output from the API
Ensure your API returns the right resources by placing some API output headers. This allows the API resources to be returned securely. These are basically descriptive metadata for your API assets that provide information on content type, access control, and protective policies.
Encoding API output helps prevent cross-site scripting attacks and controls access to the API resources for users. It is important to restrict sensitive information that can returned as well, such as user IDs or passwords. It is also important to make sure that the API returns the proper status codes for each operation.
8. Conduct regular API vulnerability scans
Another important part of this API audit checklist is conducting API vulnerability scans that are quick and can be carried out on a daily basis. The scan essentially analyzes your API against the most common vulnerabilities from a large database to match and identify any potential threat. Common vulnerability lists include CVEs, SANS Top 25, and OWASP Top 10.
Astra vulnerability scanner does 8000+ tests based on NIST, SANS Top 25, and OWASP Top 10 vulnerabilities to detect any flaws within your API assets that need fixing. API vulnerability scans are more pocket-friendly.
9. Carry out API penetration testing
Once you’ve implemented and carried out the rest of the items on the API security testing checklist, it is wise to go with an API penetration test to thoroughly assess your API security from a hacker’s perspective.
API penetration tests differ from vulnerability scans in that they not only involve the detection of vulnerabilities within an API but also go a step further and exploit the vulnerabilities. This exploitation allows you to gain a deeper understanding of how the vulnerabilities present in your API can severely impact your business operations, data & API security.
How Can Astra Security Help?
Astra Security is a vulnerability assessment and penetration testing company that provides API penetration tests as well as security testing for assets such as web & mobile applications, cloud infrastructures, and networks.
Our VAPT offerings help with:
- Detection and remediation of vulnerabilities and security gaps of varying criticality in the APIs.
- Maintenance of compliance with regulatory requirements like HIPAA, SOC2, PCI-DSS, ISO 27001, and GDPR.
- Shifting from DevOps to DevSecOps giving due priority to security testing applications in SDLC.
- Varying style reports ( customizable for developers and administrators) with detailed vulnerability information as well as mitigation measures.
Astra Pentest
Astra Security provides both manual and automated penetration testing for assets.
Additionally, for penetration testing, these vulnerabilities are exploited manually by Astra’s experienced pentesters or through automated pentesting. Brute forcing, fuzzing, and injections are some of the tests carried out on the vulnerability to try further access.
Astra Vulnerability Scanner
Automated vulnerability scans by Astra Vulnerability Scanner are further available in three different categories.
- Lightening: Super quick scan for vulnerabilities that takes around 9-10 minutes.
- Emerging: Targeted scans that check for the emerging or latest vulnerabilities mentioned in the world of cyber security.
- Full Scans: Complete in-depth automated scans that scan for well-known vulnerabilities, CVEs, OWASP Top 10, SANS Top 25, and newer ones from bug bounty reports.
Bottom Line
This API security checklist exhaustively covers a wide range of critical API security measures to protect your APIs. However, it is critical to understand that the checklist always has a scope for improvement and additions keeping in mind the ever-evolving nature of cyber attacks and attack techniques.
The role of API vulnerability scans and API pentest therefore cannot be understated. For all the measures implemented, these two measures can help you detect the effectiveness of your API security solutions and patch them in a timely manner if required. At Astra Security, expert pentesters provide API security testing that covers a wide range of vulnerabilities and attack scenarios that can affect your API leaving no stone unturned.
FAQs
Why is input validation crucial in API security?
You can prevent common API vulnerabilities such as SQL injections and XSS attacks through verification and sanitization of data received by your API endpoints. Proper validation of input ensures that only safe data is processed, reducing the chances of exploitation. the
How does rate limiting contribute to API security?
Rate limiting is a crucial part of an API security checklist since it restricts the number of API requests per time period. This prevents DDoS attacks and excessive resource usage. It mitigates the chances of brute force attacks and protects the API, ensuring its availability.
What role does encryption play in API security?
Using encryption measures such as TLS and SSL prevents modification of data. This safeguards its confidentiality and integrity during client and server data transmission. It does this by converting the APIs into unreadable text which can only be decoded with the right decryption key.














