Mobile app security refers to the measures, protocols, and practices implemented to protect a mobile application, its data, and its users from unauthorized access, data breaches, vulnerabilities, and cyberattacks. This includes implementing encryption, authentication, access controls, secure coding practices, and regular security assessments to mitigate specific threats and risks to the mobile app and its ecosystem.
Conversely, an API, or Application Programming Interface, is a set of rules and protocols that allows different software applications to communicate and interact with each other. It defines the methods and data formats that applications can use to request and exchange information, enabling seamless integration and functionality between diverse systems allowing the app to access and transmit data securely.
Common cases may include social media plugins, payment gateways, and location and map-based attachments. As such, ensuring mobile app API security is crucial for secure and effective communication.
Action Points
- Mobile app API security involves protecting the APIs through API keys and OAuth tokens, access control, and encryption of data transmitted.
- It is crucial to prevent data breaches, financial losses, and legal consequences.
- Industry standards like OWASP, GDPR, NIST, and HIPAA help enforce strict API security measures.
- Protect a mobile app API through robust authentication, encryption, input validation, security headers, versioning, monitoring, testing, and careful error handling.
What Is Mobile App API Security?
Mobile app API security refers to the measures and protocols put in place to protect the Application Programming Interfaces (APIs) used by mobile applications to interact with servers, databases, and other external resources. APIs act as bridges, allowing apps to send and receive data, perform transactions, and access various functionalities from remote servers.
It involves employing authentication methods like API keys or OAuth tokens, enforcing access controls to ensure that only authorized users and apps can access specific API endpoints, and implementing encryption for data transmitted between the app and the API server.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Why Is Mobile App API Security Important?
1. Data Loss:
Mobile apps frequently handle sensitive data, including personal information, financial details, health records, and location data. Such personal information is highly valuable and, if compromised, can lead to devastating impacts.
Improper API security can lead to data breaches and unauthorized access, as without proper validation and authorization checks, attackers can gain unauthorized access to sensitive data through the API endpoint, which allows them to retrieve, modify, or exfiltrate confidential information.
Conversely, poorly managed API Keys, lack of rate limiting, and data sanitization give hackers a chance to manipulate, slow response times, and disrupt daily services, through:
- Injection attacks (e.g., SQL injection)
- Broken authentication, and
- Denial-of-Service (DoS) attacks
2. Financial Loss:
When users lose trust in an app due to a security incident, they are likely to stop using it, leading to a reduced traffic and interaction rate. This will lead to
- Lower ad revenue from Google ad placements,
- Reduced in-app purchases,
- Diminished opportunities for monetization
- A drop in word-of-mouth recommendations
3. Compliance Considerations:
The regulatory landscape governing data protection is both complex and unforgiving. Several industry frameworks such as those listed under impose stringent mandates including mobile app API security with hefty fees and legal claims to ensure the safety of user data across industries and continents. Examples include:
A. OWASP API Security Top Ten
The OWASP API Security Top Ten is a list of the most critical security concerns a company faces when developing and deploying APIs. Besides outlining the problem, the above also suggests ways to mitigate the vulnerabilities identified.
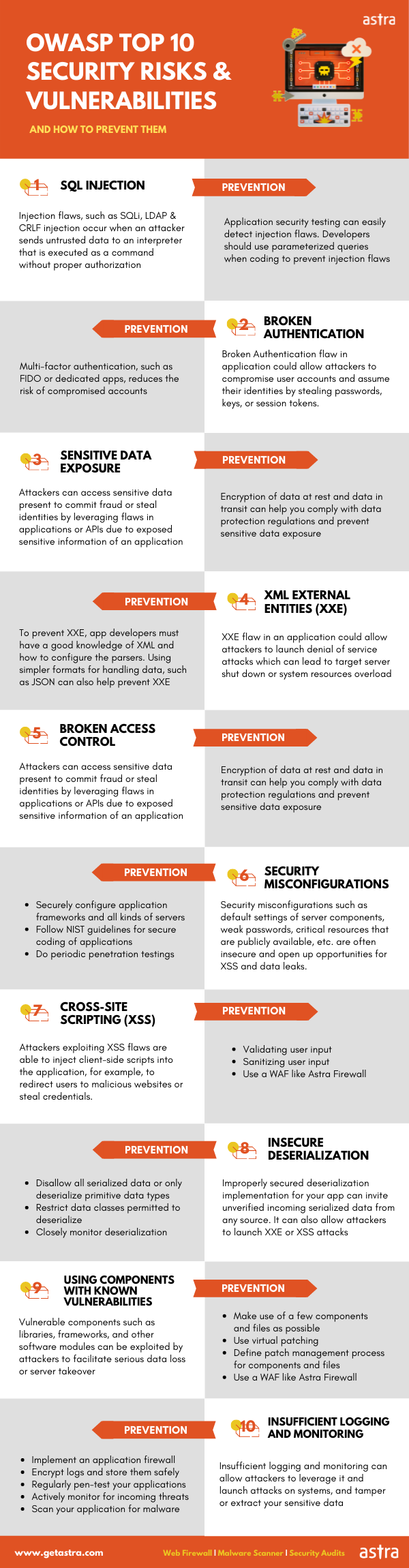
API Security Considerations: Some common issues highlighted in OWASP API Security Top Ten include:
- Improper authentication
- Broken access control
- Insufficient logging & monitoring in the context of APIs.
Follow the suggested best practices such as:
- Conducting thorough security checks of all vendors,
- Leveraging TLS for secure communication,
- Sanitizing data.
B. General Data Protection Regulation (GDPR)
GDPR is a comprehensive data protection regulation in the European Union that holds implications for API security as organizations must ensure safe transfer and user control over their data especially through APIs.
API Security Considerations:
- Implement encryption (e.g., TLS) for data transmitted via APIs
- Authenticate and authorize API users
- Provide mechanisms for data portability and erasure as applicable.
Failure to comply can cost up to €20 million, or 4% annual global turnover – whichever is higher, along with a suspension and ban of services across the globe.
C. NIST Cybersecurity Framework:
The NIST Cybersecurity Framework is a set of guidelines for enhancing cybersecurity that emphasizes the importance of protecting data and systems through APIs.
API Security Considerations: To ensure compliance align your API security practices with the NIST Framework’s core functions: Identify, Protect, Detect, Respond, and Recover. This includes:
- Identifying API risks
- Protecting API endpoints
- Having incident response plans.
Non-compliance can cause loss of federal funding and projects if any, along with lawsuits.D.
D. Health Insurance Portability and Accountability Act (HIPAA)
HIPAA regulates the protection of personal health information (PHI) in the healthcare sector and mandates its protection, which has API implications as it includes data accessed via APIs.
API Security Considerations: Ensure that APIs handling PHI are:
- Encrypted
- Access-controlled
- Audited to prevent unauthorized access to sensitive healthcare data.
Non-compliance fines can range from $127 to $250,000, along with jail time up to 5 years and criminal as well as civil lawsuits.
As such, non-compliance with industry standards and mandatory compliances such as the above often carry hefty penalties and legal actions.
How Do You Protect Mobile App API?
Here are some best practices and strategies to help you secure your mobile app APIs effectively:
1. Authentication and Authorization:
- Use robust authentication methods, such as OAuth 2.0 or JWT (JSON Web Tokens), to verify the identity of users and devices accessing your APIs.
- Use strong password policies and implement multi-factor authentication (MFA) for all user accounts.
- Define granular access controls to ensure users have appropriate permissions to access specific API endpoints.
- Use role-based access control (RBAC) to assign permissions based on user roles.
- Use secure tokens and sessions for user authentication and authorization, and ensure they expire after a reasonable period.
2. Encryption:
- Employ HTTPS (SSL/TLS) to encrypt data in transit between the mobile app and the server. Ensure that SSL certificates are properly configured and up to date.
- Always encrypt sensitive data stored on the device as well as the server using strong encryption algorithms and secure key management practices.
3. Input Validation:
- Implement strict input validation and sanitization to prevent common security vulnerabilities like SQL injection, cross-site scripting (XSS), and command injection.
- Implement rate limiting to prevent abuse and DoS attacks. Limit the number of requests a client can make within a specified time period.
4. Security Headers & API Versioning:
- Implement security headers like Content Security Policy (CSP), Strict-Transport-Security (HSTS), and X-Content-Type-Options to enhance security.
- Use versioning in your API to maintain backward compatibility. This prevents breaking changes from affecting existing users.
5. Security Assessments
- Set up comprehensive monitoring and logging to detect and respond to suspicious activities or security breaches in real time.
- Perform regular security testing, including penetration testing and code reviews, to identify and remediate vulnerabilities.
- Train your development and operations teams on best practices for API security to ensure everyone understands their role in maintaining a secure API.
- Periodically conduct security audits and assessments to identify and address potential weaknesses in your API.
6. Error Handling:
- Ensure that error messages returned by your APIs do not disclose sensitive information about the application’s structure or data.
- Provide generic error messages to users while logging detailed errors for debugging.
Top 3 Tools for Mobile App API Security
1. Astra Security:
Astra, a potent API penetration testing tool, combines manual and automated pentesting services to identify flaws, misconfigurations, and potential attack vectors efficiently. It streamlines security assessments by automating tests, generating detailed reports, and aiding in industry compliance.
Features
- Platform: Online
- Scanner Capacity: Unlimited continuous scans
- Manual Pentest: Available for web app, mobile app, APIs, and cloud infrastructures
- Accuracy: Zero false positives
- Vulnerability Management: Comes with dynamic vulnerability management dashboard
- Compliance: Helps you stay compliant with PCI-DSS, HIPAA, ISO27001, and SOC2
- Price: $2,499/year
With seamless tech stack integrations, customizable reporting, and real-time expert support, the team strives to make AWS SaaS security simple, effective, and hassle-free for thousands of websites & businesses worldwide.
2. Intruder:
Intruder, a widely recognized AWS cloud security testing solution performs continuous scans to uncover vulnerabilities in your AWS space. Its comprehensive scans leave no stone unturned, ensuring robust security.
Features:
- Platform: Windows, Linux, macOS
- Scanner Capacity: Websites, servers, and cloud
- Manual Pentest: No
- Accuracy: False Positive Present
- Vulnerability Management: No
- Compliance: SOC2, and ISO 27001
- Price: $2,656/year
This tool aids organizations in vigilant monitoring of their attack surfaces, swiftly detecting any alterations or weaknesses that could pose online vulnerabilities. Furthermore, Intruder facilitates informed decision-making by categorizing vulnerabilities based on their severity, enabling organizations to prioritize and address them effectively.
3. Nessus:
Nessus is a widely used vulnerability assessment tool that can be adapted for API security testing. It scans APIs for known vulnerabilities and provides detailed reports to help organizations address security weaknesses.
Features:
- Platform: Windows, macOS
- Scanner Capacity: Web applications
- Manual Pentest: No
- Accuracy: False positives possible
- Vulnerability Management: Yes (Additional Cost)
- Compliance: HIPAA, ISO, NIST, PCI-DSS
- Price: $4,236.20/ year
Offering point-in-time analyses, it streamlines detection and remediation, providing real-time alerts for new vulnerabilities. The tool’s flexible configuration options align with specific target requirements and contribute to compliance maintenance as well.
Conclusion
In conclusion, understanding and prioritizing mobile app API security is crucial in today’s interconnected digital landscape. As mobile apps continue to thrive, neglecting API security can lead to data breaches, financial loss, and damage to a company’s reputation and customer trust. By adhering to industry standards, conducting regular assessments, and implementing robust security measures, such as authentication, encryption, input validation, and rate limiting in the face of evolving threats, we can ensure that mobile app APIs remain a secure conduit for data, fostering user confidence and data protection in an increasingly interconnected world.
FAQs
What is meant by API security?
API security refers to the measures and protocols put in place to protect Application Programming Interfaces (APIs) from unauthorized access, data breaches, and other security threats. It involves authentication, authorization, encryption, and validation mechanisms to ensure that only authorized users or systems can interact with the API, maintaining data integrity and confidentiality.
What is the difference between REST API and mobile API?
A REST API is a type of web API that follows a specific architectural style for communication, while a mobile API generally refers to APIs specifically designed to support mobile applications. Mobile app API security in iPhone and Android ensures that APIs used by the respective apps are protected from security threats.
How much does API penetration testing cost?
The cost of API penetration testing can vary widely depending on factors like the complexity of the APIs, the number of APIs to test, and the scope of testing. On average Mobile app API penetration tests typically range in cost from $5,000 to $30,000. These tests aim to identify vulnerabilities in SaaS applications, web applications, along with mobile application APIs and their supporting backends.














