With a cyberattack happening every 39 seconds, the question isn’t “Do you need a pentest?” anymore, but rather – HOW OFTEN do you need a pentest to secure your business?
Navigating the maze of 50+ global and local penetration testing companies can feel overwhelming. They all promise detailed reports, feature-packed solutions, and “holistic security” wrapped in a confusing bow of technical jargon. But which company is the best fit for your needs?
Our security experts have curated the top 10 pen-testing providers.
They have focused on the quality of various non-negotiables such as Pentester’s qualifications, pentest management platform, scan-behind-logins, effectiveness of pentest reports, compliance satisfaction, realistic timelines, and cost.
Top 10 Penetration Testing Companies
- Astra Security
- Intruder
- Cobalt.io
- Acunetix
- Invicti
- Breachlock
- Rapid7
- Sciencesoft
- SecureWorks
- Cyberhunter
Factors To Consider When Choosing a Penetration Testing Company
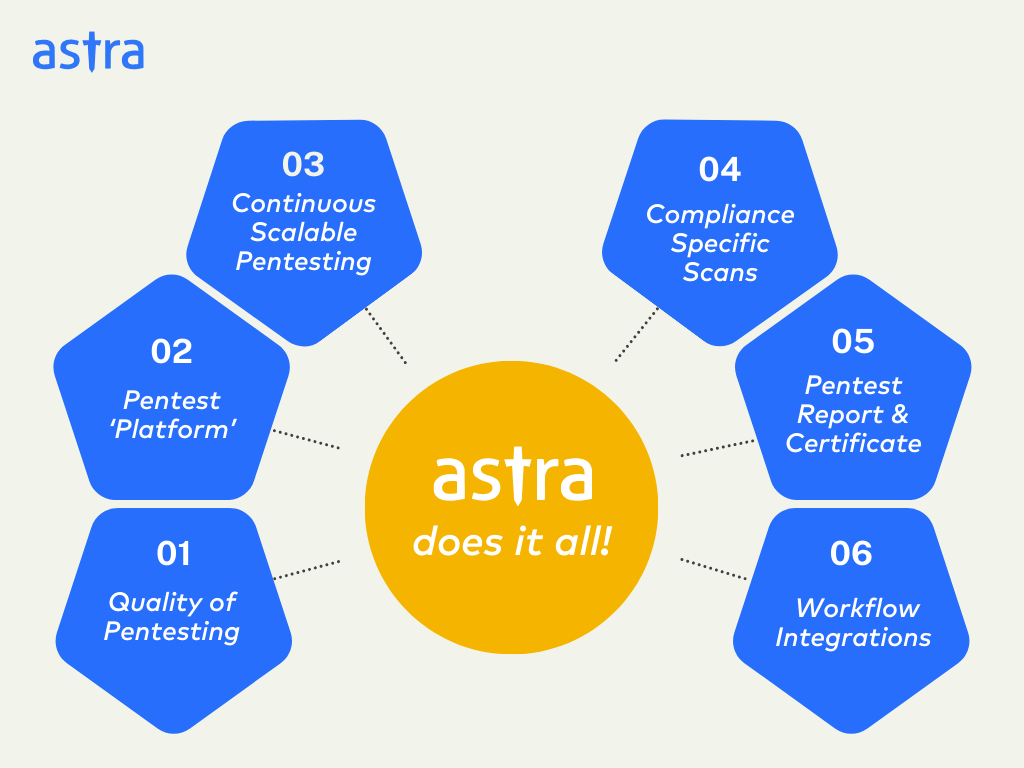
1. Quality of Pentesting:
Prioritize pen-testing companies equipped with scanners to run event-triggered, continuous, and ad-hoc scans. Look for experienced analysts with OSCP certifications and 3+ years of experience in pentesting your specific type of application.
2. Pentest ‘Platform’:
Choose a company that offers a centralized dashboard to track real-time updates on pentests, key reports, and streamlined communication to avoid bottlenecks. An intuitive interface, customizable views, and a customer success team help avoid bottlenecks and delays.
3. Continuous Scalable Pentesting:
With growing attack surfaces and tech stacks, the pentest platform should offer seamless integration along with the ability and know-how to undertake large-scale tests. Continuous vulnerability assessments with scan-behind-logins help expose zero days between updates.
4. Compliance-Specific Scans:
Comply with industry-specific regulations (e.g., HIPAA, PCI-DSS, SOC2, ISO 27001, etc.) requiring distinct digital checkpoints. Choose external penetration testing companies that offer in-built compliance-focused scans and reporting algorithms.
5. Pentest Report and Certification:
Look for companies that offer executive reports for management and exhaustive reports for developers with vulnerability details, CVSS score, and steps to replicate and patch it. Publically verifiable certificates showcasing a clean bill of health build trust with your consumer base.
6. Workflow Integrations:
To avoid workflow and communication delays, the ideal platform should conduct endpoint mapping & robust authentication to view vulnerabilities comprehensively. It should also seamlessly integrate with your CI/CD pipeline, such as Jira, GitHub, GitLab, Slack, etc.
Why Astra is the best in pentesting?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- Our automated scanner scans for 9300+ vulnerabilities
- Vetted scans ensure zero false positives
- Our intelligent vulnerability scanner emulates hacker behavior & evolves with every pentest
- Astra’s scanner helps you shift left by integrating with your CI/CD
- Our platform helps you uncover, manage & fix vulnerabilities in one place
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

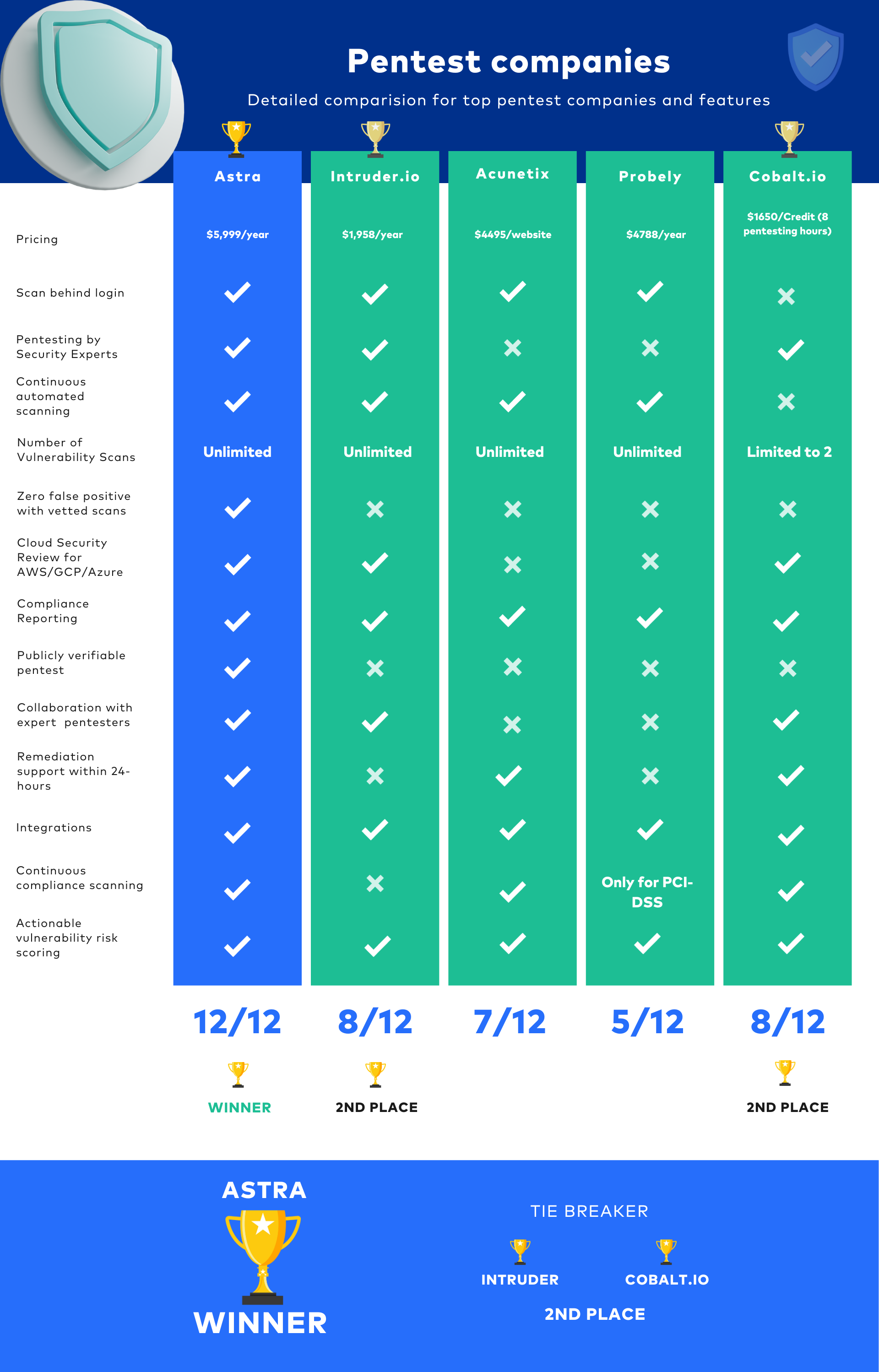
Comparing the Top 3 Pentesting Companies
| Features | Astra | Intruder | Cobalt |
|---|---|---|---|
| Pentest Capabilities | Web and Mobile Apps, Cloud, API, and Networks | Websites, Servers, and Cloud | Web and Mobile Applications, APIs, Networks, and Cloud. |
| Platform | Manual, Automated & AI-augmented | Automated scanning | Manual pentest |
| Continuous Vulnerability Scanning | Yes | Yes | Yes |
| Compliance Scanning | Yes | Yes | Yes |
| AI-powered Test Cases | Yes | No | No |
| Pentest Reports | Yes | Yes | Yes |
| Publically Verifiable Certificates | Yes | No | No |
| Workflow Integrations | Slack, GitLab, GitHub, Jira, Jenkins and more | GitHub, Atlassian. Jira, and more | JIRA, Slack, Onetrust, GitHub and more |
| Expert Remediation | Yes | No | Yes |
| Scan Behind Login | Yes | Yes | No |
| Pricing Plan | Starts at $1999/yr | Starts at $1958/yr for VA only | Starts at $1650/credit |
The Top 10 Best Penetration Testing (Pentest) Companies in 2024
1. Astra Security

Key Features:
- Pentest Capabilities: Web and Mobile Applications, Cloud Infrastructure, API, and Networks
- Accuracy: Zero false positives (Assured with Vetted Scans)
- Scan Behind Logins: Yes
- Compliance: Reporting for PCI-DSS, HIPAA, SOC2, and ISO 27001
- Expert Remediation: Yes
- Publically Verifiable Certification: Yes
- Workflow Integrations: Jira, GitHub, GitLab, Slack, and Jenkins
- Cost: Starting at $1999 per year
- Best Suited For: Pentestig multiple assets & continuous vulnerability scanning going forward
Astra is a leading penetration testing company that blends automation, artificial intelligence, and manual expertise of security engineers with a combined experience of 50+ years to run 9,300+ tests and compliance checks, ensuring complete safety, irrespective of the threat and attack location.
With customers spanning various industries and countries, our industry-specific AI test cases, world-class GPT-powered chatbot, and customizable reports guarantee a smooth experience while saving you millions of dollars proactively.
With zero false positives, seamless tech stack integrations, and real-time expert support, we strive to make pentesting simple, effective, and hassle-free.
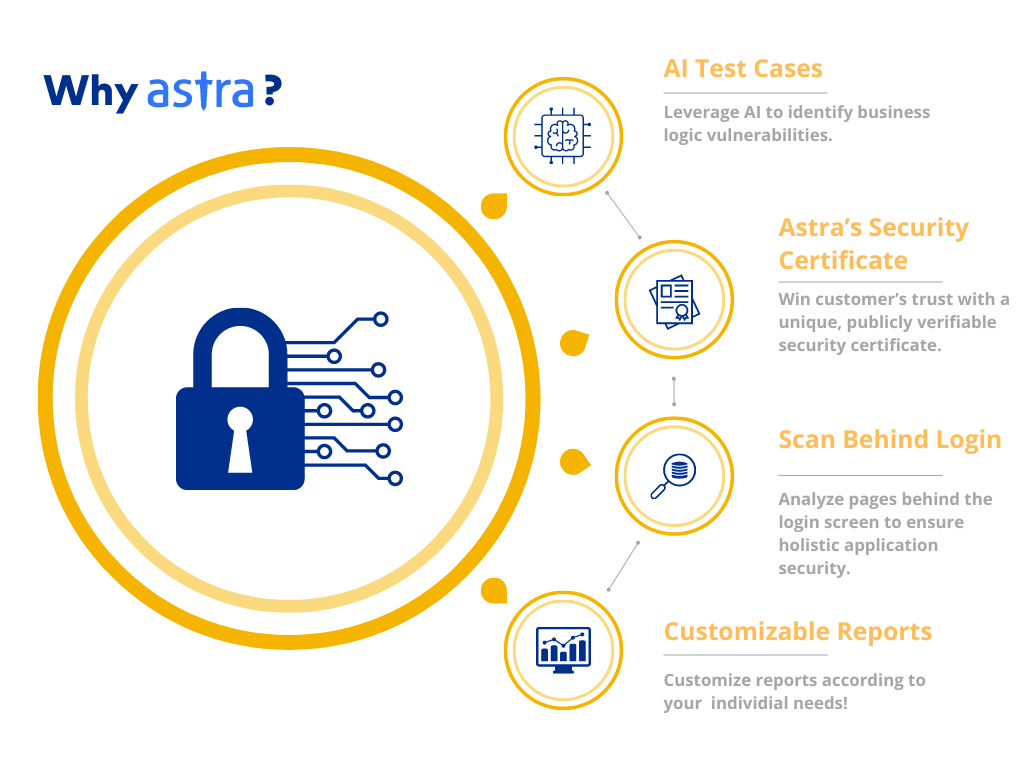
Pros:
- Pentest by security experts with OSCP, CEH & CVEs under their name
- Continuous proactive pen testing available via vulnerability scanner
- Seamless CI/CD, JIRA & Slack integrations
- Customized executive and engineer-friendly reporting
- Scan behind logged-in pages
- Zero false positives
Limitations:
- Only 1-week free trial available
2. Intruder
Key Features:
- Pentest Capacity: Websites, servers, and cloud.
- Accuracy: False positives present
- Scan Behind Logins: Yes
- Compliance: SOC2, and ISO 27001
- Expert Remediation: No
- Publically Verifiable Certification: No
- Workflow Integrations: GitHub, Jira, Atlassian
- Cost: $1958/ year (Vulnerability Scanning only. Pentest pricing available on demand)
- Best Suited For: Cloud pentesting
As a penetration testing platform for cloud infrastructures and web apps, Intruder employs a mature vulnerability scanner that helps you find and fix critical vulnerabilities. The platform’s reports are famous for their evidence-based formatting, which promotes a cyber risk-education strategy.
With the majority of clients in the banking and financial services industry, Intruder’s consultants have an intimate understanding of financial application landscapes, compliance requirements, and data security needs.
Pros:
- Easy to deploy
- Easy to manage alerts
Limitations:
- Unavailability of bespoke pentest pricing
- The pricing can get too steep quickly
3. Cobalt.io
Key Features:
- Pentest Capacity: Web and mobile applications, APIs, Networks, and Cloud
- Accuracy: False positives possible
- Scan Behind Logins: No
- Compliance: SOC2, PCI-DSS, HIPAA, CREST
- Expert Remediation: Yes
- Publically Verifiable Certification: No
- Workflow Integrations: Jira, GitHub, Onetrust, JupiterOne, and Kenna
- Cost: $ 1650/Credit (8 pentesting hours)
- Best Suited For: Manual pentesting
Cobalt.io is a penetrating testing platform that helps you connect with pen testers according to your security testing needs. The program designs and runs practical attack scenarios personalized to your industry and risk profile.
As a veteran-owned business, Cobalt offers special discounts to government agencies, although the majority of their clients belong to the financial and healthcare industries. Unfortunately, they don’t offer any automated scanning services.
Pros:
- Industry-specific real-world attack simulations
- Pentesters are extremely responsive during the tests
- Simple UI
Limitations:
- A crowdsourced security team is not acceptable to every business
- Lack of continuous vulnerability scanning post the pentest
- Complex pricing structure
4. Acunetix
Key Features:
- Scanner Capacity: Web applications
- Accuracy: False positives possible
- Scan Behind Logins: Yes
- Compliance: OWASP, ISO 27001, PCI-DSS, NIST
- Expert Remediation: Yes
- Publically Verifiable Certification: No
- Workflow Integrations: Jira, GitHub, GitLab, DevOps, and Mantis
- Cost: Available on quote
- Best Suited For: Automated vulnerability scanning & pentesting
As a fully automated web vulnerability scanning tool, Acunetix is capable of detecting over 4500 vulnerabilities which include variants of SQL and XSS injections. The tool also supports HTML5, CMS systems, single-page applications as well as Javascript.
Being developer-friendly, Acunetix offers integration support for everything from IDEs to CI/CD pipelines and GRC platforms. The detailed scan reports include proof of concepts and remediation guidance.
Pros:
- Fully automated vulnerability scanner
- Optimizable for different platforms
- Easy to schedule scans.
Limitations:
- Difficult to add users
- Vulnerability PoCs are too complex
- Pentest offering is self-served without security experts doing it, this isn’t always accepted by customers
5. Invicti
Key Features:
- Scanner Capacity: Web applications and APIs
- Accuracy: False positives possible
- Scan Behind Logins: No
- Compliance: PCI-DSS, HIPAA, OWASP, ISO 27001
- Expert Remediation: Yes
- Publically Verifiable Certification: No
- Workflow Integrations: Jira, GitHub, GitLab, Kenna, and Bitbucket
- Cost: Available on quote
- Best Suited For: Dynamic pentesting
As a leading VAPT service provider, with 20+ years of experience, Inviicti offers the complete package. Even with offerings of quality pen testing services, the true strength lies with their world-class vulnerability scanner that helps conduct quick security audits on web apps using advanced DAST techniques.
With graphical representations of vulnerability analyses, compliance assistance, and a very transparent way of presenting data, Invicti is surely one of the top security testing companies.
Pros:
- Abundance of security policies
- SAST/DAST/IAST enabled scans
- OWASP Top 10 vulnerability detection
Limitations:
- No support for 2FA and MFA apps
- Slows down while scanning large applications
6. Breachlock
Key Features:
- Scanner Capacity: Web applications, cloud, and networks
- Accuracy: False positives possible
- Scan Behind Logins: Yes
- Compliance: SOC 2, PCI DSS, HIPAA, and ISO 27001
- Expert Remediation: Yes
- Publically Verifiable Certification: No
- Workflow Integrations: Jira, Slack, and Trello
- Cost: Available on quote
- Best Suited For: Vulnerability management and AI-augmented pentesting.
Breachlock is a penetration testing platform that leverages a lethal combination of automation, AI, and certified ethical hacking to identify vulnerabilities. The penetration-testing-as-a-service model aims to deliver end-to-end services.
The platform also conducts AI-augmented pentests with compliance reporting options for standards like SOC 2, PCI DSS, and HIPAA, giving you a comprehensive picture of your security posture.
Pros:
- Continuous addition of risk checks
- Scalable vulnerability management solution
- 360-degree view of vulnerabilities on the platform
Limitations:
- Product support could be improved
- Documentation can be confusing
7. Rapid7
Key Features:
- Scanner Capacity: Cloud and Web Applications
- Accuracy: False positives possible
- Scan Behind Logins: No
- Compliance: CIS, ISO 27001.
- Expert Remediation: No
- Publically Verifiable Certification: No
- Workflow Integrations: ServiceNow Security Operations, LogRhythm NDR, and ManageEngine
- Cost: $2100/year
- Best Suited For: Vulnerability management penetration testing
With multiple cybersecurity tools in its arsenal, Rapid7 is one of the top penetration testing firms that aims to deliver end-to-end vulnerability management and sustainable security solutions.
The service portfolio includes detection and response, security scanning, and vulnerability management. The penetration testing experts at Rapid7 leverage the company’s deep roots in open-source pentesting tools like Metasploit, to find vectors automated scanners often miss.
Pros:
- Great for finding hidden vulnerabilities
- They maintain top-notch threat intelligence
Limitations:
- Users have reported issues with functionality and customer support
- The devices that are scanned have to be removed manually
Should you integrate your SDLC environment into your pentest’s SOW?
Integrating your Software Development Life Cycle (SDLC) environment into your pentest’s Statement of Work (SOW) ensures thorough testing aligned with your development processes, identifying vulnerabilities early and enhancing overall security.
8. Sciencesoft
Key Features:
- Scanner Capacity: Web, mobile applications, network, IoT
- Accuracy: False positives possible
- Scan Behind Logins: No
- Compliance: GDPR, HIPAA, PCI-DSS, NIST
- Expert Remediation: Yes
- Publically Verifiable Certification: No
- Workflow Integrations: Jira, Jenkins, and GitHub
- Cost: Available on quote
- Best Suited For: Custom penetration testing
Sciencesoft is a penetration testing service provider that specializes in designing security checks for networks, mobile, IoT, and embedded systems. It is an ISO 9001 and ISO 27001 compliance-certified company.
Additionally, Sciencesoft offers compliance-specific scans for industry standards such as HIPAA, PCI DSS, GDPR, and NIST. The biggest advantage of the platform is its 30+ years of experience and partnerships with IBM, Microsoft, and several other retailers providing data analytics.
Pros:
- End-to-end services from identification to remediation
- Social engineering testing exercises
Limitations:
- Weak remediation support
9. SecureWorks
Key Features:
- Scanner Capacity: Web and mobile applications, networks, APIs
- Accuracy: False positives possible
- Scan Behind Logins: Yes
- Compliance: PCI-DSS, HIPAA
- Expert Remediation: Yes
- Publically Verifiable Certification: No
- Workflow Integrations: AWS, zScaler, Slack, and Jira
- Cost: Available on quote
- Best Suited For: Security consulting
As a Managed Security Services Provider (MSSP), Secureworks offers penetration tests for information assets, networks, and systems. The portfolio also includes services like application security testing, malware detection, risk assessments, and incident response.
Its high-functioning security event analysis engine is capable of performing nearly 250 billion cyber programs that help in threat detection and mitigation making it one of the most extensive cybersecurity solutions.
Pros:
- Easy to align the security environment with industry standards like NIST and ISO
- Active communications with executive-level summaries are available
Limitations:
- Too expensive for SMEs
- There’s a delay between suspicious activity and the alert raised
10. CyberHunter Solutions
Key Features:
- Scanner Capacity: Websites and networks
- Accuracy: False positives possible
- Scan Behind Logins: No
- Compliance: ISO 27001
- Expert Remediation: No
- Publically Verifiable Certification: No
- Workflow Integrations: SentinelOne
- Cost: Available on quote
- Best Suited For: Network pentesting
As a security leader who specializes in comprehensive network threat audits, Cyberhunter provides a variety of services including but not limited to threat assessments, penetration testing, and network log monitoring.
The platform carries out extensive reconnaissance, vulnerability mapping, exploits, and real-time threat analysis activities on networks and web apps for both compliance and security-driven needs.
Pros:
- Good for network traffic analysis
- Aligns security control analysis with industry standards
Limitations:
- Doesn’t offer cloud and mobile pentesting
- No CI/CD integration
Penetration Testing Companies in The USA
While global penetration companies offer obvious benefits, the messages lost in translation or cultural and cannotation cracks, can pose a significant risk for bottlenecks.
Moreover, with rigid federal laws guarding national security, public undertakings under the government of the USA (and private firms associated with them) are often legally mandated to choose a domestic vendor with appropriate government certifications.
However, despite these challenges, the United States boasts a strong selection of top-tier penetration testing companies. The top 3 USA-headquartered companies include:
Can’t Decide? Leverage the Pentest Company Chooser by Astra!
How To Choose The Right Pentesting Company?
1. Put Yourself First
After all is said and done, it is quite easy to get lost in all the technical jargon of security postures, continuous scanners, and end-to-end vulnerability managers Our tip, before starting, write down these 3 essentials such as:
- Why do you need the pentest?
- What’s your financial budget and timeline cutoff?
- Are there any specific compliances you need to test for?
Why? This gives you a list of your non-negotiables and helps you outline your ideal cybersecurity partner, while also defining the maximum length of rope you can sacrifice.
2. Ditch the Guesswork:
It’s every company’s job to highlight its benefits and offerings. Take time to go through their best and worst reviews to get an insight into the real picture. Try to also find similar industry players or requirements to avoid future problems.
Pro Tip: Look for proven players – companies with rock-solid reputations and glowing customer reviews (outside of the company-owned channels).
3. Evaluate the Pentest Reports:
That 50-page pentest report is the difference between keeping your business assets secure and giving in to a false sense of security. Make sure that behind all the developer-friendly jargon, the exhaustive reports offer actionable insights into vulnerabilities and how to patch them.
Pro Tip: The jargon-heavy reporting makes executive meetings quite brutal. As such customizing “executive’s special report” goes a long way.
4. Assess the Customer Support
The problem of choice is real! Once you identify a vulnerability, there is usually more than one way of fixing it available, leading to back-and-forth between teams also known as bottlenecks.
With evolving environments, active customer support is essential to solving such bottlenecks. They can not only help you gain better insights but also help speed up the remediation processes.
Why is Astra the Best Choice For You?
Besides catering to the pentesting needs of a diverse set of industries from finance and healthcare to e-commerce, we have emerged as a leader in the G2 penetration testing category.

With high-performer tags across the continents, from America to Europe, India, and APAC, 650+ companies trust Astra! Moreover, with us, our customers have saved potentially more than $42 million and patched 892k+ vulnerabilities in one year.
Still don’t believe us? Well, let’s take a look at what some of our recent customers have to say!
Final Thoughts
Although the above is far from an exhaustive list, they offer some deep insight into the world of penetration testing providers. But, only you can decide which is the best choice for your needs, budgets, and industry.
Key considerations include scanning capabilities, an all-encompassing dashboard, scalable testing, compliance-specific scans, and adherence to security protocols. Prioritizing reviews, comprehensive reports, and responsive customer support can also help significantly.
A penetration test is far from cheap, but the ROI is definitely worth it!
FAQs
1. Who are Penetration Testing Providers?
Penetration testing providers are external third-party penetration testing providers. The main purpose of external penetration testing is to identify security problems that are not visible to the internal penetration testing team.
2. Why do I need a Penetration Testing Provider despite having an Internal Security Team?
Choosing an external pentest provider can significantly benefit your organization, even if you already have an internal team. External pentest providers can provide you with a much more in-depth analysis of your security.
3. Can I trust Astra for Penetration Testing?
Well, the answer is YES. As a leading provider of information security and penetration testing services, we have been helping businesses worldwide to enhance and maintain their security posture. We have a team of experienced penetration testers who have worked in various industries and have a diverse range of experience.
This post is part of a series on penetration testing, you can also check out other articles below.
Chapter 1. What is Penetration Testing
Chapter 2. Different Types of Penetration Testing?
Chapter 3. Top 5 Penetration Testing Methodology to Follow in 2024
Chapter 4. Ten Best Penetration Testing Companies and Providers
Chapter 5. Best Penetration Testing Tools Pros Use – Top List
Chapter 6. A Super Easy Guide on Penetration Testing Compliance
Chapter 7. Average Penetration Testing Cost in 2024
Chapter 8. Penetration Testing Services – Top Rated
Chapter 9. Penetration Testing Report

















Nice informative article. I was curious on how to get the most out of a penetration testing services?
To get the most out of penetration testing services you must stick with a reputable provider you can trust, establish a clear testing scope that prioritizes important assets, provide detailed information regarding your network and systems, and have a realistic expectation of the outcomes.