In today’s world, it is seemingly impossible to find a website security guide that does not mention an IT Security audit as a must. But, the word ‘audit’ makes us think of managers, business owners, and an expensive affair altogether.
However, the cost of dealing with the aftermath of cybercrime is a lot more expensive than investing in effective security and insight. The IT security audit cost usually varies depending on the size of the business and the risks associated with it.
Before going into what the average IT security audit cost is, let’s look at why it’s important to conduct them.
Why are IT security audits important?
Regular audits can identify the vulnerabilities in your existing security measures – and they can also boost your customers’ trust in your website! In some industries, it is required by law to carry out regular audits.
| Scanner | Pentest | Enterprise |
|---|---|---|
| $1,999 per year | $ 5,999 per year | $ 7,999 per year |
| Weekly Vulnerability Scans | Unlimited Vulnerability Scans & 1 Manual Pentest | Vulnerability Assessment & Pentesting by Security Experts |
| 9,300+ Tests | Integration with CI/CD Tools | Cloud Security Report |
| Pentest Dashboard, Scan Behind Login | Zero False Positive Assurance | Publicly Verifiable VAPT Certification |
| Free trial for 7 days | Everything in the Scanner Plan | Everything in the Pentest Plan |
Also, in some cases where businesses keep getting re-infected despite malware cleanups and security infrastructure, the reason may be an unpatched vulnerability in the system. In such cases, IT security audits work like a charm. They uncover all the hidden vulnerabilities in your system.
Here are a few more benefits you can get out of IT security audits:
- IT security audits uncover the new vulnerabilities that are introduced by new technology or processes
- Verify if your current security is capable of fending off threats
- Ensure that your IT infrastructure is compliant with the latest regulations
- Analyse the strengths and weaknesses of the security measures you have in place
You may like to read: Choosing The Right Security Audit Company Made Easy
What does an IT security audit entail?
A detailed IT security audit consists of several independent assessments of various IT aspects. The auditor would first access the external vulnerabilities of the IT infrastructure to assess how quickly an attacker can break into your defenses. This aspect of auditing usually involves in-depth system scans along with white-hat hacking.
The auditor then tries to compromise the existing IT security systems to prove their effectiveness in the wake of an attack. After that, the auditor would investigate the internal mechanisms of the network to ensure that the password permissions and account standards are maintained properly. In many cases, the security experts would often interact with a company’s employees themselves to achieve this.
Also Read: Security Audit Services: Importance, Types, Top 3 Companies
In order to prepare the company for worst-case scenarios, the auditor would also check the backup plans and disaster recovery systems. These thorough checks would establish whether these systems can help the company bounce back after a cyber attack.
Is an IT security audit worth it?
The cost of a comprehensive IT security analysis depends largely on the size and complexity of the company.
Generally, the cost of an IT security audit usually ranges from $700 to $2500. This might seem like a lot – but when you look at the bigger picture, these audits can save your organization from cyber attacks – dealing with which can prove to be far more expensive.
The average cost of a corporate data breach in 2020 was calculated to be $3.9 million – so you can see why it is becoming increasingly crucial for companies to partner with cybersecurity organizations so that their business and reputation don’t suffer. The IT security audit cost is well worth the benefits!
Related blog – Cloud Security Audit: Everything You Need to Know | Pen Testing Cost
What does Astra’s professional IT security audit cost?
Astra ensures that your IT infrastructure is in safe hands. In addition to the security suite, we also offer comprehensive security audits and VAPT.
You can choose how frequently you want us to audit your security – we offer one-time, bi-annual, and quarterly scans. These scans are offered in three tiers of plans – Scanner, Pentest, & Enterprise – which differ in the number of tests offered, the support offered, rescans, reports, etc. which you can choose based on your needs. You can find out more about Astra’s IT security audit cost and plans here.
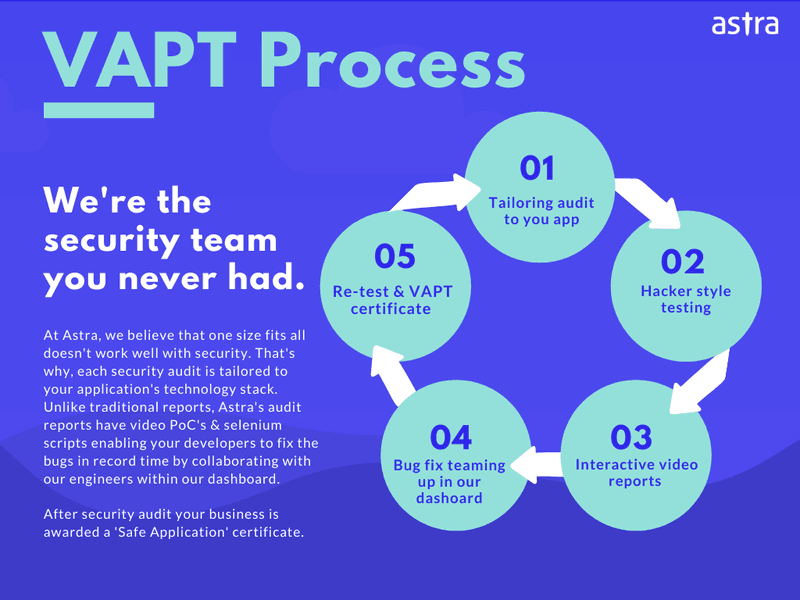
Astra ensures that your IT infrastructure is impermeable to malware attacks and remains that way – our tried and tested VAPT process will tell you the same:
Also Read: 10 Best Cyber Security Audit Companies: Features and Services Explained
If you have other queries about our IT security audit cost or plans, just initiate a chat with us using the chat widget. One of our engineers will be with you soon 🙂
About Astra Security Suite
Astra is the essential web security suite that helps you fight hackers, internet threats & bots by finding vulnerabilities in your systems and helping you place adequate security measures. We provide proactive security for your websites running popular CMSs like WordPress, OpenCart, Magento, etc.
FAQs
How long does a security audit take?
The security audit by Astra takes 7-10 days for websites and apps, and 4-5 days for cloud infrastructures.
How much does IT security testing cost?
The cost for security testing ranges between $199 and $499 per month for websites.
Why choose Astra security Scans?
The security engineers at Astra perform extensive manual pentest on top of machine learning-driven automated scans. The vulnerability reports appear on your dashboard with detailed remediation guides. You will have access to a team of 2 to 10 security experts to help you with the fixes.
Do I also get rescans after a vulnerability is fixed?
Yes, you get 1-3 rescans based on the type of Pentesting and the plan you opt for. You can avail of these rescans within 30 days from the initial scan completion even after the vulnerabilities are fixed.
















