An IT security audit is a comprehensive assessment of an organization’s security posture and IT infrastructure. Conducting an IT security audit helps organizations find and assess the vulnerabilities existing within their IT networks, connected devices, and applications. It gives you the opportunity to fix security loopholes and achieve compliance.
So, let’s dig deep and find out how to do an IT security audit, its benefits for online businesses, and more.
Why Is There A Need For IT Security Audits?
Online expansion of IT assets has come with increased cyber risks with more targeted attacks against organizations ranging from small to large to disrupt their businesses and revenue.
Performing an IT security audit can help organizations by providing information related to the risks associated with their IT networks. It can also help in finding security loopholes and potential vulnerabilities in their system. Thereby patching them on time with patch management software and keeping hackers at bay.
This includes things like vulnerability scans or conducting penetration tests to gain unauthorized access to the systems, applications, and networks. Finally, the penetration testing reports generated after performing all the necessary procedures are then submitted to the organization for further analysis and action.
How Often Do Conduct IT Security Audits?
Companies that store sensitive information and handle payments or security data are advised to carry out security audits at least twice a year. It is important to keep in mind that security audits are a time-taking process and therefore beforehand planning is required to ensure a smooth security audit.
IT Security Audit Checklist
This section provides a comprehensive list of items that should be checked out during a security audit. It is important to note that this differs based on the company’s needs and requirements. However, this IT security audit checklist will provide a general idea.
1. Data Security
- Check for data encryption both at rest and in transit (TLS).
- Verify implementation of access controls
- Check for data backups and verify their secure storage
2. Network Security
- Verify the up-to-date configuration of firewalls.
- Check for open ports and ensure their security.
- Verify the presence of updated antivirus and malware protection.
3. App Security
- Verify that all patches and security fixtures are current.
- Scan for vulnerabilities like SQL injections, XSS, and others.
- Carry out penetration tests for detailed information on vulnerabilities.
4. User Security
- Verify the strength of password policies in place.
- Ensure that users are trained on best security practices.
- Review and update user access regularly.
These are major areas that should be checked of during an IT security audit.
Benefits of IT Security Audit
As we mentioned, an information security audit reveals underlying vulnerabilities and security risks in an organization’s IT assets. Identifying risks, however, has a positive rippling effect on the organization’s overall security. How? We discuss them point by point below:
- Weighs your current security structure and protocols and helps you define a standard for your organization with the audit results.
- Mitigates hacker-risks by discovering potential hacker entry points and security flaws well in advance.
- Verifies how compliant your IT infrastructure is with top regulatory bodies and helps you conform in accordance.
- Finds lag in your organization’s security training and awareness and helps you make informed decisions towards its betterment.
Also Read: Why Firewall Penetration Testing is Essential to Your Security Strategy
Types of IT Security Audit
There is more than one way to categorize an information technology security audit. Generally, it’s been categorized on the basis of approach, methodology, etc. Some of the common categorizations are:
Approach Based
- Black Box Audit: Here, the auditor only knows about the info that is publicly available regarding the organization that is to be audited.
- White Box Audit: In this type of security audit, the auditor is provided with detailed info (i.e. source code, employee access, etc) regarding the organization that is to be audited.
- Grey Box Audit: Here, the auditor is provided with some info, to begin with, the auditing process. This info can also be gathered by the auditors themselves but is provided to save time.
Methodology Based
Based on IT security audit methodology, audits are divided into:
- Penetration Tests: The auditor tries to break into the organization’s infrastructure.
- Compliance Audits: Only certain parameters are checked to see if the organization is complying with security standards.
- Risk Assessments: An analysis of critical resources that may be threatened in case of a security breach.
- Vulnerability Tests: Necessary scans are performed to find possible security risks. Many false positives may be present.
- Due Diligence Questionnaires: Used for an analysis of existing security standards in the organization.
Also Read: PHP Penetration Testing | 10 Best Cyber Security Audit Companies [Features and Services Explained]
Importance of an IT security audit
- Protects the critical data resources of an organization.
- Keeps the organization compliant to various security certifications.
- Identifies security loopholes before the hackers.
- Keeps the organization updated with security measures.
- Identifies physical security vulnerabilities.
- Helps in formulating new security policies for the organization.
- Prepares the organization for emergency response in case of a cybersecurity breach.
How to conduct an IT security audit for your business? [With tools]
Before beginning with the process of security audits, it is important to use the right set of tools. Kali Linux is one such OS that is customized and contains a bundle of tools to conduct a security audit. This OS can be used by installing on a separate machine or making the present machine dual-booted or on a virtual machine. To install it on a virtual machine, follow this article.
Once everything is set, let’s begin!
1. Recon Dog
While doing a black box IT security audit, it is necessary to gather some info about the target like CMS being used, etc. This would help in narrowing down and targeting the precise security weak points. Recon dog is just the right tool for this purpose. This tool requires no installation so download it from here and start using it as a normal script.
Alternatively, you can open up your terminal in Kali and type:
git clone https://github.com/s0md3v/ReconDogThis will save it into a directory called ReconDog. Now navigate to the directory and run it using the following commands:
cd ReconDogpython dogThereafter, an interface will open asking you for the type of recon you wish to perform. Once you enter the recon option, it will ask for the target URL. After typing it, press enter and the scan will start.

2. Nmap
Another great tool to conduct an IT security audit is Nmap. It can be used to discover open port vulnerabilities and to fingerprint the network internally as well as over the internet. To use this tool, open the terminal in Kali and type:
nmap -v -sS -A -T4 targetReplace target with the IP address you wish to scan. This command runs a stealth scan against the target and tries to detect the Operating system and its version. For more help type:
nmap -h
Also Read: Security Audit Services: Importance, Types, Top 3 Companies
3. Nikto
Nikto is another great tool to find vulnerabilities in the server. Use it to discover all kinds of potential server misconfigurations. However, it also generates a lot of false positives so they need to be verified by exploiting. To scan your site using Nikto, open the terminal in Kali and type:
nikto -h www.your-site.comFor more help type:
nikto -H
4. Metasploit Framework
Metasploit is perhaps one of the most powerful exploitation frameworks used to conduct an IT security audit. All the potential vulnerabilities discovered using Nikto can be checked using Metasploit as it contains a large number of exploits. To use them, open the terminal in Kali and type:
msfconsoleThis will load the Metasploit framework. For further using Metasploit, read this article.

Is your website often hacked? Secure my website now!
5. Xsser
While conducting an IT security audit, it is important to check for common web injection vulnerabilities like SQL injection and cross-site scripting. To tool used to check for XSS vulnerabilities in your website is Xsser. To use it, open the terminal in Kali and type:
xsser --gtkThis will open a graphical interface like the one in the image given below. Just set the necessary options and start hunting for XSS bugs!

6. Sqlmap
To check for SQLi bugs on your site, there is no better tool than Sqlmap. Firstly select a parameter you wish to test. Thereafter, open the terminal in your Kali and type:
sqlmap -u "www.your-site.com/page?param=1" --dbs --random-agent --batchReplace the URL part with the URL of your site and page with the name of the page you wish to test for SQLi and param with the parameter you wish to check. Thereafter, this command will automatically try to exploit SQLi bugs and enumerate the database names to you. For more info type:
sqlmap -h
Tips for IT Security Audits
Here are some tips that are sure to make your information security audit go as smoothly as possible:
- Understanding the scope: This is important for all parties i.e. the auditors and the customer since ill-defined scope can lead to an audit that is not thorough.
- Involve relevant staff: It is important to include all the stakeholders who support your IT environment.
- Use recognized frameworks: Industry-accepted standards such as CIS, and NIST will give your audit credibility and acceptance.
- Detailed documentation: Documenting and having reports on all activities carried out is highly crucial as this can help with remediation and IR planning.
- Prioritize risks: The vulnerabilities and associated risks should be prioritized based on the severity posed to the application in order to make remediation more efficient.
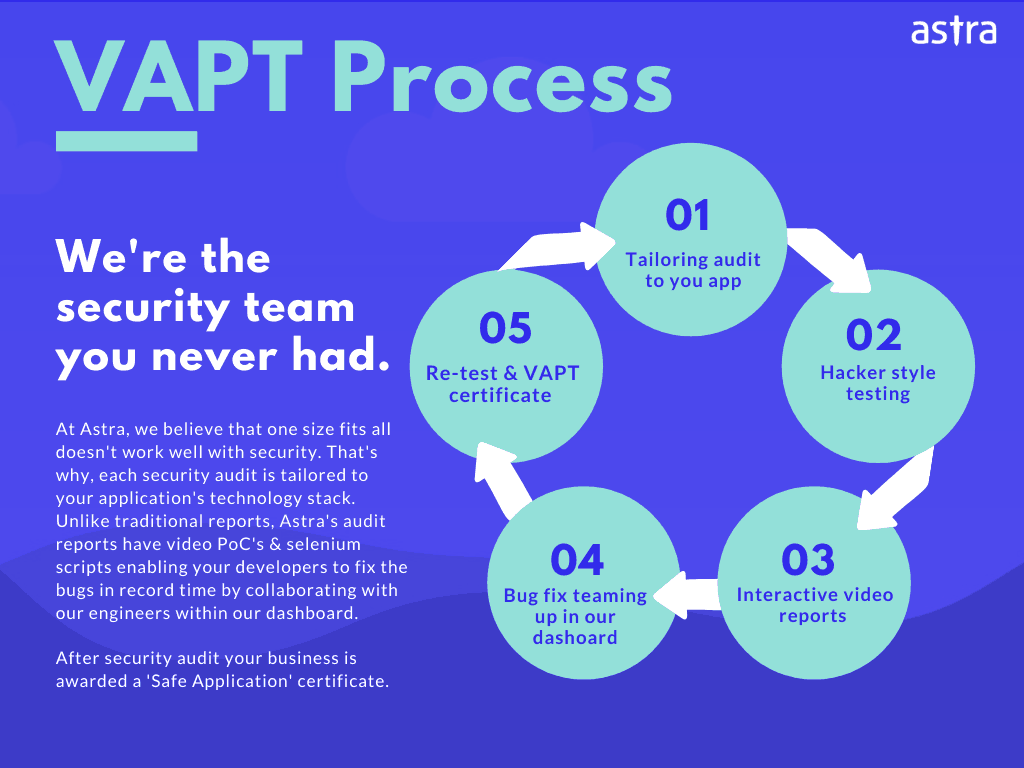
IT Security Audit Service By Astra
Although this article covers many tools, it is just introductory in nature. Hackers are smarter these days. Therefore, for better security and to avoid the cumbersome process of manual security audits, it is advised to go for a professional security audit that can cover vulnerability assessment and penetration testing for an organization’s physical network assets such as firewalls, routers, etc, integrated cloud services, devices such as cameras and printers, etc., and ultimately the web applications.
We at Astra Security provide a robust IT security audit with more than 8000+ active security tests done on applications and networks at very efficient and flexible pricing plans. In addition to this, Astra’s support team ensures that all doubts regarding security audits are clear to you. IT security audit done by Astra can help you discover:
- Zero-day vulnerabilities in applications and networks
- OWASP Top 10 vulnerabilities
- SANS Top 25 vulnerabilities
- Security weaknesses in IoT and Blockchain security controls
- Technical & Business Logic Errors
and much more.
Also Read: Plugin Security Audit
FAQs
What is information security audit?
An information security audit is a comprehensive assessment of an organization’s information security posture and IT infrastructure. Conducting an information security audit helps organizations find and assess the vulnerabilities existing within their sensitive documents, networks, connected devices, and applications.
Do I also get rescans after a vulnerability is fixed?
Yes, you get 1-3 rescans based on the type of Pentesting and the plan you opt for. You can avail of these rescans within 30 days from the initial scan completion even after the vulnerabilities are fixed.
Why choose Astra Security Testing?
8000+ tests, adherence to global security standards, an intuitive dashboard with dynamic visualization of vulnerabilities and their severity, security audit with simultaneous remediation assistance, and multiple rescans, these are the features that give Astra an edge over all competitors.
What is the timeline for IT Security Audit?
IT security testing takes 4-5 days. The rescan takes 2-3 more days after you have fixed the vulnerabilities.

















Much thanks!
🙂