Blockchain technology powers a number of industries today like fintech, crypto, healthcare, etc, and is starting to get its foothold into several others. Being the backbone of these capital-rich industries, blockchain has garnered the attention of hackers. Additionally, security issues in blockchain applications also arise due to improper implementation and maintenance of blockchain apps. A recent survey showed that blockchain hackers stole more than $3.8 billion in about 125 attacks in 2020.
If we are to make a sustainable future out of blockchain, we need to talk about blockchain security today. This is why through this article we will discuss in detail the process of blockchain penetration testing and how it helps in securing blockchain applications. But before that, let’s discuss what exactly is blockchain and blockchain penetration testing?
What is Blockchain?
Blockchain is a type of spreadsheet that contains transaction information, each transaction information creates a hash and each block refers to the previous block. And collectively they form a blockchain. Blockchain technology has successfully transformed the business transaction industry. With its unmatched potential, blockchain has presented us with a wonderful opportunity to take control over transactions, health, and various other services that need privacy and transparency.
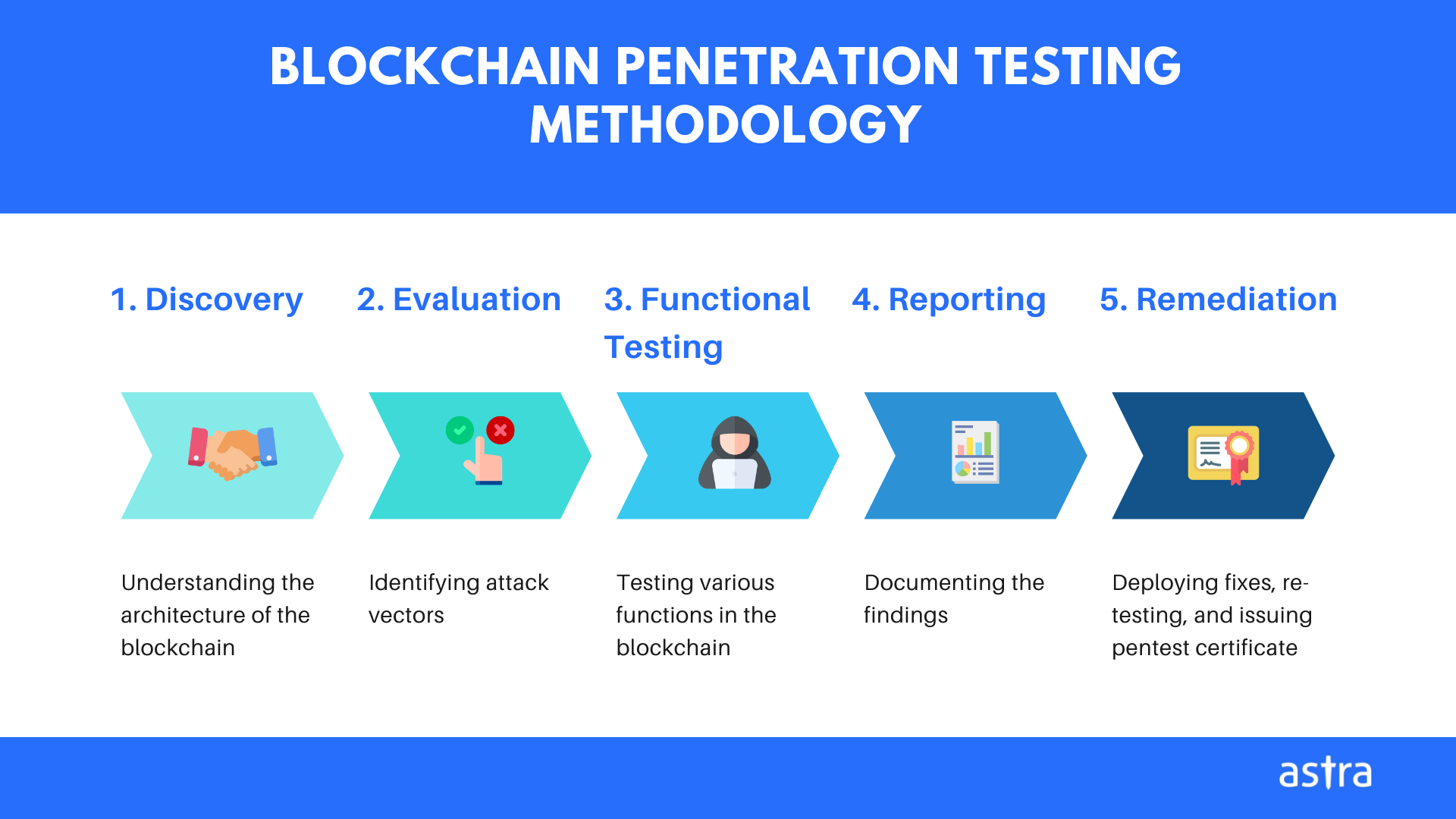
5 Steps involved in the process of Blockchain penetration testing
Effective blockchain penetration testing services involve core testing services such as functional testing, performance testing, API testing, security testing, integrating testing, etc. Penetration testing, as the name suggests, is achieved by targeting and exploiting the possible weaknesses in the system. In this section, we will discuss the steps involved in the process of penetration testing.
Also Read: API Penetration Testing: What You Need To Know
STEP 1: Discovery
The first step of a penetration testing process is the discovery of the potential vulnerabilities in the system. It is important to know how the blockchain works in your application in order to secure it.
- The architecture of Blockchain: Try to analyze the blockchain implementation to ensure blockchain’s capability to preserve integrity, confidentiality, and availability throughout the delivery, fulfillment, and storage of data.
- Compliance Readiness: Do not forget to ensure the blockchain implementation complies with the governance legal requirements.
- Readiness Assessment: Also, exert an in-depth glimpse on the technological features of Blockchain application in order to ensure the most beneficial security and practices.
STEP 2: Evaluation
The second step of blockchain penetration testing is the evaluation and analysis of the information gained in the discovery step. The evaluation will help you determine which vulnerability or loophole can put your blockchain application at risk. It involves the following tests:
- Network penetration testing
- Blockchain Static and Dynamic Application Testing including testing wallets, GUI, databases, Application Logic.
- Blockchain Integrity Testing
All the attack vectors mentioned above will be analyzed properly to ensure that security controls are in status to recognize, alleviate, and adequately review access.
Also Read: Why Firewall Penetration Testing is Essential to Your Security Strategy
STEP 3: Functional Testing
Functional testing is performed to ensure that all the services employed in your blockchain application are working as expected. The components taken into consideration by a blockchain penetration tester are:
3.1. Size of the block and chain
A block contains the information of a transaction itself. Currently, the size of a block is 1MB. This value needs to be checked regularly. Also, there is no limit to the size of the chain as it keeps increasing with time. It is important to test the functional performance of the chain to keep it under check.
3.2. Addition of blocks
After the verification and authentication of a transaction, the penetration testers validate the box and adds it to the chain.
3.3. Data Transmission
Blockchain makes it easier for testers to make the encryption and decryption of data flawless because of its peer-to-peer architecture.
3.4. API Testing
API testing is performed to keep a check on the interaction of the Blockchain application ecosystem. It is done to make sure that requests and responses sent by APIs are valid.
3.5. Integration Testing
Integration testing is don’t ensure that different components of the blockchain talk to each other seamlessly. The need for integration testing arises due to the deployment of blockchain across parallel platforms.
3.6. Performance Testing
The purpose of performance testing is to determine potential bottlenecks and to check whether the blockchain application is ready to be pushed into production or not.
3.7. Security Testing
The objective of performing security testing is to ensure that your blockchain application is completely secure against malware and viruses.
STEP 4: Reporting
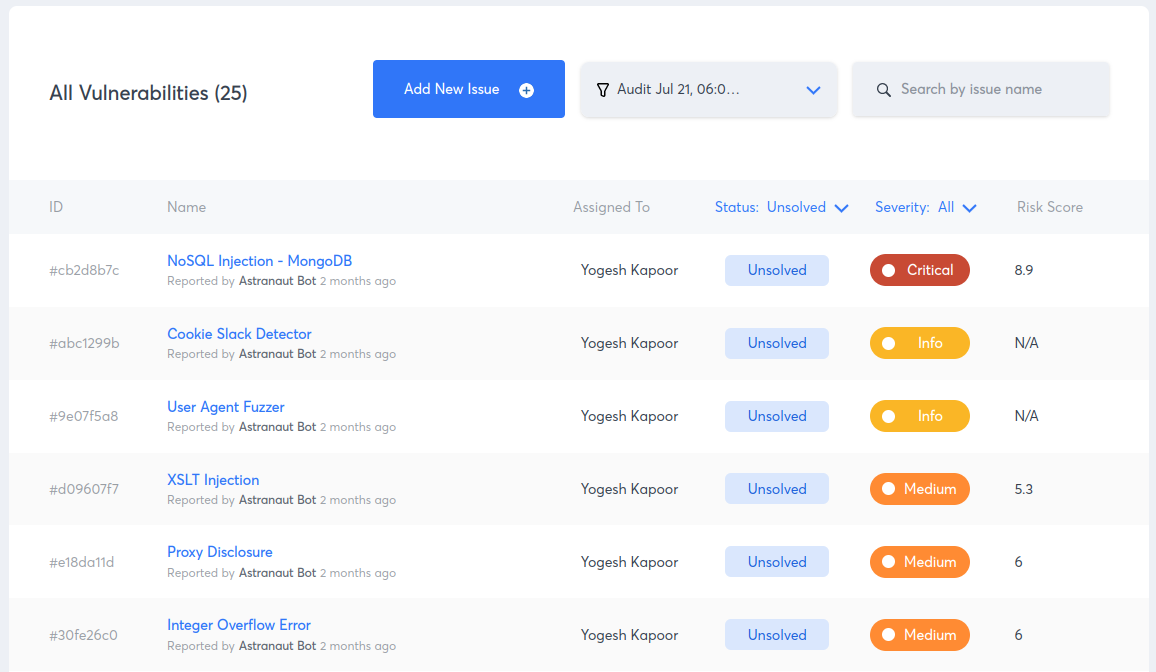
An effective penetration testing is incomplete without a detailed penetration testing report. Make sure that the report contains a detailed outline of each vulnerability found in the blockchain application. A well-explained pentesting report makes it easier for cyber security experts to employ necessary security practices while keeping in mind the found loopholes.
5. Remediation & Certification
The last step in blockchain penetration testing is to remediate the vulnerabilities reported by the security expert and request for a re-scan.
Read Also: Tools for Blockchain Security Testing | 11 Top Penetration Testing Tools/Software of 2022 [Reviewed]
Blockchain penetration testing solution by Astra
Astra offers an in-depth level of blockchain penetration testing with its Astra Pentest solution. The solution includes manual as well as automated vulnerability scanning and an easy-to-use web-ui platform for developers and security engineers for easy vulnerability management.
Here are some features and key highlights of the Astra Pentest solution for blockchain penetration testing:
- Rich-dashboards: Easy-to-use dashboards designed to simplify security.
- Easy collaboration: Options to collaborate with your internal development team and with Astra’s security engineers.
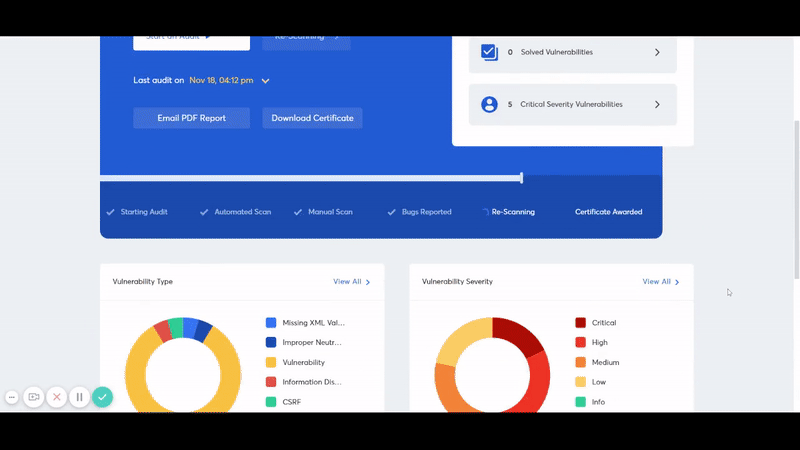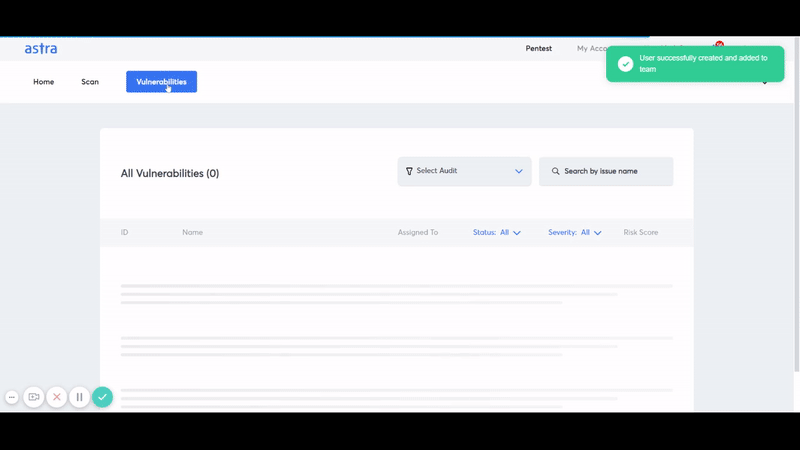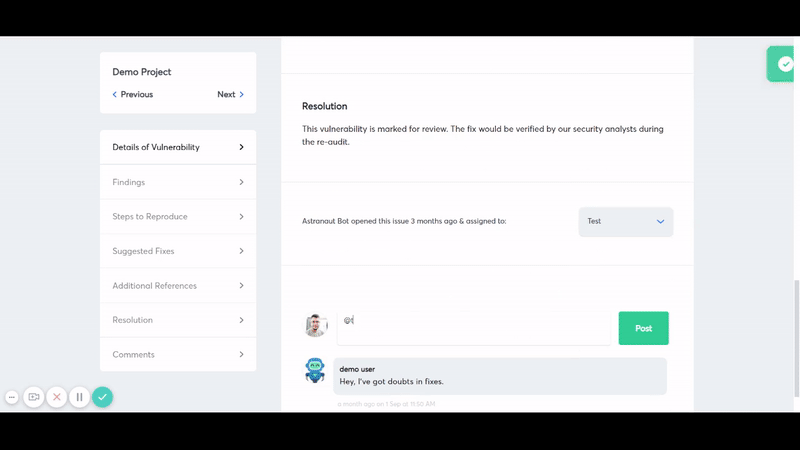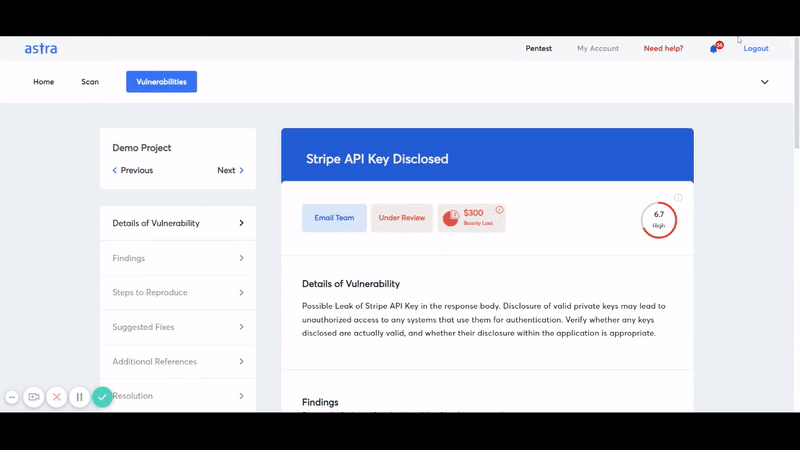
- Automated Scanning: An intelligent automated scanner that performs 2600+ test cases.
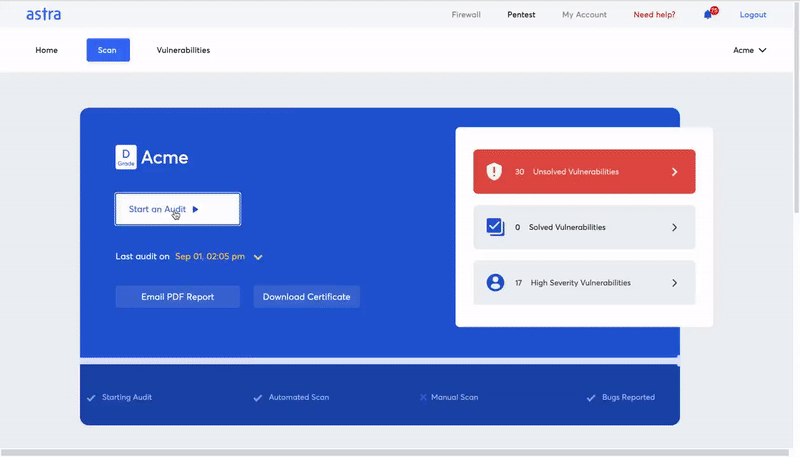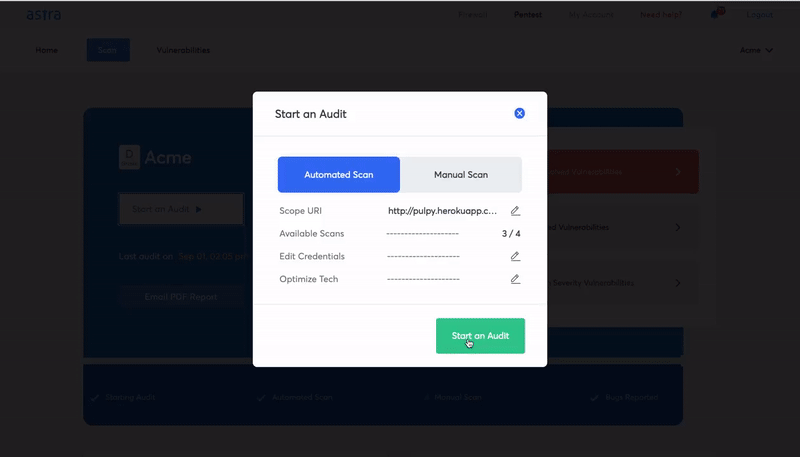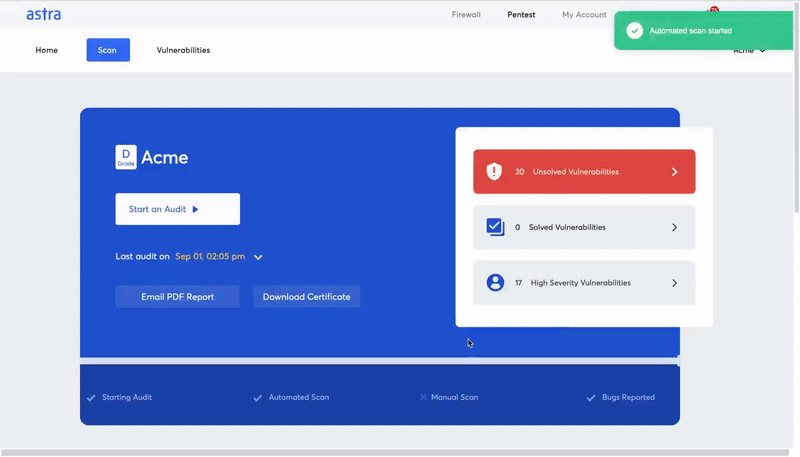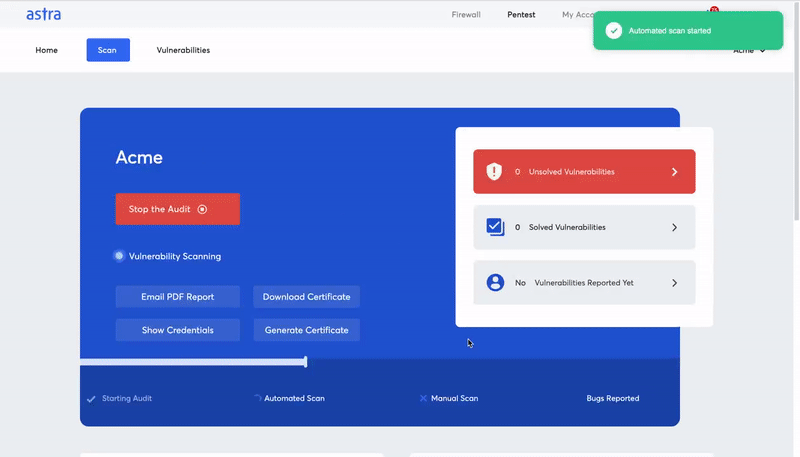
- Risk grading: Risk grading allows management and development team to look at risk factors such as potential loss in dollars, CVSS score, bug bounty amount saved and much more for every single discovered vulnerability.
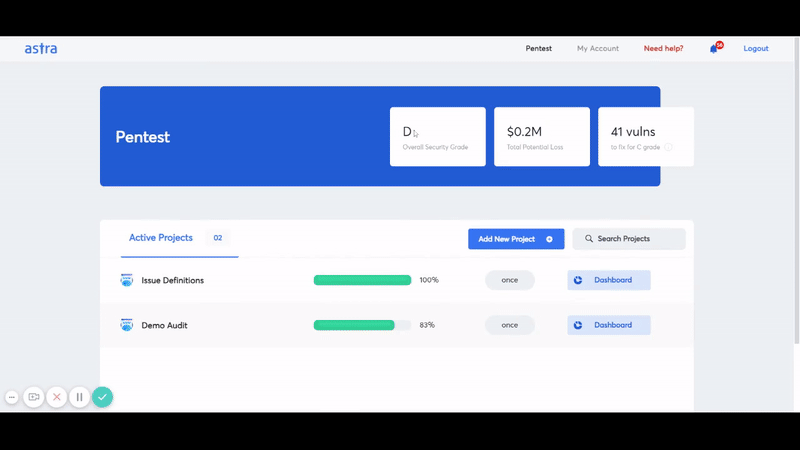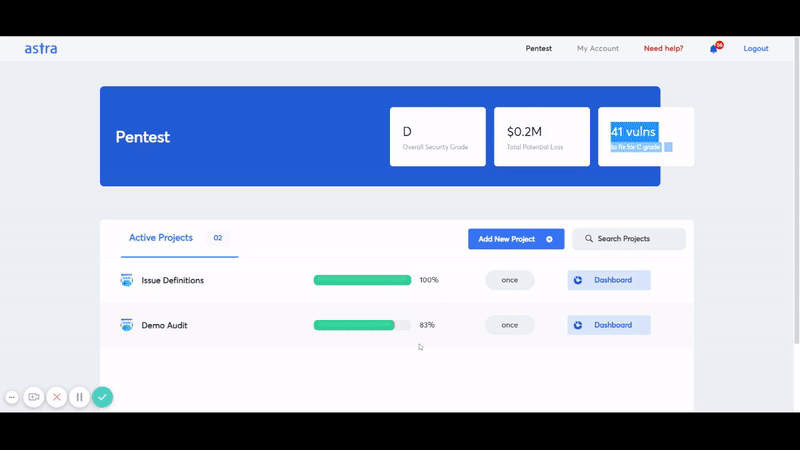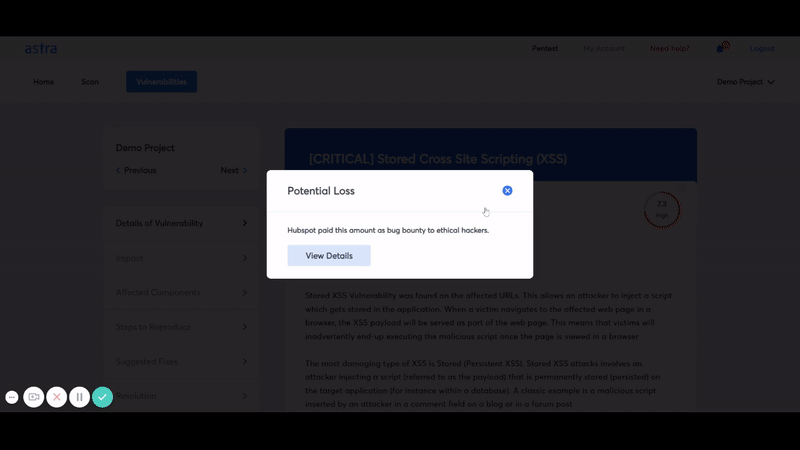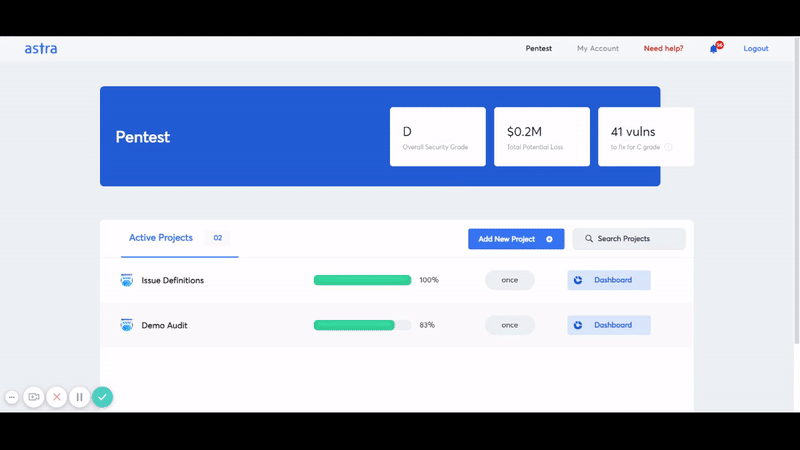
- Detailed In-Dashboard and PDF Reporting: Options to see detailed VAPT reports in dashboard as well as PDF reports in email.
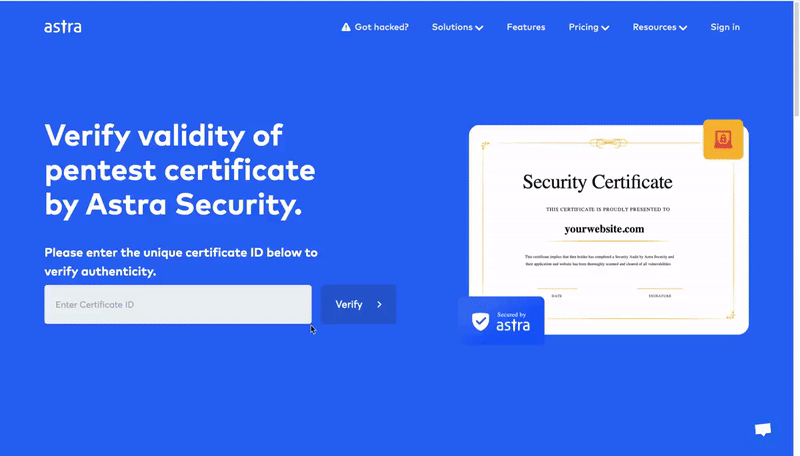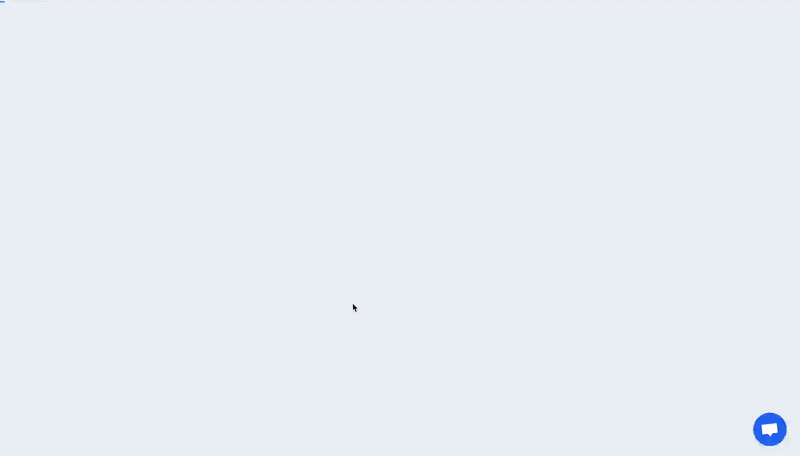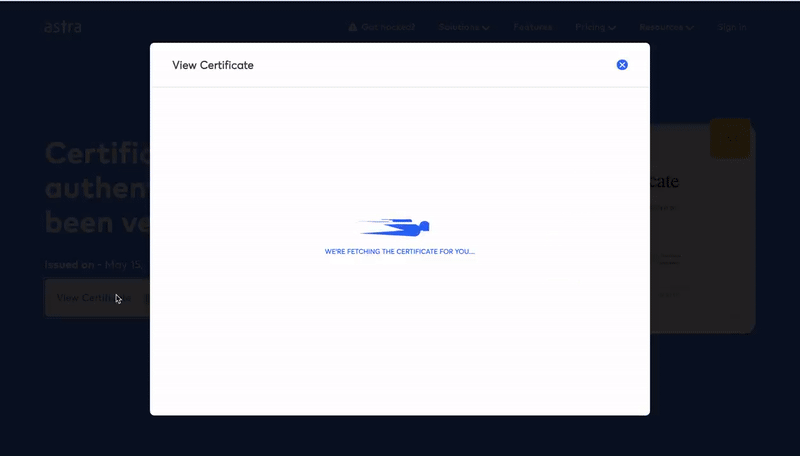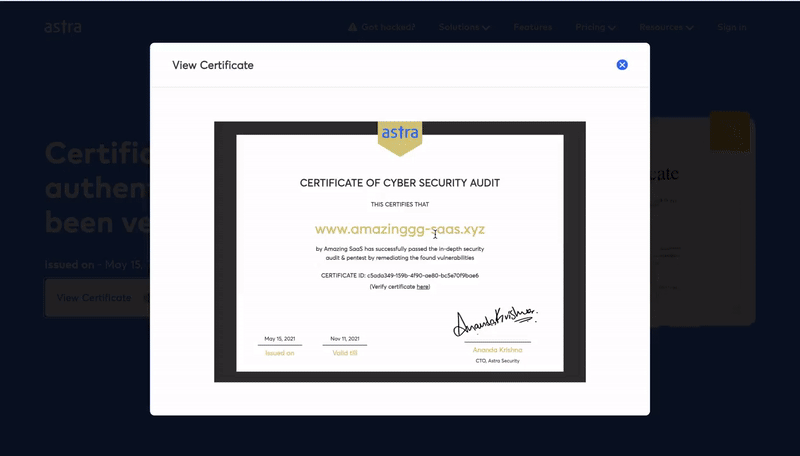
- Publicly verifiable pentesting certificate: After every successful pentest, you get an industry-recognized publicly verifiable pentest certificate.
Conclusion
Blockchain penetration testing is a new and emerging niche in the cybersecurity industry. Since blockchain technology can be used to store any type of data, and this opens up the potential for serious vulnerabilities in the system. Companies are turning to blockchain pentesters in order to find these vulnerabilities before they’re exploited.
















