Azure is a solid and all-inclusive assortment of cloud services that help organizations to conceive, launch, and oversee applications with unparalleled scalability, versatility, and agility. As enterprises migrate their operations to the Azure cloud, the issue of Azure security management gains increasing significance.
Cloud security, posing its unique set of challenges, necessitates thorough planning and persistent vigilance to prevent cyber threats and ensure data confidentiality. Azure security management is engineered to tackle these challenges, providing a wide range of tools and services aimed at safeguarding, identifying, and reacting to potential security hazards. It delivers an integrated and multi-tiered approach stemming from Microsoft’s years of expertise in administering security for global enterprises.
What is Azure Security Management?
Azure security and management is best defined as a comprehensive set of tools and techniques offered by Microsoft that implement a robust and holistic security approach to your cloud infrastructure. Some key components include Azure Security Center, Sentinel, Azure AD, and Azure Key Vault.
It aims to streamline security operations, mitigate risk, and establish a secure foundation for cloud-based operations without compromising the safety of data.
Understanding Azure Security Management
Azure advanced security management is of three segments:
- Azure security
- Azure defender
- Azure sentinel
Azure Security
Azure Security Center acts as a consolidated infrastructure security management system that bolsters the security structure of data centers and offers advanced threat protection spanning hybrid workloads, both in the cloud and on-premises.
With the help of Azure Security Center, organizations can gain a visual representation, exercise control, and enhance the security of their Azure resources. This tool goes beyond mere monitoring and detection.
Azure Security Center facilitates continuous security assessment and practical security recommendations. Its Cloud Security Posture Management (CSPM) features enable effective compliance evaluation, allowing businesses to gauge the overall security condition of their Azure resources at a single glance.
It also encourages secure DevOps by integrating with Azure Pipelines and other CI/CD tools, helping developers incorporate security measures from the initial stages of application development.
Azure Defender
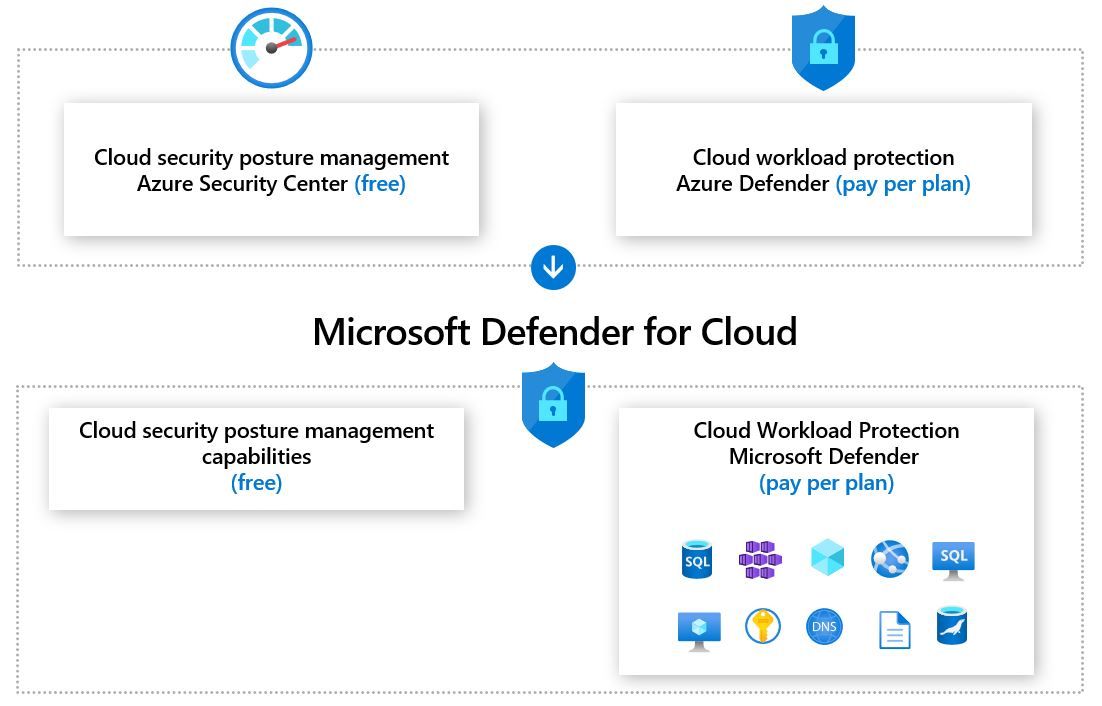
Azure Defender helps safeguard Azure’s resources as well as the hybrid environment. This built-in system offers an extra line of defense by providing threat protection for workloads running not only in Azure but also those located on-premises or in other cloud environments.
Its role is to block a broad spectrum of threats, such as network attacks, phishing attempts, and ransomware incursions. Azure Defender functions on a multi-layered level – it broadens its security measures to encompass the data level by securing crucial components like SQL databases, storage accounts, and Kubernetes deployments.
The tool maintains an active watch on the environment and utilizes the intelligence of machine learning to spot any unusual activities. Upon detection, it sends alerts about potential threats, thereby mitigating any potential damage before it can occur.
Azure Defender is adept at identifying and alerting about an unexpected surge in login attempts or any dubious IP addresses trying to gain access to your databases.
Azure Sentinel
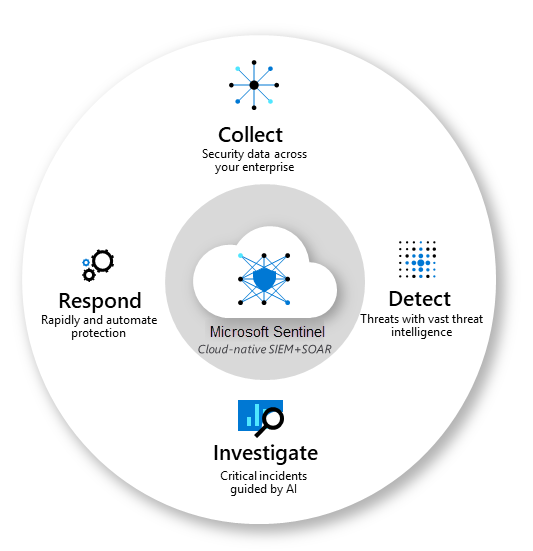
If you imagine your enterprise as a bustling city, Microsoft Sentinel acts as your vigilant, ever-alert police force. It’s a scalable, cloud-native whizz, effectively bringing together two crucial security elements – SIEM (Security Information Event Management) and SOAR (Security Orchestration Automated Response).
Its expertise? Delivering intelligent security analytics for every corner of your corporate cityscape.
Being cloud-native, Sentinel seamlessly ropes in security data from every nook and corner of your organization. Be it from the user working remotely on their device, from the apps they use, the servers humming away in your data center, or from any cloud floating in your digital sky, Sentinel’s got it covered.
Why is Azure Security Management Important?
Did you know? In 2023 alone, according to a recent report, nearly 81% of organizations experienced cloud security incidents in the past 12 months. Moreover, the 2023 Cost of a Data Breach report suggests that the average cost of a cloud data breach exceeds $4.45 million.
Thus, as businesses continue to migrate to cloud-based solutions, with Microsft Azure capturing 23% of the global market, adopting a comprehensive Azure security and data management policy is crucial.
As such, the tools and best practices discussed aim to help strengthen your security, minimize exposure, and maintain compliance with key standards. Moreover, they act as a strategic investment that helps avoid huge costs in compliance and legal fees that come with data breaches.
Key Components of Azure Security Management
Exploring the heart of Azure Security Management, we come across several crucial components that make up its defensive core. These components of Azure cloud security, each playing a unique role, come together to provide a robust shield against the menacing world of cyber threats.
Azure advanced security management is made of 5 components:
- Azure threat protection
- Identity and access management (IAM)
- Information protection
- Security posture management
- Advanced threat analytics
1. Azure Threat Protection
Azure Threat Protection continuously scans your digital resources. It detects threats that may be scattered across different locations and endpoints. It blends smoothly with other Azure services and outside security solutions building a robust line of defense for your organization.
It utilizes sophisticated algorithms to spot unusual and potentially harmful activities. Offering a deep dive into the threats your business faces, it delivers comprehensive reports that encompass the nature of the attacks, the resources that are in the line of fire, and actionable steps to resolve the problem.
The speedy and efficient identification, evaluation, and addressing of threats bolster your organization’s defenses, ensuring your cloud resources stay secure.
2. Identity and Access Management (IAM)
In the digital universe, you have to know who is who, and that’s where Identity and Access Management, or IAM, steps in as a vital part of Azure security management. It ensures that every user is verified and given the right amount of access to resources.
Azure Active Directory (Azure AD) is a one-stop shop for identity and access management in the cloud. It has a suite of security enhancements, such as multi-factor authentication and conditional access policies.
Imagine being able to set rules for users to log in only from certain spots or at specific times; that’s exactly the sort of extra security layer Azure AD is capable of.
3. Information Protection
Azure’s Information Protection is designed as a toolkit of services with a single goal – keeping your data secure wherever it might be. A crucial part of this toolkit is Azure Information Protection (AIP), which relies on labels and policies to support businesses in classifying and protecting their documents and emails.
The application of these labels can be set up in several ways. Administrators can define rules and conditions for automatic labeling, or it could be done manually by users. In some cases, you might even see a mix of both, where users receive recommendations on applying the labels.
If we’re dealing with situations involving data leaks or breaches, AIP jumps into action to shield the data from unauthorized access through encryption. It also keeps an eye on all the activities around shared data, giving organizations the power to withdraw access when they deem it necessary.
In essence, it ensures the right information is accessible to the right people. This goes a long way in reducing the risk of data leaks and helping organizations meet regulatory compliance.
4. Security Posture Management
Managing Azure advanced security management is no small feat, and Azure security management stands tall in this regard. At the core of this setup is something called Azure’s Security Score, a living, breathing evaluation of how well you’re doing on the security front.
The way it works is pretty straightforward. It takes a good look at all your resources and configurations and assigns a score based on how much risk is associated with your current setup. It also offers you clear, actionable steps to bump up that score.
Here’s the cool part: your security score isn’t set in stone. As Azure introduces new security controls, or as you make changes to your cloud resources and configurations, your score updates. This gives you a continually updated snapshot of your security posture.
But the real gold is in the recommendations that come with your Security Score. Follow them and you can step up your security game and reduce the size of the bullseye for potential attacks.
5. Advanced Threat Analytics
Azure’s Advanced Threat Analytics is all about protecting businesses from different types of sophisticated cyber attacks and inside threats.
The way it goes about this is by leveraging machine learning to spot anything out of the ordinary in user activity and any known harmful attacks. It doesn’t just flag these, it dishes out easy-to-understand reports on a neat attack timeline.
The beauty of Azure ATA is that it never stops learning. The more it observes the behavior of your resources, the smarter it gets at adjusting itself. These clear insights from Azure ATA mean your teams can jump into action, dealing with threats swiftly and smartly.
Best Practices for Azure Security Management
Let’s now turn our attention towards the best practices in Azure Security Management. By implementing these practices, organizations can further bolster their security posture and make the most of Azure’s robust security features.
You should implement these best practices after you choose the Azure security tool best suited for your requirements.
Azure security best practices are made of a 4-step Azure security checklist
- Regular security audits
- Implementation of Multi-Factor Authentication
- Least Privilege Principle and Role-Based Access Control (RBAC)
- Utilizing Azure Security Score for Continual Improvement
1. Regular Security Audits
One thing you’ve got to stay on top of is regular security check-ups. These are like your regular dental check-ups but for the health of your Azure setup. With these regular checks, you can spot any potential weak points or security gaps before they turn into full-blown issues.
Two great tools in your arsenal for these check-ups are Azure Policy and Azure Security Center. They can give you the lowdown on how well you’re doing with various compliance standards.
Azure Policy is your go-to for applying your organization’s standards and doing compliance checks at scale. Azure Security Center, on the other hand, gives you a birds-eye view of your security posture, constantly checking and making recommendations.
2. Implementation of Multi-Factor Authentication (MFA)
Let’s talk about Multi-factor Authentication (MFA) next. MFA gives your login process a security boost, making it a tough nut to crack for unwanted intruders. It’s a straightforward and potent method to ramp up the security level of your Azure setup.
Azure Active Directory is all in for MFA. This means that every user, even those with admin privileges, is under its umbrella. The beauty of MFA is that it demands users to show at least two distinct identification proofs before they’re allowed in, thereby ensuring solid access security.
3. Least Privilege Principle and Role-Based Access Control (RBAC)
Essentially, the idea behind the Least Privilege Principle is pretty simple: a user should only have exactly enough access rights or permissions they need to do their job, no more, no less. This strategy can help keep possible harm from mistakes or security incidents to a minimum.
Azure’s advanced security management makes it possible to use Role-Based Access Control (RBAC), which is like your very own access gatekeeper. It lets you assign permissions to users, groups, and applications within a defined boundary.
RBAC is a must-have for organizations aiming to ensure only the right folks get their hands on specific resources and to ward off any unauthorized access to confidential data.
4. Utilizing Azure Security Score for Continual Improvement
Let’s talk about the Azure Security Score again. As discussed before, it’s a nifty tool for keeping tabs on your security posture. A good practice is to frequently check in on your security score and act on the advice it offers to keep bolstering your defenses.
Think of the Azure Security Score as a ‘security health check-up’. It quantifies your current security standing, pointing out what needs your immediate attention. Aiming to keep improving your score should be on the to-do list of every Azure user. It’s like keeping your system in its best shape, always ready to fend off security threats.
Conclusion
Wrapping up, Azure Security Management isn’t just a set of features – it’s a whole fortress designed to shield your digital treasure. From mom-and-pop shops to colossal corporations, it underpins any organization’s cloud cybersecurity game plan. Getting to grips with the key pieces of Azure advanced security management and sticking to smart practices, businesses can confidently navigate the sometimes murky waters of cloud security with Microsoft Azure management tools.
Want to ramp up your defenses even more? Consider pairing Azure’s security suite with Microsoft Azure management tools like Astra Security. Astra is a champ at tackling tricky security issues, helping your organization tick those compliance boxes, and reinforcing your overall security stance. Pairing Azure with Astra, you get a full-fledged cloud security strategy that helps fortify your Azure setup effectively.
Frequently Asked Questions
Frequently Asked Questions
How would you ensure security on Microsoft Azure?
Use strong passwords, enable multi-factor authentication, restrict access, encrypt data at rest and in transit, keep an eye out for suspicious activity, enable backups and disaster recovery, and stay up-to-date on the latest security trends and threats to ensure security on Microsoft Azure.
Depending on whether the workload is hosted on software-as-a-service (SaaS), platform-as-a-service (PaaS), infrastructure-as-a-service (IaaS), or in an on-premises data center, the workload responsibilities change.
When you operate an on-premises data center, you are responsible for the entire stack; however, when you move to the cloud, Microsoft takes on some of your duties.
Adopting a cloud-enabled strategy may free up internal resources and have the cloud provider handle routine security tasks. You own your data and identities for all types of cloud deployments. When combined with cloud-based security features, cloud intelligence can significantly improve the efficiency of identifying and dealing with threats.
Your organization is responsible for ensuring the safety of its information, identities, on-premises resources, and cloud components (which can change depending on the service).
Who can modify security policies in Azure?
Users with the appropriate administrative rights and permissions, such as the “Owner” or “Contributor” roles at the subscription or resource group level, are able to change security policies in Azure. In Azure AD, users who have the “Security Admin” or “Security Reader” roles can also access and manage security rules.