Data, applications, and infrastructure on the Microsoft Azure cloud platform are all protected by a comprehensive set of tools and controls called Azure security. Azure Security offers robust safeguards to lower risks, prevent unauthorized access, find and address security incidents, and ensure regulatory compliance. Azure security best practices checklist provides a secure foundation for businesses to create and implement their applications and services in the Azure environment.
Azure security best practices checklist
Data Encryption
Set up Azure Storage Service Encryption or Azure Disk Encryption to encrypt data at rest for all Azure-stored data.
- The Azure Storage Service Data in Azure storage services is automatically encrypted at rest to give an extra layer of security.
- Data stored in Azure storage services is shielded from unwanted access and potential data breaches by SSE, which makes sure that the data is encrypted at rest.
- SSE eliminates the need for users to manually implement and manage encryption mechanisms.
When transferring data between applications and Azure services, use SSL or TLS to implement encryption in transit.
Use Azure Information Protection to categorize and tag sensitive data and implement encryption and access policies.
Use Azure Disk Encryption, Azure Storage Service Encryption, and Azure SQL Database Transparent Data Encryption to encrypt the disks of virtual machines.
Encryption keys, secrets, and certificates can be securely stored and managed using the Azure Key Vault.
Utilize Azure Information Protection to categorize and label sensitive data, limit access, and automatically encrypt it.
Implement Azure DLP policies to identify and stop the unauthorized or accidental sharing of sensitive information.
Database Security
Secure your Storage Account using Management Plane Security using Azure role-based access control (Azure RBAC).
Use Transport-Level Encryption for Azure File Shares by utilizing HTTPS and the encryption provided by SMB 3.0.
When you need complete control over the encryption keys, use client-side encryption to protect the data you send to storage accounts.
Store and manage cryptographic keys, secrets, and certificates in a secure manner using Azure Key Vault.
To automatically encrypt data in Azure Storage, use Storage Service Encryption (SSE), and to encrypt virtual machine disk files for the OS and data disks, use Azure Disk Encryption for Linux VMs or Azure Disk Encryption for Windows VMs.
You can see if users have used a Shared Access Signature or the storage account keys by using Azure Storage Analytics to track the authorization type, similar to how Blob Storage allows you to do it.
Security Governance and Compliance
Recognize and follow any applicable compliance standards and rules for your sector, such as GDPR, HIPAA, or PCI DSS.
Review Azure compliance documentation frequently to make sure it complies with the standards set by your company.
For security advice, use Azure compliance tools like the Azure Security Benchmark, the Azure CIS (Center for Internet Security) Foundations Benchmark, and the Azure Advisor.
To enforce compliance measures and track compliance status, enable Azure Policy.
Verify compliance by conducting routine audits and assessments and noting gaps or vulnerabilities.
To detect and correct security configuration drift, regularly monitor compliance using Azure Policy, Security Center, and Azure Advisor.
Secure Azure Subscriptions and Resource Groups
Use Azure role-based access control (RBAC) to grant the proper permissions and limit access following the least privilege principle.
Defining and deploying resource configurations using Azure Resource Manager templates ensures secure and reliable setups.
To continuously monitor security, identify threats, and provide security recommendations, implement the Azure Security Center.
To enforce network-level security policies and limit access to Azure resources, use the Azure Firewall or Network Security Groups.
Implement Strong Identity and Access Management
Utilize Azure AD to synchronize your local directory with your cloud directory.
Users can access their SaaS applications using single sign-on using their organizational Azure AD account.
Use the Password Reset Registration Activity report to monitor who is signing up.
Give users access to MFA (multi-factor authentication).
Single sign-on (SSO), multiple-factor authentication (MFA), and conditional access policies are available features.
Ensure PIM can manage and track access to privileged roles, which calls for just-in-time access and approval workflows.
Implement robust password policies, MFA, and Azure AD Identity Protection to identify and reduce identity-related risks.
Applications like Microsoft Security Development Lifecycle (SDL) use secure identity capabilities.
Utilize Azure AD Premium anomaly reports and the identity protection features of Azure AD to actively monitor suspicious activity.
Protect Network Resources
Network-capable devices can communicate using TCP/IP by connecting virtual network interface cards to a virtual network.
Managing essential network services like IP addressing, virtual network and subnet provisioning, and ExpressRoute
ExpressRoute, a virtual network appliance feature and IP addressing administration are all part of network security.
You can see your network and security if you use a shared set of management tools to monitor them.
A simple, unified security strategy lowers errors because it improves both human comprehension and the dependability of automation.
Secure Cloud Applications
Put into practice secure coding techniques like input validation, secure session management, and frequent security code reviews.
To isolate and secure web applications, use ASE, which offers dedicated network connectivity and improved security controls.
To defend web applications against frequent flaws and attacks, use Azure WAF.
Utilize the Security Center to secure your cloud applications through continuous monitoring, threat detection, and recommendations.
Threat Detection and Monitoring
To recognize and react to security threats in real-time, enable the threat detection capabilities of the Security Center.
Use the cloud-native security information and event management (SIEM) tool Azure Sentinel to detect, analyze, and respond to advanced threats.
To gather, examine, and correlate security logs and events from various on-premises and Azure sources, use Log Analytics in conjunction with Azure Monitor.
Incident Response and Recovery
Create a plan for handling security incidents that outlines roles, responsibilities, and channels for communication.
Investigate, contain, and mitigate the incident using the Security Center’s incident response tools.
Put regular backups in place and use Azure Site Recovery for disaster recovery scenarios.
Integrate Azure Sentinel or other SIEM programs to centralize security event logging and facilitate effective incident response.
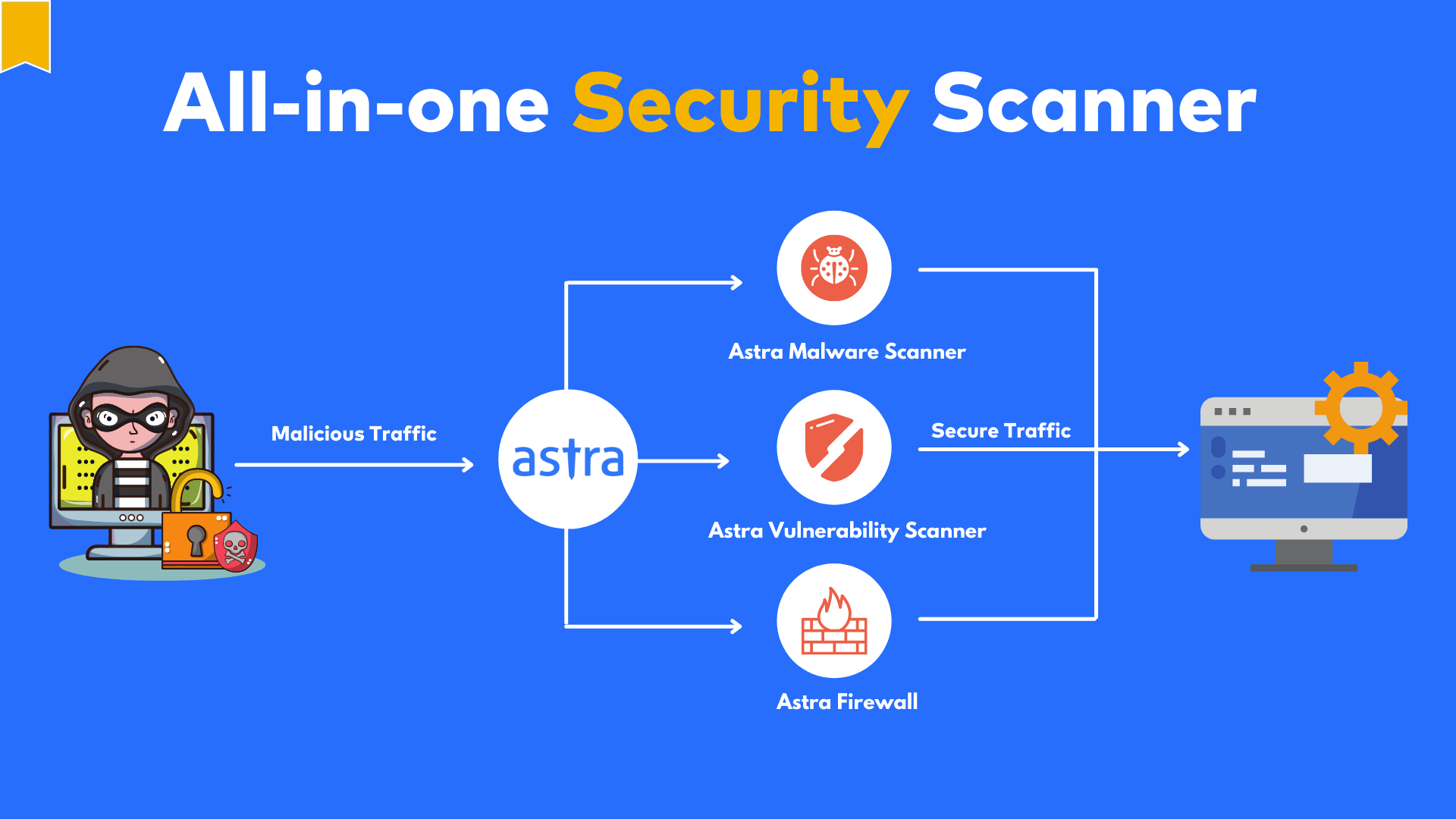
As one of the leading penetration testing companies, Astra Security provides a complete pentest suite that helps companies find potential security flaws, vulnerabilities & loopholes in their system.
Astra Security is a cybersecurity company committed to making security simpler for online businesses by enhancing and testing your measures of data security in Azure.
We offer a complete suite of security tools including a firewall, a malware Scanner, an IP & a Country blocker, to fight off coming attacks & malicious requests on a website or app.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

What is the importance of The Azure cloud security checklist?
Comprehensive Security Coverage
By offering thorough coverage across numerous layers and domains, the Azure cloud security checklist provides a comprehensive approach to security.
Network security, data security, identity and access management, threat detection, and incident response are just a few of the crucial security issues it addresses.
Businesses may use the checklist to ensure that all essential security areas are covered, lowering the likelihood of security problems like unauthorized access and data breaches.
Best Practice Guidance
Based on standards and suggestions from the industry, the Azure cloud security checklist offers helpful best practice advice.
Organizations can use it as a guide when implementing security configurations and controls that adhere to accepted security standards.
There are suggestions on the checklist for securely setting up Azure services like Azure Virtual Machines, Azure Storage, Azure Networking, and Azure App Services.
It advises safeguarding Azure AD, implementing multi-factor authentication, and monitoring Azure resources for potential security incidents.
Risk Mitigation
It is primarily concerned with locating and addressing potential risks and vulnerabilities in the Azure environment.
Organizations can reduce the likelihood and impact of security incidents by implementing specific security measures using the checklist.
The checklist encourages organizations to conduct recurring vulnerability assessments and penetration tests to find vulnerabilities in their Azure deployments.
Security Awareness and Education
The Azure cloud security checklist acknowledges that security awareness and education are crucial to maintaining a secure cloud environment.
It emphasizes how crucial it is for businesses to train staff members in security best practices, make them aware of typical threats, and know how to handle security incidents.
Companies can enable their employees to maintain a secure Azure cloud environment by regularly conducting security awareness campaigns and training sessions.
Standardization and Consistency
For effective security management, standardization is essential, and the Azure cloud security checklist encourages the adoption of standardized security controls and configurations across Azure resources.
To manage and maintain security across various deployments, it offers suggestions for developing uniform security policies and practices.
Organizations can guarantee uniformity in security procedures and lower the risk of misconfigurations by implementing standardized security measures.
Risk Assessment and Prioritization
An emphasis on a risk-based approach to security is made in the Azure cloud security checklist.
Identifying and prioritizing potential threats and vulnerabilities encourages organizations to conduct regular risk assessments.
In this case, Astra security provides a robust VAPT solution with unlimited vulnerability scans with 8000+ tests, integrations with CI/CD tools, Slack, Jira and reporting compliance for SOC2, ISO27001, PCI-DSS, HIPAA and more.
Organizations can effectively allocate their resources by assessing risks and concentrating on the areas with the most significant risks.
Organizations can better understand their unique security requirements by using risk assessments to tailor their security controls.
They can implement the necessary security controls and safeguards to reduce the risks by identifying the essential assets and potential vulnerabilities.
By doing so, you can be assured that your company’s security measures are commensurate with the level of risk you’re willing to take.
Azure Security Audit Checklists
Azure Security Center
By turning on the Azure Security Center, you can see how secure your Azure resources are and get security advice.
Follow the recommendations made by the Azure Security Center to increase the security of your virtual machines, databases, storage accounts, and other Azure services.
Use the JIT access feature of Azure Security Center to restrict temporary access to specific ports for a set amount of time, lowering your virtual machines’ exposure.
Reduce the attack surface of your virtual machines by defining and enforcing permitted application behaviors using the adaptive application controls in Azure Security Center.
Azure Compliance
Determine the particular compliance laws and guidelines that apply to your business, such as GDPR, HIPAA, PCI DSS, or ISO 27001.
Learn about the possibilities for Azure compliance and the services that each certification covers.
Follow Azure’s recommendations for the relevant compliance standards concerning encryption, access controls, data retention policies, and auditing.
Conduct routine audits and assessments to guarantee ongoing compliance with the pertinent laws and standards.
Azure Identity and Access Management (IAM)
To add a layer of security, enable multi-factor authentication (MFA) for user accounts.
Limiting access privileges to what is necessary can reduce the possibility of illicit use.
Review user accounts, roles, and permissions regularly to ensure access is granted following the principle of least privilege and to remove unused tickets.
Use features like Conditional Access policies, Privileged Identity Management (PIM), and Azure AD Identity Protection to improve IAM security.
Azure Network Security
Control traffic to and from your Azure resources, such as virtual machines and subnets, using NSGs.
Use the Azure Firewall or Azure DDoS Protection for network-based attacks to protect your Azure resources.
Create secure connections to your Azure resources using VPNs or Azure ExpressRoute to ensure encrypted communication.
Regularly review network configurations, including firewall rules, to ensure they comply with your organization’s security needs.
Azure Logging and Monitoring
For proactive monitoring and early detection of security incidents, activate Azure Monitor to gather and examine logs and metrics from your Azure resources.
Set up alerts and notifications based on specific security-related events and thresholds to ensure a quick incident response.
Detect security incidents in real-time and take action by utilizing Azure Security Center’s threat detection capabilities.
To gain complete visibility into your environment, use Azure Log Analytics to gather, examine, and correlate logs from various Azure services.
Azure Backup and Disaster Recovery
Automated backups should be created for all your most important Azure resources, including virtual machines, databases, and storage accounts.
Make sure backups are kept for the appropriate amount of time by establishing retention policies that align with your organization’s needs for data protection.
Test your backup and recovery procedures regularly to ensure data integrity and the ability to restart services in an emergency.
Make a thorough plan detailing what to do in a disaster, including communication protocols and failover procedures.
Difference between Azure Security Audit Checklist and Azure Cloud Security Checklist
Azure Security Audit Checklist
- The Azure Security Audit Checklist and the Azure Cloud Security Checklist are separate Microsoft resources for assessing and enhancing the security of Azure cloud environments.
- Despite having the same objective of enhancing security, the two have some significant differences.
- The primary purpose of the Azure Security Audit Checklist is to serve as a comprehensive assessment tool for assessing the security posture of an existing Azure deployment.
- Organizations can use it to evaluate the security effectiveness of their Azure environment by using a comprehensive set of security controls, best practices, and recommendations.
- This checklist addresses several security-related topics, including network security, data protection, vulnerability management, and incident response.
Azure Cloud Security Checklist
- On the other hand, the Azure Cloud Security Checklist is a more proactive and prescriptive tool that offers a set of instructions and suggestions for securing Azure cloud deployments from the ground up.
- During the initial design and deployment phases, it provides a structured method for putting security precautions and configurations in place.
Conclusion
Cloud solutions like Microsoft Azure are rapidly used by organizations, making security a priority. Azure security best practices checklist provides full protection for data and applications. Every kind of business can make use of its many features, including its scalability, adaptability, privacy, and hybrid support. Proactive cloud penetration testing, clear allocation of responsibilities, stringent Identity and Access Management (IAM), and constant monitoring are all examples of best practices. These solutions enable Azure customers to confidently use the cloud, protecting their digital assets. This Azure security best practices checklist ensures that you have all bases covered. Investing for security in Azure cloud is important to ensure overall security posture of your Azure infrastructure.
Frequently Asked Questions
How would you ensure security on Microsoft Azure?
Use strong passwords, enable multi-factor authentication, restrict access, encrypt data at rest and in transit, keep an eye out for suspicious activity, enable backups and disaster recovery, and stay up-to-date on the latest security trends and threats to ensure security on Microsoft Azure.
Depending on whether the workload is hosted on software-as-a-service (SaaS), platform-as-a-service (PaaS), infrastructure-as-a-service (IaaS), or in an on-premises data center, the workload responsibilities change.
When you operate an on-premises data center, you are responsible for the entire stack; however, when you move to the cloud, Microsoft takes on some of your duties.
Adopting a cloud-enabled strategy may free up internal resources and have the cloud provider handle routine security tasks. You own your data and identities for all types of cloud deployments. When combined with cloud-based security features, cloud intelligence can significantly improve the efficiency of identifying and dealing with threats.
Your organization is responsible for ensuring the safety of its information, identities, on-premises resources, and cloud components (which can change depending on the service).
Who can modify security policies in Azure?
Users with the appropriate administrative rights and permissions, such as the “Owner” or “Contributor” roles at the subscription or resource group level, are able to change security policies in Azure. In Azure AD, users who have the “Security Admin” or “Security Reader” roles can also access and manage security rules.