Cloud security is a set of policies, best practices, controls, and technologies used to secure applications, data, and infrastructure in cloud environments. It provides storage and network protection against internal and external threats, access management, data governance and compliance, and disaster recovery.
Companies require agility and flexibility needed to accelerate innovation and meet the expectations of today’s modern consumers. Migrating to more dynamic cloud environments requires new approaches to security to ensure that data remains secure across online infrastructure, applications, and platforms.
In the last 18 months, 79% of companies have faced at least one cloud breach. 88% of cloud data breaches are caused by human error.
Organizations need to implement effective cloud security policies, best practices, controls, and technologies to protect their applications, data, and infrastructure from internal and external threats. Additionally, they need to invest in cloud security skills and solutions that can help them monitor, manage, and secure their multi-cloud environments.
What is Cloud Security?
Cloud security is dedicated to protecting cloud computing systems and resources. This includes keeping data private and secure across various online-based infrastructure, applications, and platforms. Securing these systems involves collaborative efforts of both cloud providers and the clients that use them, whether an individual, small or medium business, or enterprise uses.
Security architecture in cloud computing consists of:
- Data security
- Identity and access management
- Governance
- Data retention
- Legal compliance
Cloud Security vs Traditional IT Security
Cloud security and traditional IT security are both methods of protecting data, resources, and applications from unauthorized access, malicious attacks, and other threats.
| Cloud Security | Traditional IT Security |
| Uses cloud-based services and tools to secure data and applications that are stored and accessed on the internet | Uses physical hardware and software to secure data and applications that are stored and accessed on local networks and servers |
| Scalable, flexible, and cost effective by utilizing automated backup and recovery options which can reduce the risk of data loss or corruption | More rigid and requires manual intervention and additional investment to protect against evolving threats |
| Relies on a data-centric approach to prevent unauthorized access, which includes data encryption, authorization processes, multi-factor authentication and throughput security. | Relies on a perimeter security model, which controls access through firewalls, antivirus software, and other defenses. |
| Requires a shared responsibility model between the cloud service provider and the cloud user. The cloud service provider is responsible for securing the cloud infrastructure, platform, and software, while the cloud user is responsible for securing the data, applications, access that they use on the cloud. | Requires a sole responsibility model where the organization is responsible for securing all aspects of their IT environment. |
Both cloud app security and traditional IT security have their advantages and disadvantages, depending on the needs and preferences of your organization. However, cloud security is becoming more popular and prevalent as cloud computing offers many benefits and opportunities for businesses.
Cloud Computing Security: Layers and Differences
Cloud and traditional computing follows a logical model with four layers:
- Infrastructure
- Metastructure
- Infostructure
- Applistructure
Cloud metastructure has network-enabled and remotely accessible management plane components.
Cloud has two sublayers for each layer. For example, infrastructure hsa physical and virtual sub-layers. In the private cloud, the same organization manages both; in the public cloud, the provider manages the physical sublayer and you manage the virtual sub-layer. This affects the security responsibilities and practices of each party.
The metastructure layer has the most obvious and immediate security management differences, but cloud also differs from traditional computing in the other layers. The scale and nature of the differences on the cloud platform and the cloud usage.
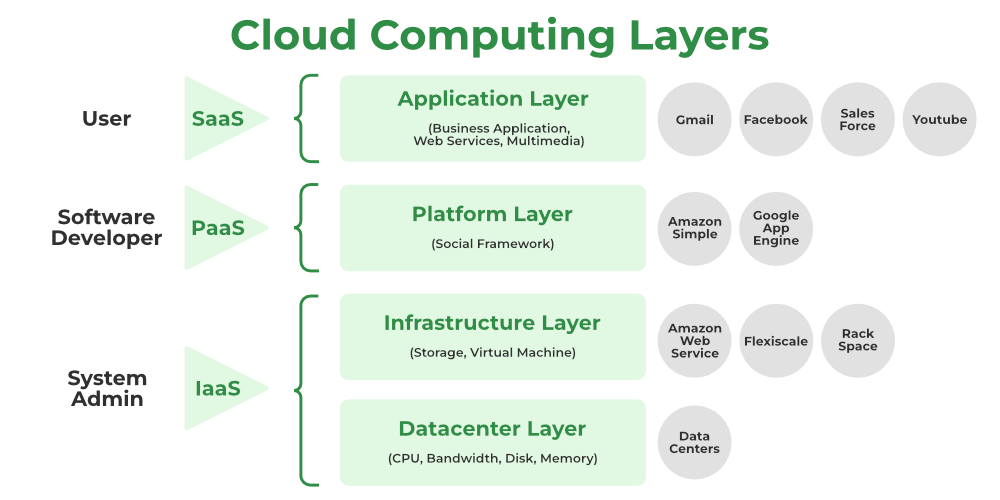
How does Cloud Security Work?
Security management in the cloud depends on the type of cloud computing service model you use and the shared responsibility model you’ve established with your cloud service provider (CSP).
The more the CSP manages, the more they can generally protect.
In IaaS, you are responsible for securing your data, applications, virtual network controls, operating system, and user access. The CSP secures compute, storage, and physical network, including all patching and configuration.
In PaaS, you only need to secure your data, user access, and applications. The CSP will take care of the rest.
In SaaS, you only need to secure your data and user access. The CSP will manage the applications and the underlying infrastructure.
A new model is emerging – shared fate model. In this, the CSP provides more comprehensive guidance, resources, and tools to help customers sustain secure use of the cloud.
How do CSPs maintain security in cloud computing?
Cloud security solutions are tools and services that help you implement policies, processes, and technologies to secure your cloud environment.
Identity and access management (IAM)
IAM services and tools allow administrators to centrally manage and control who can access what resources in the cloud. IAM also enables authentication and authorization mechanisms such as passwords, tokens, biometrics, or multi-factor authentication.
Data loss prevention (DLP)
DLP solutions help prevent data breaches by monitoring, detecting, and blocking sensitive data from leaving the cloud environment or being accessed by unauthorized users.
Encryption
Encryption is the process of transforming data into an unreadable format that can only be decrypted by authorized parties. Encryption helps protect data at rest (stored in the cloud) or in transit (moving between devices or networks) from unauthorized access or modification.
Firewall
A firewall is a network security device that monitors and filters incoming and outgoing traffic based on predefined rules. It helps prevent unauthorized or malicious traffic from reaching your cloud resources or applications.
Intrusion detection and prevention systems (IDS/IPS)
IDS/IPS are network security tools that monitor and analyze network traffic for signs of malicious activity or policy violations. IDS/IPS can alert administrators or take action to block or mitigate potential threats.
Security information and event management (SIEM)
SIEM is a software solution that collects, analyzes, and correlates data from various sources such as logs, events, alerts, or incidents across the cloud environment. SIEM helps provide visibility into the security posture of the cloud environment and enables threat detection and response.
What is the difference between cloud server security and cloud computing security?
Both of these concepts are related but are not identical. Cloud server security is an aspect of cloud computing security. It focuses on protecting the data and information stored on cloud services from unauthorized access, misuse, malware, or online attacks.
Cloud computing security, on the other hand, is a broader term that refers to all security measures and practices that apply to cloud-based applications, data, and infrastructure.
| Cloud Server Security | Cloud Computing Security |
| This is concerned with securing the cloud infrastructure layer which includes the physical servers, virtual machines, storage devices, and network components that host and deliver cloud services. | Cloud computing security also covers the higher layers of the cloud stack such as the platform layer (PaaS), the application layer (SaaS, and the data layer. |
| It is more dependent on the type of cloud deployment model such as public, private, hybrid, or community clouds. Different deployment models have different levels of control and responsibility for the customer and the CSP over the cloud servers. For example, in a public cloud, the CSP is responsible for securing the cloud servers, while in a private cloud, you have more control and accountability over the cloud servers. | Cloud computing security is more influenced by the type of cloud service model, such as IaaS, PaaS, or SaaS. Different service models have different implications for the customer and the CSP over the security of the cloud applications, data, and platform. |
| This requires more technical skills and knowledge to implement and manage than cloud computing security. It involves configuring and maintaining firewalls, encryption, IDS/IPS, IAM, DLP, and other tools and technologies to protect the cloud servers from internal and external threats. | This also requires some technical skills and knowledge, but it also relies on following best practices, policies, standards, and regulations to ensure compliance and governance of the cloud environment. |
What are the top 5 challenges in secure cloud computing?
Cloud computing poses some significant security challenges that need to be addressed and mitigated. Some of the top security challenges in the cloud are:
- Misconfiguration: This occurs when cloud resources are not configured properly leaving them vulnerable to unauthorized access, data leakage, or malicious attacks. These can be caused by human error, lack of awareness, or complexity of cloud environments.
- Unauthorized access: This is when an attacker gains access to cloud resources or data without proper authorization, either by exploiting vulnerabilities, stealing credentials, or bypassing authentication mechanisms. Unauthorized access can result in data theft, data manipulation, ransomware attacks or denial-of-service attacks.
- Insecure interfaces: This occurs when the interfaces or APIs that are used to interact with cloud services are not secure allowing attackers to intercept, modify, or inject malicious data or commands. Insecure interfaces can also expose sensitive information or functionality that should not be accessible to unauthorized users.
- Account hijacking: This is when an attacker takes over a legitimate cloud account and uses it for malicious purposes. These can be for launching attacks, stealing data, or abusing resources. Account hijacking can be achieved by phishing, keylogging, credential stuffing, or social engineering. This is the most serious issue in cloud computing.
- Multi-cloud challenges: This occurs when an organization uses multiple cloud service providers for different purposes. It increases the complexity and diversity of your cloud infrastructure. Multi-cloud environments can have advantages such as redundancy, performance optimization, and cost reduction. But they also introduce new security challenges such as data protection and privacy, compliance, visibility and control, and interoperability.
Best Practices in Cloud Computing and Security
To achieve enterprise-grade cloud workload protection from breaches, data leaks, and targeted attacks in the cloud environment, you need to combine the cloud native security features and services offered by cloud providers such as AWS, Azure, and GCP with additional third-party solutions. This will allow you to implement the following industry best practices:
- Use group-based and role-based IAM and authentication controls across complex infrastructures, and grant only the minimum necessary access privileges to assets and APIs. Enforce strong password policies, permission time-outs, and multi-factor authentication for higher privileges.
- Deploy your critical resources and apps in isolated sections of the cloud network, such as VPCs or vNETs, and use subnets to create micro-segments for different workloads. Apply granular security policies at subnet gateways, and use dedicated WAN links and static routing configurations for hybrid architectures.
- Use Cloud Security Posture Management tools from third-party cloud security vendors to consistently apply governance and compliance rules and templates when provisioning virtual servers, audit for configuration deviations, and remediate automatically where possible.
- Protect all your applications (especially cloud-native distributed apps) with a next-generation WAF that can inspect and control traffic to and from web application servers, update WAF rules automatically based on traffic behavior changes, and deploy closer to microservices that are running workloads.
- Encrypt your data at all transport layers, use secure file shares and communications, manage compliance risk continuously, and maintain good data storage resource hygiene by detecting misconfigured buckets and terminating orphan resources.
- Use threat intelligence tools from third-party cloud security vendors to add context to the cloud-native logs by cross-referencing aggregated log data with internal and external data sources. Use tools that help visualize and query the threat landscape and promote quicker incident response times. Apply AI-based anomaly detection algorithms to catch unknown threats, and perform forensics analysis to determine their risk profile. Receive real-time alerts on intrusions and policy violations, and trigger auto-remediation workflows where possible.
How does Astra secure your cloud infrastructure?
Astra Security is a comprehensive suite of cloud security solutions that can help companies implement these pillars effectively.
Some of the features and benefits of Astra Security are:
- Web app pen testing: Astra Security can perform automated, continuous, and on-demand penetration testing of web applications hosted in the cloud. It can identify and report various security issues, such as misconfigurations, vulnerabilities, malware infections, etc. It can also provide recommendations and fixes for improving the security posture of the web applications.
- Cloud security pen testing: Astra Security can also perform penetration testing of cloud infrastructure and services. It can assess the security of cloud platforms (such as AWS, Azure, GCP), cloud storage (such as S3 buckets), cloud databases (such as MongoDB), cloud APIs (such as RESTful APIs), etc. It can also provide insights and guidance for enhancing the security of the cloud environment.
- Mobile app pen testing: Astra Security can also perform penetration testing of mobile applications that interact with cloud resources. It can evaluate the security of mobile platforms (such as iOS, Android), mobile frameworks (such as React Native), mobile APIs (such as GraphQL), etc. It can also provide suggestions and solutions for securing the mobile applications.
- API pentest: Astra Security can also perform APIs penetration testing of that are exposed or consumed by cloud applications. It can analyze the security of API endpoints (such as GET, POST), API parameters (such as headers, body), API responses (such as JSON), etc. It can also provide tips and tools for protecting the APIs from attacks.
- Secured by Astra seal: Astra Security can also provide a seal of trust that can be displayed on the websites or applications that use its services. The seal can validate the security level of the websites or applications and increase customer confidence and conversion rates.
Astra Security is a powerful and flexible cloud security platform that can help companies achieve robust standard cloud security by addressing all the six pillars mentioned above. By using Astra’s cloud security services, companies can gain visibility into their data and assets in the cloud and protect them from various threats.
Frequently Asked Questions
What to look for in cloud security?
Cloud security is a complex and evolving topic that requires careful consideration and planning. Some of the factors to look for in cloud security are:
1. The type and level of security offered by the cloud service provider, such as encryption, firewalls, intrusion detection and prevention, compliance, etc.
2. The shared responsibility model between the cloud provider and the customer, and the clarity of roles and expectations for each party.
3. The identity and access management policies and tools that control who can access the cloud resources and how.
4. The data protection measures that ensure the confidentiality, integrity, and availability of data in transit and at rest.
5. The monitoring and auditing capabilities that provide visibility and accountability of cloud activities and events.
What are common cloud computing security risks?
Common Cloud Computing Security Risks
1. Security system misconfiguration.
2. Denial-of-Service (DoS) attacks.
3. Data loss due to cyberattacks.
4. Unsecure access control points.
5. Inadequate threat notifications and alerts.
What is the role of cloud security?
Cloud security involves identifying and mitigating potential cloud-based security risks and developing and implementing security controls for the cloud, such as access control, data encryption, and network security. Other typical tasks are: Ensuring compliance with relevant security regulations and standards.
















