Cloud-native services are increasingly relied on for building and running applications rather than having on-premise data centers. This is because it is more economical in terms of security, maintenance, and capacity. Cloud-native security is an important consideration for users since the protection of the codes, applications, and customers’ data is heavily dependent on it.
This article discusses the cloud-native security strategies, the four important layers that need protection, and a tool that provides a comprehensive solution for cloud-native security. The benefits of cloud-native application security are also mentioned.
Action Points
- Cloud native security is the integration of security measures and protocols into the software development lifecycle of an application hosted in the cloud.
- Top cloud native security strategies to implement include the shared responsibility model, shift left approach, and security testing.
- Major components of cloud infrastructure that require security controls are the cloud, clusters, containers, and code. The code layer offers the most amount of security controls.
- Use Astra Security to carry out cloud and application penetration tests, cloud configuration reviews, and source code reviews.
- Astra Security’s security testing services can be easily integrated into your cloud native application’s SDLC (software development lifecycle).
What Is Cloud Native Security?
Cloud native security refers to the integration of security in the development strategy of applications built and hosted in the cloud. This refers to addressing the cloud architecture, development teams, infrastructure, and processes involved in building secure cloud native applications. The cloud native architecture includes applications, storage containers, and codes.
Must-Have Cloud Native Security Strategies
Ensuring steady security for applications and their components on the cloud is crucial for a company’s business continuity, stability, and success. Some of the approaches taken to cloud-native security include:
Cloud providers and users are equally responsible for the security of the platform, applications, codes, and customer data in it. Cloud-native application developers should have a better idea of secure coding practices while security teams should know the tools and processes used to code and deploy applications. This tandem approach to each team’s operations can help integrate and manage cloud-native security better.
Shift Left Approach
The shift left approach is a cultural shift in the IT industry that is happening and being encouraged due to the higher importance it places on security and its automation throughout the software development lifecycle (SDLC). Essentially it helps companies move from DevOps to DevSecOps by applying security measures like vulnerability scanning & pentesting earlier during app development. This reduces the chances of faulty codes and other vulnerabilities in the software.
Security Testing
Application codes can often contain faults or vulnerabilities that if not tested, will end up in production resulting in buggy software. When building cloud-native applications a thing to keep note of is network security. Therefore testing out app codes, the applications and the networks with thorough pentests can help in the early detection & mitigation of vulnerabilities in your application. This in turn reduces the chances of a data breach or leak.
4 C’s of Cloud Native Security Architecture
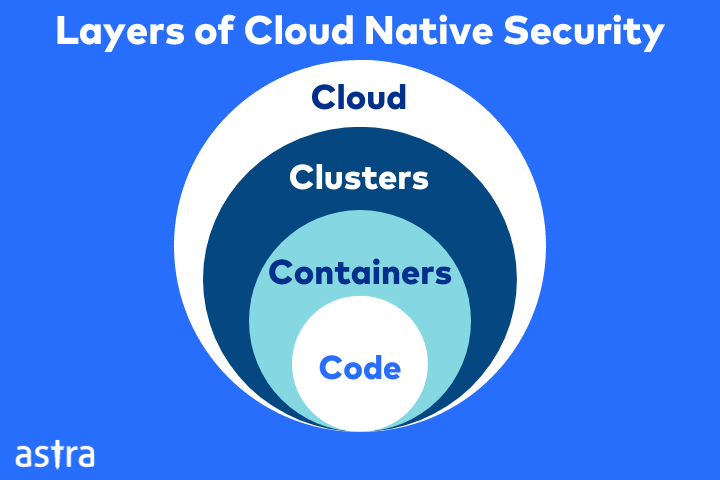
The above-mentioned strategies for security in cloud apps have to be implemented at various levels to provide holistic security for your company. These levels include clouds, clusters, containers, and code.
Cloud
The first C in Cloud Native Security stands for the cloud itself. It refers to the infrastructural security provided by your cloud service provider. However, the responsibility for the configuration of the security for your applications, servers, and data falls on you. This is known as the shared cloud responsibility model.
Issues that affect cloud platforms commonly include misconfigurations and attacks that can be inflicted manually or through automated tools. Not configuring the security settings properly or placing improper access control measures can lead to such exploits.
Clusters
Applications that are containerized are run with the help of nodes called clusters. Clusters allow the easy development, movement, and management of applications in containers. It is important to protect and manage access for Kubernetes clusters.
Clusters have many pods that can freely communicate with each other. If an attacker gains access to one pod, it can easily affect the rest of the cluster as well thus putting the whole cloud native application at risk. Protecting clusters can be done by:
- Placing restrictions on network traffic
- Encrypting data traffic
- Authenticating users
- Adopting the principle of least privilege to limit access
Containers
Containers are lightweight, portable, and isolated application runtimes orchestrated by container orchestration systems like Kubernetes. The vulnerabilities in the container layer often lie in the container images which can be scanned. Companies often overlook image security and privilege configurations leading to the exposure of containers.
To avoid this, it is important to keep your application containers updated regularly. Carrying out vulnerability scans using reputed tools like Astra Vulnerability Scanner can also go a long way in the detection of any container vulnerabilities. Lastly, ensure that images used or built come from trusted sources.
Code
The code layer refers to the software applications and microservices that run within containers in a cloud platform. Because of this, it is also known as the application layer. This is the layer that provides the most security control for companies. Analyzing a software application during its SDLC (software development lifecycle) allows you to detect and resolve a lot of security issues.
In protecting the code layer monitoring and restricting endpoint access, encryption of data at rest and in transit, and carrying out code analysis come into play. Security risks such as insecure codes, cross-site scripting attacks, and other vulnerabilities can be detected.
Astra Security – Top Notch Cloud Native Security Tool
Astra Security is a vulnerability assessment and penetration testing company that provides round-the-clock security testing services to assess cloud native assets for the detection of vulnerabilities.
Application Penetration Testing
Astra Security provides both manual and automated penetration testing for assets in the cloud. Our intelligent vulnerability scanner is capable of testing for 8000+ vulnerabilities and is deployed to detect and identify vulnerabilities.
In Astra’s cloud penetration testing, vulnerabilities are exploited manually by Astra’s experienced pentesters or through automated pentesting. Brute forcing, fuzzing, and injections are some of the tests carried out on the vulnerability to try further access.
Vulnerability Scans
Astra provides automated vulnerability scans. These scans are comprehensive and personalized per customer requirements. Automated vulnerability scans by Astra Vulnerability Scanner are further available in three different categories.
- Lightening: Super quick scan for vulnerabilities that takes around 9-10 minutes.
- Emerging: Targeted scans that check for the emerging or latest vulnerabilities mentioned in the world of cyber security.
- Full Scans: Complete in-depth automated scans that scan for well-known vulnerabilities, CVEs, OWASP Top 10, SANS Top 25, and newer ones from bug bounty reports.
Cloud Configuration Reviews
Expert security analysts at Astra conduct a thorough review of your cloud configuration to find any misconfigurations or security vulnerabilities. The review also ensures that you are following the latest and best cloud security practices to ensure protection against any potential threats. Your cloud implementation and security controls are also checked to provide further recommendations if required.
Detailed Pentest Reports
Astra’s pentest reports can be downloaded in multiple formats including PDFs, and XLS. It is a detailed document that provides an executive summary of vulnerability findings with their risk level and CVSS scores. The report is customized to be easy to understand for all parties involved from CXOs, and CTOs to security teams.
Publicly Verifiable Pentest Certificates
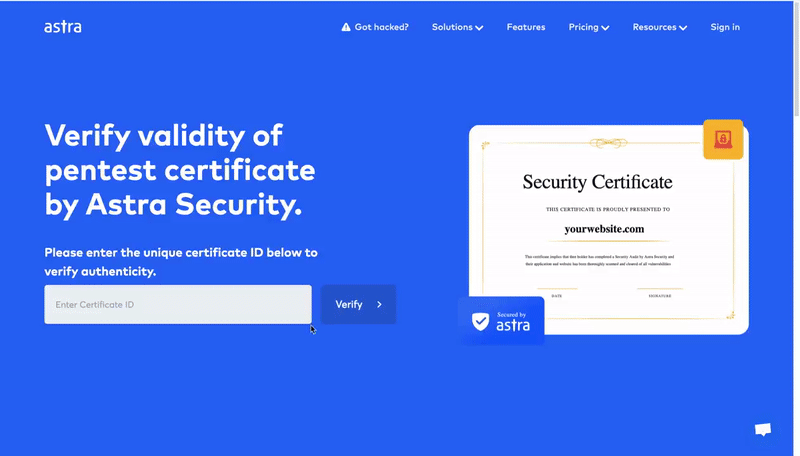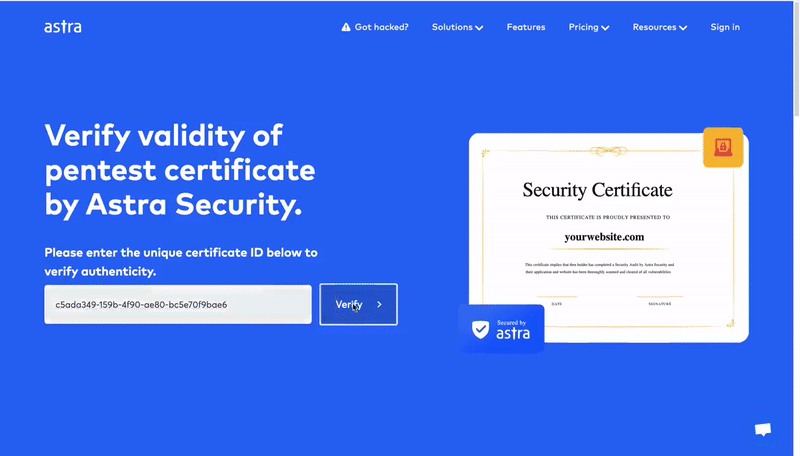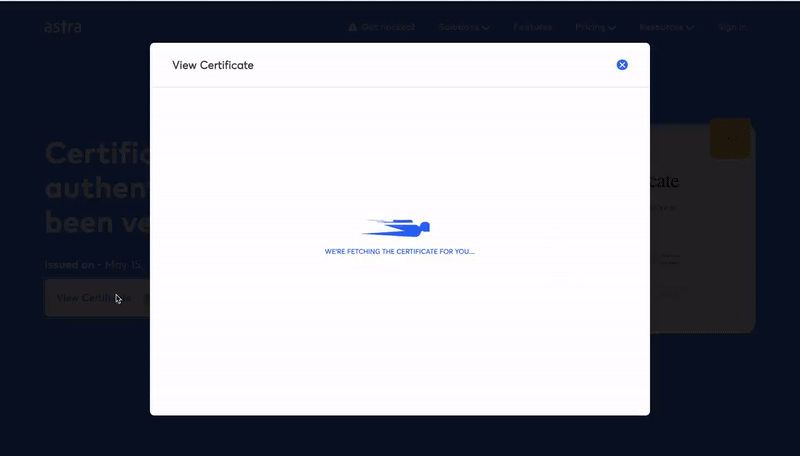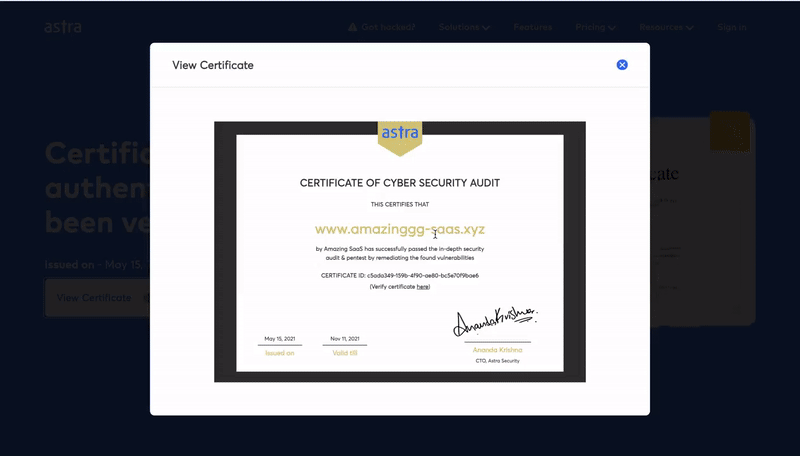
Astra provides a Pentest Certificate which can be publicly verified by the target’s customers to ensure the validity and security standards of the organization. The certificate is only provided upon successful remediation of all vulnerabilities and is valid for 6 months or until the next major code update, whichever is earlier.
CXO-friendly Dashboard
Astra Pentest boasts an easy-to-navigate CXO-friendly dashboard that displays the vulnerabilities detected in the cloud application in real time. Members of the development team can be added to the dashboard to collaborate with pentesters for quicker vulnerability resolution.
The dashboard also offers the option to comment under each vulnerability so that the development team can clear queries quickly. Customers can also track the progress of the manual scans & ETA from the dashboard.
CI/CD Integrations
Astra Security provides integrations with multiple project development tools & web repositories like GitHub, GitLab, Jenkins, Circle CI, and BitBucket. It also provides integrations with project management platforms such as Jira and Slack. These integrations allow scanning applications in the cloud for vulnerabilities during their development phase.
Benefits of Cloud Native Security
Here are some key benefits of cloud native security:
- Cloud native security ensures the scalability of security measures along with the applications and cloud infrastructure.
- It is flexible for the dynamic nature of cloud platforms.
- Provides automation of cloud security management policies and threat response.
- It reduces the cloud attack surface by isolating resources into clusters and containers.
- Provides enhanced security for containers and images through scanning.
- Can be easily integrated into the SDLC.
- Provides real-time vulnerability scanning and monitoring.
Conclusion
Integration of cloud native security into the development strategy of a cloud native applications is quickly becoming paramount due to the ever-increasing threats in the cyber landscape. It is prudent for you as a software developer or cloud provider to know and implement crucial security strategies such as the shared responsibility model, shift left approach, and security testing.
Using a comprehensive cloud security tool like Astra Security can help you fortify the cloud and code layers of your cloud native security through source code reviews, cloud configuration reviews, vulnerability scans, and pentests.
FAQs
What are the three R’s of native cloud security?
The three R’s of native cloud security are:
1. Rotate: Frequently rotate your credentials such as passwords, tokens, and encryption keys.
2. Repair: Repair vulnerable systems, applications, and their components as soon as patches are available to reduce the chances of business downtime or a break in business continuity.
3. Repave: Repave and rebuild your applications and containers to reduce the chances of vulnerabilities and subsequent exposure.
What are common security challenges in containerized environments?
Common challenges include securing container images, ensuring isolation between containers, managing encryption keys, and protecting against privilege escalation and other forms of attacks.
What cloud-native security tools and services are available from major cloud providers?
Major cloud providers, such as AWS, Azure, and Google Cloud, offer a range of security tools and services like AWS Identity and Access Management (IAM), Azure Security Center, and Google Cloud Security Command Center, among others, to enhance cloud-native security.
















