Today’s cybercriminals are constantly seeking new techniques to infiltrate security defenses of of software by exploiting hidden vulnerabilities and misconfiguration errors present in them. To counter this, organizations are carrying out regular vulnerability scans. And this is helping them discover and remediate potential vulnerabilities before hackers take advantage of it to break in and steal sensitive data in the software.
Vulnerability scanning has become a critical element in the organizations’ security program. In this article, we will discuss this along with its overview including, its importance and how it can help improve security. We will also discuss some of the challenges associated with vulnerability scanning, and finally a vulnerability scanning process.
So, let’s dig in!
What does vulnerability scanning actually mean?
In simple terms, vulnerability scanning is the process of identifying and assessing security weaknesses in computer systems, networks, and applications. Vulnerability scanners can be used to scan for a wide range of vulnerabilities, including weak passwords, unpatched software, open ports, etc. And today’s organizations are rigorously doing vulnerability scans to prevent massive data breaches and hacking attacks on their IT and internet-facing assets.
Also Read– Docker Hub Vulnerability Scanning
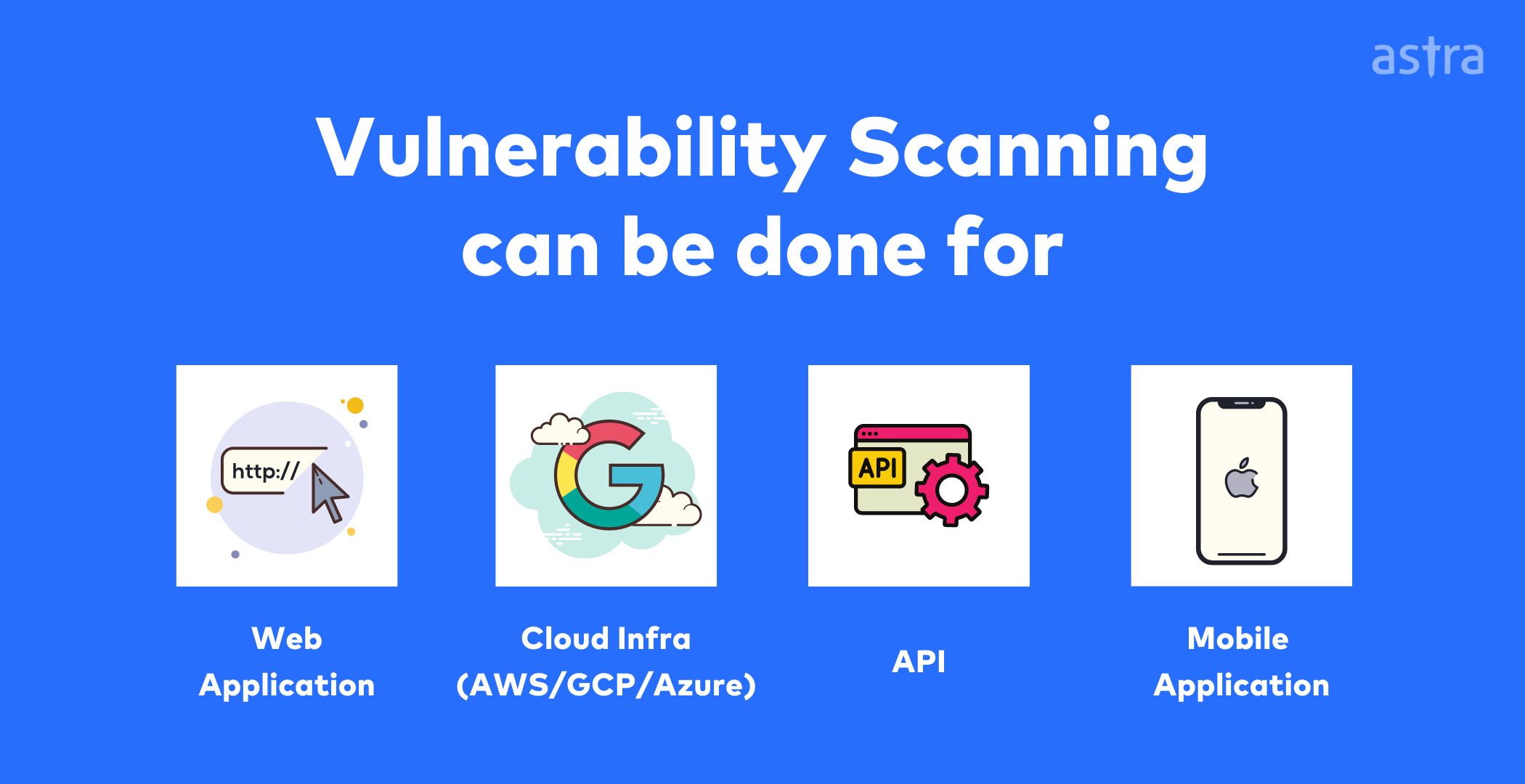
Why is vulnerability scanning important?
There are several reasons why vulnerability scanning by managed vulnerability scanning services becomes an efficient cybersecurity process:
First, it can help find out potential vulnerabilities that could be easily exploited by hackers. By conducting regular scans, organizations can make sure that they are aware of potential security issues and take steps to remediate them.
Additionally, vulnerability scanning can help organizations comply with industry and regulatory standards.
Finally, vulnerability scanning can help organizations improve their overall security posture.
What are the challenges of vulnerability scanning?
Despite its importance, vulnerability scanning can be a challenge for organizations.
- It requires access to accurate and up-to-date data about vulnerabilities and this data can be difficult to obtain, especially for smaller organizations.
- Another challenge is conducting regular scans can be time-consuming and resource-intensive.
- And interpreting scan results can also be a challenge, especially for organizations without security expertise.
Despite these challenges, by taking corrective steps, organizations can improve their overall security posture and reduce their risk of being exploited by cybercriminals.
Also Read: What is Network Vulnerability Scanning? The Ultimate Guide
Types of vulnerability scanning
There are two main types of vulnerability scanning: active and passive.
Active scanning is a process where the scanner tries to exploit the vulnerabilities that it discovers. This can be done by sending requests to the system or application and observing the responses.
Passive scanning is when the scanner observes network traffic and looks for indications of vulnerabilities.
Both active and passive scanning have their advantages and disadvantages. Active scanning can provide more accurate results, but it can also be more disruptive to systems and applications. Passive scanning is less disruptive, but it can miss some vulnerabilities.
Most organizations use a combination of both active and passive scans to get the most complete picture of their system’s vulnerabilities.
Vulnerability scanning process in five easy steps:
Now that we’ve covered the basics of vulnerability scanning, let’s take a look at the process.
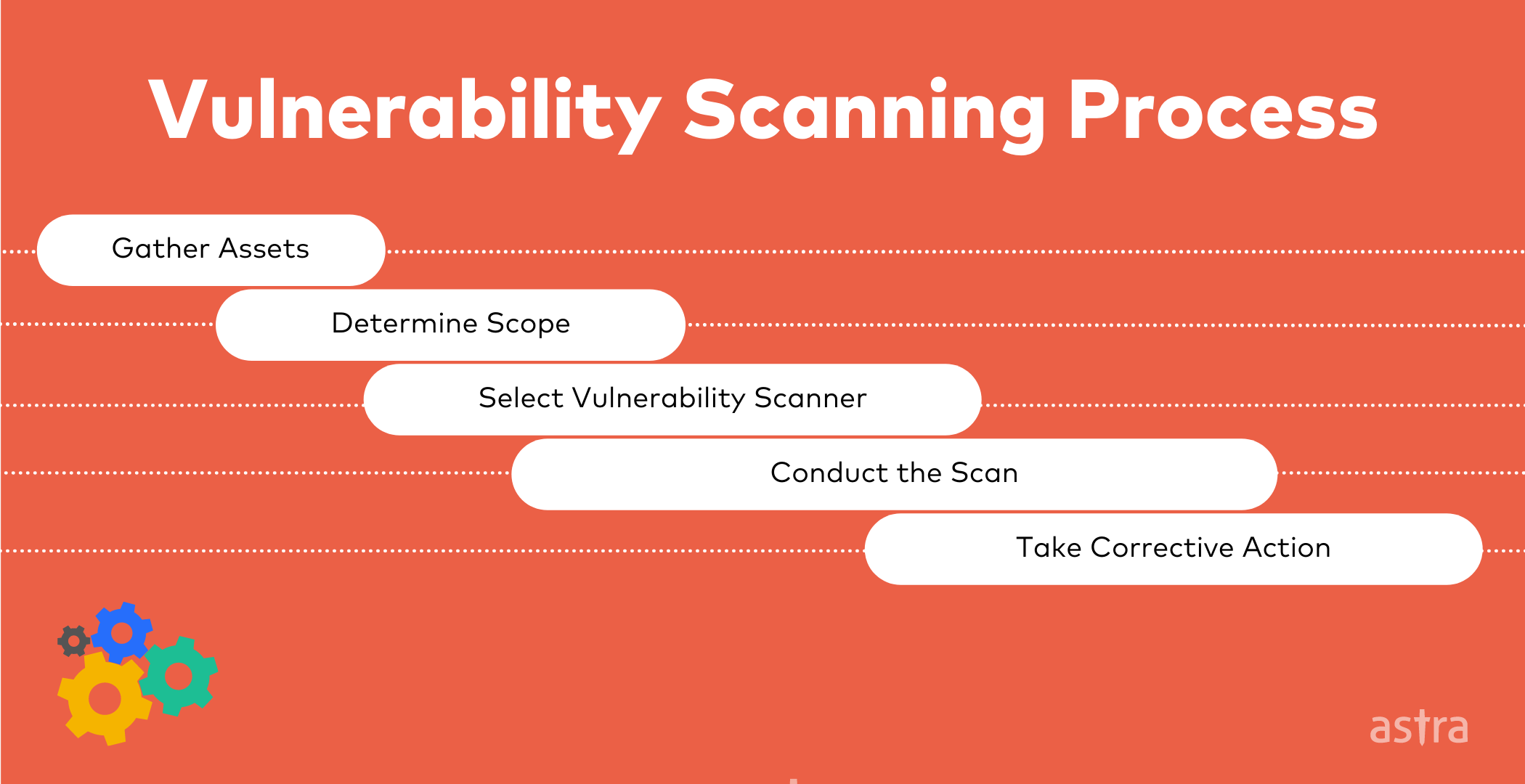
The first step is to gather the assets that need to be scanned and make a kind of inventory. This includes systems, networks, and applications.
The second step is to determine the scope of the scan. This includes deciding which vulnerabilities to scan for and which systems and networks to include in the scan.
The third step is to select the appropriate vulnerability scanner. There are many different scanners on the market, so it’s important to choose one that meets your organization’s needs.
The fourth step is to conduct the scan. This involves running the scanner and interpreting the results.
Finally, the fifth step is to take corrective action. This may involve patching vulnerabilities, implementing security controls, or taking other steps to mitigate the risks that have been identified.
How often should you conduct vulnerability scans?
The frequency of vulnerability scans will vary depending on the organization’s needs. However, most experts recommend conducting regular scans, at least once per week. Additionally, organizations should conduct scans more frequently if they are making changes to their systems or applications.
It can also be based on the type of assets you are going to scan. For example if the asset or system falls under the ‘high-risk’ tag then it should be regularly scanned on a daily basis (using a continuous scanning solution). And if the asset or system falls under ‘medium or low risk’ tag then you can perform monthly or quarterly scanning for them.
Note: To decide on these ‘high, medium, and low risk’ assets, you first need to understand how much impact your every network, application, etc. will cause you if they are compromised.
How to automate vulnerability scanning?
Simply put, organizations should consider using a vulnerability management solution to automate and streamline the vulnerability scanning process. A vulnerability management solution can help organizations to schedule and conduct regular scans, track and manage vulnerabilities, and generate vulnerability scanning reports.
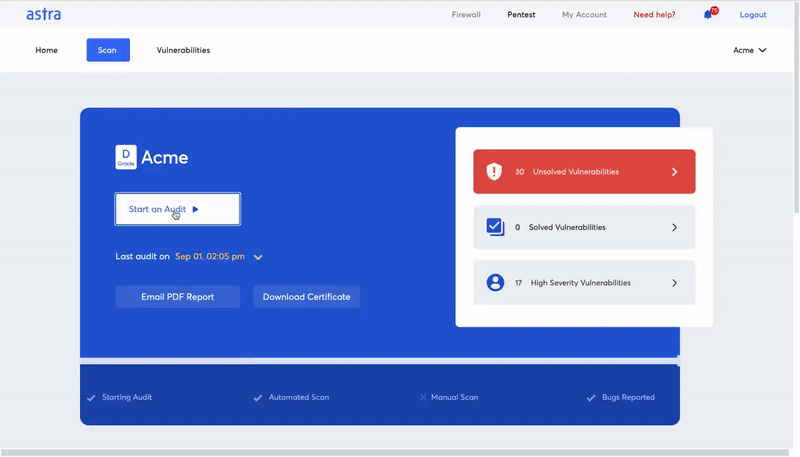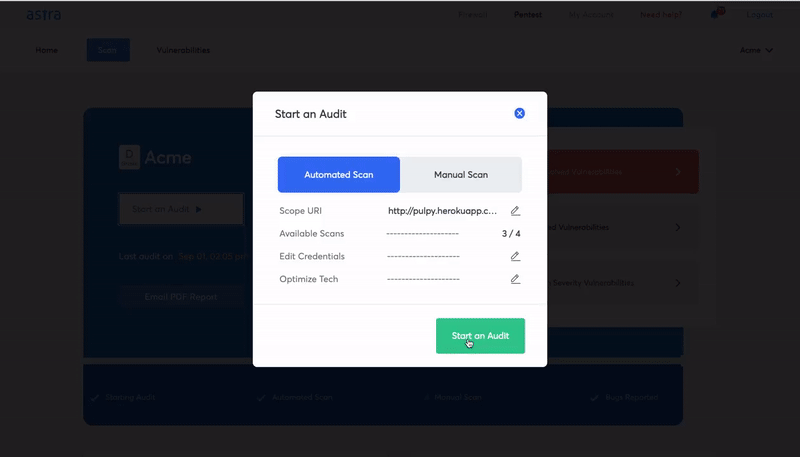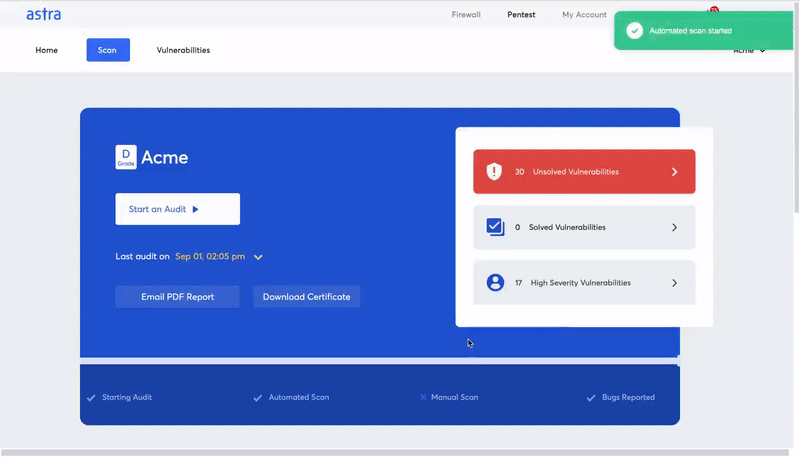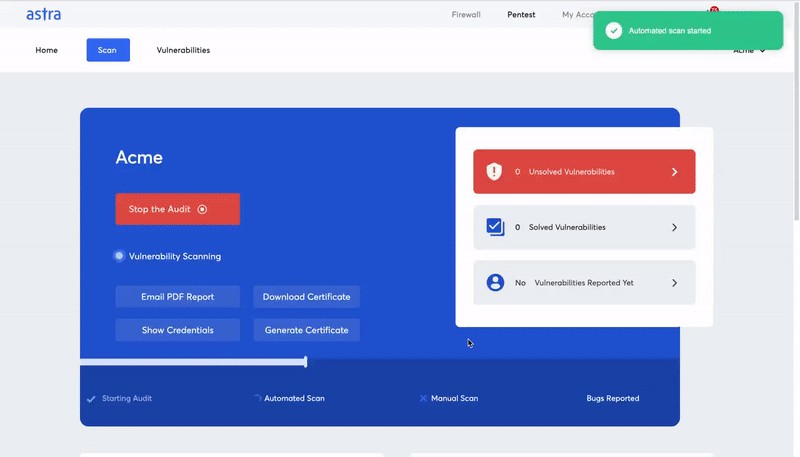
How to evaluate the best vulnerability scanner?
When looking for a vulnerability scanner, there are a few key features to consider.:
- The scanner should be able to scan for a wide range of vulnerabilities,
- The scanner should be easy to use and provide clear and actionable results,
- And, the scanner should be able to integrate with other security tools and systems.
Organizations should also consider their budget when selecting a vulnerability scanner. While there are many free and open-source scanners available, they may not have all the features that an organization needs. Conversely, commercial scanners can be very expensive.
The best way to find the right scanner is to evaluate the needs of the organization and compare them against the features and prices of different scanners.
How Astra Pentest can help you with automating your vulnerability scans?
Astra Pentest is a comprehensive vulnerability assessment and penetration testing suite that is specially designed to help organizations with their vulnerability scanning services and security compliance needs.
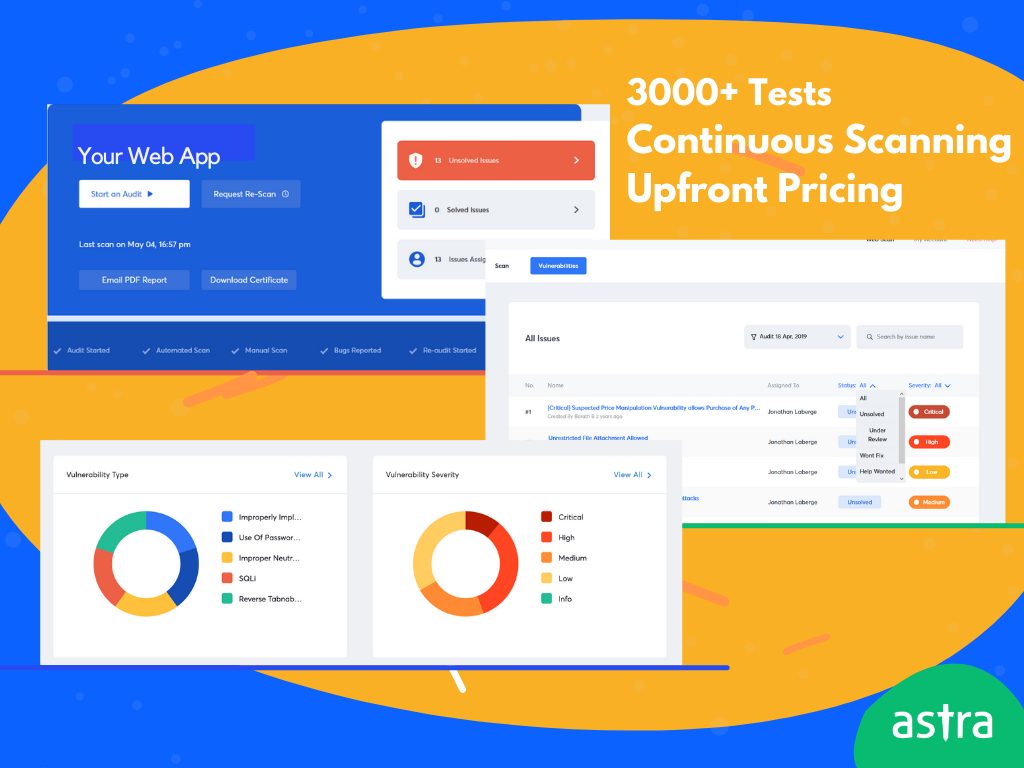
Astra Pentest has the following key unique features that make it stand out from the crowd:
- Automated vulnerability scanning with Astra’s Automated Vulnerability Scanner.
- Deep scan behind login pages with Astra’s Login Recorder feature.
- A combination of both automated and manual penetration testing with 8000+ test cases.
- Easy vulnerability management dashboard to collaborate with dev and security teams and fix vulnerabilities on priority.
- Integration options with your CI/CD pipelines are apps such as GitHub, Gitlab, Jenkins, Jira, Slack, and much more.
- Test cases for compliance (GDPR, ISO 27001, PCI-DSS, etc.)
- Publicly verifiable Pentest Certificate you earn the trust of your existing and new customers. And more…
Conclusion
As we have seen, vulnerability scanning is a critical process for any organization. By following the steps and guidelines provided in this article, you can conduct your assessment and procure the necessary tools to protect your organization from cyberattacks. Remember, it is always better to be safe than sorry; so make sure that you implement a comprehensive vulnerability scanning process today.
















