Cyberattacks and associated crimes are always on the rise, especially these days. With this, the need for SOC for every organization has also skyrocketed.
SOC as a service (Security Operation Centre) is a cloud-based set of services like comprehensive protection, continuous monitoring, and threat detection services on a subscription model.
SOC-as-a-service providers are those organizations that offer services like protecting vulnerability detection and management, VAPT services, and more to customers based on their needs.
However, maintaining an in-house SOC can be a daunting task, especially for up-and-coming companies. Here are some factors that you should keep in when choosing between top SOC as service providers:
- Capacity for threat detection
- Good vulnerability management services
- Dashboards with contextual collaboration
- Comprehensive VAPT Services
Top SOC as a service providers are:
- Astra Pentest
- Symantec
- Sophos
- Rapid7
- AlertLogic
- Qualys
- Arctic Wolf Networks
- Netsurion
- Secureworks
- Palo Alto Networks
This article will detail the top SOC as a service providers, the services provided by them, and their pros and cons in detail. Furthermore, it will also elucidate the factors to keep in mind when looking for a good service provider.
Top 10 SOC as a Service Providers
1. Astra Pentest
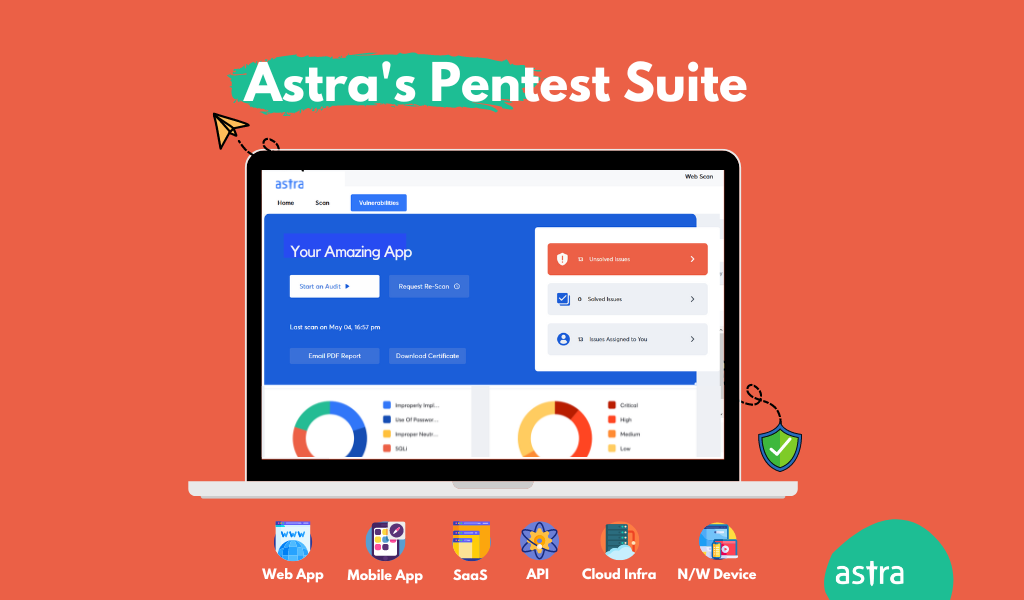
One of the top-notch data security audit tools, Astra Pentest provides expert security audits with the assurance of zero false positives to find all the weak spots plaguing one’s security.
- Regular Pentests
Astra provides continuous hacker-style penetration tests to identify and exploit vulnerabilities through vulnerability scans. This helps organizations gain an in-depth understanding of how an actual hack would affect their systems, network, and data.
- Comprehensive Vulnerability Scanner
Astra Pentest provides a world-class comprehensive vulnerability scanner capable of finding vulnerabilities using NIST and OWASP methodologies. These vulnerabilities are identified based on known CVEs, OWASP Top 10, SANS 25, and intel from various reliable sources.
- Easy-To-Navigate Dashboard
With total ease of use and navigation, Astra’s dashboards win customers over with their great user experience. The dashboard displays the vulnerabilities found in real-time with the severity scores and provides an option of collaboration with the target’s development time for quicker smoother patching.
- Maintain Compliance
Astra helps maintain compliance with its compliance-specific scans for regulatory standards like PCI-DSS, SOC2, GDPR, ISO 27001, and HIPAA. Compliance scanning has a dashboard dedicated to it.
- Detailed Reports
Well-detailed reports are yet another alluring feature of Astra’s penetration testing services. These reports have the scope of testing explained, vulnerabilities found on scanning, methods employed for exploitation of vulnerabilities, and the damages and information revealed from exploiting them as well.
Based on this, the report also mentions the CVSS scores for these vulnerabilities and well the detailed steps to take to patch them up. These reports are extremely useful for organizations when it comes to patching, or for documenting purposes for an audit.
- Pentest Certificate
Astra pentest certificate is a must-have and is only provided to customers who patch all the vulnerabilities found in the security weaknesses audit and obtain a rescan to ensure that there are no further vulnerabilities.
This certificate is publicly verifiable and can be displayed on customer websites to showcase its reliability and security-conscious nature. This brings about more customers who trust the services offered by your network.
- 24*7 Customer Care
Astra provides 24*7 expert assistance to its customers through e-mails, phone calls, and even the dashboard. Customers can touch with any queries they have regarding any vulnerabilities within the reply box under every vulnerability detected.
- Zero False Positive
Zero false positives are a sure thing with Astra’s thorough vetting which is done by expert pentesters based on the automated pentest results obtained. This double-checking, therefore, ensures that the customers don’t have to worry about any false positive vulnerability detection.
Pros
- Detailed and thorough reports
- Great remediation assistance
- Easy to use and navigate
- Budget-friendly
- Assures zero false positives with vetted scans.
Cons
- Could have more integrations.
- No free trial.
2. Symantec
Symantec’s cloud workload protection provides automated security measures for your cloud providers and customers alike.
Pros
- Provides end-point protection and threat detection.
- Also has centralized management.
- Has malware detection capabilities with the capacity for immediate remediation.
- Can be integrated within the CI/CD pipeline.
Cons
- A pricey cloud security solution that may not be feasible for small to medium-sized companies.
- Could provide better integration possibilities.
3. Sophos
Established in 1985 Sophos Cloud offers simplified enterprise-level solutions for cloud security including 24/7 cloud threat detection and response, native protection, and security automation for DevOps.
Pros
- Available for AWS, GCP, and Azure.
- Helps with security automation through DAST, SAST, and SCA code analysis.
- Intuitive user-friendly dashboard.
Cons
- It can be expensive.
- Difficult to set up.
- Customer support could be better.
4. Rapid7
Rapid7 provides world-class application security, vulnerability management, and SIEM services.
Other services provided by this company include penetration testing services and vulnerability scanning.
Pros
- Simple and easy-to-navigate interface.
- Capable of finding hidden vulnerabilities
- Great and easy-to-understand reports.
Cons
- Customer support can be improved.
- Removal of scanned devices must be done manually.
Also Read- Qualys vs. Rapid7
5. AlertLogic
AlertLogic is a well-known SOC-as-a-service provider that provides managed threat detection and response services (MDR).
Their holistic services include 24*7 threat monitoring, incident validation, remediation, log management, and more.
Pros
- User-friendly solution
- Precise and timely notifications
- Easy-to-navigate dashboards.
Cons
Could have better end-point protection.
6. Qualys
Qualys provides its cloud customers with continuous monitoring, vulnerability management, compliance solutions, and web application firewalls. These services make Qualys a top cloud security solution contender.
Pros
- Well-designed and easy-to-navigate user interface.
- Constant updates ensure the current security measures for the cloud environment.
Cons
- Limited scheduling options.
- Scans are not applicable to all applications.
7. Arctic Wolf Networks
This company provides managed detection and response solution that is available 24*7. It includes constant monitoring of networks, cloud environments, and endpoints.
Arctic Wolf eliminates alert fatigue and the possibility of any false positives while customizing responses catered to the organization.
Pros
- Good security protection solution.
- A cost-efficient solution to having an in-house SOC.
Cros
- Notifications can take time.
- Could have more integrations than currently available.
8. Netsurion
This company has a Peerspot rating of 7.8 out of 10. It provides SOC as a service with a managed open XDR (eXtended Detection and Response) with services like threat hunting and response, attack surface coverage, and cybersecurity services that are highly adaptive.
Pros
- Provides real-time alerts for threats detected.
- The solution is easy to deploy.
- Scalable solution.
Cons
- Some versions are rather slow.
- Could have a quicker response and update timings.
- Could provide more contextual support.
9. Secureworks
This company provides both managed and extended detection and response services. It combines security analytics, threat hunting, round-the-clock support, and incident response together.
The dashboard provides complete visibility to the user in terms of network, cloud environment, and endpoints, making the correlation of events much faster. It also comes with other services like prioritization and threat triage, remote incident response services, and more.
Pros
- Flexible pricing based on customer needs.
- More visibility and control over endpoints.
- Prioritization of threats.
Cons
- Not easy to implement.
- Needs to implement tamper-proofing.
10. Palo Alto Networks
Palo Alto Networks provides an all-around malware detection service as well as a next-generation firewall with high-end capabilities. It provides network speed and threat protection due to its streamlined organization.
Pros
- Palo Alto Network’s cloud security solution is easy to set up.
- Provides zero-day monitoring.
- Provides scope for integrations.
Cons
- Can be an expensive choice to opt for.
- No alerts for cloud performance degradation.
Now that we have seen the major top SOC as service provider contenders with their services and pros and cons, you might be wondering how to make the right choice.
Well, fret not, the next section service to help you analyze the factors to consider when choosing a provider.
Factors to Consider When Choosing A SOC as a Service Provider?
1. Capacity for threat detection
Top SOC as a service provider continuously monitor your organization’s assets and detect a threat in a timely manner.
They also must be proficient in the deft handling of vulnerabilities so as to keep your organization and assets safe from any breaches or hacks.
2. Good vulnerability management services
Upon the detection of vulnerabilities, the provider must also give appropriate remediation steps, POC videos, and more to ensure that the developers can easily fix the vulnerabilities.
The whole point of SOC as a service is to ensure that the developers can work on creating bug-free applications without compromising on security. Hence the delegation of vulnerability management makes their services more efficient.
3. Dashboards with contextual collaboration
The dashboard provided by the SOC as a service company should provide timely alerts, quick accessibility to reports, and steps for remediation.
It should have features for collaboration between the SOC team and developers within the dashboard itself.
4. Comprehensive VAPT Services
The SOC providers should also have the provisions to carry out regular vulnerability assessments and penetration tests according to your requirement.
This rigorous testing ensures that all the vulnerabilities are detected before they are exploited.
With penetration tests, one not only detects the vulnerabilities but also understands the level of impact from its exploitation.
Benefits Of SOC as a Service Over In-Premise SOC
1. Quick Identification and Remediation
Since SOC as a service provider is dedicated to protecting your assets 24/7, it reduced the burden on in-house security through quick detection and remediation of any vulnerabilities.
Constant monitoring and real-time alerts provided by SOC as a service provider help you keep your assets safe and secure.
2. Reduce Risks
SOC as a service provider helps you by reducing the chances of a breach and its remediation expenses like legal fees and other incurred costs from the damage done by such risks.
3. Cost Efficient
You can get a monthly subscription for SOC as a service based on your needs. This is far more cost-effective when compared to the cost and operating expenses of running an in-house security operations center.
4. Scalability
Businesses are seeing unprecedented growth and changes more quickly than ever before.
Therefore it is equally essential that the security operations center be just as agile and scalable according to the growing and changing needs of customers.
5. Compliance
SOC-as-a-service providers provide constant monitoring, detection, and remediation of any vulnerabilities your assets may have. By doing so, they help you maintain the necessary global security standards that your organization needs to be compliant with.
Conclusion
This article has detailed the benefits of choosing among the top SOC as a service providers like Astra Pentest and others mentioned. Opting for SOC as a service makes scalability and budgeting easier while putting security in the front seat of your organization’s procedures.
So make a wise and informed decision today to secure your assets from the get-go!
FAQs
What is SOC as a service?
SOC as a service (Security Operation Centre) is a cloud-based set of services like comprehensive protection, continuous monitoring, and threat detection services on a subscription model.
Who are the top SOC as a service providers?
Top SOC as a service providers include Astra Pentest, Symantec, Rapid7, and AlertLogic among others.
What are the steps in a penetration test?
A penetration test usually starts off by defining the scope, which is followed by scanning the determined assets for vulnerabilities, exploiting them, and reporting the learnings found.
![10 Top SOC as a Service Providers [Pros and Cons]](https://cdn-blog.getastra.com/2022/11/socasaservice.png)















