Article Summary
Let the title, Security Testing vs Pentesting not confuse you. You can choose both depending on your needs. In fact, Pentesting or Penetration Testing is a form of Security Testing. This article will talk in some detail about Security Testing in general, focus a bit on Pentesting, and establish the differences between Pentest and other forms of Security Tests.
The real threat of cyberattacks often eludes us. We are content with the firewall we installed three years ago and an expired SSL certificate. So, before we dive into whatever the title promises, that is a discussion of Security Testing vs Pentesting, let us quickly brush up on some sore memories from the major cyberattacks of the past. Remember, fear is a great motivator.
2014 – The attack on Yahoo compromised 500 million accounts. (Source)
2017 – The WannaCry ransomware affects 200,000 computers across 150 countries and results in financial losses of around 6 billion pounds. (Source)
June 2021 – The RockYou2021 breach compromised 8.4 billion passwords. The name commemorates the breach of the RockYou site in 2009 which had compromised around 32 million passwords. Some tribute! (Source)
Well, most of these were targeted attacks, meticulously devised for specific networks. But a staggering number of websites fall prey to blunt mass attacks. The mass attacks target sites with common vulnerabilities as simple as a weak password. By a simple act of testing your systems once in a while, you can avoid most attacks. Enough of security preaching. Let us get on with the story.
What is Security Testing?
The process of scanning your network as well as physical environment for vulnerabilities that could lead to a cyberattack, data theft, or other malicious activity, is called Security Testing. It is a broad term encompassing a number of different techniques.
We can generally divide Security Testing into three categories.
- White Box Security Testing: This is when the security testers receive ample information about the internal structure of the target system. They go in knowing how the code is supposed to be implemented, and they check whether everything is aligned.
- Black Box Security Testing: In this form the testers hardly receive any information about the internal structure of the system. Their work is based on input and response. This approach is similar to how a real attacker would make their moves.
- Grey Box Security Testing: The Grey Box approach is a combination of whitebox and blackbox. While the testers do not know the code structure, they are given some crucial information like login credentials. These tests are important to figure out how much damage an attacker with privilege access can cause.
Also Read: Security Testing Software – 5 Things to Understand Before You Choose One
What is Penetration Testing?
Penetration testing is a form of security test where security experts simulate a hack of your systems to uncover and exploit vulnerabilities.
At the end of a successful penetration test, you learn,
- What vulnerabilities are hiding in your system
- How much risk each of them poses to the business
- How to fix them
Different forms of Security Testing
As mentioned earlier, Security Testing is a broad term. We will learn about some of the different methodologies that fall under the umbrella.
Network Scanning
This is a process of identifying devices and users operating within a network by employing a feature in the network protocol. Attackers use Network scanning in order to discover operating systems, servers, and services associated with a network and then look for vulnerable entry points. Security experts can take a similar approach to find and fix those vulnerabilities.
Vulnerability Scanning
This is an automated procedure where a program scans the target system for a known set of vulnerabilities and security loopholes. The scanners can locate security vulnerabilities in a network, as well as in the software connected to it. It is used by Pentesters and security experts as a foundational security exercise.
Also Read: A Complete Guide Cloud Penetration Testing | API Penetration Testing: What You Need to Know
Ethical Hacking
Ethical hacking, again, is a broad term encompassing all activities performed by security experts to alert organizations about potential threats to their network, applications, or site. Ethical hackers employ a skill set similar to that of a malicious actor, but with a different intention and within strict legal boundaries.
Penetration Testing
Just as the name suggests, in this process, a team of security experts try to penetrate your website, application, or network, through weak points or vulnerabilities. They exploit the vulnerabilities to an agreed extent, and create a report. The pentest report contains the list of vulnerabilities, their risk score, and detailed guidelines for remediation.
Know About: Penetration Testing Quote | Continuous Penetration Testing: The Best Tool You’ll Find in 2022
What Separates Penetration Testing from Security Testing in General?
Simply put, Penetration Testing is an advanced form of security testing where not only do you identify the vulnerabilities, you also understand how each of those vulnerabilities could affect your business. For instance, if your site has a faulty plugin, that is a vulnerability. The Pentester would try and establish how much damage that faulty plugin can cause if an attacker exploits it. It will also show you how the defenses in place react to the threat. There are some other distinguishing factors. Let us look at them.
Also Read: 11 Top Penetration Testing Tools of 2022 [Reviewed]
Security Testing vs Pentesting
| Security Testing Except Pentest | Penetration Testing |
|---|---|
| A broad term covering a number of security exercises. | One of those many security exercises. A special one, in fact. |
| Has a broad yet shallow area of operation. | Has a narrow yet deep area of operation. |
| Ends up with a long list of potential vulnerabilities. | Ends up with a list of real vulnerabilities with risk scores. |
| Does not exploit vulnerabilities. | Exploits certain vulnerabilities to assess them. |
| Does not come with detailed guides for reproducing and fixing vulnerabilities. | Comes with a detailed remediation guide. |
| Companies looking for a wide surface level security check should opt for it. | Companies dealing with a lot of sensitive data that already have security protocols in place, should opt for it. |
| High level security tests like Network scanning take 20 minutes to an hour. Automated vulnerability scans can take up to 10 hours. | Penetration testing can take 4-10 days depending on the scope of the test. And rescans take 2-3 more days. |
| Security testing reports come with a list of potential vulnerabilities and some security recommendations. | Penetration Testing reports are significantly more detailed with risk scores, and guidance for remediation. |
Security Testing vs Pentesting – Explained
Understanding the Pentest Process
The process of Penetration Testing is in itself an elaborate affair. Not that you need to worry about each step of the process, especially if you are working with an efficient penetration testing company. But you never know when this information might come handy.
We usually divide the Penetration test into 7 different phases. Let us quickly run through them.
Phase 1. Pre-engagement
In this phase the client and the security team discuss the scope of the pentest. They decide which assets to leave out of the test. They talk about a strategy where the vulnerabilities can be exploited without interfering with business. They basically set up the rules of engagement. And this is also the part where any information required is given to the Pentesters.
Phase 2. Reconnaissance
This is where the Pentesters use various tools and techniques to gather information about the target. They can assume active or passive strategies to achieve their goal. This phase determines the course of action for the entire Penetration Test.
Phase 3. Discovery
Some more information is gathered in this phase along with the vulnerability scan. This phase uncovers vulnerabilities contained in the target system.
Phase 4. Vulnerability Analysis
The threats found in the previous phase are tied to specific kinds of vulnerabilities in this phase. You start gaining an understanding of the potential vulnerabilities, and the risk each of them comes with.
Phase 5. Exploitation
Some of the vulnerabilities found earlier are exploitable. The Pentesters exploit certain vulnerabilities to find out how much access they can gain through those loopholes. They also try to escalate their access by different means.
Phase 6. Pentest Report and Remediation
The Pentest report contains all relevant information about the vulnerabilities including CVSS scores. The risks posed by the vulnerabilities are judged by how easy they were to exploit, and how much access they yielded. The report also contains detailed guidelines for the developers to fix the vulnerabilities.
Phase 7. Rescan
Most Pentesters offer a rescan of your systems after the vulnerabilities are fixed. If the rescan does not come up with any vulnerabilities, your network, site, or application, can be considered as safe.
Read also: A Detailed Guide to Internal Penetration Testing
Special benefits of Penetration Testing
When we discuss a topic like Security Testing vs Penetration Testing, it is quite obvious that we would want to point out certain special benefits of one of them. The whole point here is to show you how Penetration Testing has a strong upper hand on most other forms of Security Testing in terms of depth of coverage and effectiveness.
- You understand the real risk posed by a security loophole when it is actually exploited to gain access to your system.
- The Pentest is conducted from the vantage point of a real attacker, it helps you focus on the most significant attack vectors, rather than having a surface level approach to security.
- The detailed report from the breaches give you real-time data on how a breach could affect your business. It becomes easier for you to allocate the security resources.
- The same data helps your developers reproduce the vulnerabilities and fix them for good.
Who should get a Pentest done?
In some industries Penetration Testing is mandatory.
Payment processing companies must engage in Penetration Testing in order to comply with the PCI DSS regulations.
Healthcare institutes need Pentesting to operate within the HIPAA guidelines.
IT service providers need regular Pentesting for SOC2 Type II compliance.
Any organization that has internet-facing assets or holds and transmits sensitive data – credit card information, personal data of customers, healthcare-related information, confidential government data – should engage in regular Penetration Testing.
Also Read: 11 Top Penetration Testing Tools of 2022 [Reviewed] | Top 5 Software Security Testing Tools in 2022 [Reviewed]
Astra Makes Penetration Testing Super Simple for Users
As a business owner or as someone who is responsible for the security of a business, you are hardly bothered about things such as Security Testing vs Penetration Testing, or which one of the tests you should opt for.
Your goal is to improve the security posture of your organization, get certified, and carry on business without the threat of hacks and with a good security ROI. Astra simply ensures that.
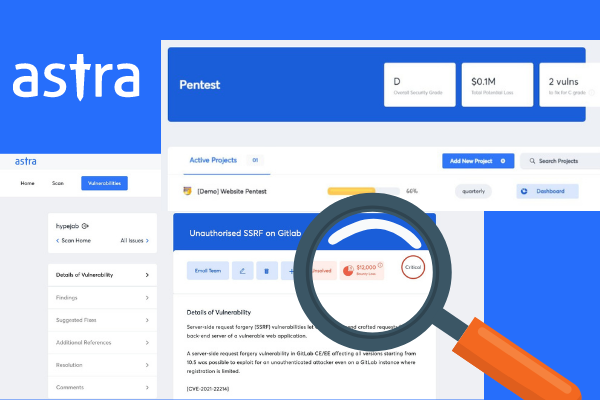
The security experts at Astra perform 8000+ tests to scan out all the vulnerabilities. They explore each of them, and figure out ways to fix them.
Within a day of starting the security scans they start updating the vulnerabilities on a Pentest dashboard which is dedicated to your organization. You monitor the vulnerabilities, visualize the analytics, and plan the remediation according to the degree of threat.
Astra eases up the remediation too by offering video POCs to aid your developers. The Devs can even get in-call assistance from the security engineers in case they face a roadblock.
After you are done with the repairs, Astra offers multiple rescans to ensure that your system is clean. Then you get a globally acknowledged certificate. Neat, isn’t it?
Final Words
The nature of your business, the amount of sensitive data you are handling, the value your company may hold for hackers, the kind of software you are using, all of these should factor into your choice of a security test. It is in your best interest to enlist professional help when you are making this choice. Just remember, that all the forms of security testing can work in tandem to improve your overall security posture and help you repel cyberattacks.
FAQs
- What is the time line for Penetration Testing?
Penetration Testing takes up to 10 days depending on the scope of the test. The rescan after the initial test can take half that time. - How frequently should I conduct security audits?
The exact number of scans per year depends on a number of different factors – industry, compliance, etc. – the general recommendations is to have quarterly audits. - What is the cost of Penetration Testing?
The cost of Penetration Testing is between $700 and $7,999 per scan depending on the scope of the test and the number of scans.
















