94% of all technical professionals use SaaS-based solutions and 73% of all businesses are planning to move all systems to SaaS by the end of 2022. So, we won’t be wrong to say that Software as a Service is all the rage. And why not? SaaS applications offer your business agility and scalability like never before. The accessibility of the data is on point, SaaS providers are always on their toes to increase operational speed, and mitigate any issue you might face. But like most good things, SaaS comes with a hiccup i.e. security. That is why we will be talking about SaaS security assessment in this post.
What is SaaS Security?
SaaS security is an umbrella term that covers all defensive and offensive measures taken by SaaS providers to make their applications, and services safe for the users. It includes but isn’t limited to firewalls, access controls, vulnerability assessment, penetration testing, etc.
Since we’ll be talking about SaaS security assessment, our discussion will revolve largely around VAPT. But we’ll also make general best practices for saas security, and various principles and policies, part of the discussion.
Why is Security Assessment Vital for SaaS Companies?
SaaS is the natural destination for businesses trying to achieve more with less. Adopting software as a service means moving towards better productivity, more speed, and faster innovation. You cannot take these away from SaaS solutions even for the sake of security. But when a SaaS provider is attacked and exploited, it affects hundreds of businesses that depend in some way or the other on the said SaaS provider.
So, SaaS applications are always on, always reachable targets, overshared, and needlessly authorized by users who misunderstand the security audit logs which desperately try to monitor disparate information. It is just as messy as it sounds in the previous sentence. As a result, SaaS apps exist as constant security threats to the millions of businesses that use them, and to the providers of such apps and services.
What are the Primary SaaS Security Challenges?
We can divide the security challenges of SaaS applications and services into five categories.
- Adversaries: There can be external malicious actors trying to hack into your SaaS app through a common vulnerability. For instance, a hacker could take advantage of a lack of input validation in your SaaS app to slip malicious code into it and gain access to sensitive information.
- Privileged Activity: We often lose track of people who have privileged access to our SaaS applications. It opens doors for former or current employees to cause harm by tampering with data.
- Accidental Activity: As we mentioned earlier, a large percentage of SaaS security breaches are caused by human error. Gartner predicts that by 2025, 99% of all cloud security failures will be caused by human error. This includes using weak passwords, falling prey to phishing emails, revealing sensitive information by mistake, etc.
- Insider Threat: This is especially applicable for businesses with crucial intellectual property. SaaS applications are often used for sharing sensitive information, developing ideas, creating prototypes, etc. An insider with malicious intent can take advantage of their privileged access to the SaaS platform to leak or sell this information.
- Zero-Day Vulnerabilities: These are software security vulnerabilities that sit undetected until they are exploited by attackers. When a SaaS service provider has a zero-day vulnerability, it can affect all the customers depending on the said SaaS provider at the time of the attack.
Best Security Practices for SaaS Providers and Users
In this section, we will talk about principles and habits you can encourage and explore within your enterprise to make SaaS security as simple as possible. These tips will eventually help you with your general security acumen.
1. Protect Account Access
We have already discussed how granting admin-level access to an application to too many people can affect your security. You should always grant access to someone for a certain period, and then renew access when required. This ensures that someone who’s no longer associated with your business doesn’t retain access.
Apart from this, you need to monitor access regularly. Monitor the privileges granted to certain employees, and their behavior on the application.
It’s on you to encourage and enable responsible usage. Make it easier for people to gain access to a service when they need it so that they do not hesitate to relinquish access when they no longer require it.
Also Read: 5 SaaS Security Certifications to Wrap Your Head Around
2. Multi-Layered Authentication
Thanks to the two-step authentication process recently adopted by Gmail, we all understand the notion of multi-layered authentication where you cannot log into your account using just one set of credentials. Now, layered authentication has taken many different forms.
- Time-based OTP via SMS or Email: This is the most widely used two-step authentication system. You receive a one-time password via SMS or via email which you need to provide to log into your account after putting in the credentials. This is not among the most secure processes because attackers hacking into SMS or Email is quite a well-known phenomenon.
- HMAC and Shared Key: Hash-based Message Authentication Code combined with a shared key is one of the most secure data authentication systems right now. In this process, the client and the server are provided with secret shared keys. Now, the client creates a unique hash for every request, and the server hashes the request with the private key. If the HMACs from the client and the server match, the client is considered to be legitimate.
- Authentication through key-stroke dynamics: This one is a real piece of innovation where a behavioral analysis system analyzes the press-time (the duration of pressing a key) and seek-time (time taken to find the next key) to authenticate a user. This is also called typing-biometric analysis.
3. Data Encryption
When you use a SaaS solution, you trust the software service provider with your data. But should you trust them with your data? Well, if your organization uses 3-4 SaaS applications, and you have time to review their privacy policies and make a vendor assessment, you can count on the SaaS providers to keep your data secure but according to Netskope, an average enterprise uses 900+ SaaS apps.
Every bit of data you share with the SaaS provider has to be encrypted. Encryption usually works in three ways.
- Client-side Encryption: All the data you send is encrypted and you never share the key with the application provider. This is a secure way of using SaaS apps but you cannot unlock the full functional potential of said apps with this kind of encryption in place.
- Fully Homomorphic Encryption (FHE): In this form of encryption all the client-side data is encrypted without affecting the performance of the SaaS app. However, there are a couple of issues around this as well. Computation with FHE is not as fast as unencrypted computation and it doesn’t allow all the functionalities.
- Enterprise Key Management (EKM): This refers to the centralized control over encryptions on multiple servers, operating systems, and databases. The enterprise key manager is centrally located in a hardware security module. It is an entity with high availability and is in control of encrypting and decrypting data and rotating keys.
4. Discovery and Inventory of SaaS usage
You cannot assess or protect what you cannot see. That is exactly what happens with SaaS apps. We use so many of them at any given point in time that we often lose track. The foremost crucial step of any SaaS security assessment is discovering all the tools in use and creating an inventory of the same.
The challenge with this is that often SaaS apps are brought into an organization by employees without involving IT. You can follow API discovery, app permission discovery to discover, and inventory SaaS usage.
5. Use Cloud Access Security Broker Tools
A cloud access security broker or CASB is a tool that sits between your on-premise infrastructure and cloud infrastructure ensuring that the traffic between the cloud and your on-premise assets is regulated by your security policies.
CASB tools can include firewalls, web application firewalls, and discovery app discovery mechanisms. It can detect high-risk applications, high-risk users, apps in use, etc. CASB tools can be on-premise or cloud-based.
Also Read: A Complete Guide to Cloud Security Testing | Cloud Security Audit: Everything You Need to Know
6. Use SaaS Security Posture Management
An organization’s security posture refers to the strength of its security against cyber threats. Your organization’s SaaS security posture helps you understand the state of SaaS security and SSPM or SaaS security posture management is the entire process of monitoring and fixing the security issues related to SaaS apps.
The goal of SSPM is to ensure compliance, remove security misconfiguration, have a detailed SaaS security checklist, and fight cyber threats. SaaS security assessment is a vital part of SSPM. The following are the key functionalities of an SSPM system.
- Visibility into the security stature of all the SaaS apps
- Detect risky apps and users according to industry standards
- Raise alerts for security misconfiguration and broken access controls
- Guidance for resolving common security issues
7. Regular Vulnerability Assessment and Penetration Testing
This is equally important for both the providers and the users of SaaS. By performing regular VAPT you can identify security vulnerabilities related to your SaaS apps. A SaaS provider should conduct regular penetration tests as part of its security practices to ensure its web app is not susceptible to mass attacks. Engaging a VAPT provider for your regular SaaS security assessment is a good idea since it takes the load off your shoulders and ensures a foolproof assessment of your systems.
Read also: 8 SaaS Security Solutions You Can Count On | 11 Top Penetration Testing Tools of 2022 [Reviewed]
What role does pentest play in SaaS security assessment?
Pentest is the short form for penetration testing which refers to the simulation of a hacker-style attack on a system to detect its security vulnerabilities. Wait, pentest does not only detect the vulnerabilities, but it also exploits them to draw insights about their nature – how difficult it is to exploit them, how much damage an attacker can cause by exploiting them, what the potential cost of a breach is.
By conducting regular pentesting a SaaS provider can ensure that the offerings are safe for the clients. They can also produce the pentest certificate as an assurance to the clients regarding the safety of the SaaS offering. A lot of SaaS users insist on receiving a SaaS vendor security assessment report before taking their business to a SaaS provider.
Read also: Penetration Testing: What, Why and How [A Complete Guide]
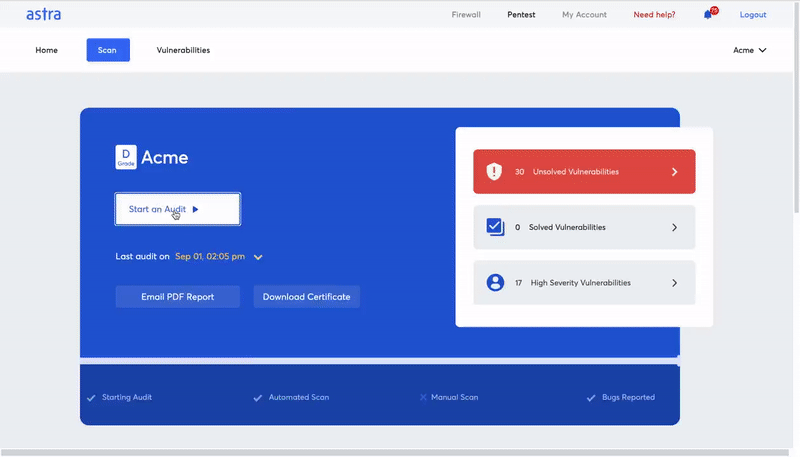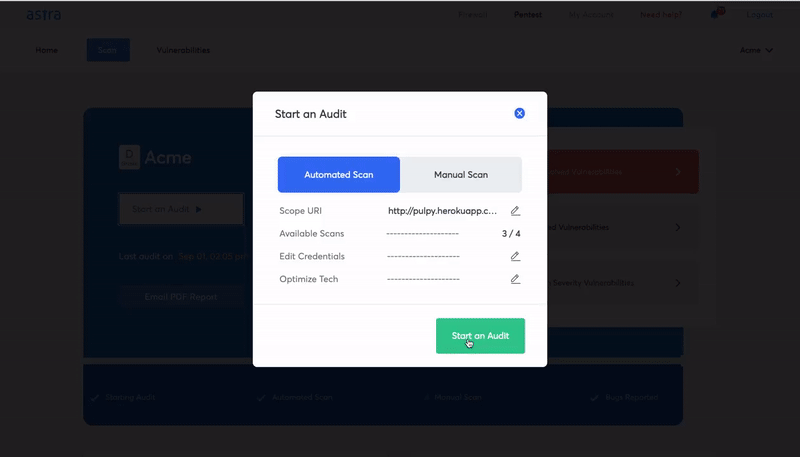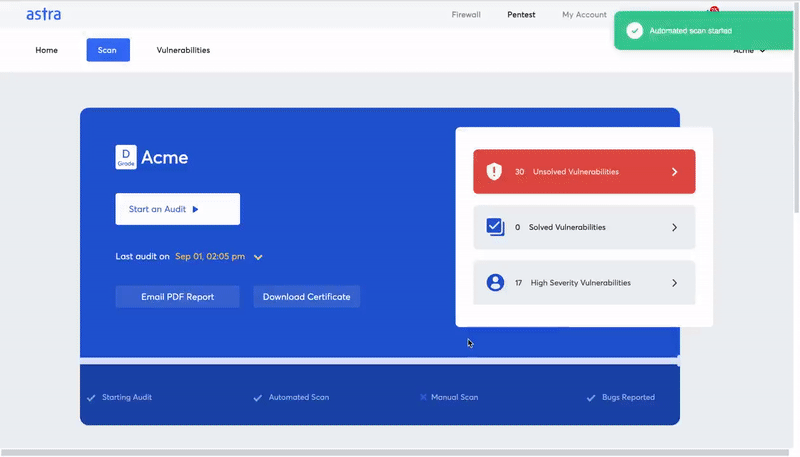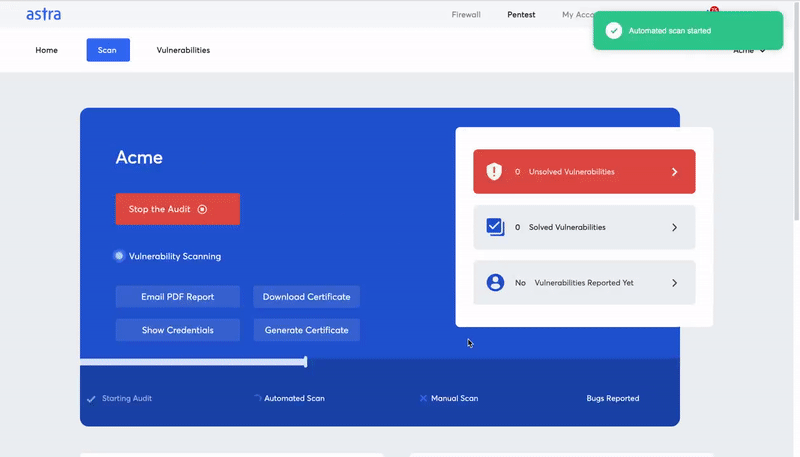
Astra’s Pentest as a SaaS security solution
Astra’s Pentest suite is a complete vulnerability assessment and penetration testing solution for both SaaS providers and users. Astra brings a plethora of customizable features that turn SaaS security assessment into a smooth process.
Astra’s pentest includes a powerful automated vulnerability scanner along with manual pentest capabilities. You can use Astra’s pentest dashboard to monitor important information related to the SaaS security assessment. It allows you to monitor the vulnerabilities, assign them to developers, and communicate with Astra’s security experts regarding remediation of the issues. The following are some cool features that Astra’s pentest brings onto the table.
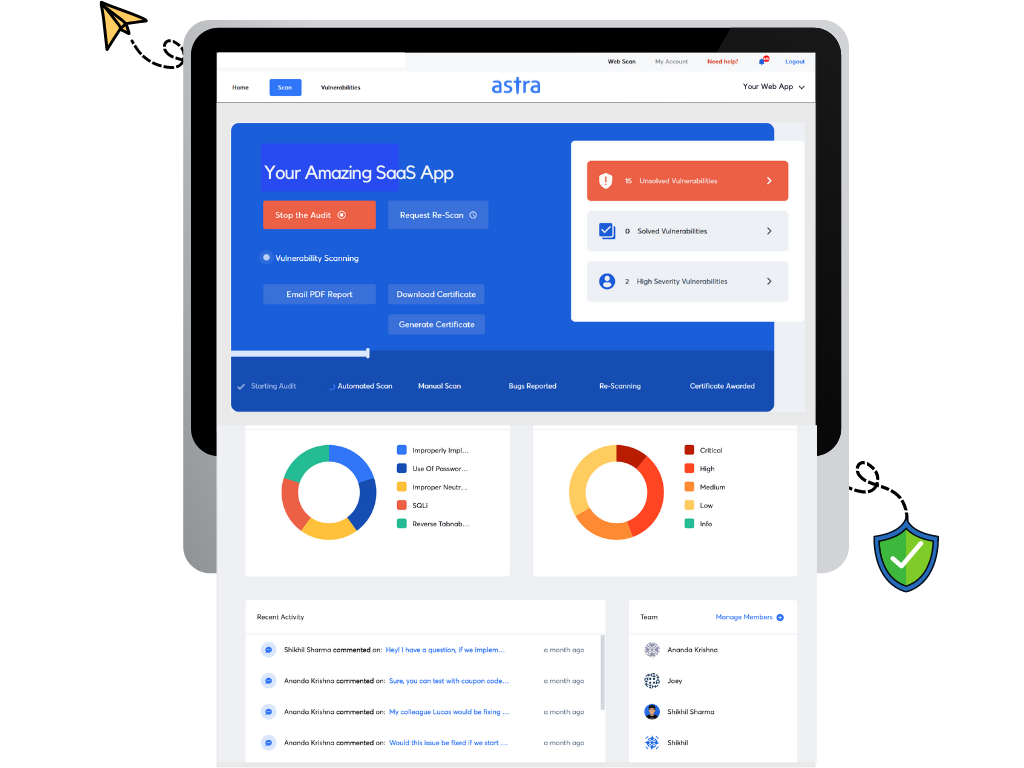
- Continuous testing of software updates with the help of CI/CD integration
- Slack and Jira integration for better workflow management
- 8000+ automated tests covering OWASP top 10 and SANS 25
- Manual pentesters ensure zero false positives
- Publicly verifiable Pentest Certification
The pentest report by Astra’s security experts is extremely thorough and designed to cater to both developers and executives. Your developers can use the step-by-step guides and video PoCs to reproduce and fix the vulnerabilities before you avail of the free re-scans and gain the pentest certification. All of these and more make Astra an impeccable SaaS security assessment tool.
Conclusion
SaaS applications are like the adhesive that holds most of today’s businesses together. Since you cannot imagine an hour of work without logging into some SaaS tool, it is better to be aware of SaaS security issues, and the importance of consistent SaaS security assessment. We have discussed various practices and policies around SaaS security all of which come down to a few simple principles – grant access only where it is needed, detect misuse, investigate, and clean up. A good SaaS security assessment tool can help you with all of it quite easily. The question is whether you are ready to bring discipline to your SaaS usage.
FAQs
What is the cost of a SaaS security assessment?
The cost of a SaaS security assessment depends on multiple factors like the scope of the assessment and the size of the target organization. Find out more here.
Why is a SaaS security certificate necessary?
The certificate allotted to your SaaS application after the SaaS security assessment carries the proof that your application is safe at that point in time. It helps you build trust with clients, and stay ahead of the curve. It also prepares you for compliance. Read about SaaS Security Guide.
What is the timeline for SaaS penetration testing?
It takes 7-10 days to complete the SaaS penetration testing process. Read about what is SaaS Penetration Testing.
















