Things may have gone a bit overboard. The Internet of Things (IoT) is all the rage these days. Everyone is running around trying to catch up with the latest IoT trend. It seems that no matter how often you read about the IoT, it’s changing so fast that your head is spinning. IoT is the network of interconnecting devices to exchange data. While the definition may not be great, IoT is the future.
The Internet of Things has been a buzzword for the past few years, and many businesses are adopting it. However, devices’ vulnerabilities and the IoT environment could be exploited. This blog is going to look at the different aspects of IoT security testing and why it is important.
Understanding Internet of Things (IoT)
Internet of Things is a network of devices connected to the Internet. It consists of everyday physical objects connected to the Internet and can be controlled remotely. It includes smart homes, smart cars, smart cities, connected medical devices and smart devices in general.
It is expected that there will be 29 billion devices connected to the Internet by 2022. The Internet of Things is the next big thing after smartphones. It is a new wave of technology that will bring many changes in our daily lives.
The Internet of Things is a network of physical objects that contain sensors and microchips and are capable of sending and receiving data over the Internet. This creates the ability for these “things” to be controlled remotely.
Imagine if your alarm clock could read your calendar, automatically set itself to the right time, and then inform you about the weather for the day. Imagine if your coffee maker could let you know that you have low coffee grounds. The Internet of Things, or IoT, is the future of how all of these things and more can be possible.
What is IoT Security Testing?
IoT Security testing is a process of testing IoT devices to find security vulnerabilities that hackers could exploit to access your network, modify your data, or steal your information. This can lead to significant financial losses, identity theft, and damage to the reputation of both your business and the manufacturer of the vulnerable device.
Taking IoT security measures for your devices will help make sure that they are secured from the hackers and other unauthorized users.
Why do you need to worry about IoT Security?
With the introduction of IoT and connected devices in our daily life, the number of devices being used has increased significantly. IoT devices have brought about a whole new range of issues.
The new world of IoT and connected devices have opened up the possibility of a massive attack surface with an exponential increase in the number of entry points for hackers. The threat of cyber-attacks on IoT devices is genuine and severe. The way we use our devices to control our homes, cars, and even the way we bank are all at risk of being compromised by cyber-attacks.
The world of the Internet of Things is, without a doubt, the future of technology. However, with the rise in popularity of IoT products, we also see an increase in the number of vulnerabilities found in those products.
Also Read: 11 Top Penetration Testing Tools/Software of 2022
Exploring common attacks on IoT devices
1. Mirai Botnet Attack
Mirai Botnet, or Mirai malware, is a malware that takes over and controls Internet of Things (IoT) devices such as routers, security cameras, DVRs, and even refrigerators, using them to form a botnet that can be used to conduct cyberattacks.
Mirai can also download other malware onto infected devices. It’s important to mention that Mirai malware is designed to infect devices running on ARC processors. This processor is most commonly used in IoT devices, such as AV equipment and IP cameras.
2. Mozi
A recently discovered botnet is currently spreading around at a rapid rate, a botnet that is so unique that it has its name: Mozi. This new botnet has been active for two years, with the first mentions dating back to 2019.
Mozi is a P2P botnet that spreads to IoT devices using known vulnerabilities and weak (default) Telnet passwords.
OWASP Top 10 – IoT Security Testing
1. Weak, Guessable, or Hard-Coded Passwords
Weak, guessable, or hard-coded passwords in IoT devices are a severe problem that can be used to gain unauthorized access to systems. This can allow attackers to do anything from stealing data to control systems.
2. Insecure Network Services
Insecure network services are the network services running on the device itself. These are accessible from the Internet and are exposed to the Internet by default. It may be insecure in the sense that it is not configured with the security best practice. For example, it may be exposing some form of critical information to the public network.
3. Insecure Ecosystem Interfaces
In the software industry, when the term ecosystem is used, it refers to all third party software, hardware, networks, cloud-based services, and interfaces around a software product. This means that any element that is part of the ecosystem can be a source of risk for the product and the company, which is a part of this ecosystem.
4. Lack of Secure Update Mechanism
The key to securing IoT devices is in the maintenance of the software. The software is at the heart of the IoT device. We have seen IoT devices being compromised by using insecure code libraries, 3rd party SDKs, bad code design and more. Even if the device is physically secured, if the software is compromised, there is nothing to stop an attacker from taking over the device, collecting data and exfiltrating it.
5. Use of Insecure or Outdated Components
An insecure or outdated component in an IoT device can create many issues. It can be leveraged to access the network or the device, allowing attackers to control it remotely. It can be used to steal data and access the internal network. It could be used to create a botnet, launch DDoS attacks or spread new malware and whatnot.
Also Read: 10 Best Cyber Security Audit Companies [Features and Services Explained]
6. Insufficient Privacy Protection
IoT devices have the ability to collect a lot more data than your smartphone. The difference is that smartphones have more security and privacy controls than most IoT devices. IoT devices are usually used to monitor and control devices at home. If security is compromised in an IoT device, a hacker could gain access to your home. This is especially scary when considering that many IoT devices monitor security systems and control door locks.
7. Insecure Data Transfer and Storage
As the Internet of Things (IoT) expands and more devices and sensors are being connected to the Internet for gathering and exchanging data, the related security risks and challenges also increase.
8. Lack of Device Management
One of the issues that IoT developers face is that they are not fully prepared with IoT device management tools and asset management which leads to improper management of IoT devices.
9. Insecure Default Settings
Some Internet of Things (IoT) devices are shipped with insecure default settings or lack the ability to make the system more secure by restricting operators from modifying configurations. This has made it easy for hackers to access the devices and collect data from them.
10. Lack of Physical Hardening
There are several ways to harden a device physically, but if you aren’t careful, it can significantly decrease the device’s usefulness.
For example, many IoT devices are made to assume that they’ll be placed in a public environment, like a shop or restaurant or a place where they won’t need a lot of security, like a home. This means that devices are often designed to be as simple as possible and don’t need a lot of physical security.
Also Read: Top 6 Web Pentest Tools You Should Not Miss in 2022
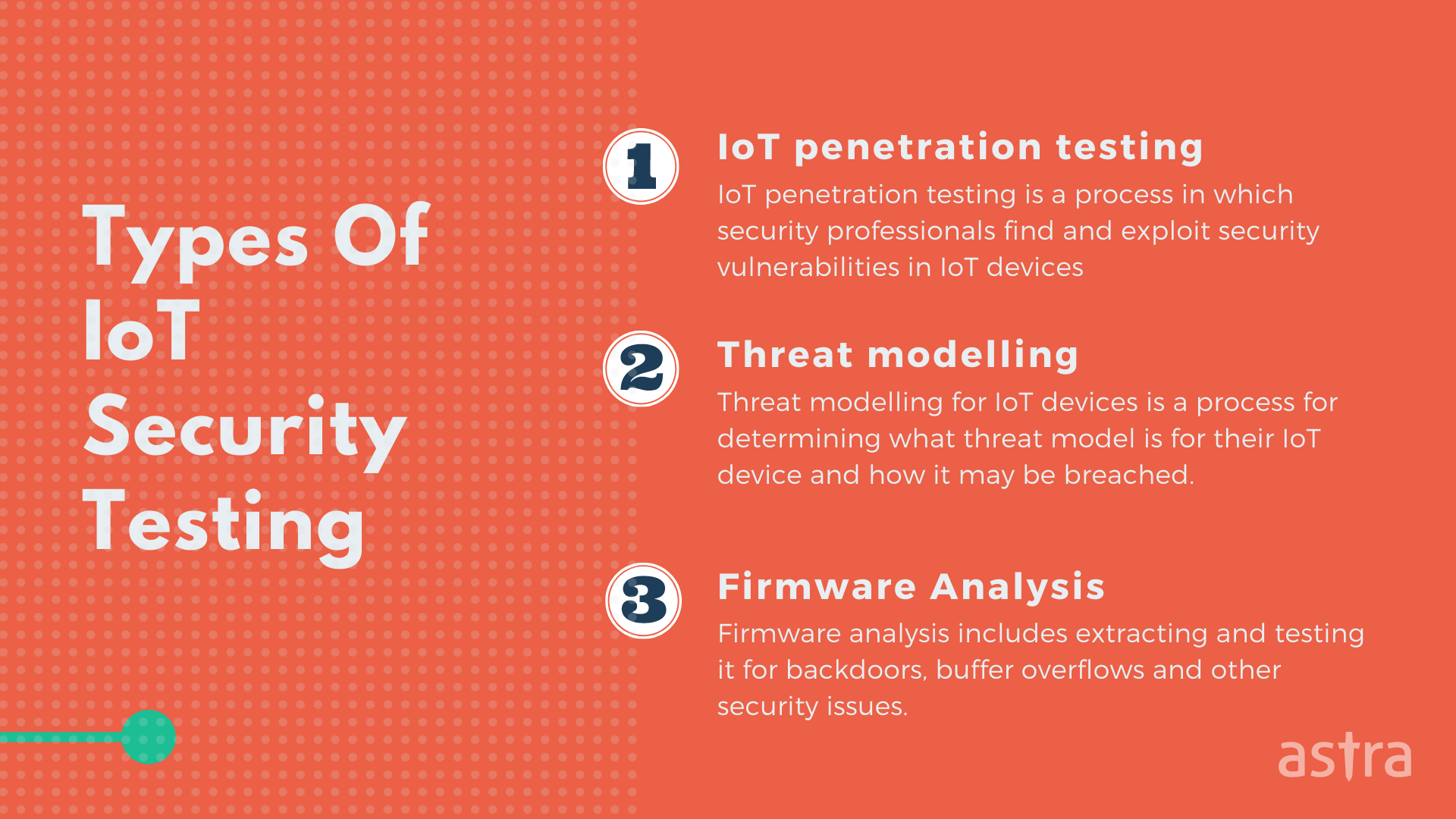
Types of IoT Security Testing
The Internet of things are all around us, and now and then, we hear stories of them being exploited. IoT security testing is a significant part of developing IoT applications. Below are some of the most common types of IoT security testing:
1. IoT penetration testing
IoT penetration testing is a type of IoT security testing methodology in which security professionals find and exploit security vulnerabilities in IoT devices. IoT penetration testing is used to check the security of your IoT devices in the real world. When we talk about IoT penetration testing, we are referring to testing not only the device or the software but also the entire IoT system.
2. Threat modelling
Threat modelling for IoT devices is a process for determining what threat model is for their IoT device and how it may be breached. For example, a camera may be used to spy on people within a certain distance. It may be used to monitor the inside of someone’s home. The camera may be breached physically by a third party, or a hacker may get into the camera’s system and view the images it is recording.
3. Firmware Analysis
One of the most important things to understand is that firmware is software, just like a computer program or application. The only difference is that firmware is used on embedded devices, small computers with a dedicated function. For example, a smartphone, router, or even a heart monitor. Firmware analysis includes extracting and testing it for backdoors, buffer overflows and other security issues.
Best Practices for keeping your IoT devices secure
Security is a vital aspect of the Internet of Things (IoT), and a lot of research has gone into finding secure designs and techniques that IoT devices can use. Keeping that, we have created a list of a few pointers to keep in mind to keep IoT devices secure and free from vulnerabilities.
1. Always change default credentials
2. Implement strong encryption for data transportation and storage
3. Implement secure booting
4. Regularly perform IoT security testing
5. Update, Track and manage your devices properly
Top 3 IoT Security Testing Tools
The Internet is the most unsecured place where anything can be hacked. Therefore, it is essential to perform IoT security testing to ensure that your device is not part of the next big hack. The following are the top 3 IoT security testing tools:
1. Firmware Analysis Toolkit: FAT is built to help security researchers analyze and identify vulnerabilities in IoT and embedded device firmware.
2. PENIOT: PENIOT is a penetration testing tool for the Internet of Things (IoT) devices. It helps you test/penetrate your devices by targeting their internet connectivity with different types of security attacks.
3. AWS IoT Device Defender: AWS IoT Device Defender is a fully managed service that helps organizations protect their fleet of IoT devices from external threats. AWS IoT Device Defender gives you the ability to monitor your fleet of IoT devices’ health continuously and detect and remediate potential threats.
Wrapping it up…
Internet of Things (IoT) technology is evolving rapidly, which has led to the introduction of a wide variety of new devices, such as home automation systems, wearable devices, and smart meters. At the end of the day, IoT is a technology that has the potential to make our lives more convenient, but it’s important to understand the security risks that come along with it.
FAQ’s
1. What is Internet of Things (IoT)?
Internet of Things is a network of devices connected to the Internet. It consists of everyday physical objects connected to the Internet and can be controlled remotely.
2. What is IoT security testing?
IoT security testing is a process of testing IoT devices to find security vulnerabilities that hackers could exploit to access your network, modify your data, or steal your information.
3. Can Astra help me with IoT security testing?
No, at the moment Astra don’t offer any security services related to IoT devices.
4. What is security testing in IoT?
IoT devices are connected to the internet by definition. Hackers can manipulate these devices. With IoT security testing, you can ensure the safety of your connected devices.
5. What are IoT security tools?
Some good IoT security tools are Firmware Analysis Toolkit, PENIOT, AWS IOT Device Defender.