Today, smart contracts are becoming at the forefront of Blockchain technology. From Finance and IoT to the Supply Chain and Music industry, the implementation of intelligent smart contracts applies everywhere in our daily life.
Smart contracts are visible and thus transparent to all the users of said blockchain. However, this visibility can also extend to vulnerabilities that can be exploited by hackers or cybercriminals to further damage the smart contract. Thus resulting in loss of revenues, customer data exposure, and much more.
Therefore, to prevent such attacks, it is important to understand how smart contract security functions and learn about its proper implementation and other aspects of securing a smart contract-based platform against cyberattacks and hacking attempts.
What is a Smart Contract Audit?
A smart contract audit is the detailed analysis of programmed agreements in a smart contract consisting of functions and data that get automatically executed whenever a network tries to access it for a transaction requested by a user and the terms pre-set by both parties are successfully met.
Why Smart Contract Audit Is Important?
Smart contract security audits are important for the following reasons:
Enhanced Security
Smart contract security audits offer additional security by testing the programming code for any vulnerabilities which can be identified, evaluated, and fixed thus providing enhanced security. This increases security and reduces bugs, risks, and chances of unauthorized access.
Vulnerability Remediation
Audits help in the assessment and mitigation of coding errors, flaws in business logic, and unforeseen issues. Early identification and remediation of vulnerabilities can aid in maintaining the integrity of the smart contract.
Better Code Quality
A smart contract security audit results in a comprehensive analysis of the coding with the contract. Such a review ensures that the code is in compliance with security standards, and other coding benchmarks. It can help identify areas where the coding can be improvised for better performance or security.
Achieving Compliance
Smart contracts are often used to enforce regulatory compliance and audits help ensure they align with regulatory requirements and that the business logic is implemented with no errors.
Increased Transparency and Reputation
The standard of tests is not whether the smart contract audits are cheap or expensive, rather, based on the quality and transparency of the services provided by them. This directly translates to the reputation of the smart contract audit company as exemplary services speak loud.
How Does A Smart Contract Work?
A smart contract is a type of Ethereum Account that runs on a blockchain-based platform known as Ethereum blockchain. They are executed automatically when the parties involved meet pre-set terms and conditions. It makes the execution and outcomes of an agreement immediate without the need for any intermediary services.
An Ethereum Account consists of ether (ETH) as a balance. Users’ accounts can communicate with a smart contract and access the data by submitting a transaction. This transaction executes a predefined function on the smart contract which gives the user access to the data present in a smart contract.
A computer scientist, lawyer, and cryptographer Nick Szabo primarily defined smart contracts as “Building Blocks for Digital Markets” back in 1996. He stated that the “smart” in a smart contract is “because they are far more functional than their inanimate paper-based ancestors. No use of artificial intelligence is implied.”
Further, Nick terms smart contract as a digital vending machine. A vending machine that operates through a “contract” gets executed whenever a person puts money in the machine and gets the product.
For example: To get a drink from a vending machine:
money + drink selection = drink dispensed
Of course, smart contracts are used in a more sophisticated way while doing cryptocurrency transactions.
What Are The Different Types Of Smart Contracts?
Smart contracts are created and deployed over a network using programming languages such as Solidity and Vyper. Smart contracts are classified into 4 different types according to their usage by programmers for building applications.
- Decentralized Autonomous Organizations (DAOs) – involve a set of rules established and controlled by organization members and not influenced by external entities.
- Smart Legal Contracts – involve strict legal resources and are legally binding(also known as legally enforceable smart contracts). All the contractual agreements set are executed by a computer program automatically.
- Contracts of Applied Logics (ALCs) – built on a decentralized network (which does not rely on a single central server) that combines a smart contract with the front-end user interface.
- Distributed Applications (DApps) – These are application-based codes that are in sync or in combination with other smart contracts.
How To Audit A Smart Contract?
The smart contract auditing process includes the following steps:
Scoping
Smart contract audit and development begin with the establishment of thorough scope. This helps in establishing the assets that require to be audited thereby avoiding any scope creep and legal troubles.
Smart Contract Review
Here smart contract auditing actually begins with a thorough assessment of the various functions and parts of agreements, access from the network is all reviewed meticulously to discover any flaws that may be present.
Some of the issues checked for include, access control and authorization, and default visibility among others.
Identification and Verification
The discovered vulnerabilities are identified, evaluated, and verified to ensure that there are no false positives present. This final check is done before compiling the list of vulnerabilities and their details into a detailed report.
Smart Contract Audit Report
Smart contract audit reporting is a crucial part of the audit since this document determines the steps taken by the customer to resolve the issues that plague their smart contracts. The report comes with steps and recommendations for the mitigation of vulnerabilities along with their potential impact, and CVSS scores.
Recent Cyberattacks on Blockchain/Smart Contracts
Following recent events shows that the smart contract as blockchain technology is not immune to the exploitation of smart contract vulnerabilities:
- On August 3rd, 2022, thousands of Solana (popular blockchain for speedy transactions) wallets were drained of nearly $ 8 million in total. The exploits were thought to have occurred due to complications in importing accounts.
- On the 2nd of February 2022, the Wormhole Cross Chain Bridge Attack resulted in a loss of more than $320 million from Solana and Ethereum, two popular blockchains.
- In August 2021, one of the biggest cryptocurrency heists happened. Hackers stole $613 million worth of digital currency from a company named Poly Network. They exploited a vulnerability in the digital contracts Poly Network uses.
- In 2017, $150 million worth of ETH was stolen from an organization named Parity technologies due to a critical vulnerability present in their Ethereum smart contract.
- In 2016, a DAO called Genesis DAO was compromised by a hacker(s) exploiting a security loophole in the system. Here, hackers stole $50 million worth of ETH from Genesis DAO’s crowdfunding investors.
Key Vulnerabilities In Smart Contracts + Measures To Avoid Them
Some of the common smart contract vulnerabilities include:
Storage of unencrypted files on the blockchain
Storing confidential information on the blockchain can cause a major threat to security as blockchains are accessible to anyone thus putting your entire system at risk.
Avoid this issue by making sure to never save anything confidential on the blockchain without first encrypting it.
DoS attacks
Denial of service attacks can be done by denying authentication or services or by overloading ports with requests.
Add a failsafe into the smart contract and ensure that all nodes have sufficient storage and processing power.
Smart contracts with no upgrade options
Smart contracts by definition are not modifiable but rather self-destructed. But this poses an issue if some mistakes are made.
Avoid the issue of making a bugged smart contract by making sure they can be upgraded using proxies or pausable functions.
Function default
Functions are visible by default, therefore, meaning everyone can execute them.
Always make sure that function visibility is well-defined and stated clearly to avoid any trouble.
Also read: Blockchain Security Issues – A Complete Guide
How Can Smart Contracts be Secured?
One of the main reasons behind organizations using smart contracts technology is its strong security posture. It acts as a lawyer (with an agreement) between two parties involved in a transaction.
However, there have been many instances where the platforms running on smart contracts were compromised due to the unhealthy implementation of smart contracts during software development, and improper security measures.
Smart contract security efforts start before writing the first line of code – during planning, design, and development processes and end with securing against cyberattacks and potential vulnerabilities such as re-entrancy, front running, ETH send a rejection, integer overflow/underflow, DoS, Insufficient Gas briefing, RCE and many others mentioned in Smart Contracts Weakness Classification Registry (SWC Registry).
Here are some points on how you can secure smart contracts against attacks and vulnerabilities:
- Write a more secure smart contract code with best practices followed by leading organizations.
- Periodically perform smart contract security audits and penetration testing.
- Follow a blockchain security checklist.
- Run automated security scans on a smart contract.
- Use the trusted blockchain tools for design, development, security, auditing, and exploiting.
Let’s now discuss the above five points in more detail:
1. Smart Contract Secure Coding Best Practices
Smart contracts are developed using different programming languages such as Solidity, Vyper, Go or Java, etc. It is important to follow all the identified and publicly available resources for coding a secure smart contract. Here are some best practices that you can follow during your smart contract design, implementation, and deployment phases:
- Generate schema and architectural diagrams using Slither printers.
- Do thorough code documentation using keeps Natspec format (for Solidity) and keep as much code off-chain as you can
- Write small and meaningful functions, and split the logic either through multiple contracts or by grouping similar functions.
- Try to shorten the inheritance tree, you can use Slither’s inheritance printer to check the hierarchy.
- Write customer checks and properties with Slither, Echidna, and Manticore.
- Implement security for the wallets of your privileged users using cryptography.
2. Perform Smart Contract Security Audit and Pentesting
Even though your smart contract is bug-free and securely developed, hackers can always find a way to exploit potential security loopholes and vulnerabilities. They can either compromise a smart contract or an entire blockchain platform and steal thousands and millions worth of cryptocurrency.
A periodic penetration testing and security audit for a smart contract is the solution to this problem. Pentesting and smart contract audit processes helps you uncover these potential vulnerabilities in your system and gives you time to fix these weaknesses before a hacker(s) tries to exploit them and hack your platform.
Here are some steps you can take to do pentesting and smart contract audit online:
- Perform static analysis of your code to identify style inconsistency and vulnerable code using a SAST tool
- Perform security analysis for your smart contract using trusted tools like Mythril, MythX, Echidna, Oyente, Manticore, and ERC20 Verifier.
- Test for all the vulnerabilities mentioned in the SWC Registry.
- Organize a bug bounty program by defining a proper scope and outsourcing penetration testing if you don’t have an experienced security team available in your organization.
- Generate a detailed report on identified vulnerabilities in your system and recommendations for fixing those vulnerabilities.
We at Astra Security helped many blockchain platforms with security audits and penetration testing for their smart contracts and blockchain apps. Our pentesting tool Astra Pentest is easy to understand and offers a centralized management dashboard for the security and management teams. Further, our highly professional and certified auditors make sure no single vulnerability or security loophole goes unnoticed.
3. Follow a Blockchain Security Checklist
It’s always a good practice to follow well-researched and practically implemented checklists for the security of your blockchain-based applications. Some of the pointers in a good blockchain security checklist include:
- Mandate multifactor authentication.
- Leverage security incident and event management (SIEM).
- Definition of policies that indicate the right level of access to the right individual for the right use.
- Enforcing IAM controls to access blockchain solutions.
These are just some of the best practices, therefore make sure to check them out in detail to take full advantage of the best blockchain security practices.
Also, do check this related resource: How to Do a Blockchain Security Audit?
4. Use Automated Vulnerability Scanners
Using an automated security vulnerability scanner can help you with the security analysis of your smart contract. It can help you identify bugs in the code that can lead to security vulnerabilities and can also help you prevent a variety of attacks. You can use this open-source security scanner for Ethereum smart contract which is supported by Ethereum Foundation called Securify.
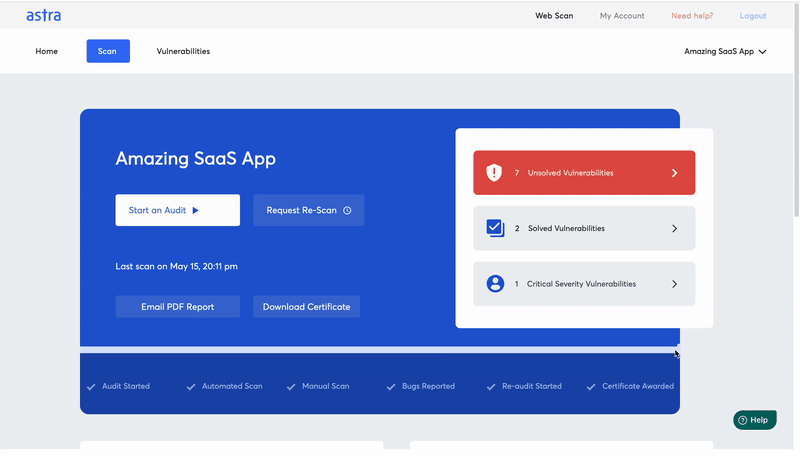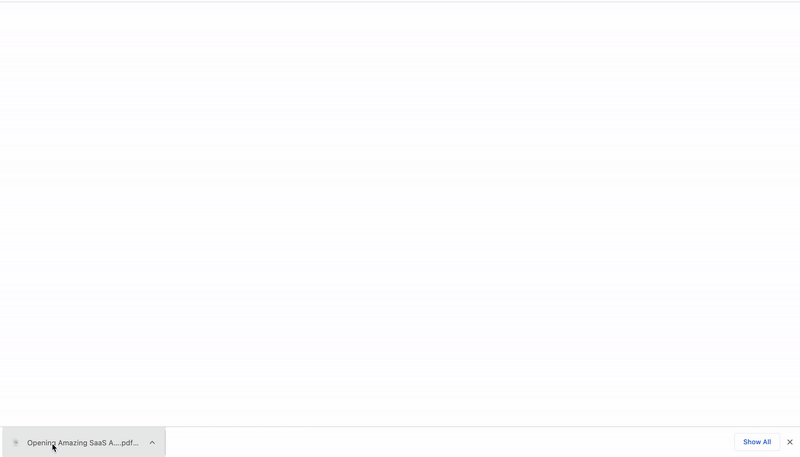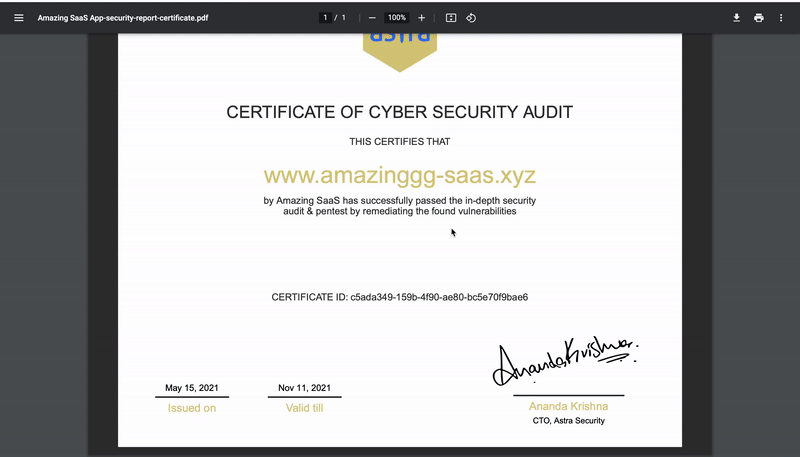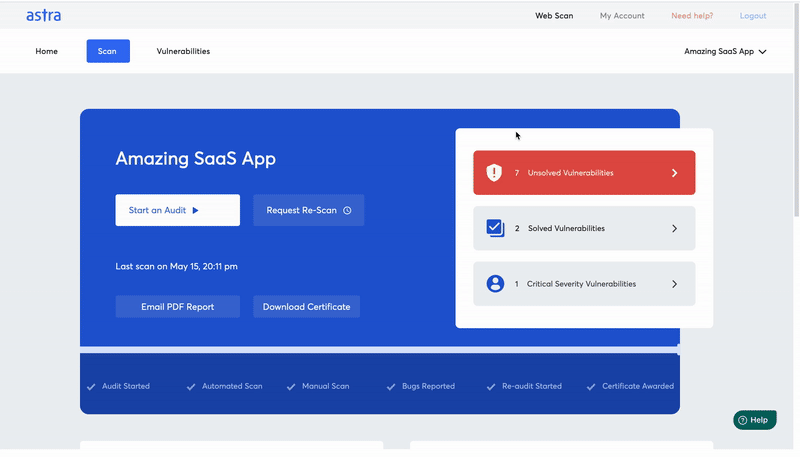
You can also use Astra’s Vulnerability Scanner. It learns from new CVEs, bug bounty data & intelligence gathered from pentest that Astra’s security engineers conduct for businesses in varied industries.
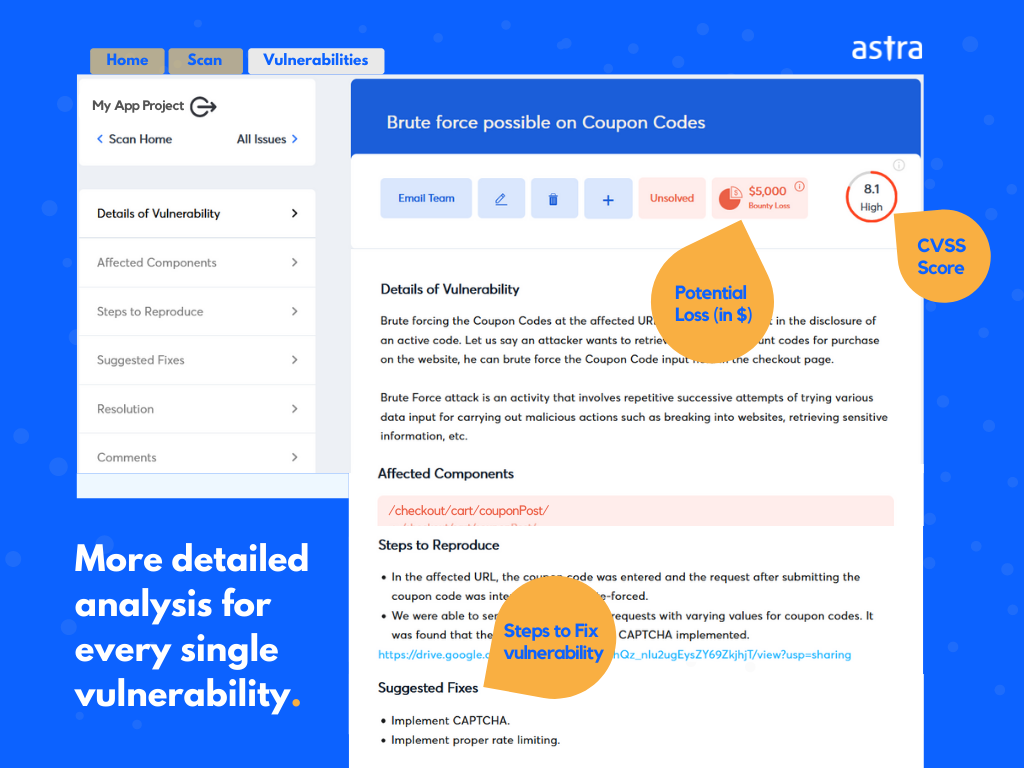
The ‘Vulnerabilities’ section in Astra’s Vulnerability Scanners provides a detailed analysis of every single vulnerability discovered in the scan results:
- Details of Vulnerability
- Affected Components (of application or N/W)
- Vulnerability Impact, Severity, CVSS Score, and Potential Loss (in $)
- Steps to Reproduce
- Steps to fix / Suggested Fixes
- Additional References
5. Use Smart Contract Audit Tools
The below-mentioned tools help in automated smart contract audits
- SWC-registry – It is a type of library for smart contract weakness and vulnerabilities
- MythX – It is a smart contract security analysis API
- Echidna – It is used for fuzzing/property-based testing of Ethereum smarts contracts
- Manticore – It is a symbolic execution tool for smart contract analysis
- Oyente – A static analysis tool for smart contract security
- SmartCheck – Security analyzer
- Octopus – It is a security analysis framework for the smart contract
- Awesome Buggy ERC20 Tokens – A collection of vulnerabilities in ERC20 smart contracts with tokens affected
Professional Smart Contract Security Audit by Astra Security
Considering the more complex structure of blockchains and smart contracts can become ambiguous for many IT teams during the security audit or pentesting of their smart contracts. Further, the limited and distributed resources about the technology can get the IT teams stuck during the audit process due to insufficient knowledge for proper implementation – which ultimately leads to a waste of time and resources for your organization.
Hence, it is always best to take professional help for smart contracts audit from certified security auditors who can easily do the job for you so you focus on the business side.
Astra Security can help you get your smart contract or blockchain platform audit done without any hassle. The award-winning team at Astra Security provides the most complete set of smart contract security solutions and services. You also get a publicly verifiable VAPT certification from Astra that can help you build trust among customers for your blockchain-based platform.
With Astra Security, you achieve every goal of your comprehensive security strategy for your blockchain platform – be it best practices to reduce risks against cyberattacks or building a rock-solid application for your customers.
Want to know more about Astra’s smart contract security audit solution and services? Schedule a call here to talk with our expert team in detail.
FAQs
1. What is the timeline for Smart Contract Security Audit?
Smart Contract Security testing takes 7-10 days to complete. The timeline may differ slightly based on the nature and scope of the test.
2. How much does a smart contract audit cost?
Smart contract audit prices generally vary from $5000 to $15,000 based on the complexity of the code, and the time-consuming nature of the task since smart contract auditors have to check codes line by line and even if automation is included.
3. Why choose Astra for Security Audit?
The security engineers at Astra perform extensive manual pentest on top of machine learning-driven automated scans. The vulnerability reports appear on your dashboard with detailed remediation guides. You will have access to a team of 2 to 10 security experts to help you with the fixes.
How to become a smart contract auditor?
Individuals aspiring to be smart contract auditors can take up courses to learn programming languages that relate to smart contracts as well as studying the best practices and gain training through actual smart contract projects.

















Hey, thank you for the detailed post. I would like to know which are the best smart contract audit companies in the US?
Hey Rebecca, here are some of the best smart contract audit companies in the US-
1. Astra’s Pentest Suite
2. Quantstamp
3. OpenZeppelin
4. Trail of Bits
5. ConsenSys Diligence