Over the years Blockchain technology has become the talk of the industry. As a foundational technology, it is not only underpinning cryptocurrencies but also a varied range of other applications too. Successful applications of blockchain technology in industries like banking & finance, health care, food safety, and gaming have made the most impact. This wide spread use of blockchain technology has made a discussion of blockchain security audit unavoidable.
So what exactly is blockchain? Well, blockchain enables peer-to-peer distributed ledger infrastructure for individuals and companies, which facilitates the procedure of recording transactions and tracking assets.
Since blockchain is a software, no one can say that it is immune from hacking. In fact, in the past couple of years, there have been many cases where several crypto trading platforms suffered brutal cyber attacks. For instance,
- Virtual currency exchange platform – Coincheck Inc. lost $532 million in NEM coins in a major cryptocurrency theft that occurred in January 2020.
- In July 2020, 2gether, another cryptocurrency exchange operator, was targeted by hackers who stole about €1.2 million in cryptocurrency.
Although the blockchain system addresses protecting the integrity of data, it doesn’t imply that this solution is immune to attacks. What’s more interesting is the fact that securing the blockchain from attack is quite challenging. That is why the notion of executing blockchain security audit is gaining prominence in industries and companies employing blockchain as software.
Why does Blockchain need to rethink security?
Even though blockchain as a technology is known to be most secure, there have been instances where loopholes and vulnerabilities were discovered – targeting its insecure integrations and interactions with different applications and servers. This makes blockchain security assessment crucial to eliminate such security loopholes and evade vulnerability exposures in the applications.
A few other problems that lead to a vulnerable Blockchain software include:
- Vulnerabilities in smart contracts: The smart contract, also known as pieces of code that run on blockchain networks are most vulnerable to the hacking attempts.
- Ignoring Security Assessments: The applications running on the Blockchain method are deployed without sufficient security assessment.
- Development Flaws: Also, a majority of IT specialists would tell you that it is impossible to develop code without any minor flaw.
Even so, many Blockchain systems have not executed regular security reviews like automatic security checks and independent security audits. Furthermore, the applications running on Blockchain differs from applications running on a centralized system. In other words, if any problem arises, you cannot interrupt the operations of the app as Blockchain is a decentralized system.
Thus, there is an ardent need to conduct a Blockchain security audit to stay protected from any cyber threats or mishaps.
How to do a Blockchain Security Audit?
While the emergence of tools like VeriSol is a relief to many, the sad reality is that there aren’t too many tools to conduct a blockchain security audit. This is the reason that manual auditing still plays a very important role in Blockchain applications and networks.
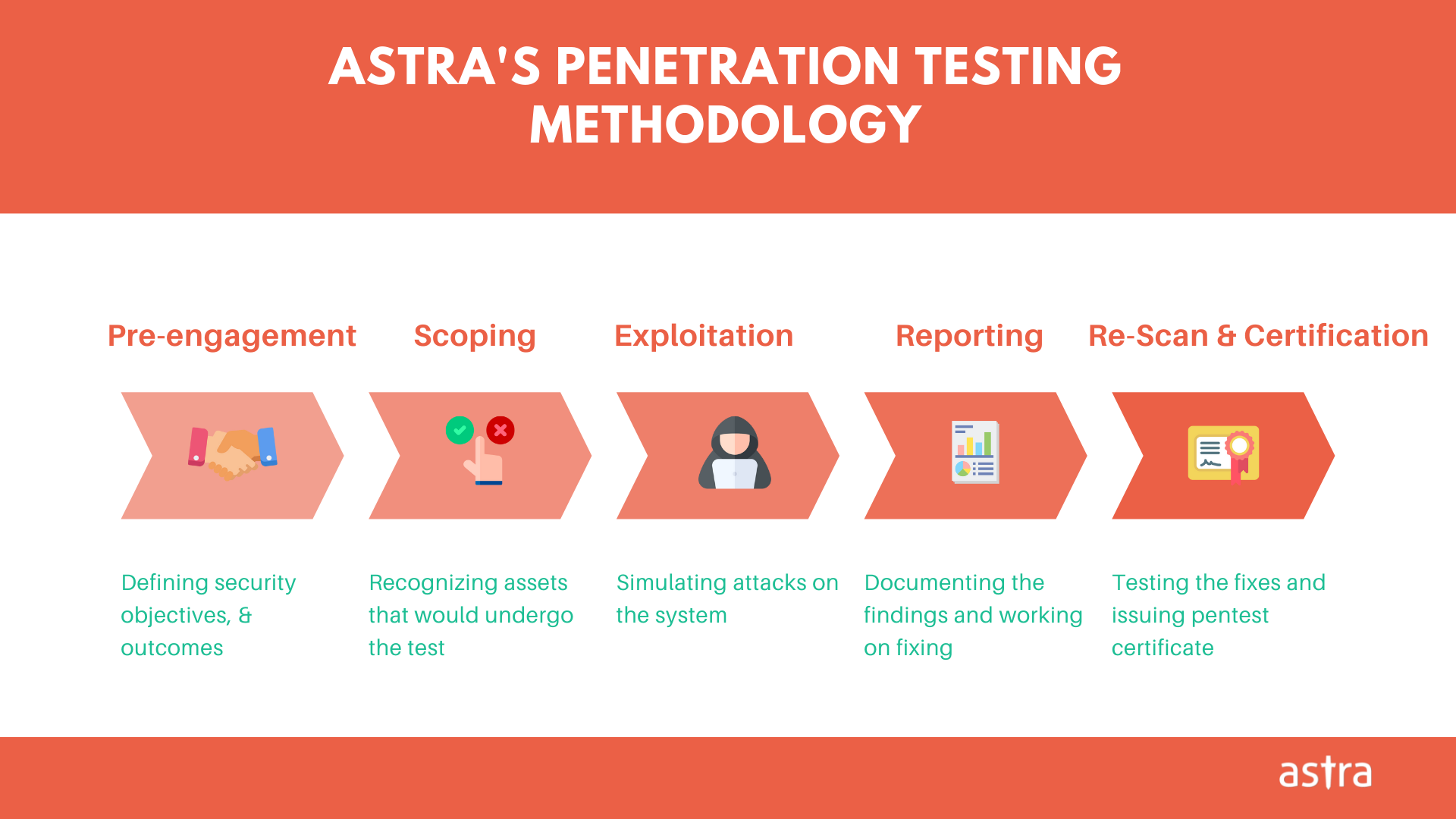
A Blockchain code audit is the systematic and structured code review of a blockchain development project which is executed manually. The process usually involves the extensive use of static code analysis tools. But the main responsibility of audit lies with the expert security professionals and blockchain developers to review the code to find bugs. Let’s take a glance at the various steps concerning the Blockchain auditing process.
1. Define goal of the target system
An ill-directed Blockchain security audit is worse than no audit. It leads to confusion, eats up time and ends without any solid result. To avoid being caught up in a direction less loop of a blockchain security audit, always define your audit goals before you start with the process.
A broad goal of a security audit, blockchain or else, is to identify security risks in your system, network and tech stack. You can also narrow down this goal to several smaller goals pertaining to different security areas and your specific needs. Also define the action plan that ought to follow the security audit. A predefined goal and action plan will prevent you (the auditor) from going haywire with the audit and keep your assessment on the right track right till the end.
2. Identify component(s) and associated data flow(s) of target system
The second step is to recognize the components and the associated data flow of the target system. Moreover, the auditing team also needs to understand the project along with its architecture and use case. A review of test plans and test cases is also necessary to perform a successful audit.
When you are undertaking a smart contract audit in Blockchain, you first need to lock down the source code version. This makes sure that there is transparency in the audit process. What’s more, this step also helps you to differentiate the version already audited compared to any new changes you render to the code. But it is important to document the version number(s).
3. Identifying potential security Risks
Blockchain applications have nodes and APIs that are accomplished by communicating over private and public networks. Nodes and their respective roles can differentiate in solutions as they are the communicating entities in the network of Blockchain. With the constant evolution of implementations and risks, organizations should consider reviewing the risks. Some of the potential security risks in blockchain are related to data, transactions, etc.
4. Threat modeling: Blockchain security audit
Threat modeling is one of the integral components of a blockchain security assessment. With threat modeling, potential system security issues can be identified more easily. To be precise, threat modeling can unearth data spoofing and data tampering. What’s more, it can also identify denial of service attacks on a Blockchain system. Being an integral part of the blockchain security audit, this step also identifies data manipulation.
5. Exploitation and remediation
The last step in the Blockchain security audit process is — Exploitation & Remediation. Exploitation of the vulnerabilities found in the above steps reveals the gravity of the risks. Exploitation, basically, is to identify the ease of exploiting a vulnerability and it’s manifestations on the system. However, Remediation deals in patching those vulnerabilities.
Professional blockchain security audit by Astra Security
If you are looking for a professional blockchain security assessment, then you can’t look past Astra Security. Once you subscribe to Astra’s security audit, Astra’s security experts will run over 1200 tests (including static and dynamic code analysis, configuration checks, network configuration flaws, permissions check, and so on) on your system.
You would also get access to a collaborative dashboard where you can check vulnerabilities reported in your Blockchain system on a real-time basis. In case you are patching the reported vulnerabilities, Astra security engineers will re-scan to make sure that all patches are working.
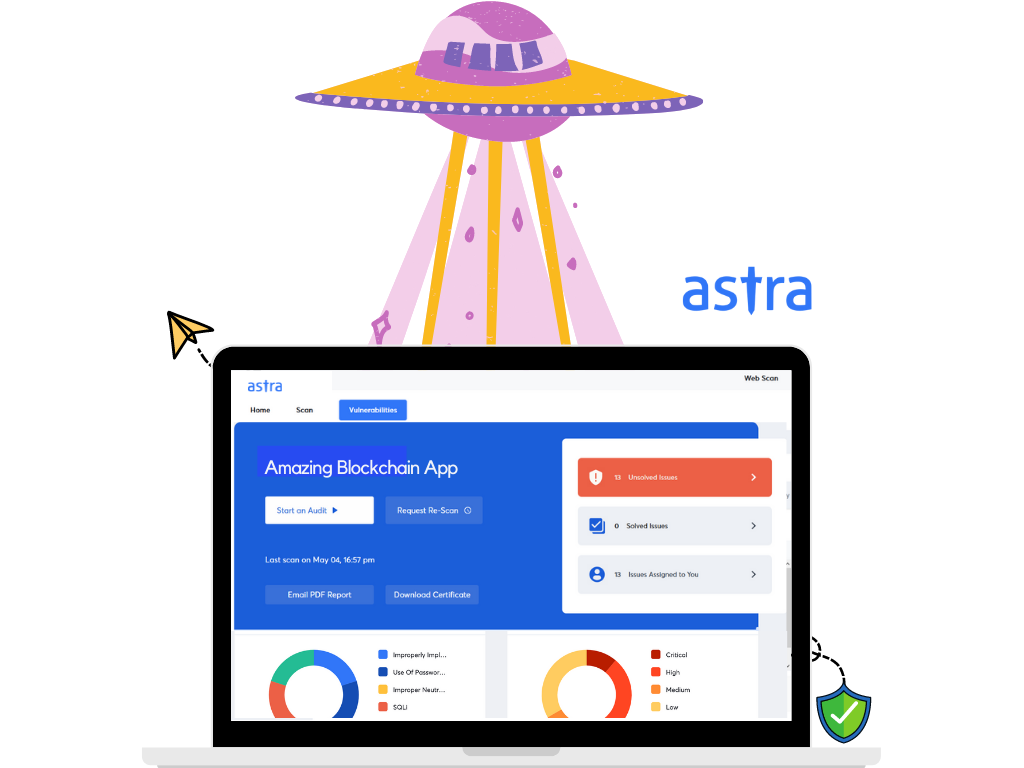
Astra Security’s Blockchain security model includes the following aspects.
- Secure Architecture Review: Astra analyses the basic architecture of your Blockchain system to eliminate probable security breaches from the initial design.
- Payment platforms review: Astra also reviews the technology and processes in the blockchain system with its exclusive and trusted governance framework.
- Security Assessment: The main goal of this security audit step is to identify issues related to smart contacts and apps.
- Review of APIs and SDKs: This phase comprises assessing the services which are hosting the platform.
A blockchain security audit is of great importance for your business. A complete assessment of your Blockchain system would let you know about the existing security loopholes and unpatched vulnerabilities. Opt for the affordable VAPT plans from Astra Security and get your Blockchain system tested today.
















