Over a million people across 190 countries use Amazon Web Services (AWS) to build and deploy different types of applications, store and manage valuable data, and other services. AWS has reduced hardships such as the need for on-premise data warehouses but not all cyber security threats. Hence, we must discuss penetration testing in AWS.
It is a critical aspect of cloud computing, as it helps to protect sensitive data and prevent unauthorized access. The company has put in place several tools, procedures, and security measures to protect the privacy, integrity, and accessibility of information and resources within the AWS ecosystem.
However, a security-first approach necessitates regular testing and scanning with popular AWS security tools which help reduce risks, provide a secure environment to run applications, store sensitive data in the cloud, and guard against unauthorized access.
List of Top 11 AWS Security Tools
- Astra Security
- Trend Micro Cloud One
- Alert Logic
- Sumo Logic
- Fortinet FortiGate
- Palo Alto Networks
- CloudTrail
- Intruder
- Invicti
- Acunetix
- Prowler
1. Astra Security
Astra Security is one of the major AWS security monitoring tools that can help find and correct holes and mistakes in your cloud configuration, and keep up with new hacks and CVEs with a constantly improving security engine.
To make sure best practices are being followed, compare your cloud setup against CIS and OWASP standards.
By collaborating contextually, you can connect with their security specialists and resolve problems more quickly than ever. With AWS cloud security tools, you can cover every important security standard, including CIS, CSA, OWASP, SANS, and CERT, among others. Astra Security is empanelled by CERT-In for providing information security auditing services.
From a single dashboard, you can manage vulnerabilities, evaluate risk, and allocate resources based on data to fix them.
Get a verified certificate and address the flaws that Astra’s AWS security services have discovered. Take pride in creating a safe organization.
Features
- Dashboard: Vulnerability management dashboard
- Actionable reports: accurate risk scores, guidelines, and video POCs
- Cloud networking check: isolation, encryption verification.
- CXO Friendly – Continues pentest with CXO Friendly dashboard
- Pricing: Custom packages designed as per your needs
What is Good?
- Vulnerability remediation and certificate acquisition
- Security and Performance Gap Analysis
- Collaborative Issue Resolution
- Optimized pentest for AWS/GCP/Azure
- Follow CIS & OWASP benchmark
Disadvantages
- Cost-effective Preemptive Measures
- Moderate complex integration
2. Trend Micro Cloud One
By integrating with the DevOps tools your company already uses, Trend Micro Cloud OneTM delivers security from commit to runtime across all major providers.
It helps you identify risks, comprehend their business implications, and address issues. For businesses experimenting with AWS, Cloud One is one of the major full-featured AWS cloud security tools.
Features
- ThreatSense: Actionable Threat Insights for AWS
- CloudArmor: Automated CSPM
- Open-source visibility: vulnerability, license monitoring.
- Pricing: Custom pricing with pay-as-you-go model
What is Good?
- Cloud Storage Security
- WorkloadShield
- ContainerSec+ for ECR and EKS
Disadvantages
- Production-Aware Updates
- Optimized Browser Performance
- Agent Uninstallation and SHA Management
3. Alert Logic

For AWS, on-premises, and hybrid infrastructures, Alert Logic MDR is one of the major fully managed AWS security tool and compliance solution suites.
With asset visibility, vulnerability assessment, threat detection and response, and web application security—all at an affordable price—Alert Logic helps you stay on top of your duties.
This AWS security monitoring tool provides configuration management to find weaknesses in your application stack that are hidden
Features
- Secure+ – Centralized AWS Log Analysis
- HybridSec- Hybrid Migration with Enhanced Security
- GuidedOptimize: Enhanced Management & Governance with AWS Well-Architected
- Pricing: Request on quote
What is Good?
- Advanced Threat Analysis Platform
- Managed Intrusion Detection Service
- Compliance-Ready Log Management
Disadvantages
- Enhance Documentation for Setup
- Customizable Alert Payloads
- Modernize UI and geo-location Enhancement
4. Sumo Logic
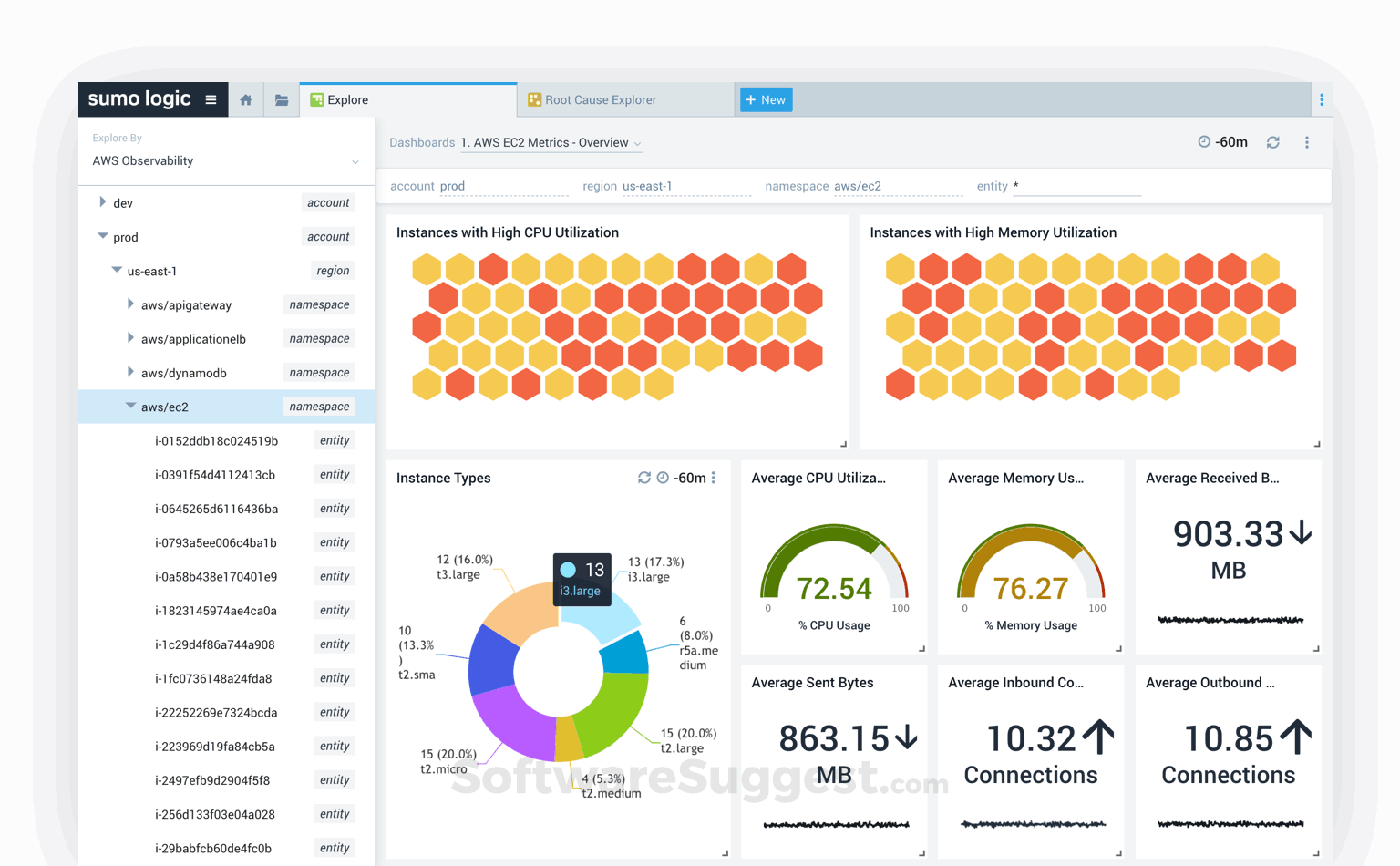
Sumo Logic is one of the major AWS security monitoring tools that provides compliance, security, and configuration management for your AWS architecture.
It is a full-stack SaaS SIEM that fuses analytics and automation to perform security analyst workflows and automatically triage security alerts and findings.
This is one of the AWS security tools that reduces the time to detect, investigate, and respond to threats in AWS and hybrid cloud environments.
Features
- Dashboard: Intuitive Threat Visualization Dashboard
- Monitoring: Simplified Multi-Service Monitoring
- Infrastructure: AWS Infrastructure Visualization & Optimization
- Pricing: Free plan available with paid pricing quotes given on request
What is Good?
- Lambda Data Ingestion Integration
- AWS Security Benchmarking with GuardDuty
- User Application Monitoring & Auditing
Disadvantages
- Expanded Query Language Support
- Simplified Advanced Feature Adoption
- Enhanced Scalability for Large Datasets
5. Fortinet FortiGate
Through their partnership with AWS, Fortinet guarantees one of the best AWS security assessment tools. Integrations with essential AWS services make security management simpler, guarantee full visibility across environments, and offer extensive, all-encompassing security.
The highest level of flexibility and control is provided by Fortinet’s security-driven networking, application and API protection, and cloud-native controls.
By enabling elastic scaling and streamlining deployment decisions, FortiFlex does away with the need to size precisely for services and solutions in advance.
Features
- FortiFlex: Flexible Protection with FortiFlex
- Agile: Dynamic Attack Surface in the public cloud
- FortiWeb Cloud: Instant Secure Protection
- Pricing: Quote on request
What is Good?
- Comprehensive Workload Visibility on AWS
- Flexible Usage-Based Licensing
- Threat-Informed FortiWeb Signatures
Disadvantages
- Improved Logging Services with Enhanced Details
- Easy FortiAP Installation Experience
- Scalability Challenges with FortiGate
6. Palo Alto Networks
For organizations starting their cloud journeys or modernizing applications using cloud-native technologies, Palo Alto Networks and Amazon Web Services (AWS) together make one of the best AWS security solutions.
You can benefit from the largest selection of market-available integrated cloud security solutions with Palo Alto Networks and AWS.
Features
- Cloud Security: Hybrid clouds are secured with cloud-native security.
- Modernization: Modernize Cloud Network Security
- Integration: VM-Series and AWS Design Integration
- Pricing: Quote on request
What is Good?
- User-friendly GUI
- advanced detection.
- Comprehensive documentation and admin guide.
Disadvantages
- Firmware updates ensure stability and security.
- Enhanced security features through upgrades.
- Challenging initial setup.
7. CloudTrail
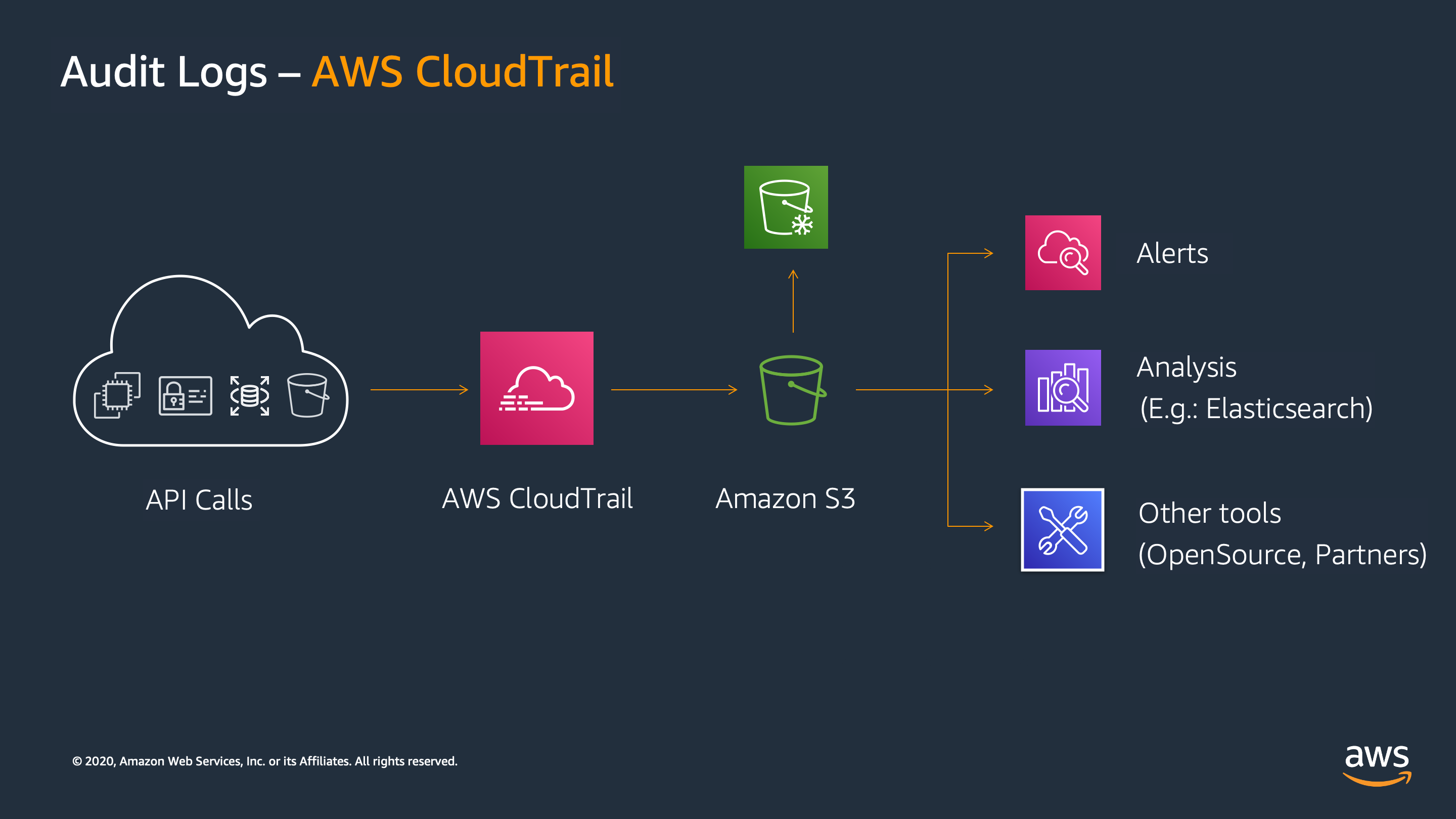
An AWS service called AWS CloudTrail assists you in setting up operational and risk auditing, governance, and compliance for your AWS account. Events in CloudTrail represent actions performed by a user, role, or AWS service.
Events consist of operations carried out through the AWS Management Console, AWS Command Line Interface, and AWS SDKs and APIs. The best practices for security and operations revolve around visibility into your AWS account activity.
Features
- Integration: API-based CloudTrail Integration and Automation
- Trailblaze: CloudTrail Account Activity Analysis
- Analysis: Comprehensive Activity Analysis for AWS
- Pricing: Free Version with custom paid packages available
What is Good?
- Convenient Event History Viewing
- Powerful Event Data Storage
- Flexible Event Integration with CloudTrail Lake
Disadvantages
- Enhanced Graphs and Tool Integration
- Streamlined Activity Filtering in CloudTrail
- Enhance log management with interfaces.
8. Intruder
Intruder is a cloud-based vulnerability scanning platform and top AWS penetration testing tool that can be used to check for known vulnerabilities in your AWS environment to reduce your attack surface.
This AWS security provider is easy to use and can be integrated into your existing security workflow. It also provides detailed remediation recommendations to help you fix vulnerabilities quickly and effectively.
Features
- Continuous scanning: Identify and report new vulnerabilities as they emerge
- Automated penetration testing: Identify vulnerabilities vulnerability scanners may miss
- Compliance Reporting: Generate compliance-tailored reports for standards like PCI DSS and HIPAA
- Pricing: Quote on trial
What is Good?
- Convenient and Easy to Use
- Comprehensive Coverage
- Continuous Monitoring
Disadvantages
- Limited Integration
- Potential for False Positives
- Limited Scope for Remediation
9. Invicti
Invicti is a comprehensive web application security scanner that can identify and report on a wide range of vulnerabilities. It can scan a wide range of web applications and APIs, including those hosted on AWS.
Features:
- Comprehensive Scanning: It employs a variety of techniques, including DAST, SAST, and IAST, to uncover a comprehensive spectrum of CVEs
- Automated Reporting: Generate detailed and actionable reports of the identified vulnerabilities
- Integration with AWS Services: It seamlessly integrates with a range of AWS services, such as AWS IAM and CloudTrail.
- Pricing: Quote on request
What is Good?
- User-friendly Interface
- Customizable Scans
- High Scalability
Disadvantages
- Limited Support for AWS-Specific Vulnerabilities
- Potential for False Positives
- Limited Scope for Remediation
10. Acunetix
Acunetix is a web vulnerability scanner that can be used to identify and remediate vulnerabilities in web applications and APIs, including those hosted on AWS.
It offers a comprehensive set of functionalities with detection capabilities for various vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure direct object references (IDOR)
It can be integrated with several other security tools, such as vulnerability management systems and firewalls.
Features:
- Manual testing: Test web applications and APIs that cannot be automatically scanned, with manual pentesting.
- Reporting: It generates detailed reports that include information about the vulnerabilities found, as well as recommendations for remediation
- Integration: Integrate with several other security tools, such as vulnerability management systems and firewalls.
- Pricing: Quote on request
What is Good?
- Ease of Use
- Accuracy
- High Scalability
Disadvantages
- Limited Support for AWS-Specific Vulnerabilities
- Potential for False Positives
- High Complexity
11. Prowler

Prowler is an open-source security assessment, auditing, hardening, and forensics readiness tool that helps you identify and remediate security risks in your AWS environment. It is a popular choice when choosing an AWS security software.
It covers a wide range of AWS security best practices, including those from CIS, NIST 800, NIST CSF, CISA, FedRAMP, PCI-DSS, GDPR, HIPAA, FFIEC, SOC2, GXP, Well-Architected Security, ENS, and more.
It also has an active community of users and contributors.
Features:
- Hardening and Forensics Readiness: Harden your AWS environment against potential attacks and prepare for forensic investigations in case of a security incident.
- Granular Reporting: Generate detailed reports that allow you to drill down into the details of each risk.
- Automated Remediation: Automatically remediate some of the identified security risks to streamline the security process and reduce the risk of human error.
- Pricing: Open-source tool
What is Good?
- Ease of Use
- Continuous Integration
- Compliance with Multiple Standards
Disadvantages
- Challenging initial setup
- High Complexity
- Potential for False Positives
Importance of AWS Cloud Security tools
1. Enhanced Data Protection
AWS security tools provide the most complete range of services, tools, and knowledge to assist you in protecting your data.
You have complete control over your data with AWS, using its robust services and AWS security tools to choose where it is kept, how it is protected, and who has access to it.
By offering services and features, such as advanced access, encryption, and logging features, that enable you to implement your own privacy controls, they continuously raise the bar on privacy protections.
2. Threat Detection and Incident Response
You should review your security posture before switching to the cloud to determine what adjustments and controls must be made in order to operate securely.
Together, Amazon GuardDuty and AWS Security Hub give AWS accounts and workloads continuous visibility, compliance, and threat detection.
With AWS security tools’ continuous monitoring for malicious activity on your AWS accounts and workloads, Amazon GuardDuty is a threat detection service that provides detailed security findings for visibility and remediation.
3. Secure Development Lifecycle
Developers can efficiently manage user permissions and secure resources due to IAM’s fine-grained access control capability.
By assessing and tracking resource configurations, AWS Config helps detect any deviations from desired settings, promoting a secure and compliant infrastructure.
The monitoring and logging of API activity by AWS security tools helps with auditing and compliance efforts by providing detailed information on who did what and when.
4. Centralized Security Management
Using pre-packaged guardrails and centralized log management, AWS Control Tower automates the creation of a secure, multi-account AWS environment.
An intelligent threat detection service called Amazon GuardDuty keeps an eye out for suspicious activity and potential data breaches in AWS accounts.
For Amazon EC2 instances, Amazon Inspector is an automated security assessment service that finds vulnerabilities and provides prioritized security findings.
By enabling the exchange of events and enabling actions to be triggered in response to security incidents, Amazon CloudWatch Events supports cross-account incident response.
Features of AWS Security Tools
1. Identity and Access Management
You can specify who or what can access AWS services and resources, manage fine-grained permissions centrally, and use access analysis to fine-tune permissions across AWS with AWS Identity and Access Management (IAM).
AWS security testing tools utilize IAM to securely manage and scale workloads and workforce access, enhancing your AWS agility and innovation.
Using attribute-based access control, you can create granular permissions based on user attributes like department, job role, and team name.
Create permission boundaries for IAM users and roles using service control policies, and implement a data perimeter around your accounts in AWS Organizations.
2. Virtual Private Cloud
The infrastructure that powers AWS services in the AWS Cloud must be protected, and that is AWS’s responsibility.
By using AWS security testing tools, you gain access to a data center and network architecture designed to satisfy the needs of businesses with the highest security standards.
As part of the AWS Compliance Programs, external auditors test and confirm our security’s efficacy on a regular basis.
3. AWS GuardDuty
Use anomaly detection, machine learning, behavioral modeling, and threat intelligence feeds from AWS and top AWS security testing tools to quickly expose threats.
Monitor your AWS accounts, instances, serverless and container workloads, users, databases, and storage for potential threats on a continuous basis.
By examining Amazon EKS audit logs and container runtime activity, you can find and profile potential malicious or suspicious behavior in container workloads.
Check Amazon Elastic Block Store (EBS) for files that might contain malware causing odd behavior in instance and container workloads running on Amazon Elastic Compute Cloud (EC2).
4. AWS Secrets Manager
You can manage, retrieve, and rotate database credentials, API keys, and other secrets throughout their lifetimes with the help of AWS Secrets Manager.
With AWS security testing tools, utilize resource-based policies and fine-grained AWS Identity and Access Management (IAM) to control who has access to secrets.
Secrets can be rotated on demand or according to a schedule without redeploying or interfering with running applications.
AWS logging, monitoring, and notification services can be integrated with secrets.
5. AWS KMS (Key Management Service)
You can create, manage, and control cryptographic keys across your applications and AWS services using the AWS Key Management Service (AWS KMS).
With AWS security testing tools, you can utilize KMS keys that you manage and control, enable server-side encryption with AWS KMS.
When handling cryptographic operations in your applications, use the AWS Encryption SDK to ensure security.
Asymmetric KMS keys are used to secure signing operations with AWS KMS.
What are the key security measures in AWS?
At AWS, cloud security is given top priority.
AWS is assisting organizations as they transform security, identity, and compliance into crucial business enablers as they embrace the scalability and flexibility of the cloud.
In order to help businesses meet their specific security needs in the cloud, AWS incorporates security into the core of our cloud infrastructure and provides a range of foundational services.
AWS complies with a broad range of security guidelines and compliance certifications recognized by the industry, including ISO 27001, SOC 2, and HIPAA.
To help customers comply with their own regulatory requirements, AWS also offers compliance-specific features and documentation.
Through network security, configuration management, access control, and data encryption, AWS offers security-specific tools and features.
Users can define precise network access controls with AWS’s Virtual Private Cloud (VPC), enabling isolated network environments to be created.
What are AWS security testing tools?
To help safeguard data and protect resources inside its cloud infrastructure, AWS (Amazon Web Services) provides a complete set of security tools.
A popular security tool is AWS Security Hub, which offers a central dashboard to track security alerts and compliance status across various AWS accounts.
It connects to a variety of AWS services and outside security programs, compiling data and producing useful insights.
The management of user access rights and permissions to AWS resources is handled by AWS Identity and Access Management (IAM), which is a further crucial tool.
The combined use of these tools improves AWS users’ security posture.

Conclusion
For organizations using Amazon Web Services, AWS security tools are crucial for ensuring the confidentiality, integrity, and accessibility of their data and resources.
Each tool — whether it is Astra or CloudTrail — has its own special features, such as centralized security management, data protection, access control, threat detection, and vulnerability management.
In the AWS environment, these tools are essential for improving data security, threat detection, the secure development lifecycle, and centralized security management.
FAQs
How to implement security in AWS?
Security in AWS can be implemented by following these measures:
1. Securing access through MFA and strong passwords.
2. Having regular data backups and strong data encryption in place.
How secure is AWS?
AWS cloud services comply with most of the regulatory standards around the globe including HIPAA, NIST, GDPR, and PCI-DSS.
What are the risks associated with AWS?
The most common risks associated with AWS are improper understanding of liability, weak IAM, and data encryption.
















