The number of data breaches in the USA in the first three quarters of 2022 was significantly lower than in 2021. Does this mean that the hackers have slowed down or that businesses have become more security conscious in the post-pandemic era? There simply isn’t enough data to answer the question accurately. What we can say for sure is that penetration testing services have made a contribution to this progress.
What is a web application penetration testing service?
A web application penetration testing service is a third-party organization that performs regulated hacker-style attacks on your web applications to find out ways to breach your security or vulnerabilities. The web pentest service provider detects the vulnerabilities, qualifies them based on their exploitability, and helps you find ways of getting rid of them.
In this post, we will discuss 13 of the best web application pentest service providers around the globe, and help you understand how you can choose the one that suits your business the best.
The 13 web app pentest services covered in the post
- Astra’s Pentest
- Intruder
- Burp Suite
- Nessus
- Indusface WAS
- Acunetix
- Breachlock
- Veracode
- Cobalt
- Probely
- Qualys
- Cipher Security
- Rapid7
What are the features you should look for in a web application penetration service provider?
Each pentest provider brings some unique features to the table and some features that they all share. You should have a clear picture of your requirements to determine the best web app pentest service for your business.
Nevertheless, some pentesting companies go the extra mile to bring some features that make it easier for you to get the most out of a pentest. They try to make it easier for you and minimize the time and resources required from your end.
An all-purpose pentest dashboard
Managing your vulnerabilities is easier when you have a clear understanding of their status and easy access to the analytics related to the vulnerability assessment and pentest.
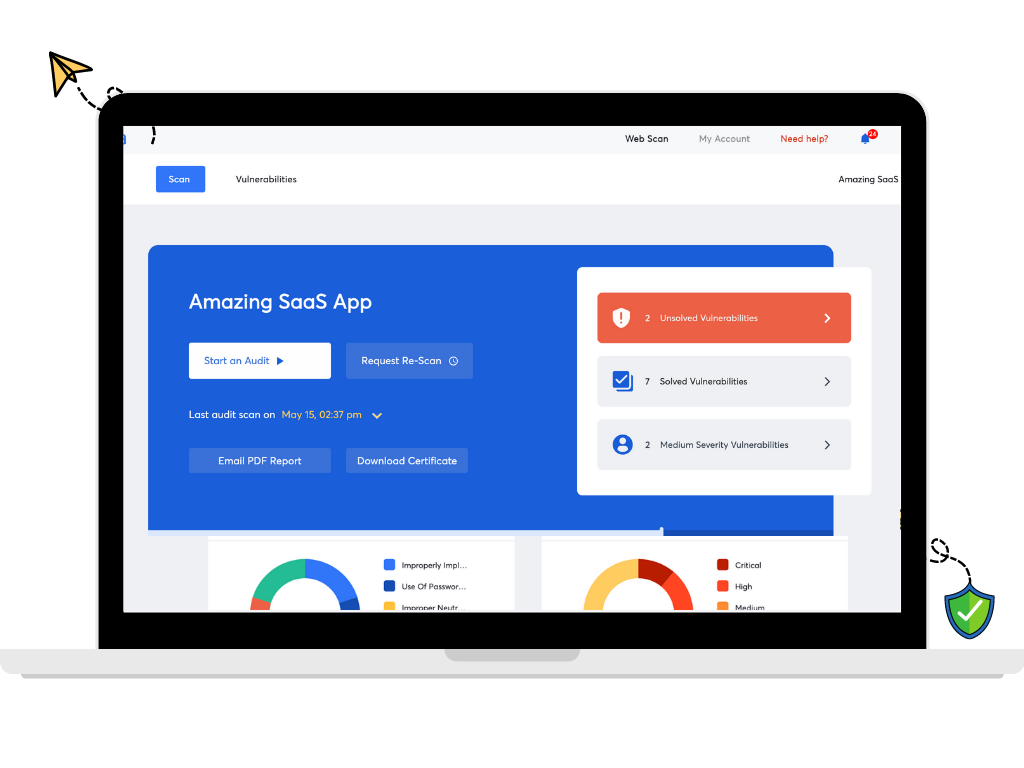
An interactive dashboard that allows you to monitor and manage vulnerabilities and helps you communicate with security experts reduces the time spent in long mail trails and jumping between multiple channels of communication.
Integration with your SDLC
Fast development cycles often result in negligence toward security. Having an integrated security suite that alerts you about the emergence of new vulnerabilities before you push new code can be really helpful.
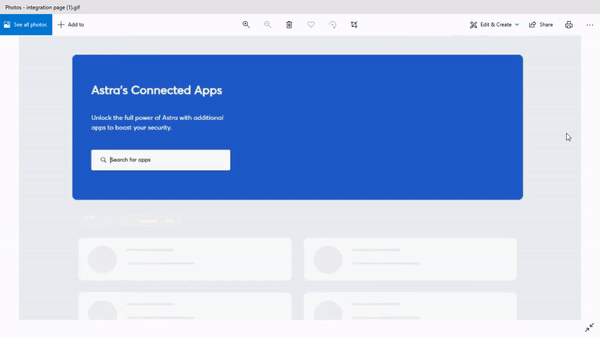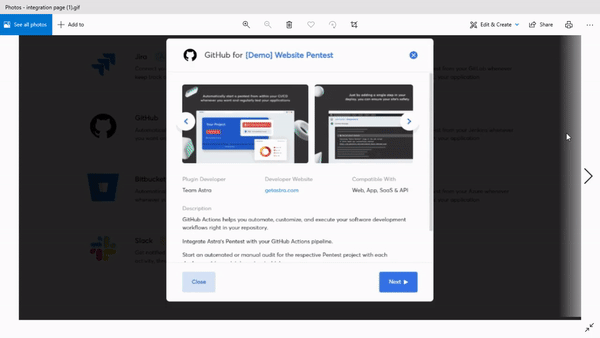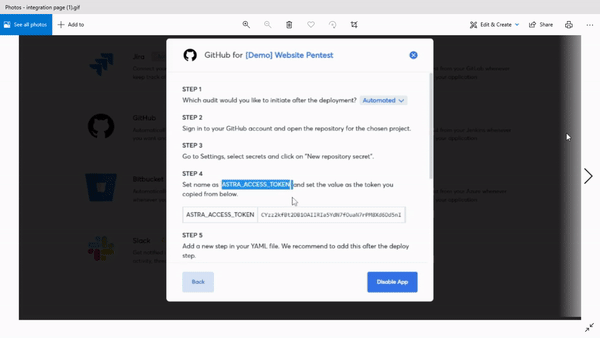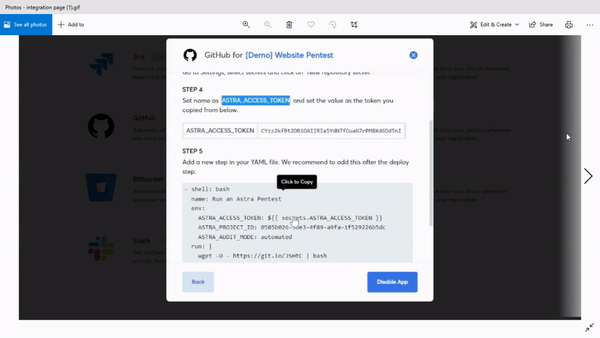
Vetted pentest to ensure zero false positives
A false positive is when a vulnerability scanning system flags issues that do not actually exist or even if they do they are not vulnerabilities. False positives waste a lot of time and resources. So, if a web application penetration testing service offers vetted scans to ensure zero false positives, that is something you do want.
Collaboration with security experts
You want to work with a penetration testing company that doesn’t just find issues but also helps you fix those issues by allowing you to communicate and collaborate with security experts.
Scan behind logged-in pages
Scanning behind logged-in pages doesn’t seem like a big deal, but if you have to authenticate the scanner every time the session runs out, then having an automated scan stops making much sense. If a company offers a way of automatic authentication of scanners while scanning behind the login, you should definitely look into it.
Reports that trigger action
Pentest reports should be easy to read and interpret. They should prompt the developers as well as the executives to action. A report should be simple enough for non-technical executives to understand the risk and detailed enough for developers to get going. Make sure you check a sample report before you choose a web application security services.
Read more on Astra’s Pentesting Reports
Top 13 web application pentest services around the world
We are finally there. By now, you’ve surely built up some expectations – things that you would want for your web application from a security testing service provider. Read ahead and find out which of the top pentest services meet your requirements.
Astra Web App Pentest Platform
Find and fix every vulnerability in your web app with Astra’s pentest platform
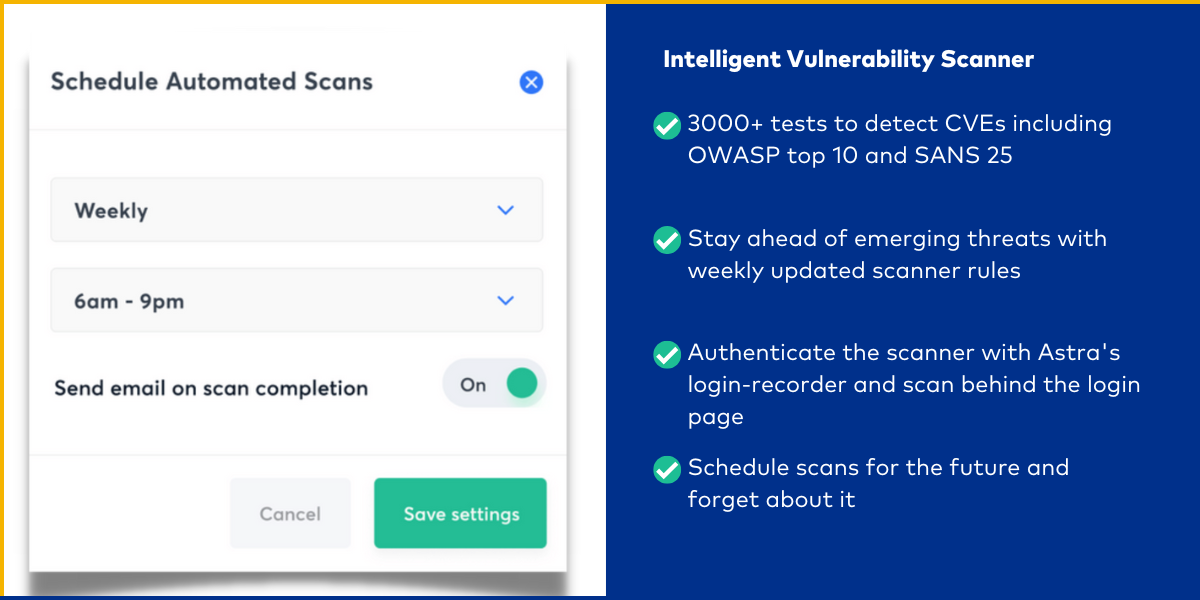
Intelligent vulnerability scanner
Root out a wide range of CVEs, get actionable risk scores, and prioritize vulnerabilities based on ROI. Integrate the scanner with your SDLC to run continuous scans. Never miss a single vulnerability.
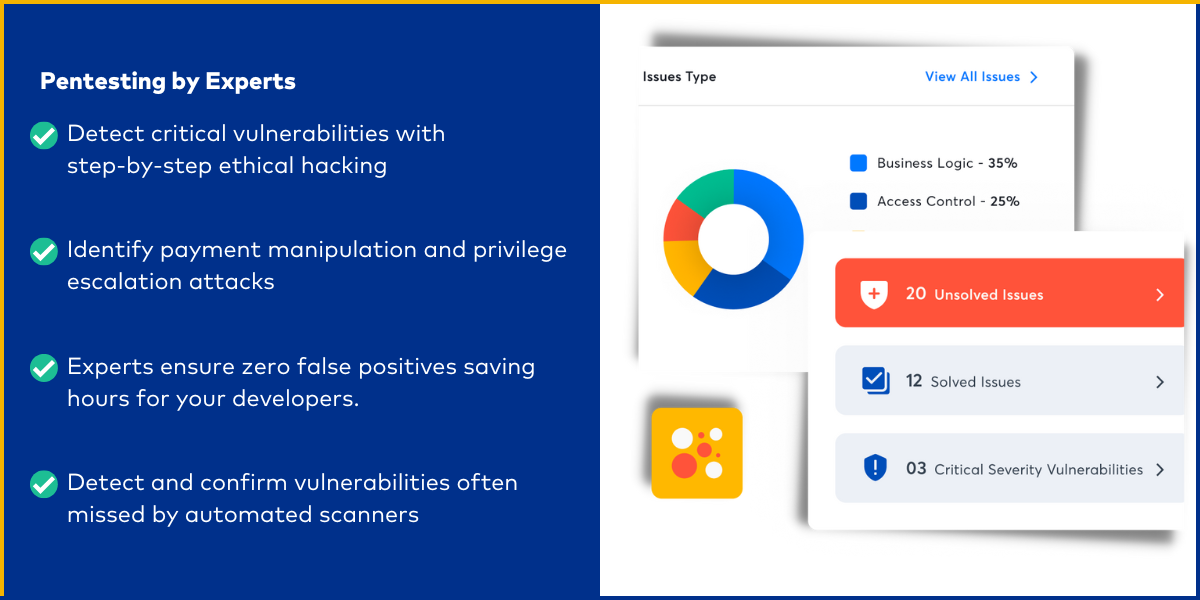
Pentest by Experts
Detect vulnerabilities missed by automated scanners. Get rid of business logic errors. Astra Builds on your previous pentest data to create an optimal pentest solution for your business.
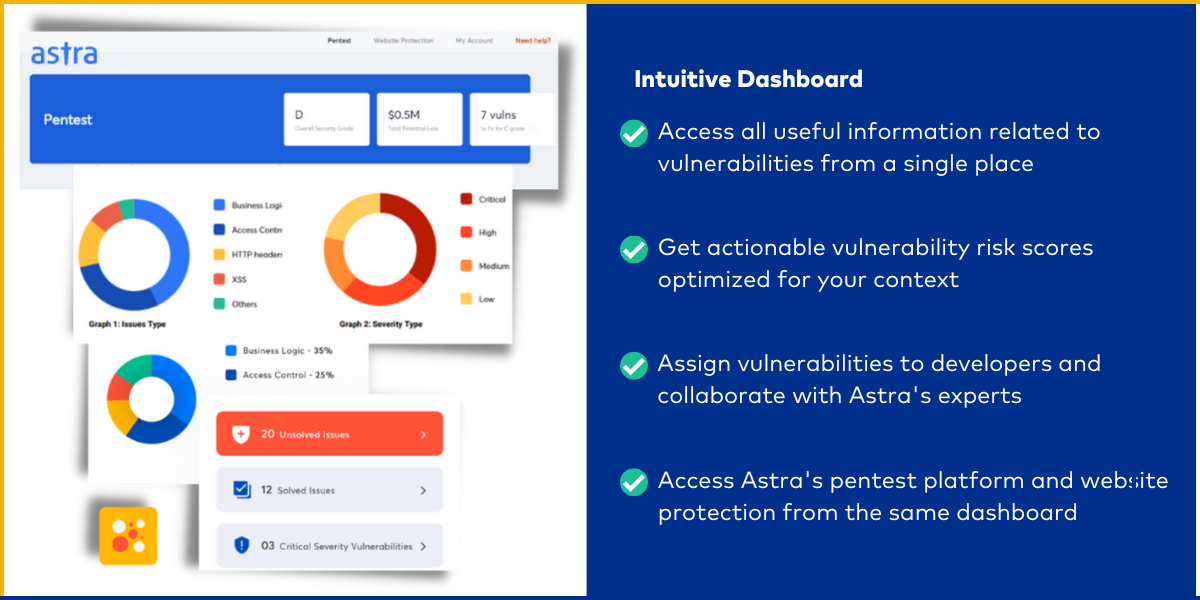
Interactive dashboard
You can use Astra’s pentest dashboard to access all information related to your vulnerability scans – monitor and update their status, observe graphical risk analytics, and communicate with developers.
Integrations
Astra’s pentest platform integrates with GitHub, GitLab, Jenkins, and BitBucket so you can automate scans before every build. Enhance workflow management through Slack and Jira integrations.

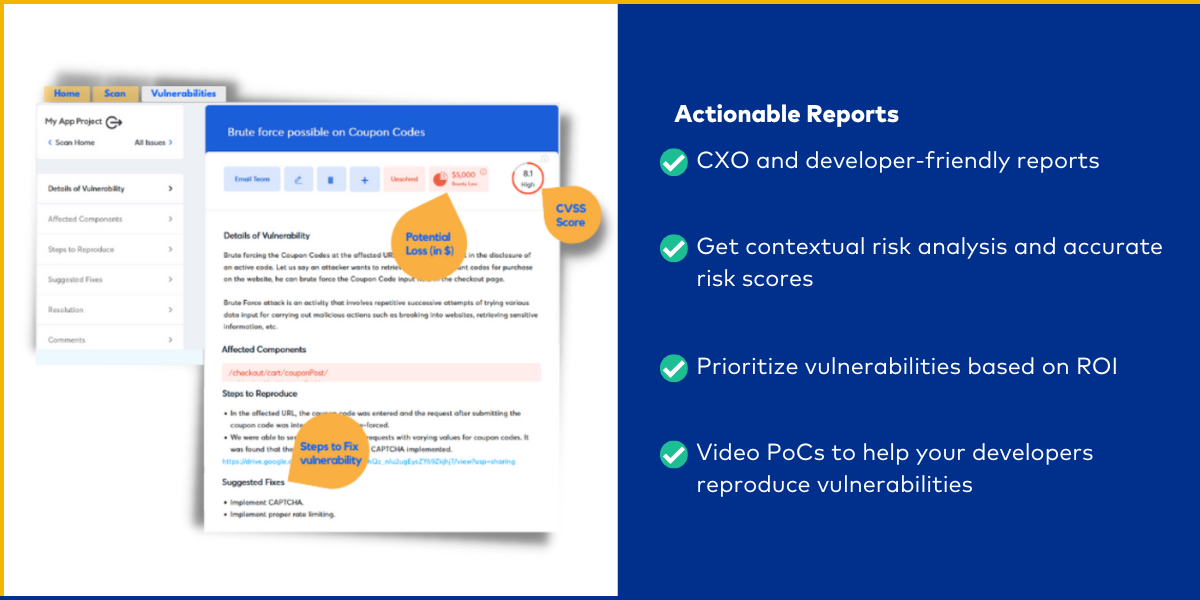
Actionable pentest reports
Astra’s pentest reports prioritize critical vulnerabilities, explain the test cases, and combine CVSS scores and contextual risk analysis to come up with accurate risk scores.
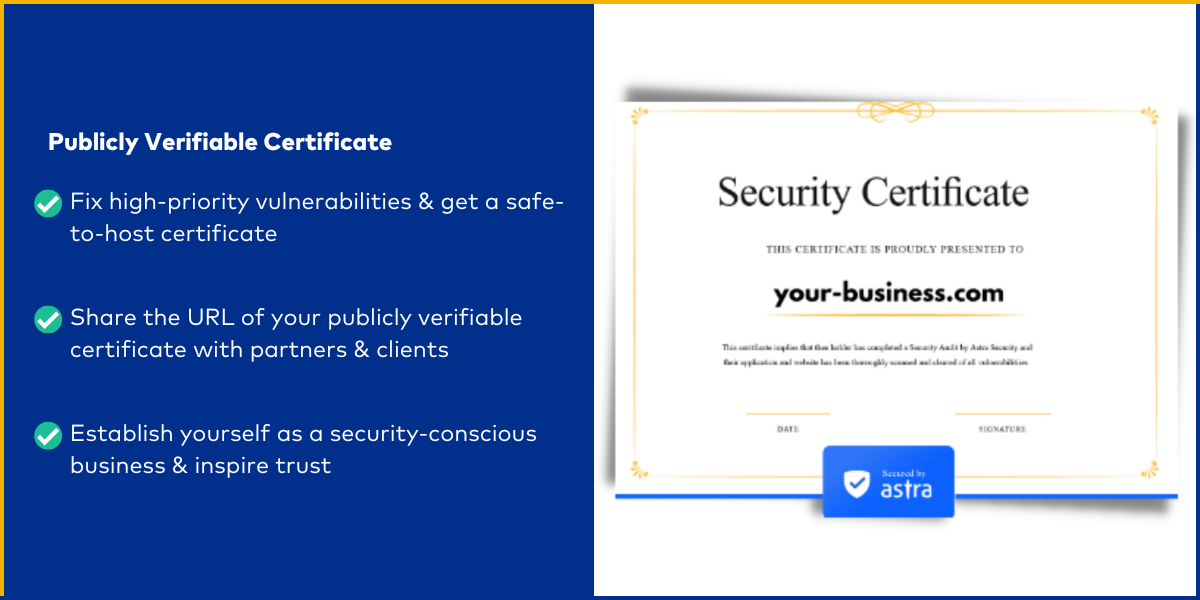
Pentest certificate
Once all the high-priority vulnerabilities detected by Astra pentest are fixed and the same is verified in a rescan, you get a publicly verifiable certificate that attests to your trustworthiness.
This is how users feel about us

2. Intruder
Intruder helps you scan your publicly and privately available assets like cloud systems, websites, endpoint devices, etc. It is a great tool to find misconfigurations, encryption errors, SQL injections, and CSS, along with a wide range of CVEs.
Intruder has a solid program for web application scanning and you can also avail of a penetration test for a higher price. It helps you streamline your security, find risk across your technology stack, and become compliance ready.
Here are some key features
- Continuous monitoring of attack surfaces.
- Coverage of OWASP top 10 vulnerabilities and more.
- Comprehensive security checks.
- Monitors alterations in the attack surfaces.
- Cloud vulnerability scanning capabilities
3. Burp Suite
Burp Suite is a security testing suite by Portswigger. It has a community edition that provides you with some useful tools for manual pentest. What we are going to talk about here is the enterprise edition of Burp Suite that packs the capabilities of integrated security testing.
Much like Astra, Burp Suite gives you the opportunity to collaborate with AppSec experts to fix security bugs. Burp Suite has an always-on scanning feature that smartly prioritizes vulnerabilities helping you plan and execute the fixes without exhausting your resources.
Here are some key features
- Customized scans to track tricky security bugs
- Always-on scanning so that vulnerabilities do not stack up.
- Fewer false positives to avoid alert fatigue
- Automated scans along your portfolio.
- Easy deployment of the vulnerability scanner
4. Nessus
Tenable Nessus helps you extend your security assessment from traditional IT assets to cloud infrastructures. It keeps the zero false positives low while also covering a wide range of vulnerabilities.

Nessus has been in the market for over 20 years and improved its service offerings based on community feedback to become one of the most trusted vulnerability assessment services.
Here are the key features
- You can deploy it in a variety of environments
- Assess cloud infrastructure security
- External attack surface scanning
- Pre-built scanning policies
- Customizable reporting
Check Out: Best Tenable Alternative
5. Indusface WAS
Indusface WAS combines automated scanning and manual pentesting to help you detect all OWASP top 10 vulnerabilities and business logic errors. Much like Astra, Indusface also promises zero false positives and provides remediation assistance.
The scanner built by Indusface is focused on scanning single-page applications and they offer intelligent crawling. It offers you unlimited scans and detects application vulnerabilities validated by OWASP and WASC.
Here are some key features
- Zero false positives ensured along with PoC for each vulnerability
- Audits for business logic-oriented vulnerabilities
- Indusface WAS detects blacklisting
- Optimized for single-page applications
6. Acunetix
Acunetix is a fast vulnerability scanner specifically designed for efficiency. They promise you 90% of the scan results by the time the scan is halfway done. It helps you scan multiple environments simultaneously and prioritize vulnerabilities.
One of the best parts of its service offerings is that it shows you the exact lines of code that need to be fixed in order to get rid of a vulnerability. While Acunetix gives your developers a fair bit of remediation guidance, it doesn’t allow you to collaborate with AppSec professionals.
Some key features include
- Pinpoints vulnerability locations
- Minimal false positives ensured
- Optimized for single-page applications and script-heave sites
- Deployable on-premise or in the cloud
7. Breachlock
Breachlock offers Penetration Testing as a Service or PTaaS. It is a SaaS platform that allows you to request a pentest and after the penetration test is conducted you can avail of monthly scans through the same SaaS platform.

Breachlock has a team of ethical hackers who conduct AI-augmented web app pentest to give you a comprehensive picture of your security posture and certifies you for having conducted a pentest.
The key features include
- Certified ethical hackers
- Automated patch validation
- Fast remediation and compliance readiness support
- Continuous addition of risk checks
8. Veracode
Veracode is a continuous software security platform that checks your web app for vulnerabilities throughout the development process. It helps you with DevSecOps management by integrating security with the software development life cycle.

Veracode provides a holistic picture of the security posture across the entire application stack. On top of that, risk management and compliance assistance, and governance assistance features make it a great choice.
Key features include
- Continuous scanning
- Prediction of future vulnerabilities with the help of machine learning
- Streamlined data governance and risk management processes
- Elastic scalability for cloud-native applications
9. Cobalt
Cobalt is another provider of penetration testing as a service. They connect your organization with the global community of vetted penetration testers whose pentesting skills are suitable for your tech stack.

Cobalt’s SaaS platform helps you gather real-time insights so that your teams can get on with the remediation quickly. It helps you with web app pentesting, mobile app pentesting, cloud scanning, and API pentesting.
Some key features are
- Agile penetration testing
- Accelerated find to fix cycles
- A data-driven approach to pentesting
Also Read- Top Cobalt Alternative and Competitor
10. Probely
Probely is designed for web application scanning and API scanning. They say, using Probely is like adding a virtual specialist to your team. We will let you be the judge after you look at the features.
Probely automatically prioritizes vulnerabilities based on the risk of the vulnerabilities and provides proof of legitimacy for each issue.
Some key features include
- CI/CD integration
- Spider crawler that crawls JavaScript apps and single-page apps with ease
- Detailed management reports assisting compliance audits
- Interactive dashboard
- Scalable application scanning
11. Qualys
Qualys is a potent network security platform that helps you discover and secure all your IT assets, cloud apps, and network devices.
It also has a solid web application security offering which helps you with continuous protection and intelligent security insights.
Key features include
- Full clarity into your data center assets
- Monitors your environment and sends alerts for malicious activity
- Exhaustive iterative testing
- Fully cloud-based security platform
12. Cipher Security
Cipher Security is a provider of managed security services or MSS. They tailor their approach to security testing for each client – their business model, and compliance requirements. Cipher has optimized services for different industries like Finance, Healthcare, Logistics, Gaming, etc.
Their managed detection and response system is called CipherBox. It is an end-to-end solution that helps with 24/7 monitoring and response.
Key features of Cipher Security are:
- Managed detection and response
- Governance and risk management services
- Red teaming
- IoT security
13. Rapid7
This vulnerability assessment service provider has a range of services dedicated to web application security. They configure the scans, schedule them, validate the findings, and remove false positives.
They optimize the vulnerability scans based on your compliance requirements. These things apart, Rapid7 also provides business logic testing that is otherwise impossible with a vulnerability scanner.
Here are the key features
- Automated vulnerability assessment for maximum coverage
- Business logic validation
- Implementing vulnerability filters
- Full visibility of assets
Also Read- Comparison between Qualys and Rapid7
To sum it up
By now you have learned about some of the best web application penetration testing service providers, and the features you should look for when choosing such services. If you are not completely certain about the best fit or need some clarity about your own requirements and would like to talk to a security expert, you can schedule a call right away.
How much does a web application penetration service cost?
The cost of getting a web application penetration testing service should be between $2000 to $5000 per year depending on the size of the company and the scope of testing.
Does a web application penetration testing service take care of compliance audits?
No, compliance audits are done separately by vetted auditors. Nevertheless, a penetration testing service can help you get ready for a compliance audit.
Who gets a penetration testing certificate?
A web application penetration testing service provider can award a pentest certificate after all the critical vulnerabilities are fixed and the same is verified by security experts.
















