More and more legacy brands are looking at digital transformation and saying ‘yes’ to cloud. Startups begin their journey with the cloud. With increased adoption comes the question of safety. Cloud Security Alliance researchers reported that only 4% of organizations surveyed have sufficient security for 100% of their data in the cloud.
So how can your company improve its security posture for the cloud infrastructure? This is where cloud security tools come in!
Not only do these cloud security solutions help safeguard your data, but they also help meet compliance requirements, necessary for reassuring all the involved stakeholders of the safety of their information, while giving your firm the occasional competitive advantage.
Best cloud security tools in 2024
What features should you look for in a cloud security tool?
Visibility and Tracking
With multiple assets, users, and stakeholders, holistic visibility, control and monitoring of your data is absolutely essential. As a thumb rule, configure your Identity and Access Management controls to Zero Trust by implementing Multi-Factor Authentication and Role-Based Access.
This ensures a higher standard of authorization, along with implementation of the Principle of Least Privilege, which states, that users should only have access to information nd assets, they need to carry out their duties successfully, and no more.
Leverage Data Encryption
A cloud security tool that encrypts your data both in rest and in motion, helps add another layer of protection, especially in case of a breach. This translates to protection even in the case of unauthorized access and modifications.
Thus, while choosing your provider, choose a tool that offers strong encryption models with AIML capabilities and easy key management solutions.
Seamless Integration
Since cloud computing is based on a shared responsibility model, your cloud security tool should offer for native integration not just with your cloud space, but also with the native security tools launched by the vendor.
For example, in case you use Azure, your cloud security tool needs to integrate with not just your Azure Infrastructre but also Security Center, to identify risks and configuration issues specific to the particular cloud.
Threat Detection & Alert Feed
With complex cloud environments, your cloud infrastructure is more vulnerable to new, emerging, and existing threats than ever. This means that as a company, you need to always keep track of every threat to ensure a quick & coordinated response.
As such, your cloud security tool should not only generate automatic security alerts but also offer real-time threat intelligence feeds and track security scores to help you keep track of your security posture while highlighting any priority issues.
10 Best cloud security software for 2024
1. Astra Security
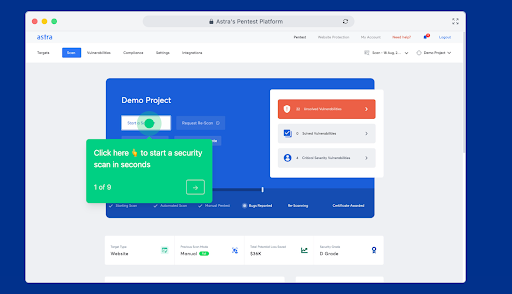
Astra is a leading SaaS company that specializes in providing innovative cloud security solutions. Our comprehensive suite of cybersecurity solutions blends automation and manual expertise to run 8000+ tests and compliance checks, ensuring complete safety, irrespective of the threat and attack location.
Key features:
- Platform – Online
- Manual pentest – Available for cloud infrastructures
- Accuracy – Zero false positives
- Vulnerability management – Comes with dynamic vulnerability management dashboard
- Compliance – Helps you stay compliant with PCI-DSS, HIPAA, ISO27001, and SOC2
- Price – Customised plans
Comprehensive Testing
Astra offers customizable pentest reports that can be downloaded in multiple formats including PDFs, and XLS. They provide an executive summary of vulnerability findings with their risk level and CVSS scores, along with detailed steps for remediation.
Industry-recognized certification
Astra provides a Pentest Certificate which can be publicly verified by the target’s customers to ensure the validity and security standards of the organization. The certificate is valid for 6 months or until the next major code update, whichever is earlier.
CXO friendly Dashboard
Astra Pentest boasts an easy-to-navigate CXO-friendly dashboard that displays the vulnerabilities in real time. Members of the development team can be added to the dashboard to collaborate with pentesters for quicker vulnerability resolution.
Pros
- Tests your cloud system for 8000+ different vulnerabilities and hacks.
- Secures systems to achieve GDPR, HIPAA, SOC-2, and ISO 27001 compliance.
- Offers unlimited continuous scans and zero false positives.
- Collaborative remediation with 24/7 human support from security experts.
- Automated scanning behind log-in pages.
Cons
- No free trial.
2. Commvault
Commvault is an automated cloud security tool that actively secures, defends and recovers your data, applications, and workload across cloud, SaaS, on-premise, and hybrid cloud environments.
Key features:
- Threat monitoring – Advanced ML differentiates between actual threats and false positives and deploys honeypot technology.
- File anomaly detection – Alerts admins on threshold breaches.
- Focused views – Monitors surface critical events using advanced pattern-identifying algorithms.
Pros
- Offers data security and availability across hybrid and multi-cloud environments.
- Broad network coverage with software, appliance, and SaaS offerings.
- Quick recovery across workloads deliver the highest level of business continuity across enterprise data.
Cons
- The interface can be challenging for first-time and non-technical users.
- The file anomaly alert algorithm is not highly accurate.
3. HCL AppScan 360
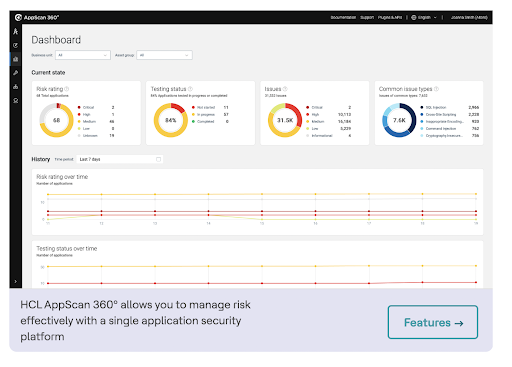
AppScan 360 by HCL is a leading cloud security tool designed for security tests on web applications and services. It offers various features such as auto-fix capabilities, machine learning for reduced false positives, and automatic scanning configurations.
Key features:
- Static analysis (SAST) – Analyzes source code in applications and APIs in real-time for the entire development lifecycle.
- Integration with CI/CD and IDEs – For SAST automation.
- DTS integration – For customized automation.
Pros
- Built on modern unified architecture it can be deployed as self-service on-premise, private and public cloud, and as a service.
- A centralized dashboard customizes the views of testing results, testing status, and remediation process.
- Actionable fixes for each vulnerability reduce the time for triage and remediation.
Cons
- Delays in scanning large applications.
- Shows false-positives.
4. Fortinet
Fortinet Cloud Security platform empowers organizations to secure any application on the cloud for all users. By using the Cybersecurity Mesh Architecture (CSMA), the cloud security system reduces operational complexity to facilitate interoperability and analytics.
Key features:
- Hybrid security – Protects and connects applications across all points of deployment across multiple clouds and both physical and virtual data centers.
- Advanced application layer security controls – Secures and protects web applications and API against threats including bots and OWASP Top 10.
- Cloud-native protection – Protects workloads and cloud-first application lifecycles.
Pros
- Comprehensive protection for all application journeys deployed on any cloud or virtual data center using consistent policies, centralized management, and security automation.
- Complete visibility and control for all cloud environments and applications.
Cons
- Initial configuration can be complex, particularly for those without prior experience.
- False positives.
- Technical support and GUI need improvements.
5. Prisma Cloud by Palo Alto Networks
Prisma Cloud is a leading cloud security platform that helps reduce the complexity of securing multi-cloud environments by eliminating cloud blind spots and detecting threats that other tools often miss. It also offers AIML capabilities to detect emerging vulnerabilities.
Key features:
- Visibility, compliance, and governance – Cloud asset inventory, configuration assessment, compliance management, and automated remediation.
- Threat detection – Network threat detection, user entity behavior analytics, and integrated threat detection dashboards.
- Data security – Multi-cloud data visibility and classification, data governance, malware detection, and alerting teams for investigation and remediation.
Pros
- Continuously monitor all cloud resources for vulnerabilities, misconfigurations, and threats.
- ML-powered and threat-intelligence-based detection pinpoints the highest risk security issues.
- Proactively monitor cloud storage for security threats and mitigate malware attacks.
Cons
- Lack of proper documentation and support.
- Expensive along with the high cost of support.
6. Singularity Complete by SentinelOne
Singularity Complete by SentinelOne is one of the best cloud security tools that allows modern enterprises to gain visibility into known and unknown threats without human intervention. Organizations can remediate endpoints with its powerful static and behavioral AI.
Key features:
- In-depth visibility – Patented Storyline technology tracks OS relationships giving a bird’s eye view to the user.
- Automated correlated telemetry – Reduces alert fatigue and manual triage for IT analysts.
- Patented one-click remediation – Reverses unauthorized changes, eliminating time-consuming scripting work.
Pros
- Patented technology gives complete visibility of an attack.
- Eliminates tedious scripting work.
- Native network attack surface protection.
Cons
- The initial setup and deployment can be complex and time-consuming.
- Limited integration options with certain third-party tools.
7. Forcepoint ONE
One of the best all-in-one cloud management tools, Forcepoint ONE allows organizations to quickly adopt Zero Trust and Security Service Edge (SSE component of SASE). The platform unifies Secure Web Gateway (SWG), CASB, and Zero Trust Network Access (ZTNA).
Key features:
- Identity-based access control – Offers identity-based control for SWG, CASB, and ZTNA.
- Agentless DSP security – Facilitates keeping sensitive data secure across cloud and private apps.
- Dynamic scalability – Delivers low-latency connectivity, and 99.99% uptime regardless of the user’s location.
Pros
- Supports offices and remote sites for secure access to SaaS and private apps.
- Identity-based access control enables the adoption of Zero Trust Principles.
- Tracks the overall security posture and measures the value of your security program for web, cloud, and private app channels.
Cons
- The deployment process can be lengthy and complex.
8. Cisco Cloudlock
Cisco Cloudlock, as a cloud security tool, monitors user activity, detects and prevents threats, and upholds security standards across cloud environments. The cloud-native CASB platform protects your cloud users, data, and apps while meeting compliance regulations.
Key features:
- Advanced machine learning algorithms – Detects anomalies and spot actions.
- Data loss prevention technology – Continuously monitors cloud environments and provides custom policies for data security.
- App firewalls – Helps discover and control cloud apps connected to your corporate environment.
Pros
- Provides data loss prevention (DLP), access restrictions, and anomaly detection.
- Protects users whether they’re on or off the network to secure hybrid and multi-cloud environments against complicated security threats.
Cons
- It is not an all-in-one cloud security solution and users would need to implement other Cisco products.
9. Orca Security
Orca Security brings core cloud security capabilities to identify, prioritize, and remediate security risks and compliance issues on a single purpose-built solution. You can leverage vulnerability posture management, workload protection, and container security across various providers.
Key features:
- Orca CSPM – Automated remediation, pre-deployment IaC scanning, reporting, and continuously monitoring, identifying, and remediating misconfigurations across the cloud.
- API Security – Get frictionless API security and visibility into the cloud within minutes.
- Vulnerability and patch management – Agentless vulnerability management across your entire cloud infrastructure.
- Container and Kubernetes security – Secure containers and Kubernetes applications and integrate security from pipeline to protection.
Pros
- Activate API security, Shift left security, and cloud detection for unified cloud security.
- Identify risks by tracing them back to the line of code that caused the issue, ensuring quick remediation, and making security and DevSecOps teams productive.
Cons
- Slower loading times and a clunky user interface.
- Room for improvement in scanning capabilities.
- Lack of integration for auto-remediation.
10. Datadog
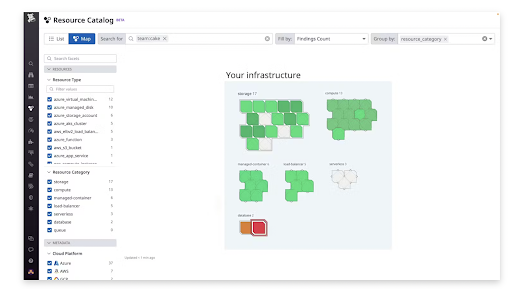
Datadog simplifies cloud-native security management for DevOps and security teams as one of the best cloud security tools. Users can view the number of misconfigured resources over a centralized dashboard without having to wait for the InfoSec team to notify them.
Key features:
- Scans cloud environments -Catalog and map out relationships between cloud resources.
- Observability Data – Automatically identifies the owner of the asset and environment variables.
- 600+ native integrations – Reduce the cost of ownership.
Pros
- Streamlines collaboration during investigations and implements incident response processes in existing workflows.
Cons
- Costly logs analytics workflow.
- At scale, Datadog can become expensive and complex to use.
- Gives false positives.
- No vulnerability management.
6 Types of cloud security tools
1. Cloud Access Security (CASB):
They are on-premise or cloud app security tools. If SaaS application usage and access is a priority, CASB is the ideal choice. They consolidate multiple types of security policy enforcement such as authentication, single sign-on, encryption, malware detection and protection, and device profiling among many other use cases.
2. Static Application Security Testing Tools (SAST):
SAST tools examine the source code to find possible security flaws. They test code in real time and prevent the loss of time and potential data security issues. Their biggest advantage is that they monitor and detect well-known vulnerabilities such as buffer overflows and SQL injection flaws.
3. Secure Access Service Edge (SASE):
Also known as secure service edge (SSE), it is an important part of cloud security network architecture. It combines VPN and SD-WAN capabilities with CASB, firewalls, zero-trust network access (ZTNA), and secure web gateways (SWG). They secure access to corporate applications, SaaS, and the web regardless of location or device.
4. Cloud Security Posture Management (CSPM):
Cloud security tools automate the identification and remediation of risks across cloud security management for IaaS, PaaS, and SaaS. It is used for risk visualization and assessment, misconfiguration management, and remediation, DevSecOps integrations, incident response, and compliance monitoring.
5. Cloud Workflow Protection Platforms (CWPP):
They provide a low-friction cloud security solution. They are used in the DevOps process with rapid development cycles. These tools can discover workloads running in multiple cloud environments.
6. Continuous Security Monitoring Tools (CSM):
They offer visibility, real-time threat detection, and continuous configuration. They collect and analyze data for suspicious activities from multiple sources including network traffic, system event logs, and user activity. As soon as a threat is identified, it alerts your IT/DevSec team.
Conclusion
Securing your data is crucial. We’ve handpicked 10 of the best cloud security tools for you in this article.
The 10 cloud security tools mentioned are:
- Astra Security
- Commvault
- HCL AppScan 360
- Fortinet
- Prisma Cloud by Palo Alto Networks
- Singularity Complete by SentinelOne
- Forcepoint ONE
- Cisco Cloudlock
- Orca Security
- Datadog
When choosing cloud security tools, you should look for the following features:
- Vulnerability management
- Unified visibility across public, hybrid, and private cloud environments
- Cloud workload protection
- Threat intelligence with real-time threat detection and remediation
- Zero false positives
Still confused? Don’t worry! We’re here to help you secure your data. Contact our Cybersecurity experts to understand how cloud security tools like Astra protect your data.
Book a call now!
Frequently Asked Questions
What are cloud security tools?
They refer to software applications that protect cloud-based systems, data, and infrastructure, often designed to address the unique security challenges posed by the cloud, such as data breaches, data loss, and account hijacking. They offer a range of features such as vulnerability scanning, asset mapping, threat detection and protection, and web application security.
Will there be any issues while integrating cloud security tools with existing security infrastructure?
Some common risks arising during the integration of cloud security tools with existing security infrastructure are:
1. High maintenance cost
2. Compliance risks
3. Security vulnerabilities
What mechanism do cloud security tools use to protect sensitive data in cloud environments?
The best cloud security tools employ encryption and access restrictions along with data loss prevention protocols to prevent illegal access and data leakage.
Which are the best cloud security tools for your organization?
Some of the widely used cloud security tools are:
1. Astra Security
2. Orca Security
3. Datadog
4. Singularity Complete by Sentinel One
5. Commvault
















