“Is penetration testing the same as vulnerability assessment? What purpose does both of them serve? How can I conduct a vulnerability assessment for my company?”
If this sounds like you, don’t panic. We understand that the vulnerability assessment (VA) could be a very explicative process and in order to do it in the right way for your applications and networks, it could cost you a lot of time to find the right resources and documentation. This is why we have crafted this vulnerability assessment checklist for you.
But first let’s talk a little about the difference between a vulnerability assessment and penetration testing.
Vulnerability Assessment vs Penetration Testing
Although both vulnerability assessment and penetration testing serve a similar purpose – which is to help organizations identify and fix vulnerabilities present in their systems, many IT professionals often get confused between these terms and conversely implement them for their IT security needs.
The main difference between vulnerability assessment (VA) and penetration testing (PT) is that the VA is an automated process where tools like web and network security scanners are used and in PT a combination of automated tools and manual process of exploiting vulnerabilities is performed.
As we have already discussed the term Penetration Testing many times in our blog, now, we plan to provide you more insights on the Vulnerability Assessment part with a detailed 10-point vulnerability assessment checklist that can help you conduct VA for your application and network security needs.
10-Point Vulnerability Assessment Checklist
1. Understand business outcomes of Vulnerability Assessment (VA)
A lot of security professionals make vulnerability assessments mandatory in their risk assessment strategy, but what most of them lack is the knowledge of business implications of it. So, before evaluating any vulnerability assessment services, it is important to understand or set a business objective for the same.
Here are some desired outcomes both business and security professionals should expect from a vulnerability assessment:
- To know how to minimize the response time if any business-critical situation arises.
- To prevent any risk of a data breach via your IT environment.
- To decide the priority for fixing identified vulnerabilities and risks within your IT assets.
- To understand the ROI on vulnerability assessment for your invested funds on IT security infrastructure.
- To help you understand the compliance of industry standards such as GDPR, ISO, PCI, etc.
- To prevent downtime of your IT and mitigate risks of being non-compliant to signed SLA with your customer.
- To minimize future risk of vulnerability exploits.
2. Prepare IT & data asset inventory
After understanding the business implications of VA, it is now time to start gathering information about your IT and data assets and prepare an inventory of them to plan and conduct the vulnerability assessment.
You may want to consider the following IT and data assets for conducting vulnerability assessment:
- Networking devices such as routers, firewalls, switches, etc.
- Web, mobile and SaaS applications
- Servers
- Public and private cloud environments such as AWS, Azure, GCP, etc.
- APIs
- Databases
Once you have a complete inventory, you can begin looking for any potential vulnerabilities. It is important to have certain documentation ready which can help you understand the potential vulnerability areas in the systems (documentation such as network diagrams, URLs, configurations, user credentials, access keys, etc).
3. Identify risk types that could harm your systems
After you make an inventory of your systems, you need to identify the types of potential security risks or vulnerabilities that could be used against your systems and further enable hackers to compromise your network or perform a data breach.
Here are some common security risks, attack types and vulnerabilities that could harm your systems:
- Malware attacks
- Denial of Service (DoS) attacks
- Phishing
- Brute-force attacks
- Man-in-the-middle attacks
- OWASP Top 10 and SANS25 risks (SQLi, XSS, Broken Access Control, CSRF, etc.)
- Security misconfiguration errors
- Zero-day attacks
There are many different kinds of attacks and vulnerabilities, so it is important to familiarize yourself with the most common ones. This will help you better understand how to protect your systems against them.
4. Decide testing types for each system
The next step is to understand the different types of vulnerability assessment. Vulnerability assessment can be divided into two main categories: active and passive.
Active assessments are typically more intrusive and can involve exploitations, while passive assessments are less invasive and usually only involve analyzing data that is already present. Each type of assessment has its own advantages and disadvantages, so it is important to understand the difference before deciding which one is right for your system.
5. Prioritize VA according to degree of risk
By understanding the different types of threats and their potential impact, you need to prioritize which areas of your business are most at risk. One way to do this is by looking at the impact each type of threat could have on your business operations or systems. For example, if a hacker was able to gain access to your customer database (high-risk system), the impact could be much greater than if they were only able to access your website (medium-risk system). By understanding the potential impact of each type of threat, you can prioritize which areas of your business need to be assessed first.
Another way to prioritize vulnerability assessment is by looking at the likelihood of each type of threat happening. For example, if you are a small business with a limited online presence, the likelihood of being attacked by a sophisticated hacker is much lower than if you are a large corporation with an extensive online presence. By understanding the likelihood of each type of threat, you can again prioritize which areas of your business need to be assessed first.
Key takeaways:
- Perform continuous vulnerability assessment scanning daily for your ‘high-risk’ systems.
- Consider doing vulnerability assessments on a monthly or quarterly basis for your ‘medium or low-risk’ systems.
6. Check for regulatory compliance
Vulnerability assessments help companies identify weaknesses in their systems and processes. If these vulnerabilities are exploited before being identified and fixed by the company, it could lead to serious damage such as disruption of financial transactions, theft of healthcare information, sensitive data breach of customers, service unavailability etc.
Hence, it is always important to comply with certain security laws and regulations. And in order to achieve this, a vulnerability assessment can be conducted by considering the requirements for compliance.
Here are some important compliances that can be achieved with vulnerability assessment and penetration testing:
- PCI-DSS for the companies that store or process payment-related data or transactions.
- HIPAA for the companies who store healthcare information.
- GDPR for data privacy and protection.
- SOC2 for services companies.
- ISO 27001 for companies in information security.
7. Involve your dev/security team in the VA process
The goal of a vulnerability assessment is to identify, quantify, and prioritize risks to organizational operations (including assets, systems, and information) posed by vulnerabilities. Vulnerability assessments can be conducted as internal or external audits. Internal audits are performed by security personnel within the organization; external audits are performed by third-party VAPT service or solution providers.
It is very crucial to involve both security professionals and development teams in the entire internal or external audit process. This is because most IT professionals aren’t capable enough to clearly read the vulnerability scan results. And of course, the development team needs to be kept in the loop in order to fix the vulnerabilities assigned to them by security professionals.
8. Manage and prioritize fixing of vulnerabilities
After a vulnerability assessment is complete, it’s time to start fixing the issues that were found. And the process of managing and assigning issues to your dev team may become cumbersome for you. But before you can do that, you need to prioritize the vulnerabilities.
Here are some factors to consider when deciding which vulnerabilities to fix first:
- Severity of the vulnerability
- CVSS Score
- Likelihood of exploitation
- Potential loss in revenue (if exploited)
- Difficulty of remediation
- Business impact
To avoid this doing manually, you should consider a comprehensive vulnerability management solution that can do this job for you. A risk-based vulnerability management offers risk-grading, severity, CVSS score, impact rating which helps you prioritize vulnerabilities for fixing in a very easy way.
9. Prepare detailed reports
When a vulnerability assessment is complete for your system, It is now time to create a report that can provide you with a bird-eye view of the security of your systems that were part of the VA process.
For example, a detailed vulnerability report for website vulnerability assessment includes:
- A list of all identified vulnerabilities, including a description, affected URLs, etc.
- The risk level for each vulnerability, including severity, impact, and potential revenue loss
- Steps to reproduce each discovered vulnerability with videos or textual documentation
- Recommendations for mitigating or remedying each vulnerability
A vulnerability assessment report can help an organization identify, quantify, and prioritize risks to its operations. By identifying vulnerabilities, an organization can take steps to mitigate or remediate them, thereby reducing the likelihood of a successful attack.
10. Maintain your learning for future reference
A well-written vulnerability report can also provide valuable information to incident response teams in the event of a breach. Incident response teams can use the information in a vulnerability assessment report to more quickly understand the scope of an attack and take steps to contain it. Hence, it is important to document and maintain all your learning from the previously performed vulnerability assessments and keep them for future reference.
How Astra Pentest helps you with Vulnerability Assessment
Astra Pentest is a comprehensive vulnerability assessment and penetration testing suite that is designed to thoroughly scan networks and applications for security weaknesses, vulnerabilities and misconfiguration errors. In addition to the assessments, Astra Pentest also provides dedicated vulnerability management and pentest compliance dashboards – just to go that extra mile to make sure your systems are in good hands.
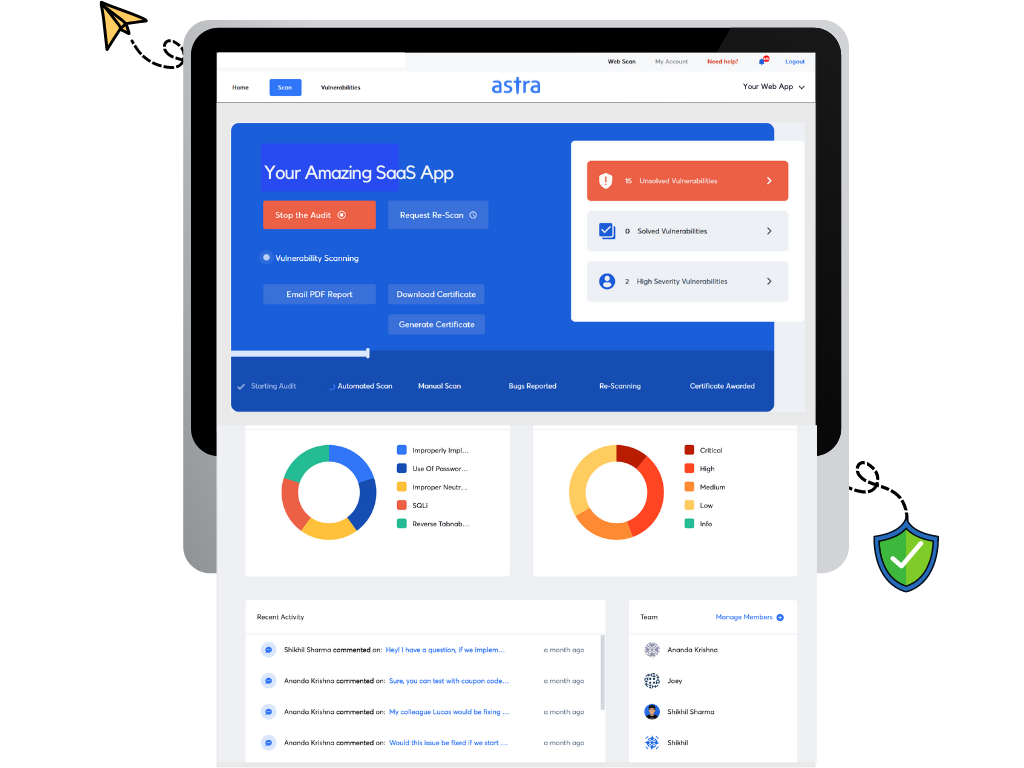
Astra Pentest has the following key features that make it a complete one-stop solution:
- 8000+ security tests.
- Automated vulnerability scanner with an option to scan behind login pages.
- A mix of automated and manual penetration testing.
- Vulnerability management platform to fix issues with set priority.
- CI/CD and other app integrations like GitHub, Gitlab, Jira, Jenkins, Slack, etc.
- Easy collaboration option to connect dev teams with security teams.
- In-depth reporting with detailed vulnerability analysis
- A dedicated pentest compliance dashboard with tests for GDPR, SOC2, ISO27001, HIPAA, and PCI-DSS.
- A PWA app to access your dashboard quickly and easily.
Final Thoughts…
Conducting a vulnerability assessment can be a complex and time-consuming process, but it is essential for ensuring the security of organizational assets, systems, and information. By taking the time to identify and assess risks, companies can make informed decisions about how best to protect their assets and ensure their continued operations. We hope that by following this vulnerability assessment checklist, you can be sure that you are doing everything possible to protect your systems against any attack.
















