A SOC 2 Penetration Testing (Pentest) is often highly recommended by the auditors to demonstrate the effectiveness of the controls implemented during the SOC 2 audit.
Developed by the American Institute of CPAs (AICPA), SOC 2 establishes a comprehensive framework based on 5 key pillars for managing data and strengthening relationships with all stakeholders. However, strong security policies alone aren’t enough to achieve or maintain compliance, often challenging those policies just like a hacker would be required.
That’s where SOC2 pentesting comes into play. But before we delve deeper into why a pentest plays a vital role in SOC 2, let’s learn a bit more about its compliance requirements.
What are SOC 2 Compliance Requirements?
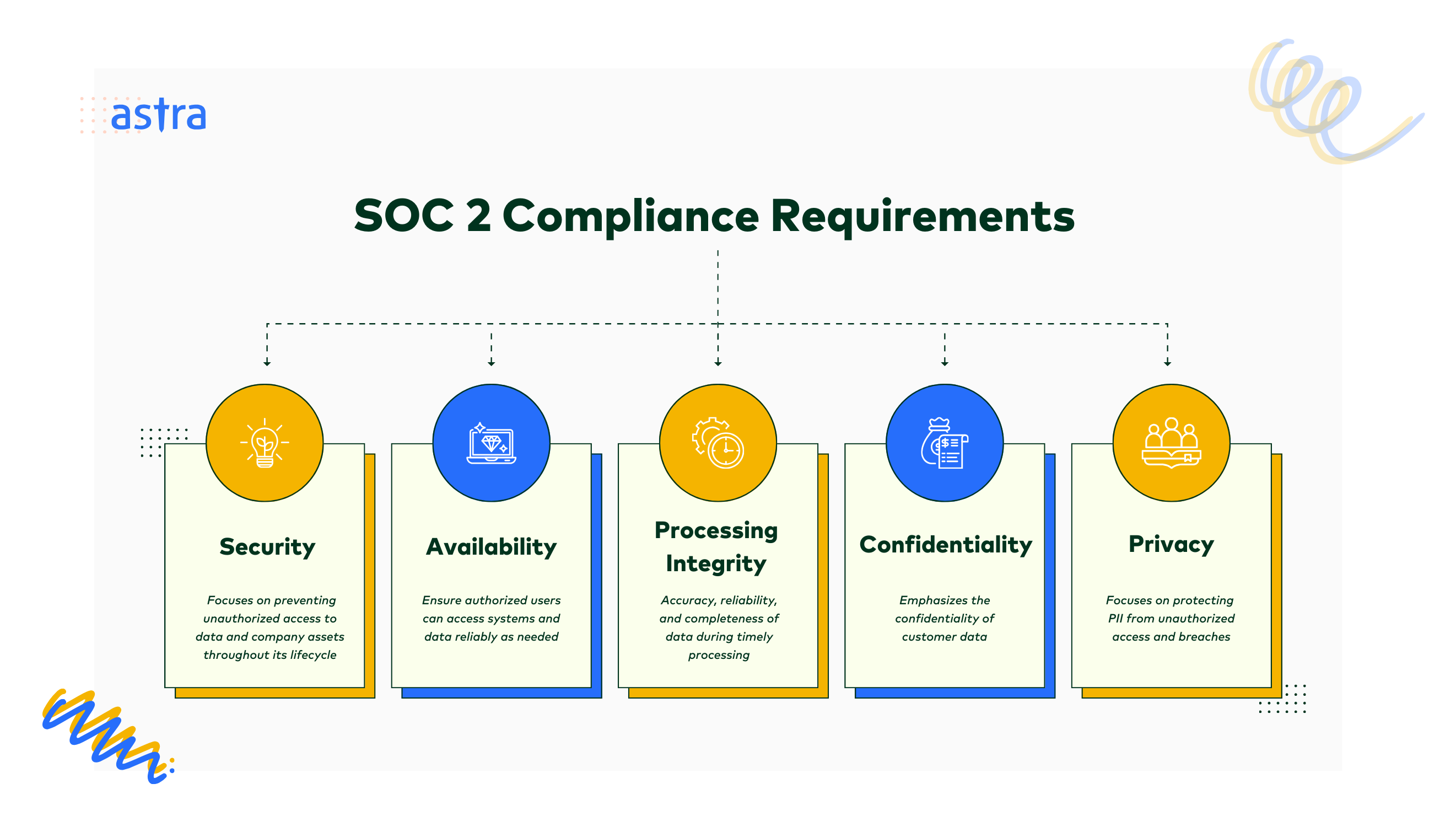
In line with AICPA policies, the SOC 2 framework outlines comprehensive criteria for how organizations should handle customer data based on five Trust Service Criteria (TSC):
1. Security:
This is the most crucial principle of SOC 2. It focuses on preventing unauthorized access to data and company assets throughout their lifecycle. It mandates controls to safeguard against malicious attacks, data deletion, misuse, or unauthorized disclosure, among other things.
Some key controls include access controls, intrusion detection systems (IDS), anti-virus, and firewalls.
2. Availability:
This criterion aims to ensure authorized users can access systems and data reliably as needed. As such, SOC 2 compliance requires organizations to maintain uptime and minimize downtime through redundancy and disaster recovery plans.
Some common focus areas include network performance monitoring, security incident response procedures, backup and data recovery as well as disaster recovery procedures.
3. Processing Integrity:
This principle emphasizes the accuracy, reliability, and completeness of data during timely processing. Controls such as quality assurance procedures and monitoring tools to prevent unauthorized data modification, errors, or omissions fall under this category.
4. Confidentiality:
As the name suggests, it emphasizes the confidentiality of customer data. To comply, organizations must limit data collection to what’s necessary, obtain user consent, and practice proper access restrictions, user activity monitoring, and appropriate disposal procedures.
Pro Tip: Data classification and NDAs also help ensure contractual obligations are met and compliance with external factors.
5. Privacy:
Unlike Confidentiality, which applies to a broader range of sensitive information, Privacy focuses on protecting Personally Identifiable Information (PII) from unauthorized access and breaches. SOC 2 mandates clear communication of data privacy practices to anyone whose information is stored.
Some key controls include clear privacy policies, rigorous access controls, encryption, and 2FA.
What is SOC 2 Penetration Testing?
SOC 2 penetration testing is a simulated cyberattack conducted within the framework of SOC 2 compliance. It is designed to identify vulnerabilities in your IT systems and assess their potential impact on securing customer data.
It leverages the Trust Service Criteria (TSC) to guide the testing process. This targeted approach exposes vulnerabilities and provides actionable remediation measures to strengthen your overall cybersecurity posture and demonstrate your commitment to data protection.
It can be further divided into Type and Type 2, as explained below.
| Feature | SOC 2 Type 1 | SOC 2 Type 2 |
|---|---|---|
| Focus | Design of controls | Operating effectiveness of controls |
| Report Type | Description of documented policies and procedures | Description of controls AND testing results over a period |
| Timeframe | Specific point in time (usually date of report) | Typically 3-12 months |
| Assessment | Evaluates the suitability of the design of controls to meet the TSC | Evaluates the suitability of the design of controls AND their operating effectiveness over time |
| Testing Procedures | Not required (may include interviews) | Testing of controls to validate their effectiveness |
| Level of Assurance | Lower | Higher |
Is Penetration Testing a SOC 2 Compliance Requirement?
While SOC 2 itself doesn’t explicitly require pen testing, it indirectly encourages it through its Trust Service Criteria (TSC). Auditors often recommend penetration testing as a way to effectively address specific TSC controls and principles, as explained below:
1. Validating Security Controls (Security Principle):
“CC4.1: The entity selects, develops, and performs ongoing and/or separate evaluations to ascertain whether the components of internal control are present and functioning.”
Simply put, a SOC 2 pentest goes beyond static reviews of policies and procedures to actively attempt to exploit vulnerabilities. This provides a more realistic overview of how well your security controls (firewalls, access controls, etc.) would fare in the real world while addressing the Security principle.
2. Identifying Unknown Weaknesses (Availability Principle):
“A1.2: The entity authorizes, designs, develops, or acquires, implements, operates, approves, maintains, and monitors environmental protections, software, data backup processes, and recovery infrastructure to meet its objectives.”
Penetration testers employ various techniques to uncover and address weaknesses that traditional vulnerability scans might miss. Such vulnerabilities could disrupt system availability if exploited by a real attacker. Addressing these weaknesses strengthens your compliance with the Availability principle of SOC 2.
3. Assessing Data Breach Risk (Confidentiality Principle):
“C1.1: The entity identifies and maintains confidential information to meet the entity’s objectives related to confidentiality.”
A pentest for SOC 2 compliance can simulate how an attacker might gain access to sensitive data. This allows your company and auditors to assess the risk and impact of a successful attack with respect to sensitive customer data covered under the Confidentiality principle.
Why Astra is the best in pentesting?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- Vetted scans ensure zero false positives
- Our intelligent vulnerability scanner emulates hacker behavior & evolves with every pentest
- Astra’s scanner helps you shift left by integrating with your CI/CD
- Our platform helps you uncover, manage & fix vulnerabilities in one place
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Does SOC 2 Compliance Mandate Vulnerability Scanning?
The criteria CC7.1 of SOC 2 listed below suggests (if not mandates) regular vulnerability scanning.
CC7.1: “To meet its objectives, the entity uses detection and monitoring procedures to identify (1) changes to configurations that result in the introduction of new vulnerabilities, and (2) susceptibilities to newly discovered vulnerabilities”
In addition to complimenting pentesting, vulnerability scanners help achieve a more comprehensive assessment of the above.
1. Continuous Monitoring:
Unlike SOC 2 pentesting, which is typically conducted periodically, vulnerability scanning can be automated for continuous monitoring. This ongoing assessment helps ensure your security posture remains strong and vulnerabilities are addressed promptly.
2. Early Detection:
Vulnerability scans proactively identify weaknesses in systems and applications, allowing your organization to minimize the risk of security incidents that could impact SOC 2 criteria like Security, Availability, or Confidentiality.
3. Control Effectiveness:
Vulnerability scanning helps assess the effectiveness of existing security controls, which can be particularly helpful in demonstrating compliance with the Security and Processing Integrity criteria. Auditors often look for evidence of ongoing vulnerability management processes.
What Are The Various Types of Pentests for SOC 2 Compliance?
Black Box Pentest
A Black Box Pentest, in the context of SOC 2 requirements, simulates an external attacker with absolutely no prior knowledge of your system, network, or applications. This testing methodology aims to identify vulnerabilities and assess the effectiveness of your security controls.
While the external approach has multiple benefits, the lack of assessment of internal controls, such as IAMs, can hamper efficiency.
White Box Pentest
A White Box approach to SOC 2 penetration testing provides analysts with complete knowledge of your system’s architecture, configuration details, and potentially even source code. This in-depth access allows for a highly targeted and efficient evaluation of your security posture.
While advantageous, it is crucial to remember, in this case, that the effectiveness of the SOC 2 pentest hinges on the accuracy and completeness of the information provided about the system.
Grey Box Pentest
A Grey Box Pentest provides testers with limited knowledge about your system and environment. This middle ground offers a more efficient and targeted approach than a purely external or internal perspective, making it ideal for SOC 2 compliance.
Simply put, by skipping the time-consuming discovery phase of a black box pentest and yet providing a more targeted control assessment than a white box, a grey box allows for efficient evaluation of security posture against SOC 2 criteria.
How Can Astra Security Help?
“Astra Pentest gave us the ability to provide the evidence necessary to satisfy the pentest and vulnerability scanning requirements for our SOC2 certification, which gives our clients confidence that they can trust Validatar with their data as Validatar helps them gain trust in their data.”
Darrell Zook,
Director of Development & Technology, Validatar
Astra’s unique PTaaS platform combines automated and manual SOC 2 penetration testing to help you stay compliant throughout the year. Our state-of-the-art vulnerability scanner mimics real-world hacker tactics to run 9,300+ security tests on your applications.
Meanwhile, with zero false positives and unique AI test cases, our engineers conduct in-depth pentests to deliver exhaustive SOC 2 reports with remediation steps customized to provide actionable insights at every level, from engineers to executives.
Once vulnerabilities are patched, we conduct a comprehensive rescan to verify effectiveness and provide a clean report for your auditors. Lastly, our seamless tech stack integrations, easy scheduling, regression test capabilities, and real-time expert support help make all pentests simple, effective, and hassle-free.
Final Thoughts
In today’s data-driven world, earning and maintaining SOC 2 compliance is necessary. While not mandatory, VAPT plays a crucial role in achieving continuous compliance with the five SOC 2 Trust Service Criteria.
By pinpointing vulnerabilities and validating the effectiveness of your security controls, SOC 2 pentests help ensure proactive security, demonstrate your commitment to data protection, and build trust with customers.
Lastly, while any manual pentest can meet SOC 2 requirements, continuous pentesting and scams with a platform like Astra help address vulnerabilities throughout the SDLC, thus saving time, energy, and worry that comes with the traditional pentest and remediation cycle.
FAQs
1. What is the timeline for SOC 2 penetration testing?
A SOC 2 penetration test typically costs between $2,000 and $25,000 depending on the size and complexity of your organization’s systems and controls, as well as the depth of analysis.
2. How much does penetration testing cost?
The cost of penetration testing for web apps ranges between $99 and $399 per month. The cost for cloud pentests and mobile pentests may vary based on the scope of the test.
3. Is SOC 2 compliance mandatory?
No, SOC 2 compliance isn’t legally mandated. But it’s a gold standard for security, showing customers you take data protection seriously. This builds trust and can be a deal-breaker for businesses seeking reliable vendors.
4. What is the difference between a SOC 2 pentest and penetration testing?
SOC 2 pentests are a specific type of penetration test designed to assess security controls relevant to the SOC 2 audit. Regular penetration testing might target broader areas, while SOC 2 pentests focus on areas like data security and access controls.
















