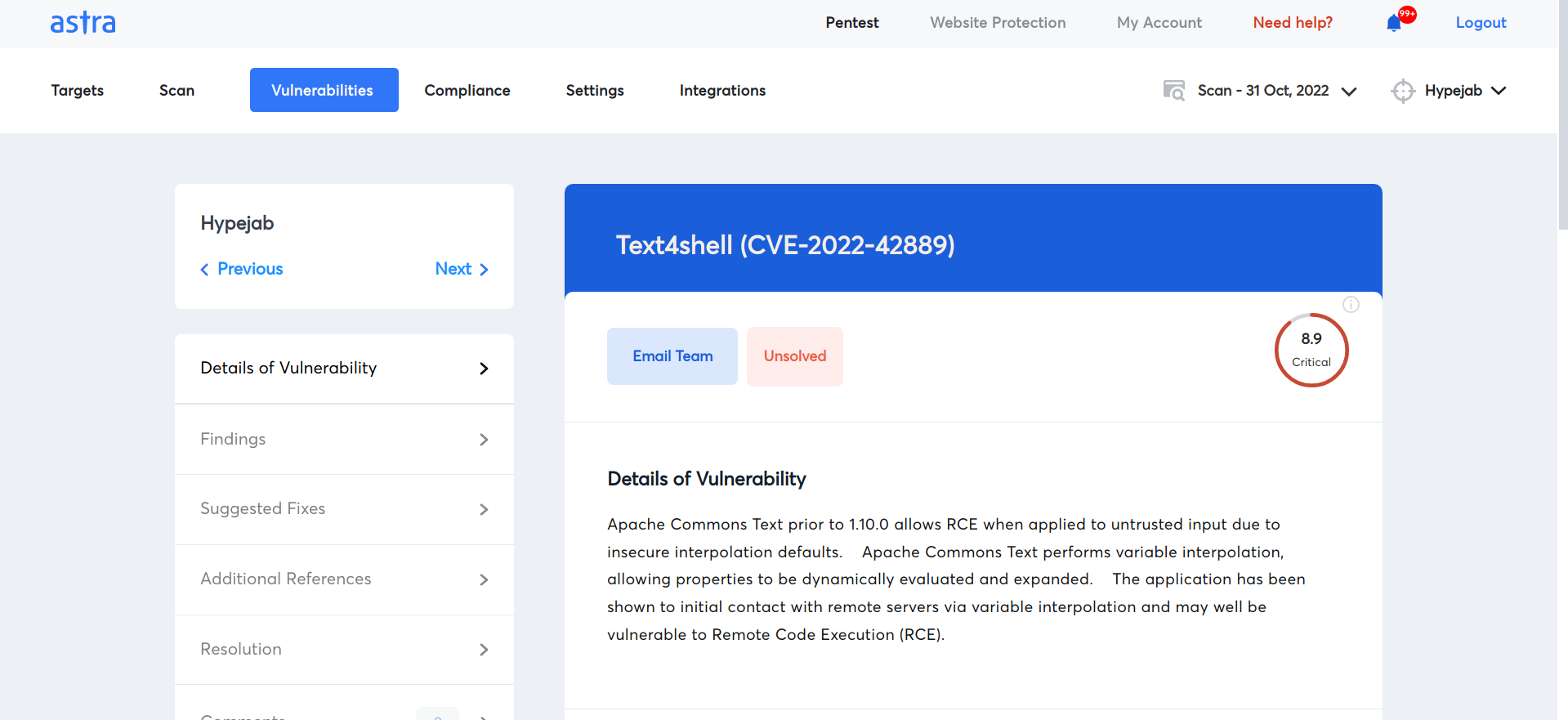
CVE-2022-42889 or the Text4Shell is a security vulnerability found in the Apache Commons Text library. It can lead to “unsafe script evaluation and arbitrary code execution” through the manipulation of a string interpolation functionality.
The name Text4Shell instantly invokes the memories of the Log4Shell vulnerability and creates anxiety, so, let us just get that out of the way. CVE-2022-42889 is not nearly as widespread or worrisome as Log4Shell (CVE-2021-44228), even though it can be impactful in certain situations. Moving forward in this post, we’ll discuss what the Text4Shell is, what are its effects, who gets affected, and how you can mitigate it.
When was it discovered?
The Text4Shell or Act4Shell vulnerability was first discovered by Alvaro Muñoz, a researcher at GitHub Security Labs in March 2022. The Apache Dev List announced the vulnerability on Oct 13, 2022.
What is the current status?
CVE-2022-42889 exists in the StringSubstitutor Interpolator object in versions 1.5 through 1.9 of the Apache Commons Text library and it has a CVSS score of 9.8 out of 10.0.
A patch was released by Apache Commons Text in version 1.10.
The Text4Shell can be exploited through JEXL engines on JDK versions 1.8.0_341, 9.0.4, 10.0.2, 11.0.16.1, 12.0.2, 13.0.2, 14.0.2. The exploitation failed on versions 15.0.2, 16.0.2, 17.0.4.1, 18.0.2.1, 19
Steps you can take
If you have dependencies on the Apache Commons Text library, you should ensure that you update to version 1.10 in order to avoid the Text4Shell vulnerability.
Astra’s automated scanner detects the Text4Shel vulnerability and offers step-by-step guidelines to fix it
It gives you
- The accurate risk score and the potential cost of exploitation
- The ROI on remediation
- Detailed guidelines and video PoC to help your developers reproduce the issue
You can manage and monitor the entire process from your pentest dashboard.
How does the Text4Shell vulnerability work?
The Commons Text library contains string-related utilities and packages – calculating string differences or similarities, translation, etc. The library is used in how Java handles strings.
One of the objects included in the library is a StringSubstitutor Interpolator. It lets you evaluate and retrieve input strings – it is a String Lookup functionality.
“The standard format for interpolation is ‘${prefix:name},’ where ‘prefix’ is used to locate an instance of org.apache.commons.text.lookup.StringLookup that performs the interpolation.” source
There are certain default Lookup instances like “script”, “DNS”, and “URLs” that include interpolators that can execute untrusted code.
Simply put, an attacker can get malicious input through the interpolators and perform remote code execution.
What is the potential impact of Text4Shell?
An attacker can use this vulnerability to get untrusted input logged or processed inside your business logic network. An attacker who executes a command using a DNS lookup followed by your web address as a string can potentially get access to your entire internal network.
The impact of the vulnerability, in this case, is limited by the use of the interpolators.
A real-life instance of Text4Shell exploitation has not been reported yet.
The comparison with Log4Shell
Even though both Log4Shell and Text4Shell are library-oriented CVEs their comparison is a little far-fetched.
Firstly, the log4j library is used at a much wider scale than the Commons Text library.
Secondly, the vulnerable method of interpolation is rarely used in open-source programs and hardly any of them parse user-controlled inputs.
Bottomline
In theory, the Text4Shell vulnerability has the ability to wreak havoc on your network and it is better to have it fixed as soon as you can. Overall it is not as potent a threat as the log4shell simply because of the limited usage of the affected library.
If you have any question regarding this or if you’d like to discuss your security in general, Talk to an expert.
















