A recent critical zero-day exploit in the popular Java logging system Log4J which was developed by Apache Foundation has set the internet on fire. In this blog, we’re going to detail how this vulnerability was exploited, how you may be affected, and how you can protect yourself against its active exploits.
On 9th December 2021, security researchers at Alibaba Cloud reported this vulnerability to Apache. An attacker can exploit this vulnerability to achieve unauthenticated remote code execution, affecting the old versions of Log4J. The report also says that it impacts default configurations of multiple Apache frameworks, including Apache Struts2, Apache Solr, Apache Druid, Apache Flink, and others.
Still, before understanding this vulnerability, you need to know what exactly Log4J is and why should you be worried?

What is Log4J?
Logging is an essential element of any application, and there are several ways to do it. Log4J is an open-source tool that makes it simple to record messages and errors. It’s flexible, easy to use and manages the complexity of logging for you.
Logging is built-in to many programming languages, and there are many logging frameworks available for Java. Log4J is probably the most popular logging API for Java and is an excellent choice for a standalone logging framework.
Log4j is a logging library based on the Java Platform, Standard Edition (Java SE), and has been around since the early days. Ceki Gülcü created it, and The Apache Software Foundation currently maintains the library. Log4J is the most popular logging framework for Java and is an excellent choice for a standalone logging framework.
Why should you be worried about a vulnerability in Log4J ?
Java is the most popular language used for the development of software applications. As of today, Java is used for developing applications for mobile phones, tablets, and other smart devices. Furthermore, it is used for developing web applications in the JAVA language.
The most important fact is that Java has the most extensive ecosystem and an extensive community of users and developers. Most of these devices running Java use Log4J for logging.
The Log4J API allows remote code execution. This means that an attacker can abuse the Log4J API to execute code on the server and other devices connected to it. A remote attacker can do this without any authentication.
If you are using Log4J for logging in Java directly or indirectly, you should take immediate steps to fix it as soon as possible.
What exactly is this vulnerability? (CVE-2021-44228 Explained)
The vulnerability was found by Chen Zhaojun from Alibaba Alibaba Cloud Security Team and has been assigned CVE-2021-44228. It is a critical flaw dubbed as Log4Shell or LogJam and is second only to the infamous Heartbleed bug with a base CVSS score of 10.
This vulnerability impacts all the log4j-core versions >=2.0-beta9 and <=2.14.1.
According to Apache:
“Apache Log4j <=2.14.1 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled. From log4j 2.15.0, this behavior has been disabled by default.”
The affected version of Log4j allows attackers to lookup objects in local or virtual context over data and resources by a name via RMI and LDAP queries using this API AFAIK, so when a log entry is created, JNDI is encountered and invoked, which supports RMI and LDAP calls. It may make it possible to download remote classes and execute them.
How to Mitigate CVE-2021-44228?
1. Upgrade to the latest release, Log4j v2.15.0
2. If you are using version >=2.10
Set log4j2.formatMsgNoLookups or LOG4J_FORMAT_MSG_NO_LOOKUPS to TRUE
3. For version >=2.0-beta9 and <=2.10.0
Remove the JndiLookup class from the classpath:
zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
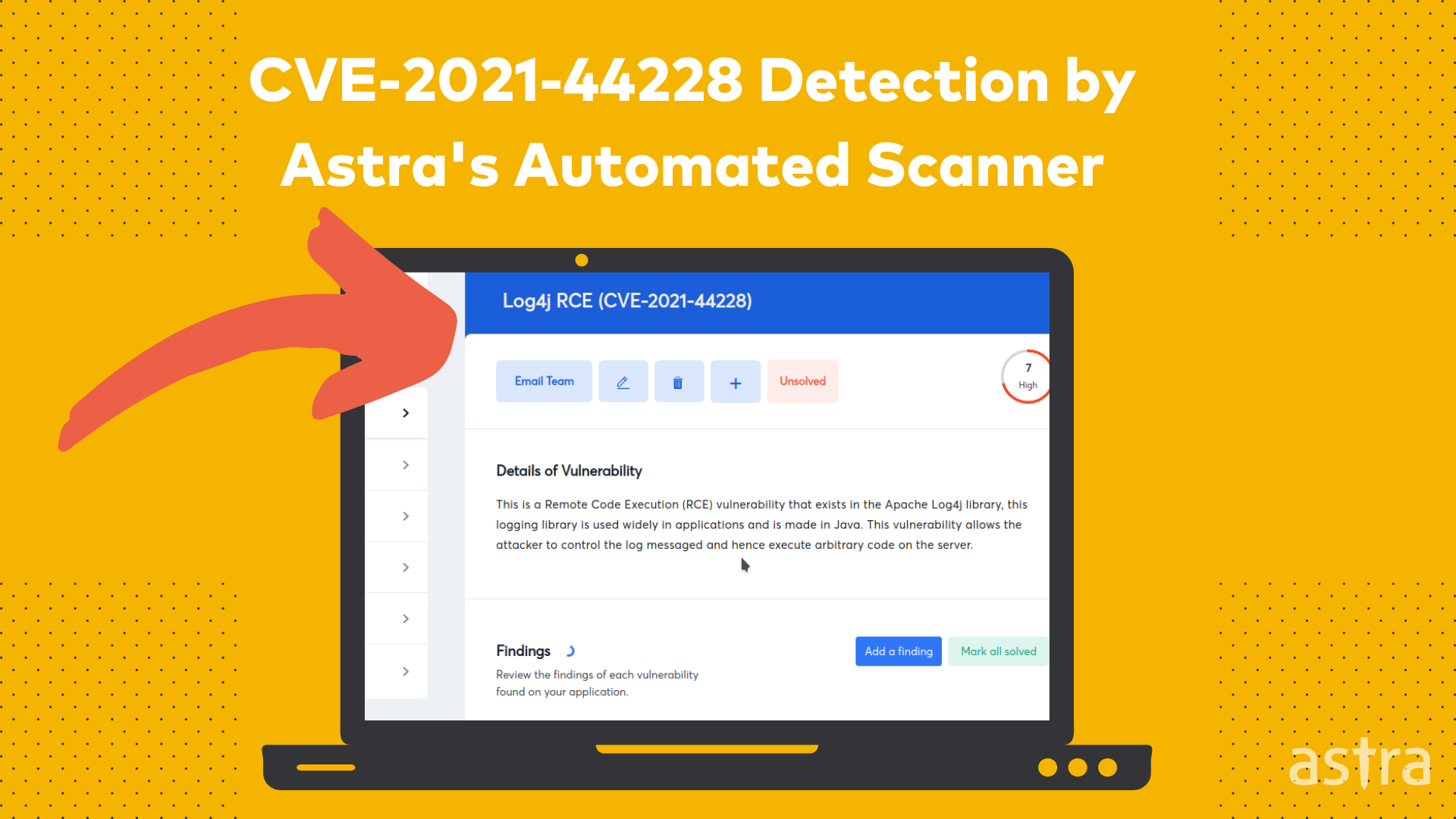
How can Astra protect you from CVE-2021-44228?
A top-notch automated vulnerability scanner by Astra identifies CVE-2021-44228 and helps your organization get rid of it with a recommended fix. With Astra Penest, you can find out all vulnerabilities that exist in your organization and get a comprehensive vulnerability management dashboard to see and fix your vulnerabilities on time.
Wrapping it up…
Whether it’s a new zero-day security vulnerability or a ransomware attack, you never know when your business will be affected by a new form of cyber attack. That’s why having a penetration testing solution by your side is essential. With Astra, you won’t have to worry about anything. Check out our website today to learn more and see how we can help you with your next project.
















