Is your Magento site sending repeated random and unrelated spam emails to users? It may be hacked! Spam emails are irritating like no other, it might piss off a user to a point that he/she may end up unsubscribing you or worse reporting your email. If you have noticed or have been receiving warnings about spam emails from your Magento account, it is time you checked it for a Magento hack. Magento hacked sending spam is a common query people have when they do come to know of hidden spam email campaigns taking place from their site.
In multiple instances, we have Magento owners telling us about unfamiliar activities and unknown users on their sites. On investigating further, we find thousands of spam emails from the same person or by bots. Like the one we saw with Magento hacked with .ru bots. These bots usually make thousands of accounts on your site and overwhelm the server.
Why spam emails are irritating? The obvious reasons are they are – intruding, unrelated, or offensive. However, there are more grave reasons for hating spams such as malware. According to a study, 94% of malware was delivered via email.
Visitors receiving spam emails from your email paint a negative image of your website in their minds. Spam emails can also cannibalize important emails from your site. All this can negatively impact traffic and thus can lead to loss of business.
Hence, we are here solving the problem of Magento hacked sending spam for you. We are positive that this guide will be of much help to you in understanding the problem and fixing it.
Symptoms of Magento Hacked Sending Spam
If you suspect that you have a case of Magento hacked sending spam, then you can confirm your suspicion through the following steps.
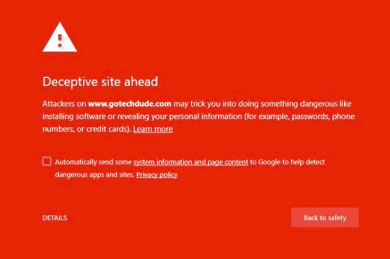
- The search engine posts a warning page when someone visits your website. This happens if a search engine detects any spam on your website. After which they blacklist your Magento website.
- The hosting company disables your website. There is a chance that they might have detected a hack in your website since they continuously scan their servers for such malicious codes
- Emails from your website land up in spam folders. Email providers nowadays have precise filters to block spam emails. If you find emails from your website being tagged as spams, then service providers might have blacklisted your IP and website
- Unauthorized accounts pop-up on your website. Attackers might have created fake accounts and hijacked your website.
Magento Spam Email Examples.
This is an example of a user-facing a Magento spam email on their website. In such cases, removing the hack can be a tedious task. The entire website needs to be thoroughly checked for any harmful codes or changes to the website files.
Take this case for example:
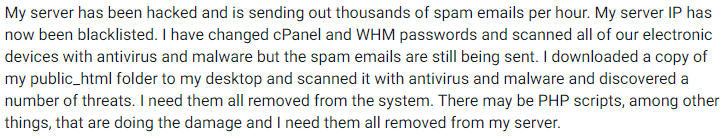
This is just one of the hundreds of cases regarding Magento hacked sending spam attacks. Further, being a popular e-commerce platform, Magento faces an even higher risk of a Magento spam hack.
Magento Hacked Sending Spam: Causes
This Magento hacked sending spam attack can have a number of reasons. The following have been proved over the years as some of the common ones:
- SQL Injection:
Attackers can inject malicious codes into your website and take control. This attack is called SQL Injection. In this attack, attackers will inject malicious SQL codes to manipulate and take control of your website. These codes can also be used to trigger the installation of malicious programs, which in turn will function to send spam emails.
- Weak Credentials:
Weak credentials are one of the main reasons of websites getting hacked. If login credentials are weak they can be breached by either using dictionary attacks or brute-forcing. Once in, hackers can host whatever spam campaigns they wish.
- Open Ports:
Programs on your website that are using open ports can be exploited by an attacker. Through open ports, an attacker sends across malicious packets of information. These packets can then infect any application that is listening to an unsecured open port.
- Script Uploads:
In a lot of cases, websites allow users to upload files. Attackers can use this opportunity to upload files that have hidden codes and infect the entire website using such files. An example of this attack is uploading PNG files with hidden PHP codes. Such images once uploaded, will execute the code which can cause a lot of damage to your website.
- Sharing Webspace:
Sharing web space can be a cheaper option for a website server. However, despite security protocols, there can be security issues. Any attacks on a shared server will affect all websites that are using it. Sometimes, websites sharing a server also share the same IP address. Anyone on the server can choose to infect the other websites due to access to common resources.
- Receiving Spam Emails:
Spam emails can lead to infections that result in more spam emails. When you receive a spam email, chances are that they may contain malware or hidden codes. Once you open them you run the risk of compromising your entire system. To protect your website from sending spam emails, you also need to make sure that you are careful in handling any spam emails that you might receive.
- Registration Spam:
There are bots that can create fake accounts and register on your website. These bots will create numerous accounts that can be used to enter your website and launch further attacks. Unless you remove these bots, fake registrations will keep happening. These accounts can also overload your website’s server and become a hindrance to the usual functioning of your website.
- Non-Delivery Reports Spam:
Email providers have a feature that lets you know if your email has encountered a problem after it is sent. In this attack, attackers send emails to non-existent email IDs by manipulating the “from” field. In the “from” field, they will mirror a legit sender, such as your website. Once the email is sent, the original target (your website in this case) will receive a receipt stating that the email has encountered a problem. This can get pretty bothersome if done on a huge scale and can easily overwhelm your email servers.
How to Stop Magento Spam Emails ?
If you have a case of Magento hacked sending spam on your website, it is important that we identify and remove the cause. Following are some of the steps that you can take to clean your website and stop spam emails:
- Fixing Inbound Spam:
The first step in fixing this issue is to stop getting spam emails to begin with. Have a strong filter to weed out spam emails as they might contain malicious content leading to security concerns. Make sure that legit emails are not landing in your spam folder and only spams are filtered out.
- Sender Policy Framework:
Sender Policy Framework (SPF) is a method to prevent others from sending emails on your behalf. This technique is used to stop spammers from forging your sender address and also prevent non-delivery report spam.
- Fixing Outbound Spam:
Once you have fixed some of the underlying issues, you need to find the codes or program responsible for sending out spam emails. Most of the time, spamming is done by certain pieces of code that have injected by attackers, or by programs like malware that have been installed without your permission. Once you find the cause, you can either install a fresh copy of your website or use a security scanner to clean your website.
- Identify and Remove Spam Scripts:
Code injection is a very popular method to take control of a website. Scripts can be uploaded by using file formats that hide such scripts or through code injections. If credentials are weak and attackers have access to files, then they can manipulate core files. Find and remove such scripts. Facing trouble finding such scripts? Get in touch with Astra security experts and we will get you through it.
Other Precautions
Apart from the above steps, make sure that there are regular security audits. This will ensure that you can catch any suspicious activities on your website. Check for appropriate file permissions for your admin files and folders. Update all your plugins and themes regularly and make sure that they do not have any known vulnerabilities. Always use the latest version of Magento. Also, ensure that you have 2FA for all your logins.
Having a top-notch security service provider like Astra will make it much easier to keep your website safe. With their state-of-the-art security tools and constant monitoring, you can rest assured that your website is in safe hands.
Conclusion
With ever-changing technology and hacking techniques, you can never be completely safe. With constant security audits and strong security protocols, you can keep your website safe. Spamming can affect your brand image which can, in turn, reduce traffic to your website. Your users will also be missing out on important emails from your website if there is a Magento spam emails.
Liked this post? Comment below and let us know 🙂