Article Summary
Scanning websites for malware could be considered the human equivalent of regular health check-ups. Your website is crucial for your business and so it should be healthy and safe. But how to keep your website safe from malware?
Scanning websites for malware could be considered the human equivalent of regular health check-ups. Your website is crucial for your business and so it should be healthy and safe. But how to scan website for malware ?
Let’s find out in this article.
But, before jumping straight to the process of scanning a website for malware, let us look into the varied reasons of malware injection.
Why Are Malware Injected In Websites?
When we hear the word malware we think of either of the two things – an enormous data breach like the Quora’s massive data breach of 2018 or a website defacement like these.
1) Defacement

Defacements and takeovers, like the European Union website, are easily noticeable and are quickly acted upon. Users will notice the change and report it. Google will flag it for strange behavior and your site will end up in Google’s blacklisted sites. Search warning like “This site may be hacked” or “This site may harm your computer” will be visible when a user tries to access your page.
Also, see: Hacked websites loads different UI?
Data Breach
When a site is hacked and user data is stolen, it is not immediately obvious. To avoid a data breach you should regularly monitor access logs and flag unauthorized access. Or you will be rudely informed about it when the data goes public.
Invisible hacking

There is a third kind of hacking when a hacker installs unnoticeable malicious codes into your website. In these cases, the site looks normal but a script may try to force the users to download a malicious file, often ransomware. Or they might try to sabotage your brand.
They might use hidden pages on your site as landing pages for spam email. They don’t meddle with the visible pages but use links to hidden subdirectories in spam emails campaigns. This might get your domain blacklisted by email providers and your domain may be flagged as spam
Also, see: How to find and remove website backdoors?
How to scan website for malware?
Diseases in humans can be detected at an early stage with regular health check-ups. Not unlike humans, websites might also show symptoms of disfunction, and if acted upon with agility it can save your website from severe damage that could have followed. Thus, websites need to be regularly scanned for malware and malicious content.
Google Site Checker
Google site checker is a free service. It does not provide detailed reports but will point out if your site has been flagged by the search engine for strange behavior.

The techniques employed by these Scanners are:
Signature-based pattern matching
This technique is the most popular in malware detection technique. The scanning tool matches files and code against known malware signatures. The main disadvantage of this technique is there is no exhaustive list of malware patterns that can be referred to. Since the malware is also a bunch of code lines, there can be an infinite number of patterns that the tool is not aware of.
Related Page – Common Malware Signature
Keyword Identification
Phrases like “eval” and “base64_decode“ are generally associated with malware. But a large number of good codes also use these words. Hence, this method is not foolproof for malware detection.
Related Article – Cleaning Eval(base64_decode) hack
Astra Malware Scanner
Astra provides complete 360° malware scanning and remedy. It provides great features like automatic daily scans, access log reports, vulnerability assessment etc. It doesn’t depend exclusively on the above mentioned techniques and employs machine learning powered scanners for 24 x 7 service.
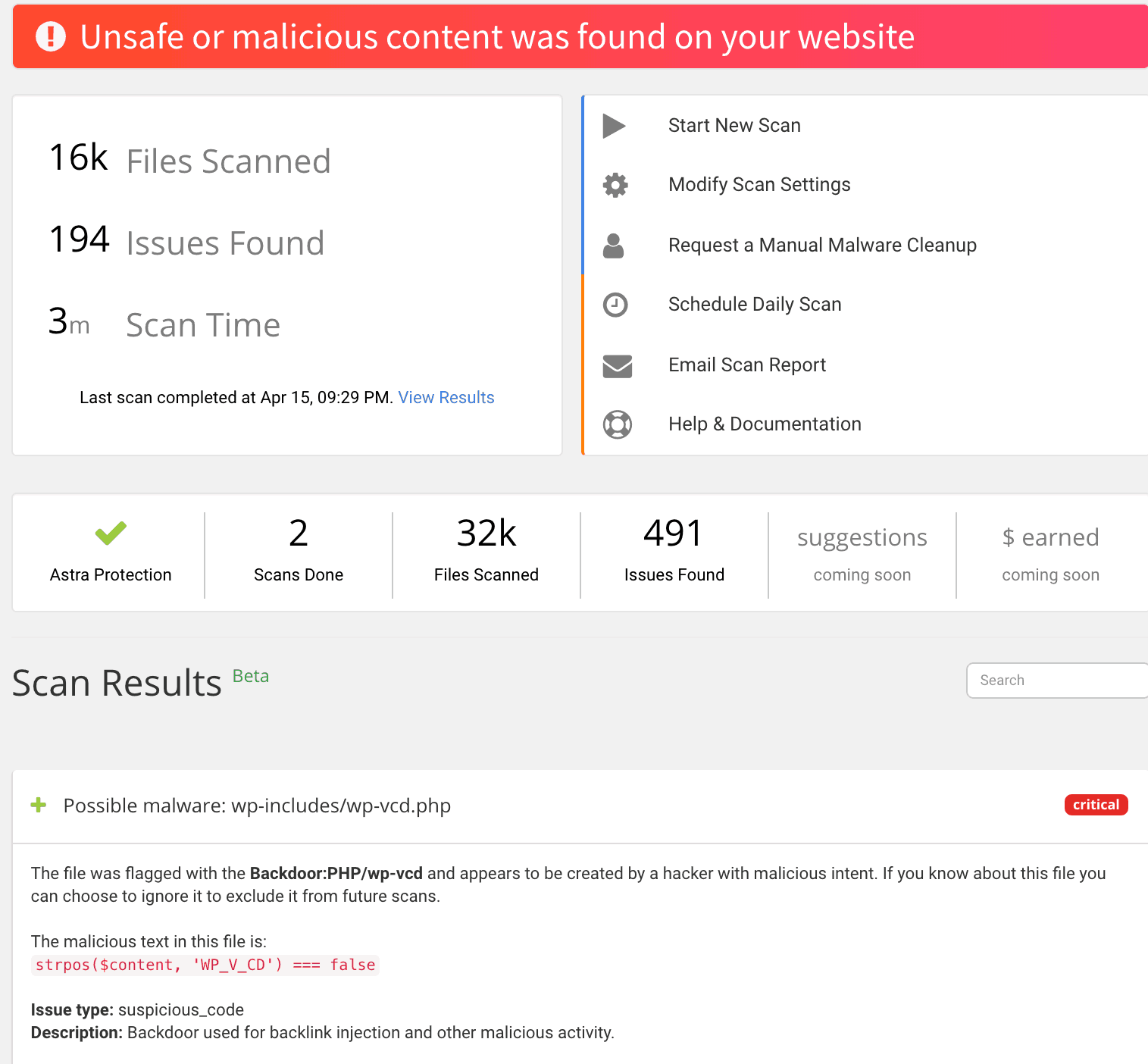
Linux Malware Detect (LMD)
Advanced users with their own servers can perform server scan with Linux Malware Detect along with the ClamAV virus engine. This malware detection software works at the server level and is especially good at detecting PHP backdoors, dark mailers and other malicious files etc.
Check Access log and Change log
Web hosts generally maintain access logs. The log is just a list of IP addresses and dates, but it can indicate when a strange IP address is accessing your site on an unusual hour. Some hackers will clear, disable, or edit the access logs to remove their presence.
Thus, better than skimming through access log is monitoring change log. A change log will show details of everything changed on your site. It shows when a file is overwritten or edited, or when new files and folders are added. Detection of unusual activity becomes easier and you can also find which specific web pages were affected.
Of course, you won’t always have logging enabled, so you might want to try a different approach.
Also, see: How can I check access logs of my website?
Code Monitoring and Backup
A tool that helps monitor and back up code is CodeGuard. It regularly backs up code and helps monitor any changes made to it.
It connects to your site and runs an initial backup. After that runs periodic backups and notifies you of any changes. This way if there are any discrepancies it can restore back your website to the previous state with a click of a button. It’s a really neat solution that combines both backup and malware checking.
Also, see: Detailed guide on website malware attack
How to protect website from malware?
Better safe than sorry. To keep your website safe and free from infections (malware injections) follow these few website health rules:
- Keep your CMS software and extensions up-to-date.
- Choose plug-ins and themes wisely as they provide additional gateways to malicious actors
- Schedule regular malware scans on website. Astra’s on demand Malware Scanner lets you scan your website in 10 minutes for the first scan and takes even lesser time (<1 minute) for subsequent scans.

- Back up the code and monitor changes made.
- Use two-step verification for login and limit the login attempts
- Enable web application firewall like Astra Firewall to block malicious traffic
Check out Astra’s complete malware protection suite.

















