2017 was the year of hackers. From content management systems, e-commerce portals, data breaches to hacked websites of financial institutions, cybercrime is on the rise with every passing year. 2017 witnessed staggering cyber attacks like the massive financial data theft in the Equifax Data Breach, the WannaCry Cyber Attack which was 2017’s deadliest ransomware attack, the Petya Ransomware attack, and the notorious yahoo data breach to name among a few.
How Are Websites generally hacked?
Google recently noted that it had seen a 32% rise in the number of hacked websites. The most common ways websites get hacked are:
- Missed Security Updates: Missing out on security patches and updates renders software vulnerable to attackers. It is imperative to make sure that the web server software, CMS, plugins, and other essential software are all set to update automatically.
- Weak Passwords: Compromised account credentials is one of the most rampant causes of hacked websites. Users often do not abide by strong password rules or use the same password for multiple accounts leading to a compromised account. A hacker can guess your password via random guesses or try different variations.
- Data leaks: On being mishandled, or improperly uploaded, data can become available as part of a leak. A method called “Dorking” can utilize common search engines to find the compromised data.
- Insecure themes and plugins: Attackers commonly add malicious code to free versions of paid plugins or themes. Therefore, while it is important to ensure patched plugins and themes, it is essential to remove themes or plugins which are no longer maintained by their developers. Moreover, be wary of using free plugins or those available through an unfamiliar website.
What hackers can do with hacked websites
But once information is compromised, what can a hacker potentially do with this data? While there are many speculations about this, getting into an attacker’s shoes to understand his post-hack actions can help you minimize damage from potential future cyber attacks.
A hacker’s post-breach checklist is likely to contain the following actions:
-
Form a Stolen Data Inventory
Post-breach, hackers form an inventory of financial information like credit card details, authentication credentials, personal information like names, addresses, and phone numbers.
-
Sell information
Personal information like names, credentials, addresses, and phone numbers are sold by hackers in bulk. Quartz estimates that a full set of someone’s personal information including identification number, address, birthdate, and possibly credit card info can cost between $1 and $450 in the black market.
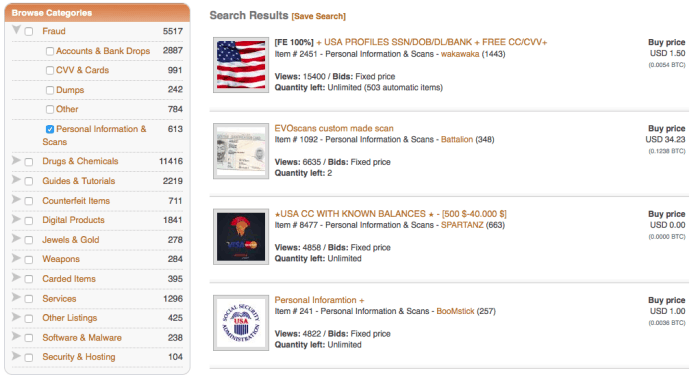
Filter out the good stuff
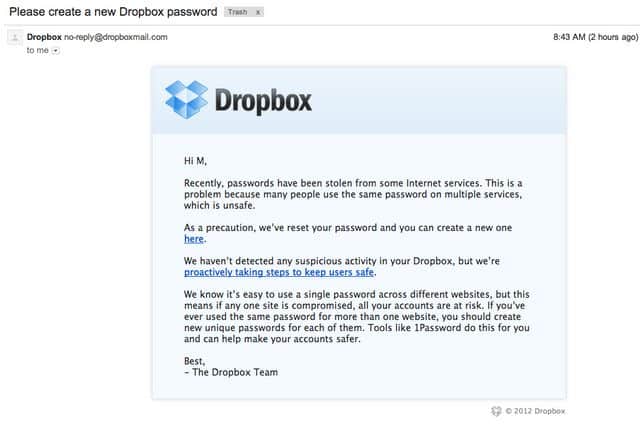
After creating an inventory of all breached authentication accounts, hackers then look for the most lucrative ones which can be sold for higher values than the rest. Information like government and military addresses are extremely valuable. Other valuable information would include company email addresses and passwords for large corporations. A hacker can sell these credentials to others on the dark web for a much higher price. Moreover, hacks from one website can lead to information breach on another. For example, when Dropbox was breached in 2012, it as done so using credentials stolen during the Linkedin data breach, the same year. Users often re-use the same passwords for multiple accounts, and this is something that a hacker usually exploits.
Sell the cards
Hackers generally sell financial information like credit card numbers in bundles to individuals with the right knowledge in groups of ten or a hundred. This information is usually sold to a “broker” who then sells them to a “carder” without being detected. These “carders” could use stolen credit card information to purchase gift cards to stores or to Amazon.com, and then use those cards to buy physical items.
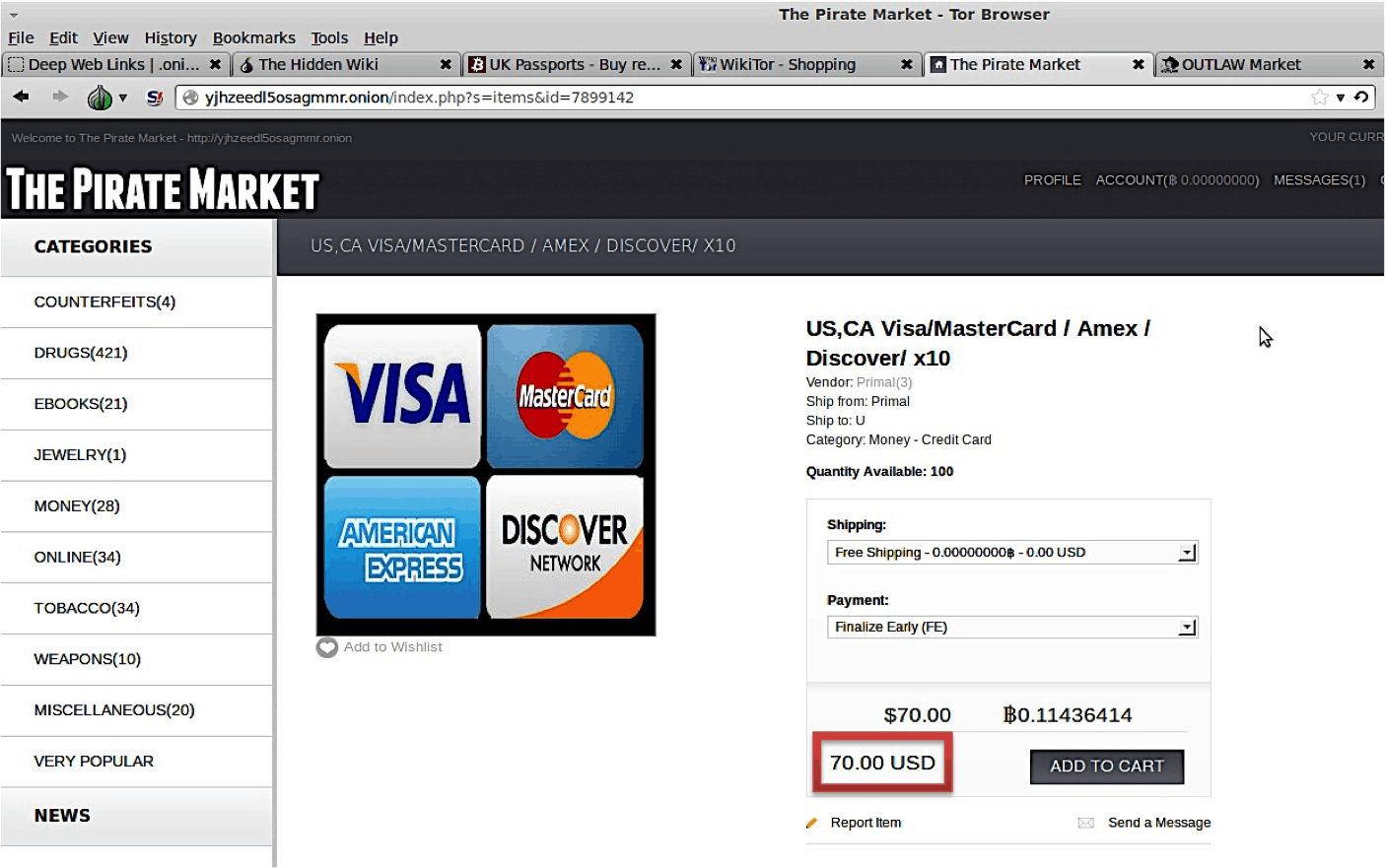
The gift card, in turn, is used to purchase high-value goods such as electronics, making it difficult for companies to trace. By the time the company figures out the fraud and the cards are blocked, the criminal is in possession of the purchased goods. These packages are usually then shipped via a re-shipping scam. Using legitimate channels such as Craigslist job listings, unsuspecting individuals are recruited as Mules (re-shippers). The goods are then usually shipped outside the country, or directly to someone who purchases the goods from an auction site the fraudster has posted the goods to.
Bulk Sale
The hacker will collect authentication credentials and sell them in bulk at a discounted price. Post-breach, the hacked company would take necessary measures to repair the damage and change credentials making most of the credentials worthless. Hence, the hacker benefits from a bulk sale at discounts.
Also, check our video on Simple WordPress Security Tips to Follow in 2018.
Download our Secure Coding Practices Checklist for Developers to reduce the chances of getting hacked.
Worried about your website’s safety in light of rampant online vulnerabilities? Contact Astra’s Web Security Suite to know more for further protection.
















