Cloud Security Frameworks is a comprehensive or specific set of rules that support cloud security precautions. This process outlines the policies, tools, configurations, and rules for specific cloud use.
Some cloud security frameworks are broad and intended for general use, whereas others are industry-specific, such as healthcare and defense.
In the cloud security framework, providers are responsible for specific security aspects, while customers are responsible for the rest of the cloud app security measures.
What does the cloud security framework cover?
1. Cloud Security Alliance (CSA) and Cloud Controls Matrix (CCM)
The CCM cloud security framework offers a control framework that provides an understanding of security concepts and principles aligned with CSA guidance. It covers 17 domains and 197 controls.
2. National Institute of Standards and Technology (NIST) Cybersecurity Framework
The NIST cloud security framework offers private sector organizations a policy framework of computer security recommendations for evaluating and enhancing their capacity to stop, recognize, and respond to cyberattacks.
3. Center for Internet Security (CIS) Controls
The Center for Internet Security (CIS) comprises experts who agree on reliable defenses in real-world scenarios.
4. ISO/IEC 27001
Organizations can manage the security of assets like financial data, intellectual property, employee information, and information entrusted to third parties with ISO/IEC 27001.
5. Federal Risk and Authorization Management Program (FedRAMP)
To ensure compliance with governmental standards for cloud assessment, authorization, and monitoring, FedRAMP standardizes how non-government organizations implement security controls.
6. CSA Security
CSA’s comprehensive security guidance includes 14 domains covering application security, data security and privacy, encryption and key management, identity, and access management, virtualization security, etc.
What are the categories of cloud security in the cloud security framework?
Checklist of cloud security or framework for cloud security will usually address the following key categories to ensure holistic security.
1. Data Security
In cloud computing, data security means securing the data processed, sent, or stored there. It safeguards cloud-based data against unauthorized access, use, disclosure, disruption, modification, inspection, recording, or destruction. Data security includes encryption, access controls, backups, and classification.
Businesses must use access control to limit who has access to their data, encrypt it before storing it in the cloud, and keep an eye out for unauthorized access or modification.
2. Identity and Access Management (IAM)
Identity and Access Management (IAM) manages user identities, authentication, and authorization. IAM involves limiting user roles, permissions, and policy-based access to cloud resources.
IAM measures include user provisioning, multi-factor authentication, access controls, and identity federation. User provisioning entails creating, modifying, and deleting user accounts, whereas multi-factor authentication adds a layer of security by requiring users to provide two or more authentication factors.
IAM plays a critical role in controlling access to cloud resources based on user roles, permissions, and policies
3. Network Security
Network security refers to safeguarding network traffic and infrastructure in a cloud environment. Cloud service providers must have a network infrastructure that is safe, dependable, and scalable. Network security measures in the cloud environment include network segmentation, virtual private networks (VPNs), intrusion detection systems, and firewalls.
Network security aims to establish and maintain the safety of network connections and infrastructure in the cloud environment. The most efficient way cloud providers can guarantee network security is through network isolation for each client.
4. Application Security
Application security is critical in the cloud environment and focuses on protecting cloud-based applications against attacks on the applications and services used in the cloud environment.
In the cloud environment, applications are typically accessed over the internet, making them vulnerable to attacks such as SQL injection, cross-site scripting, and command injection. Application security includes secure coding practices, vulnerability testing, and web application firewalls.
To identify and stop application-level assaults, cloud service providers deploy firewalls, intrusion detection and prevention systems, and code-scanning technologies.
5. Compliance and Legal
Compliance and legal measures ensure the cloud environment complies with relevant regulations, standards, and contractual obligations, including HIPAA, PCI-DSS, and GDPR. Measures taken to ensure compliance with the law include audits, monitoring, and documentation.
Cloud providers must implement various security controls and procedures to ensure their services meet multiple requirements. Compliance and legal issues deal with complying with industry standards, regulations, and laws related to data privacy and security in the cloud.
Cloud providers must implement security controls and procedures after fully understanding the compliance requirements.
6. Physical Security
Physical security is essential to cloud security, especially for cloud service providers (CSPs) who operate data centers and other physical infrastructure. Physical security refers to controlling physical access to cloud infrastructure, including data centers, servers, network devices, etc.
Access controls, surveillance, environmental controls, and redundancy are crucial physical security measures to protect the physical infrastructure from unauthorized access, theft, and damage. The data center is watched over for security incidents using surveillance. Access controls are used to restrict access to physical infrastructure.
7. Incident Response and Recovery
Incident response allows organizations to ensure that they are aware of security incidents and can respond on time to limit the damage to their systems. Incident response is the process of managing cyberattacks in a cloud environment.
Incident response and recovery measures focus on responding to and recovering from security incidents, including data breaches, system failures, and natural disasters.
A cloud incident response system differs from a non-cloud incident response system in several key ways, notably in governance, shared responsibility, and visibility.
1. Infrastructure as a Service (IaaS)
In IaaS, the provider and the customer share responsibility for security issues like network security, host security, and virtualization security.
The provider protects the physical infrastructure and virtualization, whereas the customer protects the operating systems, applications, and data.
2. Platform as a Service (PaaS)
In PaaS, the provider secures everything at the platform level, including infrastructure and components. The customer confirms only applications and data are deployed on a provider-managed platform.
3. Software as a Service (SaaS)
The provider secures everything in SaaS, including infrastructure, platforms, applications, and data. The customer is only responsible for security features within the applications (like access control) and the security of customer data.
What is the Importance of Cloud Security Frameworks?
1. Protection of Data
Data is one of the most valuable assets of an organization, and these frameworks provide measures to protect it from theft, loss, or unauthorized access. The framework implements various security measures to ensure data confidentiality, integrity, and availability.
Encryption, access control, and data backup are security measures implemented in a cloud security framework to protect data. The cloud security framework ensures that the data is encrypted, access is authorized, and data loss or leakage is prevented.
Access control mechanisms, such as multi-factor authentication and role-based access control, ensure that only authorized individuals can access sensitive data.
2. Mitigation of Security Risks
With cyber threats becoming more sophisticated, a comprehensive cloud security framework can mitigate security risks and ensure compliance with regulations. Regular risk assessments and vulnerability scans identify potential security threats and vulnerabilities.
The cloud security framework helps identify and mitigate various security risks associated with the cloud, like data breaches, account hijacking, insecure interfaces, shared technology vulnerabilities, etc.
The framework employs security controls like firewalls, intrusion detection and prevention systems, and security information and event management (SIEM) techniques to identify and stop security incidents.
Another method for finding vulnerabilities that attackers might exploit is penetration testing.
3. Compliance with Regulations
Organizations that store and process sensitive data are subject to industry-specific regulations and compliance requirements. Customers of cloud services frequently believe that the CSP is entirely in charge of security; as a result, they need to put in place robust policies.
The cloud security framework ensures that the cloud services and infrastructure comply with regulations like GDPR, HIPAA, ISO 27001, PCI DSS, etc.
Cloud security compliance management helps organizations adhere to their cloud systems’ internal rules, standards, and regulatory requirements. The cloud security standards ensure that the organization complies with these regulations and avoids fines and penalties.
4. Trust and Customer Confidence
Trust and customer confidence are essential factors that help to build and maintain a reputation with stakeholders. The main barrier to widespread cloud computing is the need for potential customers’ trust in clouds.
Cloud security frameworks contribute to building trust and confidence with customers, investors, and other stakeholders. Transparency, reliability, and security are still being added to the cloud model to meet client needs.
Organizations implementing a robust cloud security framework can demonstrate their commitment to protecting sensitive data and maintaining a solid security posture.
This can help build a positive reputation, increase customer loyalty, and differentiate the organization from competitors.
5. Business Continuity and Disaster Recovery
Cloud computing is as important as any other technology regarding business continuity and disaster recovery (BC/DR). A robust cloud security framework can ensure business continuity and disaster recovery by enabling quick responses to any security incidents.
A cloud security framework includes various measures to ensure the company can quickly recover from disruptions, including disaster recovery plans, data backup, and redundancy. Business continuity and disaster recovery ensure critical business functions can continue despite unexpected events.
Furthermore, BC/DR must adopt a risk-based strategy. In the cloud, many BC options might be too expensive, but they might be optional.
6. Scalability and Flexibility
The security controls and framework should also scale as cloud infrastructure scales. The cloud security framework provides the flexibility to scale security in line with the scaling of cloud resources. Organizations can quickly adapt to new security threats, compliance requirements, and business challenges without compromising the security of their data.
The cloud security framework ensures that the organization can continue to grow and innovate without sacrificing security. A cloud security framework is designed to be flexible and scalable to accommodate changing business needs and technological advancements.
Best Practices in Cloud Security Frameworks
1. Industry Standards and Compliance
Data considered secure in one nation might not be safe in another. Therefore, data ownership and governance become vital considerations when choosing a cloud service provider.
Cloud security alliances are more complicated than they appear because there are no reliable standards for cloud security, and this piecemeal approach does not meet the criteria for “good security.”
Cloud security standards should adhere to industry and compliance requirements such as PCI DSS, HIPAA, and GDPR. Adhering to these regulations ensures that the organization follows best practices and avoids penalties for non-compliance.
2. Comprehensive Coverage
The cloud security framework should provide comprehensive coverage of all aspects of cloud security. The several aspects of cloud security include data protection, access control, vulnerability management, network security, and incident response.
A comprehensive security framework identifies and mitigates all potential security risks. Comprehensive coverage ensures that all aspects of cloud web security are addressed and that organizations have a holistic approach to protecting their data and systems in the cloud.
3. Flexibility and Scalability
Flexibility and scalability are essential for cloud security frameworks because they allow organizations to adapt to changing business needs and technological advancements.
As business needs evolve, the security framework should be able to adapt to new security threats, compliance requirements, and business challenges without compromising data security.
Scalability is also important because it allows the organization to manage security across multiple cloud environments, including public, private, and hybrid clouds.
The cloud security framework must consistently apply security controls across all cloud environments.
4. Integration with Cloud Services
Integration with cloud services ensures that all security controls are applied consistently across all platforms, providing a unified approach to cloud security. Cloud security frameworks should integrate with cloud services to implement all security measures across all platforms.
Cloud security frameworks should leverage APIs to integrate with cloud services and ensure that all security controls are applied consistently across all cloud platforms.
Cloud-native security services, such as AWS Security Hub or Azure Security Center, can provide additional security controls and insights into the security posture of cloud environments.
5. Vendor Support and Community
Strong vendor support and community engagement ensure the framework is up-to-date with the latest security threats, vulnerabilities, and best practices. A strong vendor community provides access to resources, such as documentation, training, and support, to help organizations implement and maintain the security framework.
Choosing a trusted vendor is essential for ensuring the security framework is reliable and effective. A robust community allows the organization to collaborate and share best practices with other users.
6. Customization and Alignment with Organizational Needs
Cloud security frameworks should be customized to meet the organization’s needs. Organizational needs include identifying the types of data that need to be protected, the compliance requirements that apply, and the level of risk tolerance.
The security framework should be tailored to address the organization’s specific needs while adhering to industry standards and best practices. Customization helps to ensure that the organization’s unique security requirements are met, providing a more practical approach to cloud security.
Critical Components of a Cloud Compliance Framework
1. Regulatory Analysis
The regulatory analysis identifies the regulatory requirements and industry standards that apply to the organization’s cloud environment. Regulations such as GDPR, HIPAA, PCI DSS, and industry standards such as ISO 27001 and the NIST Cybersecurity Metric are part of regulatory analysis.
Regulatory analysis helps organizations understand their compliance obligations and design a cloud compliance framework that meets those obligations.
2. Control Objectives
Control objectives are the specific goals that an organization aims to achieve through its cloud compliance framework. Control objectives are often based on regulatory requirements and industry standards and are designed to ensure the organization’s cloud environment is secure and compliant.
Examples of control objectives include maintaining data confidentiality, ensuring data integrity, and implementing access controls.
The COSO compliance categories that the Controls are meant to mitigate are defined by the Control Objectives.
3. Risk Assessment
Risk assessment entails locating and evaluating potential threats to the organization’s culture. The risk assessment includes finding potential security threats, vulnerabilities, and compliance risks.
Identifying the assets that need to be protected, such as data, applications, and infrastructure, is the first step in the risk assessment process. Risk assessment helps organizations understand the potential impact of these risks and design controls to mitigate them.
4. Policies and Procedures
Policies and procedures are an organization’s written rules and guidelines to ensure its cloud environment is secure and compliant. Regulations and industry standards should be the foundation for data security, access control, and incident response policies and procedures.
Policies and procedures help ensure that everyone in the organization understands their responsibilities for cloud compliance and that compliance is consistently enforced.
5. Data Governance
Data collection, storage, and use within the cloud are all streamlined by a set of policies, regulations, and procedures known as cloud data governance. Data governance includes implementing data classification and access controls and ensuring data is encrypted and backed up regularly.
Data governance ensures compliance and democratizes data. Collaboration is possible even as the data landscape gets more extensive and complicated.
Data governance is essential because it ensures people can access helpful, high-quality data.
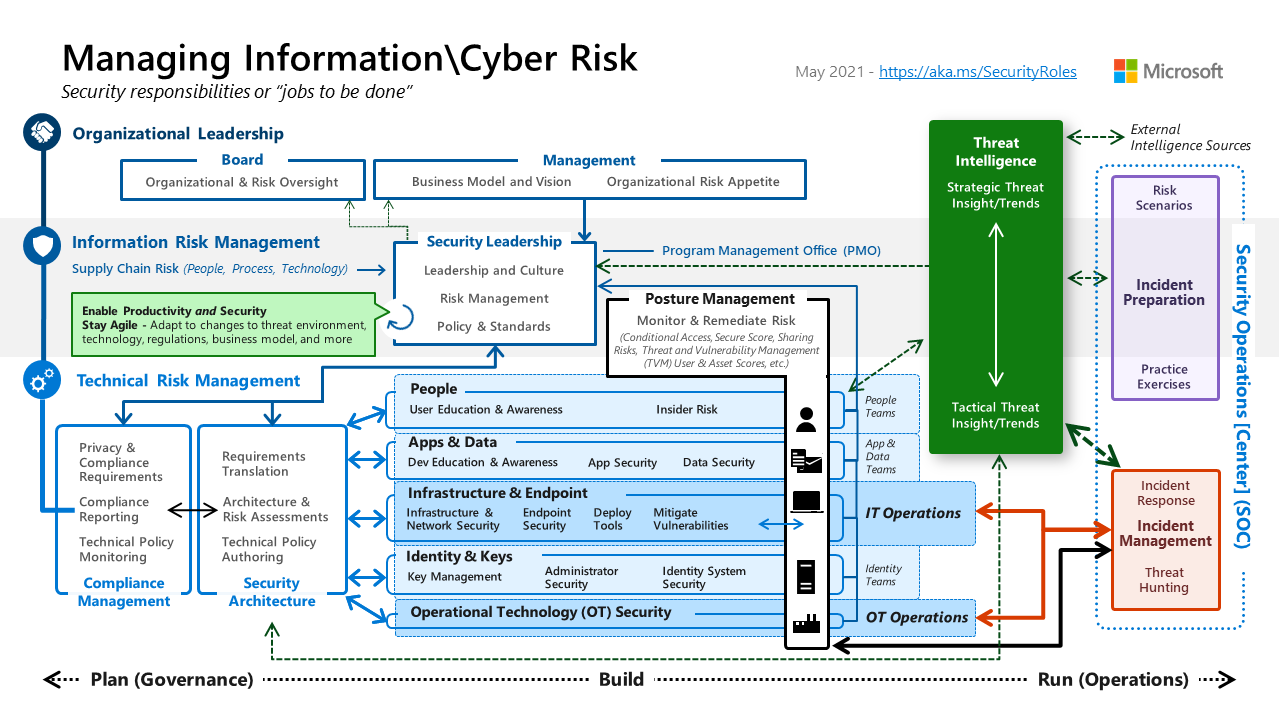
Conclusion
Cloud security frameworks guide controls and compliance with regulations. A robust cloud compliance framework helps build trust in cloud services. Following best practices around identity management, data encryption, vulnerability assessments, and auditing is vital to security in the cloud. Regular reviews of risks and controls ensure a robust cloud security posture.
Frequently Asked Questions
How does the cloud security framework work in cloud computing?
A cloud security framework provides guidelines and best practices for implementing secure cloud services.
It defines security standards, controls, and processes across identity and access management, encryption, auditing, vulnerability management, and incident response.
What is the difference between NIST and CSA cloud security framework?
NIST focuses more on technical controls and security objectives. CSA takes a broader view and covers governance, legal, and compliance issues, and technical aspects.
What are cloud security framework examples?
NIST Cybersecurity Framework: Guides organizations on managing cybersecurity risks.
CSA CSM: Assess security controls for cloud environments.
ISO 27001: Includes requirements for a cloud security framework.
PCI DSS: A payments industry standard
HIPAA: Outlines security requirements for protecting patient health data.
















