The budget appendix released by the White House, includes approximately $12.7 billion for civilian cybersecurity-related activities, a 13% increase over the previous year. the FBI reported a 48% increase in cybercrime and related frauds in a 2022 report.
As the scope and sophistication of these scams deepen, organizations need to adopt technologies and practices that enhance cybersecurity defenses. Organizations can use cloud app security checklists to deepen their horizons and cover all security bases.
This is where a cloud security checklist becomes effective. With this cloud security checklist, you will be able to assess your organization’s security posture understand your weaknesses, and reduce the risk of security breaches and data loss.
Key Cloud Security Checklist
Below detailed is a checklist of cloud security best practices that can help safeguard your cloud assets and platform from any exploitation.
1. Understand the top risks to your cloud security
Identify all sensitive information that is stored and transmitted within your cloud platform. This data could be anything that ranges from customer information, patents, confidential designs, and trade secrets.
Conduct penetration tests and vulnerability assessments to detect any threats or vulnerabilities in your cloud security. The idea here is to detect all risks to your cloud environment so that a comprehensive cloud security management plan can be made.
Have a good knowledge on the shared responsibility model followed by your company. There are different models for IaaS, PaaS, and SaaS. The shared responsibility model varies based on your CSP be it Azure, AWS, or GCP.
Having a well established shared responsibility agreement allows you and your employees to be aware of what security responsibilities fall on you and your CSP respectively. This in turns provides you with a better visibility and control over your cloud platform’s security.
This can also be included a cloud compliance checklist as compliance with data protection standards such as GDPR or industry specific standards such as HIPAA. According to most global security standards, both the cloud service provider and customer should be compliant in maintaining the cloud environment’s security.
3. Establish policies and procedures
The cloud security best practices checklist and policy is a formal guideline your employees adhere to; to ensure safe and secure operations in the cloud.
| The standard cloud security checklist and policy template includes: 1. Purpose of the policy 2. Data covered by the policy – this could include: financial, sensitive and proprietary information, personally identifiable information among others 3. Ownership information – outline accountability – who does the policy apply to and what are their responsibilities 4. Permitted services by your cloud provider 5. Compliance and regulatory details 6. Cloud inventory 7. Risk assessment before the policy is implemented 8. Security controls 9. Security incident response 10. Disaster and recovery plan 11. Policy enforcement 12. Cloud L&D policies |
4. Establish an IAM strategy
IAM systems are used to create efficient workflows and equip team members to keep your critical assets secure.
IAM is a framework of policies to manage digital identities and enable secure authentication for your organization’s digital assets across on-premise and cloud-based systems.
| The IAM cloud security best practices checklist includes: 1. Mention stakeholders with assigned responsibilities and actions they are accountable for. 2. Formulate a user access review process using Policy Based Access Control (PBAC). 3. Enable Single Sign-on (SSO), Two-Factor Authentication (2FA), and Multi-Factor Authentication (MFA). 4. Automate the access lifecycle with provisioning and de-provisioning processes (assigning and removing permissions). 5. Implement segregation of duties. 6. Delete/disable idle accounts. 7. Document the entire IAM system. |
5. Incorporate network security solutions
The umbrella term network security covers several technologies, policies, procedures, and devices to secure a network’s confidentiality, integrity, and accessibility. The combination of software and hardware technologies prevents unauthorized network access and safeguards digital assets within the network.
| The critical network solutions that should be a part of your cloud security checklist are: 1. Firewall to block malware and application-layer attacks. 2. Access control including Multi-Factor Authentication (MFA). 3. Anti-malware solutions. 4. Email security includes multi-layered email content analysis, sender identity verification, and imposter detection. 5. Data Loss Prevention (DLP) policies. 6. Intrusion Prevention and Detection Systems (IPS) especially when your workforce is remote or hybrid. 7. Endpoint security like Managed Detection and Response (MDR), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR). 8. Network segmentation |
6. Have a ransomware prevention checklist
With ransomware perpetrators refining their malware payloads, it is estimated that ransomware will cost its victims nearly $265 billion annually by 2031, with a new attack on consumers and businesses every 2 seconds. All they would need is an initial access point, encrypting networks, and extracting sensitive data for extortion from victims.
| Your ransomware prevention cloud security best practices checklist should have: 1. Employee ransomware threat education. 2. Updated firewalls and antivirus systems. 3. Email filtering systems. 4. Regular security assessments and data scans. 5. Access controls: Role-based Access Control (RBAC), Discretionary Access Control (DAC), and Mandatory Access Control (MAC). 6. Endpoint protection. 7. Continuous monitoring of networks and devices. 8. Patch management. 9. Data backup. |
7. A comprehensive data backup and recovery policy
Risk mitigation is integral to business continuity and how soon you can restore data and operations after an attack makes the difference between collapse and business continuity.
| Your data backup policy and cloud security checklist should include: 1. Frequency of backups 2. Data retention policy 3. Parties/departments responsible for the backup processes 4. Verification of policy compliance 5. Gap assessments 6. Performance data to verify data backups and recovery activities 7. Penalties for non-compliance 8. Protection policy to ensure backup data is encrypted when data is in-transit and at rest |
8. Encrypt your cloud data
This is one of the most important parts of the checklist for managing cloud security. This step protects your data and also:
- Addresses compliance with regulatory standards regarding data protection and privacy.
- Enhances protection against unauthorized data access from public cloud sources.
- Protect data as it moves to and from third-party cloud-based applications: both for data in transit and at rest.
| Your encryption related cloud security checklist should include: 1. Use hardware encryption for encryption at rest. 2. Use HTTPS or SSL with medium-strength ciphers for encryption in transit. 3. Safeguard all private keys for certificates and public keys. 4. Encrypt data in databases. 5. Encrypt backups and stored files with AES-256 or stronger encryption. 6. Use VPN tunnels with AES-256 encryption. |
9. Perform log monitoring
The adoption of cloud-native tech, hyperscale cloud providers, and containerized microservices are driving the importance of log monitoring. It tracks events and activity as and when they occur. It is a record of when and what happens in your digital infrastructure.
| The critical elements of your log monitoring activity to be included in your cloud security checklist are: 1. Monitor security events and logs on-premise, on the cloud, and for potential hardware failure. 2. Conduct regular compliance audits to ensure the cloud environment complies with regulatory standards. 3. Log change activities such as network security and overall security policies. 4. Regularly review and update security controls based on the changes in the threat landscape. |
10. Prepare a cloud incident response (IR) plan
Reviewing access controls and third-party security and verifying backup and incident response plans are integral to cloud risk assessment.
On average, companies with an incident response plan have an average data breach cost 55% lower than companies without one. Incident response is critical in your cloud security checklist as it allows your organization to determine the scope and impact of the incident and restore operations in the wake of disruption.
| Your incident response plan and cloud security checklist should specify: 1. How to respond to an incident? 2. The people responsible and their roles and responsibilities in the face of an incident 3. Steps to follow at each stage of an incident response: preparation, identification, containment, eradication, and recovery 4. Communication pathways between the IR team and the rest of the organization 5. Metrics to assess the effectiveness of the incident response plan |
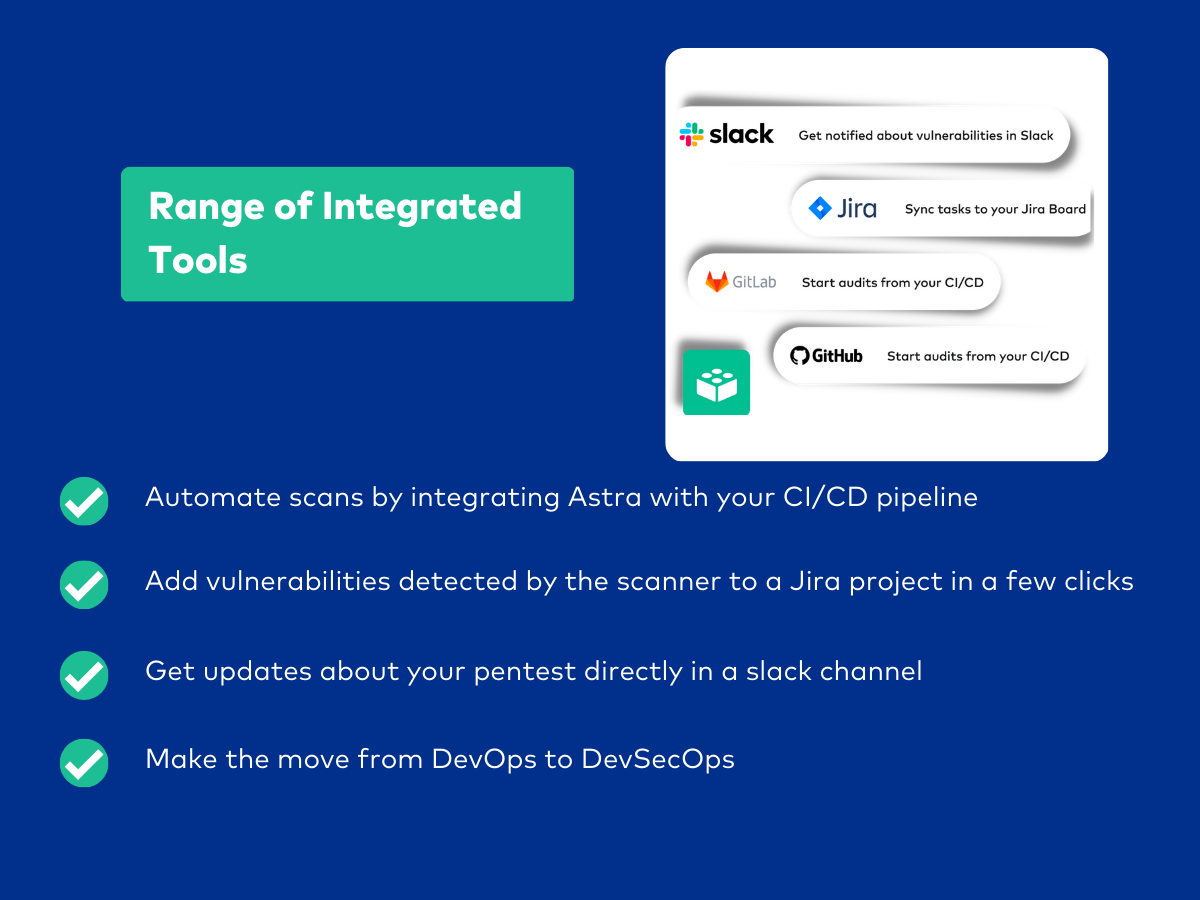
Managing your cloud security with Astra
The cloud security checklist has so many moving parts: that it is easy to let some slip down the crack. Secure your digital assets over the cloud with Astra’s cybersecurity services.
Astra’s cybersecurity services include:
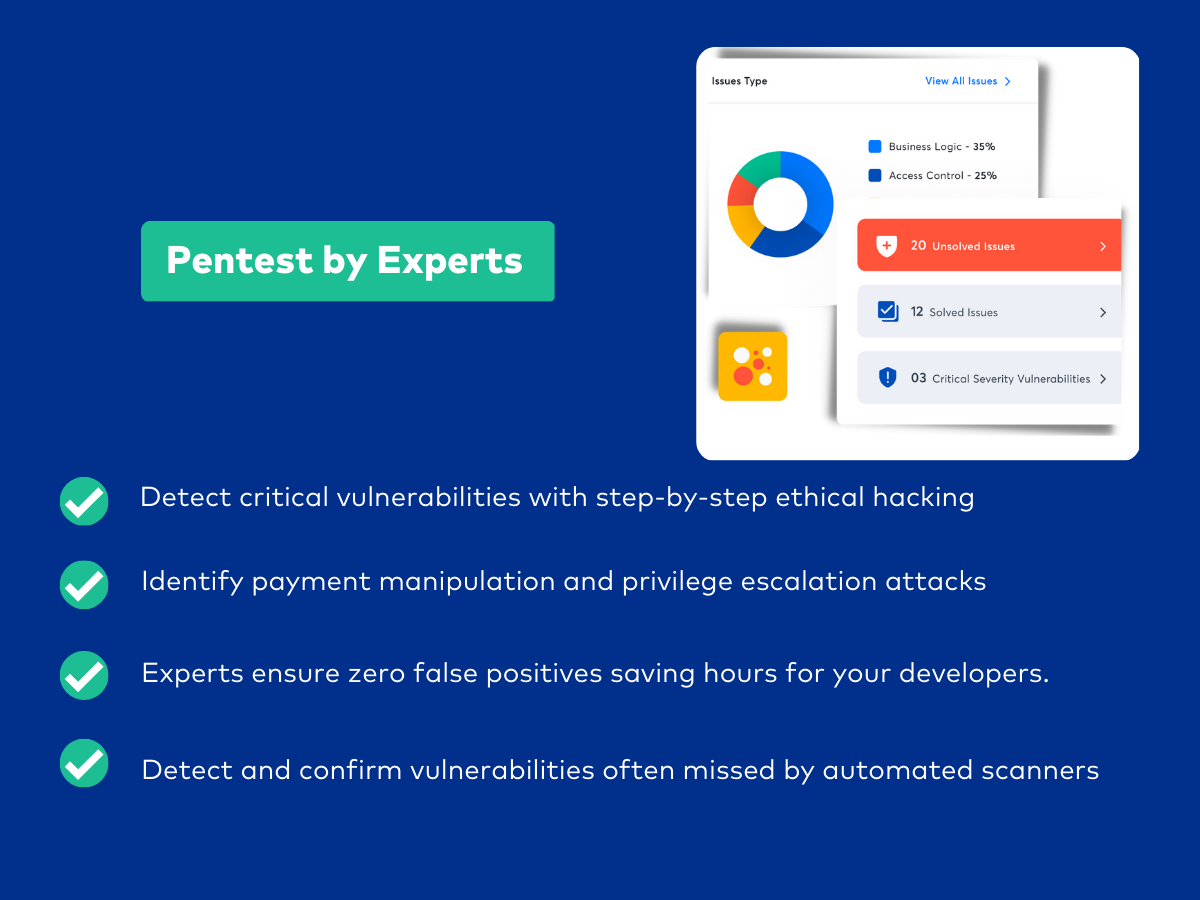
Continuous penetration testing -To detect gaps and vulnerabilities in your security, detect payment manipulations, and spot business logic errors.
Astra’s pentesting services test the security of your API, networks, web and mobile apps, and cloud infrastructure.
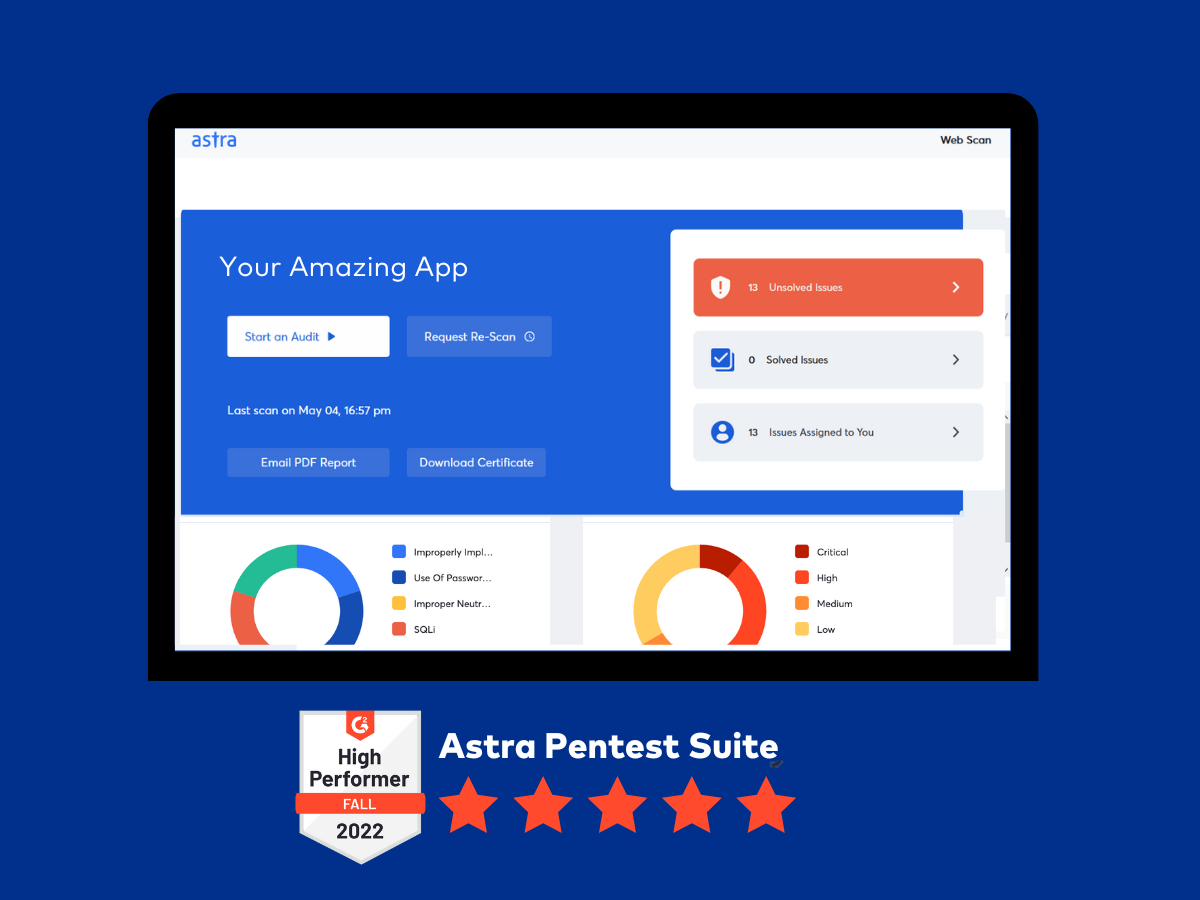
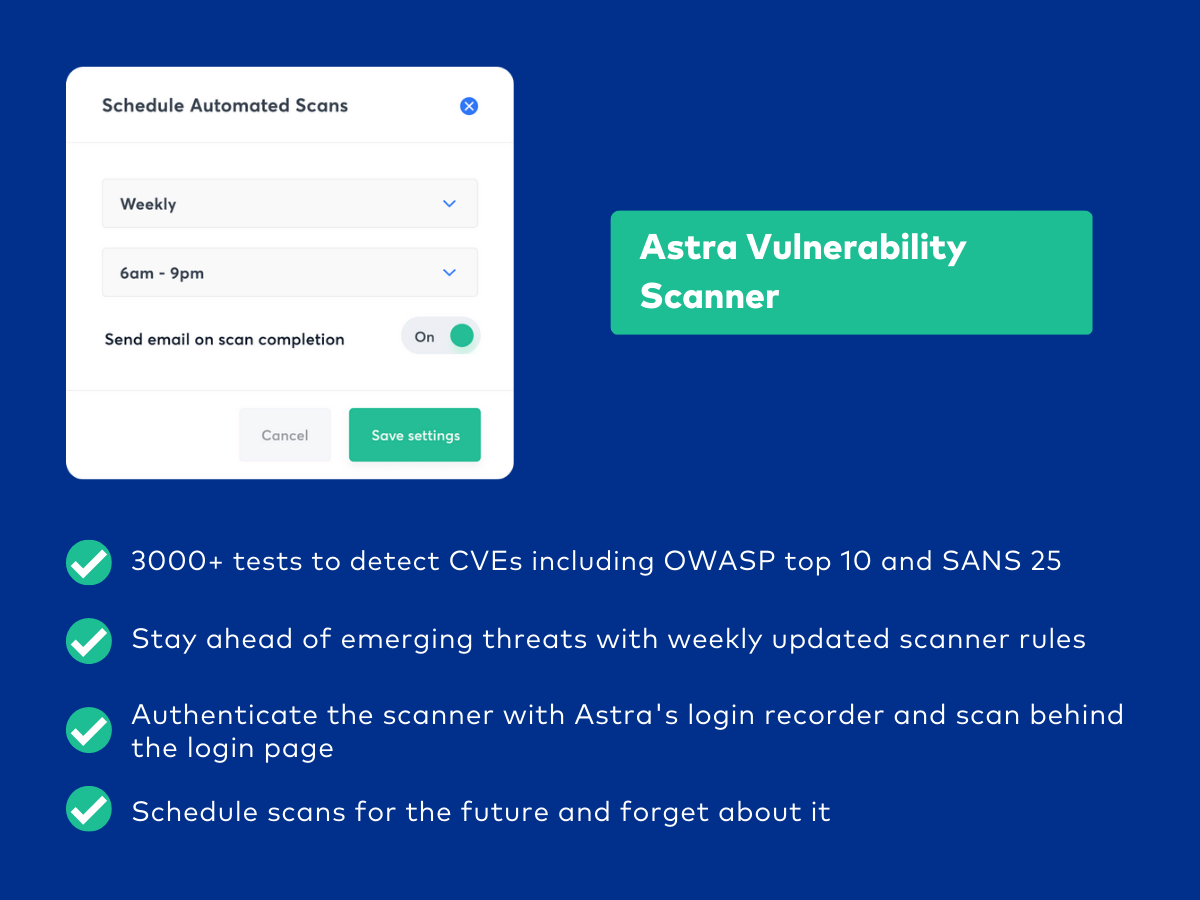
In-depth vulnerability assessment – Astra’s automated scanner continuously scans your assets with over 3,000+ tests to identify vulnerabilities.
Malware scanner – Swiftly detect and mitigate malware infections with our unlimited, automated, and scheduled scans that run daily to keep your cloud systems safe.
Compliance-specific scans – Astra’s compliance dashboard has real-time alerts for vulnerabilities and areas of non-compliance. Start by choosing the penetration testing compliance (HIPAA, SOC-2, GDPR, PCI DSS, and ISO 27001) you want to scan. Get detailed reports with compliance weaknesses and remediation measures.
Scan behind logins – Test your credentials and role-based access security with Astra’s scan behind logins.
Support from experts – Our certified security experts review each vulnerability and provide clear steps to fix the issues.
Wrapping up
Your data is your most valuable asset as a business. It is important that you have all of the best resources available to protect your assets.
This cloud security checklist gets you on step closer to absolute protection:
- Establish policies and procedures
- Establish an IAM strategy
- Incorporate network security solutions
- Have a ransomware prevention checklist
- A comprehensive data backup and recovery policy
- Encrypt your cloud data
- Perform log monitoring
- Prepare a cloud incident response plan
Well, if all of this seems a lot, you need not do it all on your own. Astra Security’s cyber security and pen testing services keep your cloud environment safe and help you achieve compliance.
To know more about how we secure your cloud-hosted environment, talk to our security experts.