Article Summary
You need not worry about hosting, online services like Hostgator have made web hosting just a matter of minutes. It has greatly improved the hosting experience for the site owners. The cyberspace, as you already know, is full of threats known and unknown. In fact, it’s just a matter of time before hackers catch up with your website’s security. A malware attack on the site can lead to account suspension from Hostgator. And if you have had your website compromised then in order to restore your suspended account, Hostgator malware removal is necessary.
Hostgator is one of the leading web hosting platforms. While Hostgator claims 99.9% uptime to its customers, there are times it takes certain websites down. If you have recently had your Hostgator account suspended, you might be wondering why it happened and what to do now, this post has your answer.
Before we start dissecting the problem, here’s how a HostGator account suspension message looks like:
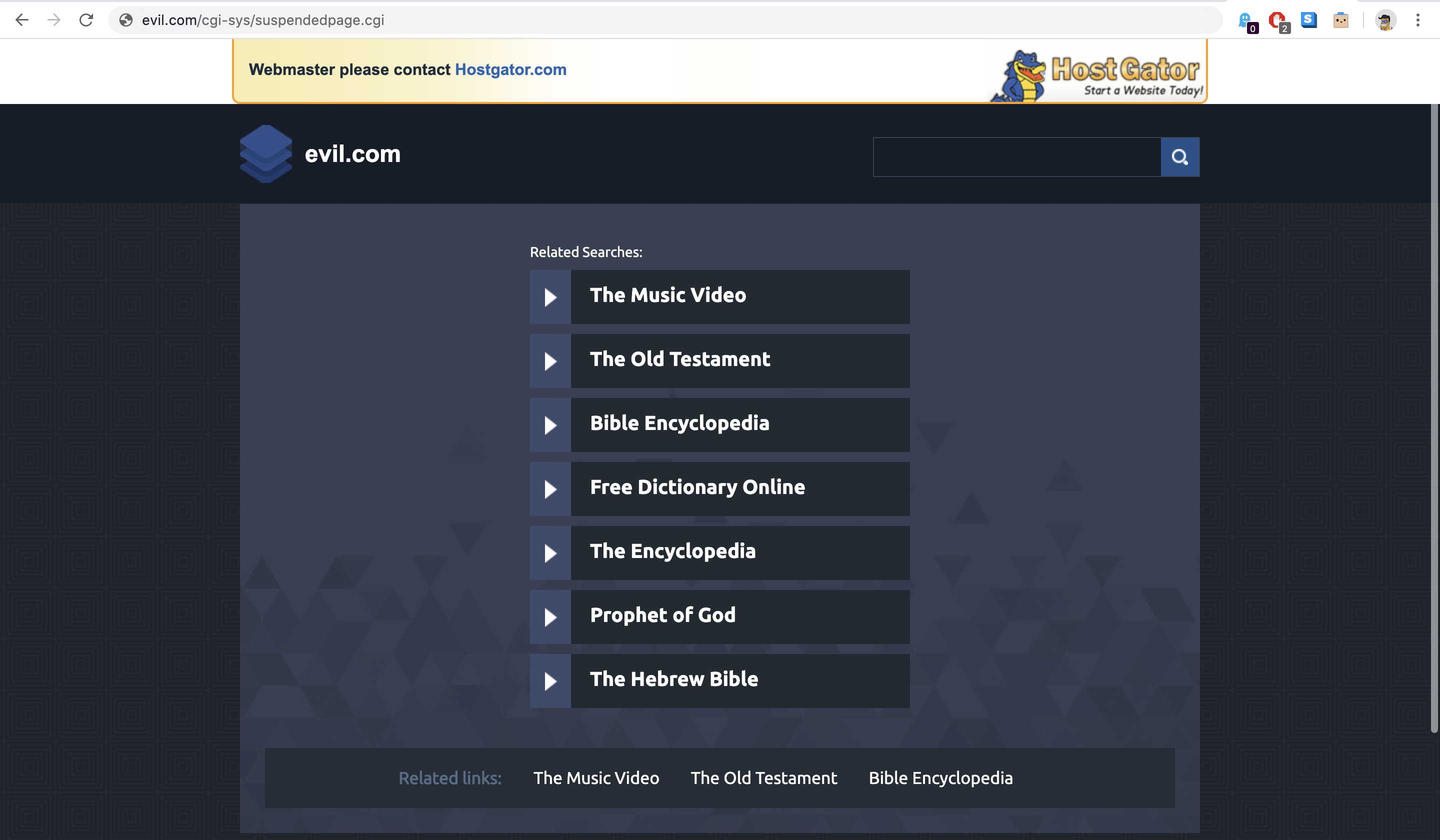
There could be many reasons behind the HostGator account suspended message. Payment failure, server overload, malware, phishing content, malverts, and so on. In order to unsuspend your website, you will have to identify the issue first and then work to solve it. In case of a malware attack, malverts, phishing & spam content on your website, a Hostgator malware removal becomes necessary.
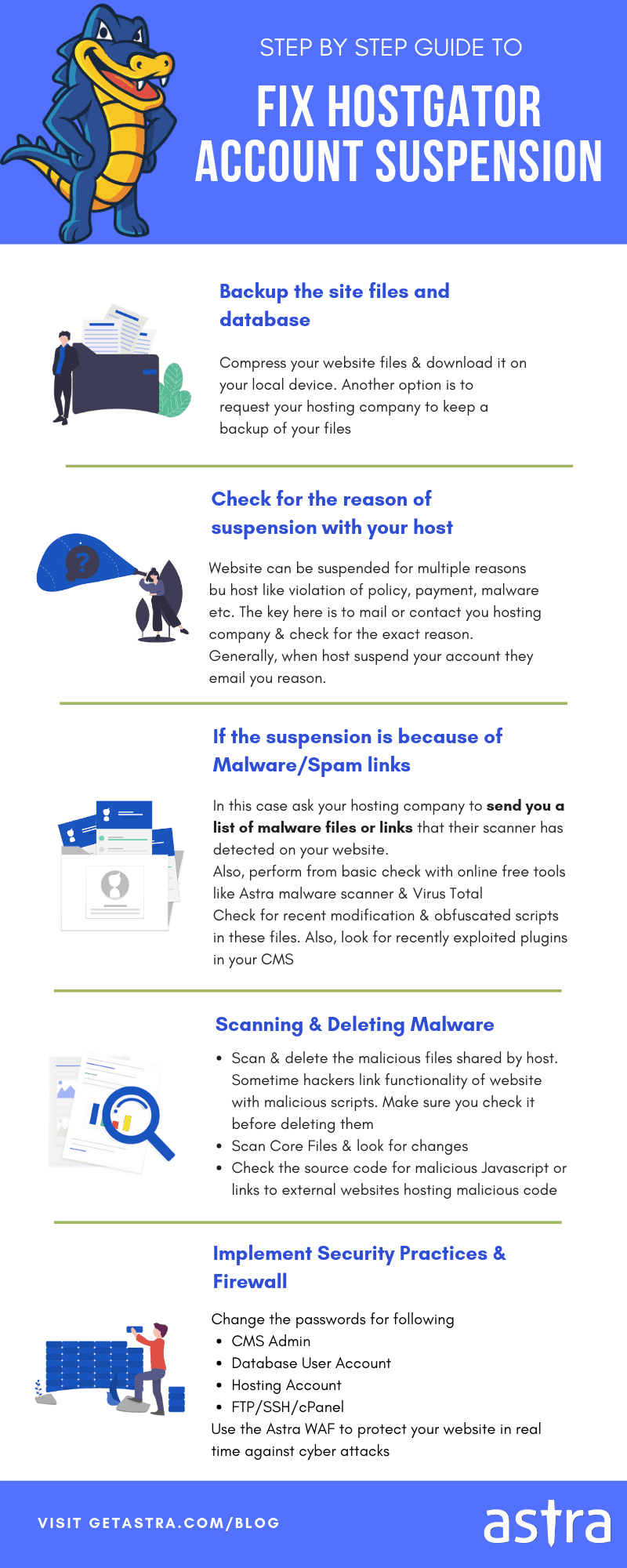
We will discuss this in detail later in the post, but if you’re really short of time the following infographic gives you a rough idea of how you go about the Hostgator malware removal process.
Hostgator Malware Removal: Symptoms of Malware Infection
- Your inbox has “Hostgator account suspended” messages.
- While logging into your Hostgator account it shows messages like “This Account has been Suspended“.
- Hostgator account has been logged in from unknown IPs.
- Index page of your Site hosted on Hostgator has been defaced.
- Unknown pages and files appear on your Hostgator site.
- Site logs show SQL injection or XSS attempts on your Hostgator site.
- Some files of your Hostgator site have been injected with fishy code causing redirects.
- Your Hostgator site has been blacklisted by search engines.
- The database of your Hostgator site shown new admins or suspicious code in the database tables.
- Your Hostgator site has become slow, unresponsive and shows malicious adverts.
- Gibberish content or spam link appear on your Hostgator site.
Hostgator Malware Removal: Causes of Malware Infection
Hostgator SQL Injection
SQLi is one of the most common vulnerabilities caused due to the buggy code of your website’s files. This attack affects the database of your Hostgator site. If you use the Linux hosting then, MySql is likely to be targeted and in case of Windows hosting, MS SQL. However, users with a Windows hosting plan +-*can also use MySql in Hostgator. So, by successfully exploiting an SQL, the attackers can :
- Edit the contents of your MySql/MS SQL database.
- Delete the tables or entire MySql/MS SQL database.
- In some cases, the attacker can also exploit the xp_cmdshell procedure to run commands on your server via SQLi.
Using this reverse shell, the attackers can infect your site which would then need a comprehensive Hostgator malware removal.
Hostgator Cross-Site Scripting
An XSS vulnerability occurs due to lack of input sanitization in the web pages of your Hostgator site. Attackers can use this XSS vulnerability to inject Javascript or HTML into the web pages of your site. Successfully exploiting this, the attackers can:. However, users with a Windows hosting plan +can also use MySql in Hostgator. So, by successfully exploiting an SQL, the attackers can :
- Trick you into clicking links and installing malware secretly using the reflected XSS.
- Steal your cookies for authentication.
- Create Phishing forms to steal credentials from you.
- Conduct CSRF attacks in some cases.
Hostgator Remote Code Execution
An RCE vulnerability can allow the attackers to run arbitrary code on the Hostgator server. This vulnerability also is caused due to buggy coding which allows unsanitized user input. Exploiting this, the attacker can run dangerous functions like eval() on your Hostgator site. Moreover, RCE can be used to silently install malware. The security mechanism of Hostgator might pick this up and suspend your site for malware infection. Hostgator malware removal may become more tricky if the attackers include backdoors via RCE to reinfect the site.
Hostgator Social Engineering Attacks
Did you receive an email or call from a person claiming to be a Hostgator employee and asking for your account details? Such scams are prevalent. Hackers often try to lure you into directly giving away your details or installing some trojan horse. Moreover, the attackers can trick you into clicking links which install the malware in the background without your knowledge which are known as drive-by downloads.
Zero Day Vulnerabilities
While hosting your site on Hostgator, you may use certain software like WordPress, Apache, etc. At times, attackers uncover flaws in popular software before their patches are released. These vulnerabilities are known as zero-day flaws. If this is causing malware infection on your site, Hostgator malware removal may become difficult. So, the best protection against such unseen flaws is a firewall or security solution.
Hostgator Server Misconfigurations
1. Open Ports
It is quite possible that some services running on particular ports of your Hostgator site are vulnerable. If you are using the shared servers of Hostgator, there is not much to worry as the Hostgator firewall blocks most of the ports for security reasons. However, while using the VPS servers of Hostgator, there is no such limitation. You are the ultimate owner of that web space. So, while configuring the server some ports may be left open which can cause trouble. Attackers can use these open ports to install the malware in your site.
2. Weak File Permissions
Your files are crucial for the operation of the site on Hostgator. Therefore, if the permissions are not set properly, the attackers can use those privilege to access sensitive files like .htaccess. The attacker can then modify these files to inject malware in your Hostgator site.
3. Clear Text Passwords and Other Sensitive Information
The server may contain some sensitive info hidden in files like robots.txt. At times, there might be some hard-coded default passwords being used for some services. Moreover, the cleartext passwords may be hidden on your server in the following files:
- License files and other files of software like Apache Tomcat.
- String files for the database connection.
- Scripts to log into the server.
Apart from this, if the directory indexing is enabled, the attackers can browse all these sensitive files easily. This gives the attackers the ability to see the source code of all your web pages and scan them for vulnerabilities. All this info can be used to break into your Hostgator site and install a backdoor. This backdoor can reinfect the site even after a Hostgator malware removal.
Hostgator Malware Removal: Cleanup
The best thing to do after the malware infection is to restore your Hostgator file from backup. However, if you don’t have one, Hostgator can provide you for a certain amount of money. Otherwise, you can start the Hostgator malware removal process by inspecting the file system. Check the source code of sensitive files like index.php, .htaccess, php.ini, etc. In all such files look for some code which is doing something unexpected, the code which is encoded in base64 format and the code with FOPO obfuscation. In case you are not sure about something, just comment it out instead of deleting that part of the code. Alternatively, all the files containing base64 encoding can be uncovered in one go via the following command on SSH:
find . -name “*.php” -exec grep “base64″‘{}’; -print &> code.txt
After this command is executed, all such code will be printed to a code.txt file. From here on, decode this using online services. As far as FOPO code is concerned, it is not easily detectable to average users so consult experts. Hostgator provides you with a great tool known as phpMyAdmin. This tool can also help in Hostgator malware removal. Use this tool to search for malware in the database or even the server files.

Hostgator Malware Removal: Secure Practices
- Delete all the license files and installation of old software from your Hostgator site.
- If you are using the MS Server plan of Hostgator, make sure to set an account lockout threshold to prevent brute force attacks.
- Remove all the hard-coded default passwords and replace them with random and secure ones.
- Update all the underlying software you are using.
- While using the Hostgator VPS, ensure there are no open ports.
- Disable directory indexing by adding the following code to the .htaccess file: Options -Indexes
- Make sure that the web pages have been built using safe coding practices to avoid SQL, XSS, etc attacks.
- Enable two-factor authentication for your Hostgator site by using the cPanel.
- Use SSL for your site by purchasing a certificate from Hostgator or any other Certifying Authority.
- Make sure to keep a backup of the Hostgator site periodically.
When all this is done and the Hostgator malware removal is complete, don’t forget to contact them and get your site restored.
Hostgator Scanner
After Hostgator has suspended your account due to malware, you can ask for a root analysis from them. And if it has found the reason for your site getting hacked, it can reveal it to you against a fee. This way you can know the reason and begin your Hostgator malware removal promptly.
Astra provides robust Hostgator malware scanner for prices as low as $24. Astra does not only scan but also protects your Hostgator site actively using its firewall. It is an out of the box solution and is simple to use and saves you a lot of time and resources.
.


















I read your blog and collect the information. It is very informative information. I suggest you to put more information and share with us. Keep up the good work and keep sharing.
It is really a good technique by that the users are capable to remove any kind of malware or any kind of viruses from their systems.
I have read your information . Your information is very obliging for me but I have a problem so please tell me How can I Identify and Remove malware?
Hi there,
For malware removal follow the below guides
WordPress Malware removal – https://www.getastra.com/blog/911/wordpress-site-hacked-malware-backdoor/
Magento Malware removal – https://www.getastra.com/blog/911/magento-hacked-fixing-magento-vulnerabilities/
PHP website hack removal – https://www.getastra.com/blog/911/php-website-hacked-causes-and-cleanup/
Hacked website repair – https://www.getastra.com/blog/911/hacked-website-repair/
Let me know if you have any specific questions