Twitter has had a forgettable year, ending on a rather embarrassing note for them. The multi-billion dollar organization is already facing a penalty of more than $500k for violating the GDPR in Ireland. And now it is threatened with further penalization and a severe reputational hazard should the stolen personally identifiable information of 400 million users get exposed.
How did this data get stolen? What could be the repercussions of a Twitter data breach? How may the users be affected? We will answer these questions in this post.
Twitter Data Breach 2022 [400 million]
The Current Situation
On December 23, 2022, a threat actor by the name of Ryushi made a post to a hacker forum, Breached, putting 400 million Twitter profiles on sale for $200,000. Ryushi wishes to sell the data from the Twitter data breach(Dec 2022) to an exclusive buyer, ideally Twitter itself. Otherwise, the threat actor intends to sell multiple copies of the data for $60,000 a copy.
Ryushi credits the 2021 API vulnerability for this exploit in fact he communicated with the hacker associated with the earlier exposition of 5.4 million profiles. The threat actor has issued a public warning towards Twitter and Elon Musk saying, “Your best option to avoid paying $276 million USD in GDPR breach fines like Facebook did (due to 533m users being scraped) is to buy this data exclusively.”
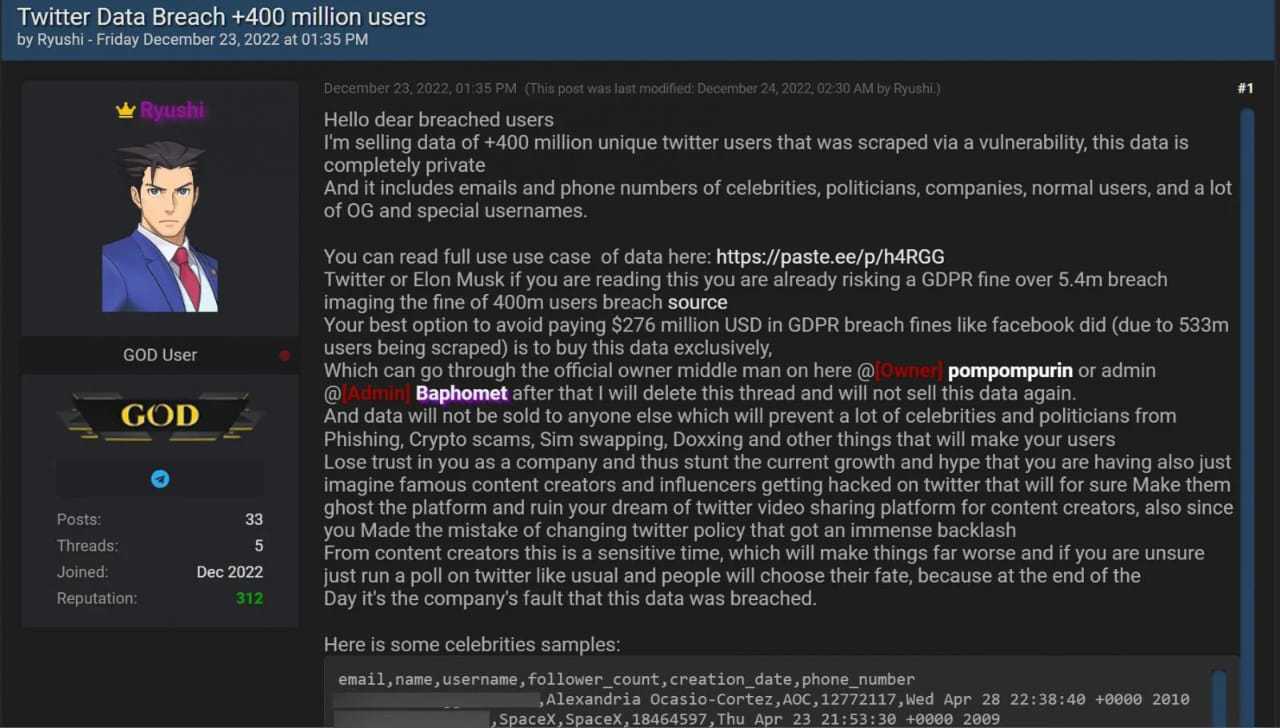
The hacker included thirty-seven sample profiles belonging to public figures like Alexandria Ocasio-Cortez, Donald Trump JR, Mark Cuba, Kevin O’Leary, and Piers Morgan. It was followed by the leak of a larger data pool of 1000 users.
The Vulnerability: When, What, & How
In June ‘21 Twitter made some updates to its code that introduced a critical API vulnerability. In January ‘22 the vulnerability was discovered by a bug bounty hunter and the issue was resolved, according to Twitter, without any ramifications. In July ‘22 some new evidence came to light. It was reported that the personal information of 5.4 million Twitter users was put on sale for $30,000. The stolen data was then bought at a lower price and was likely published.
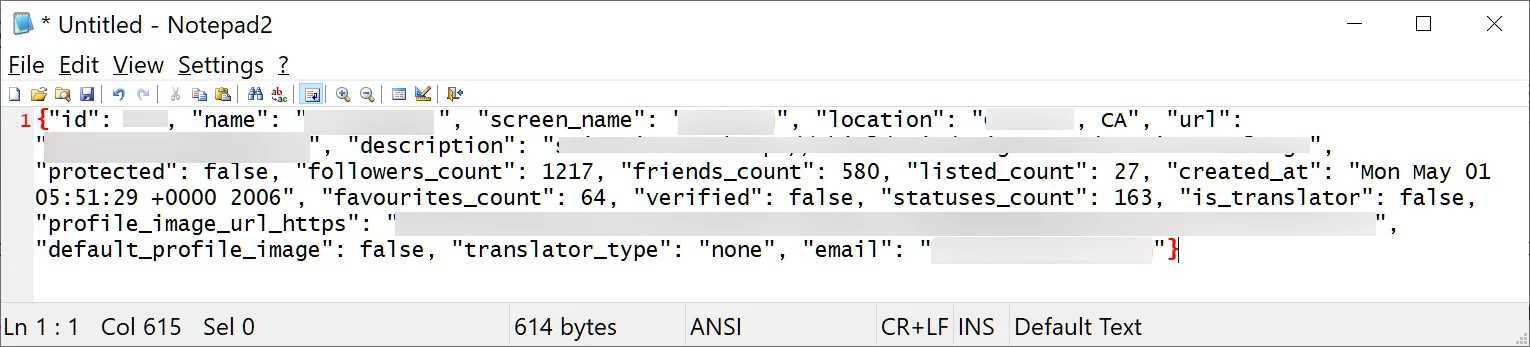
According to the owner of a hacking forum, Breached, the API vulnerability allowed you to call the profile associated with a phone number and email ID. Allegedly, the hackers created complete profiles of 5.4 million Twitter users covering phone numbers, email addresses, login IDs, and public information scraped from the internet.
This is how a user profile looked. The PII has been blurred.
How Can It Affect the Users?
The threat actor has been generous enough to create a list of misdeeds that this data dump can aid. On the wrong hand, this data can be a pretty neat instrument for stealing, tracking, social engineering, and scamming.
For instance, a malicious actor can find the email ID of the employees of a certain IT company and send them phishing emails. Government agencies may use this data to stalk and track certain individuals. Anonymous Twitter users can be exposed.
What Can You Take Away from This?
Data breaches are more common than the reports would suggest. API-based attacks are more popular now than ever. And the fact that no passwords were stolen is hardly any consolation. Twitter has deep pockets and it can survive both the ransomware and the penalties. A lot of small and mid-size businesses may fail to bounce back from something like this.
For Twitter, the chips started falling following a code update that introduced an API vulnerability that eventually wreaked havoc. It re-establishes the fact that you need a vulnerability scan every time you update your code. You need this process to be automated so that you never miss it. Check your APIs, and make sure the input validation protocols are solid. You cannot be cautious enough when it comes to handling personal data.
















