Nearly half of all businesses do not have a vulnerability management program in place to identify and fix security vulnerabilities before they can be exploited. This makes all vulnerable to new bugs at organizations with the risk of data breaches, which occur when an unauthorized individual accesses confidential information.
According to a recent study, 46% of businesses reported experiencing at least one data breach in the past two years. Having a vulnerability management plan in place is essential to protect your business from potential data breaches and the losses that can result from them. This article will discuss top 10 vulnerabilities that are commonly exploited by cybercriminals in 2024.
List of Top 10 Exploited Vulnerabilities
- ZeroLogon (CVE-2020-1472)
- Log4Shell (CVE-2021-44228)
- ICMAD (CVE-2022-22536)
- ProxyLogon (CVE-2021-26855)
- Spring4Shell (CVE-2022-22965)
- Atlassian Confluence RCE (CVE-2022-26134)
- VMware vSphere (CVE-2021-21972)
- Google Chrome Zero-Day (CVE-2022-0609)
- Follina (CVE-2022-30190)
- PetitPotam (CVE-2021-36942)
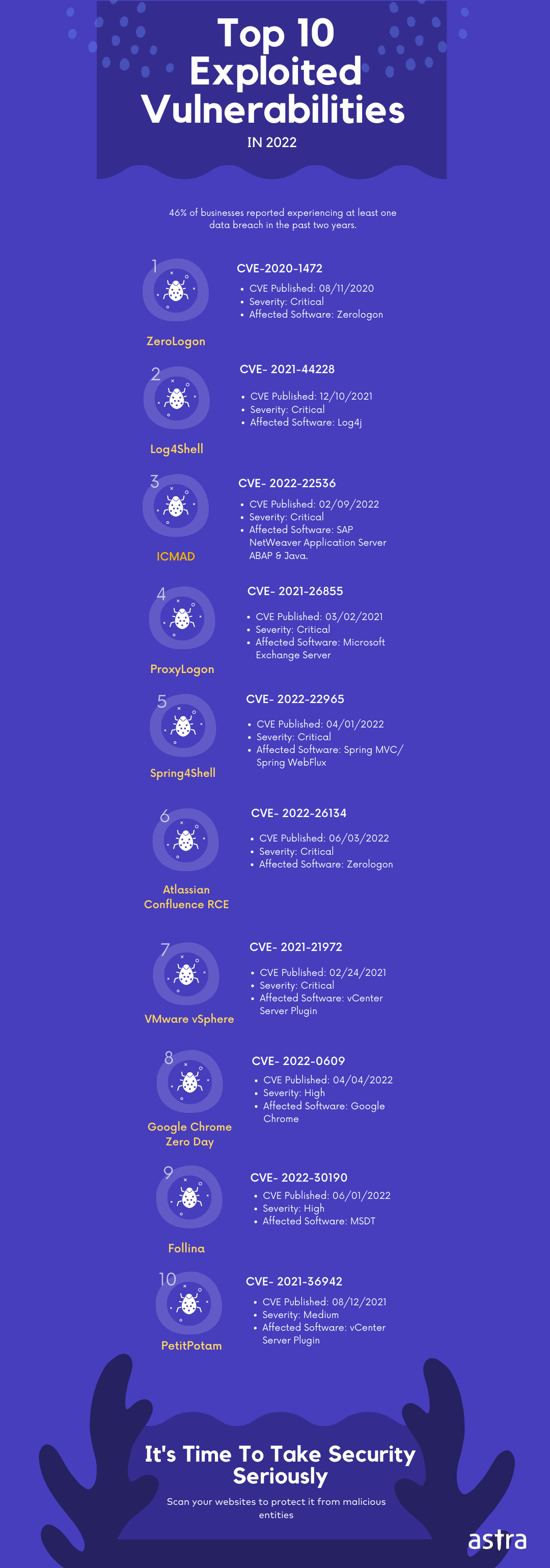
1. CVE-2020-1472 (ZeroLogon)
The MS-NRPC (Netlogon Remote Protocol) protocol of Microsoft Windows has a vulnerability called CVE-2020-1472, found in 2020. Stealing a user’s password hash and using it as authentication enables attackers to carry out “pass-the-hash” attacks, which lets them gain unauthorized access to a network. The potential for a hacker to access a network without the user’s knowledge or assistance is what qualifies this vulnerability as a critical bug impacting millions.
In August 2020, Microsoft issued a patch to address this vulnerability. To stop the exploitation of this vulnerability, it’s critical to apply the necessary patches as soon as you can if you’re using a vulnerable version of Microsoft Windows. The good news is that Microsoft Defender can now identify Zerologon. This vulnerability has a CVSS3 score of 10 out of 10.
- CVE Published: 08/11/2020
- Severity: Critical
- Affected Software: Zerologon
2. CVE-2021-44228 (Log4Shell)
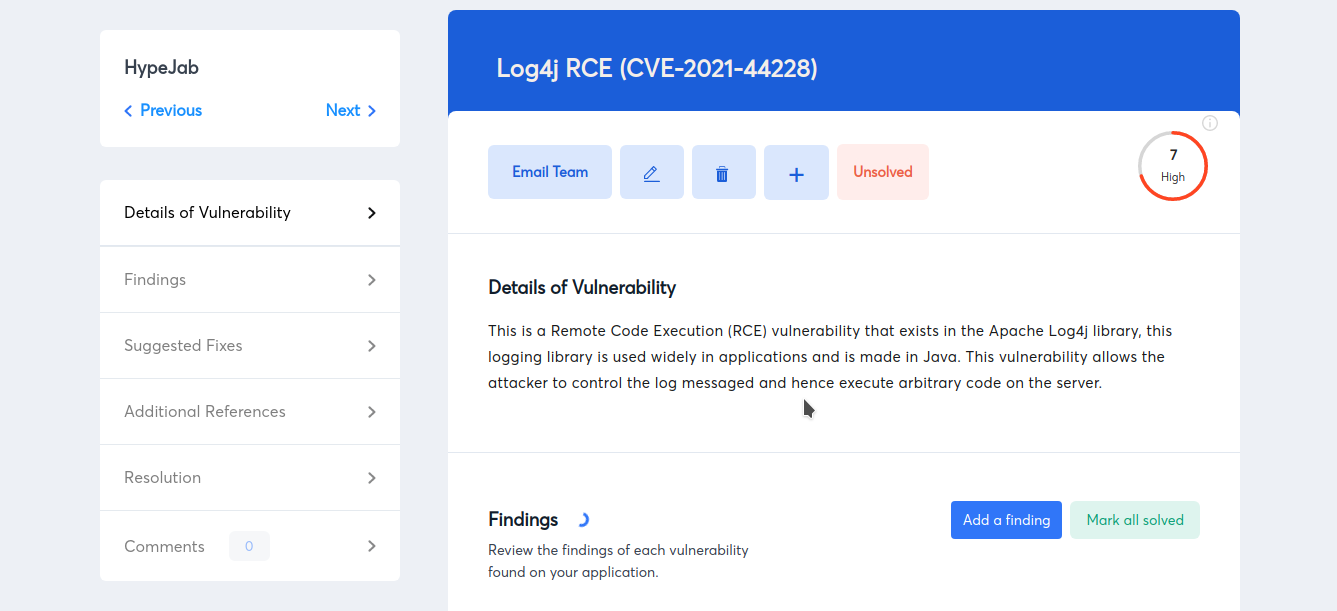
The Apache Log4j 2 library for logging error messages in Java applications contains a vulnerability called Log4shell. If successfully exploited, the vulnerability identified as CVE-2021-44228 could give a remote hacker complete control of a device over the Internet. Hackers can use any entry point that permits data entry from external users to confirm that the vulnerability is present and can be exploited.
These components include input fields, user and password login forms, and HTTP headers like User-Agent, X-Forwarded-For, or other unique headers. More specifically, successful Log4Shell exploration can activate the remote code execution mode, which enables an attacker to download and run a malicious payload on the server. This vulnerability has a CVSS score of 10 out of 10.
- CVE Published: 12/10/2021
- Severity: Critical (As per CVSS 3.x)
- Affected Software: Log4j
3. CVE-2022-22536 (ICMAD)
SAP NetWeaver Application Server ABAP, SAP NetWeaver Application Server Java, ABAP Platform, SAP Content Server 7.53, and SAP Web Dispatcher are vulnerable to smuggling and merge requests. At the victim’s request, an unauthorized attacker can deliver any data. This allows an attacker to pose as a victim or compromise an intermediary web cache. System confidentiality, integrity, and availability could all be lost entirely in the event of a successful attack. This vulnerability has a CVSS3 score of 10 out of 10.
- CVE Published: 02/09/2022
- Severity: Critical (As per CVSS 3.x)
- Affected Software: SAP NetWeaver Application Server ABAP & Java, ABAP Platform, SAP Content Server 7.53, and SAP Web Dispatcher
4. CVE-2021-26855 (ProxyLogon)
Next on any hackers list of vulnerabilities is CVE-2021-26855 discovered in Microsoft Exchange in 2021. This enables an attacker to run code remotely on a weak server, potentially gaining access to the system without authorization. Microsoft released a fix soon after the vulnerability was identified in March 2021. If you are using a vulnerable version of Microsoft Exchange Server, it is vital to ensure that you have applied the appropriate patches to protect against this vulnerability.
Hackers can easily take advantage of this vulnerability in Microsoft Exchange Server by accessing port 433 on the server without any action required from the user. This allows them to move around the server, maintain access to it, and control it remotely. This vulnerability has a CVSS3 score of 9.8 out of 10.
- CVE Published: 03/02/2021
- Severity: Critical (As per CVSS 3.x)
- Affected Software: Microsoft Exchange Server
5. CVE-2022-22965 (Spring4Shell)
Applications using Spring MVC or Spring WebFlux and running on JDK 9+ could be exposed to remote code execution (RCE) through data binding. Some exploits require the application to be deployed as a WAR and run on Tomcat.
Application deployment as a Spring Boot executable JAR, which is H by default, does not make the application vulnerable. The vulnerability’s scope is much broader, though, and there might be additional ways to take advantage of it. This vulnerability has a CVSS3 score of 9.8 out of 10.
- CVE Published: 04/01/2022
- Severity: Critical (As per CVSS 3.x)
- Affected Software: Spring MVC or Spring WebFlux
6. CVE-2022-26134 (Atlassian Confluence RCE)
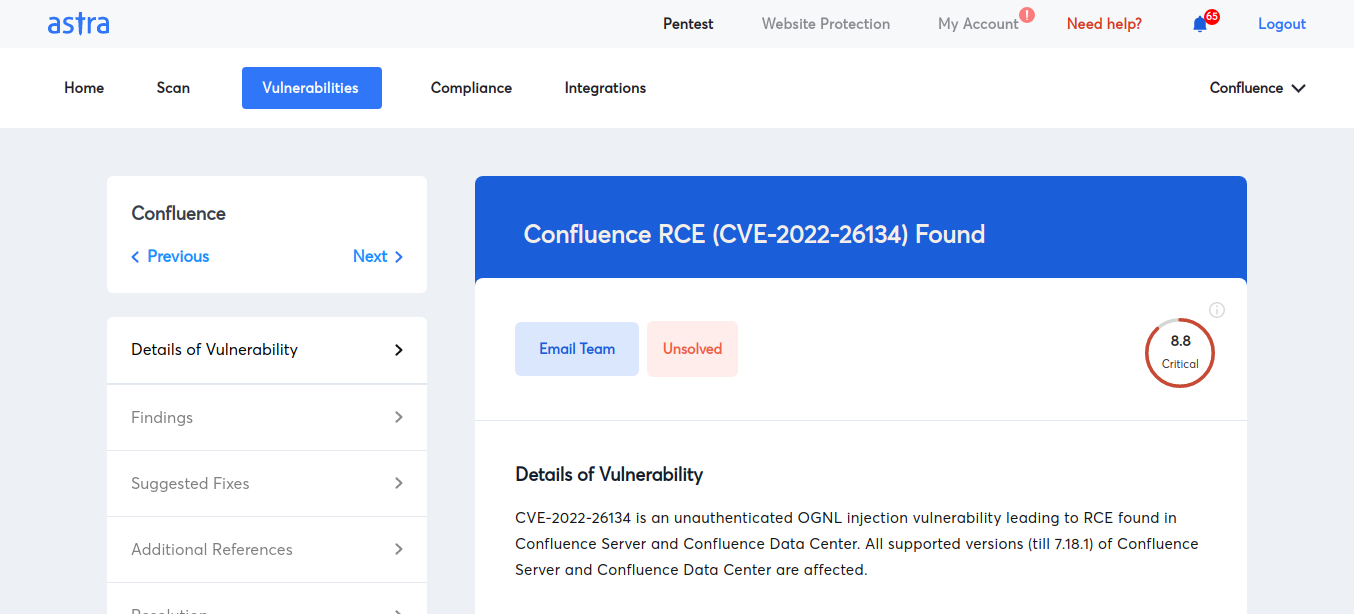
Atlassian Confluence Server and Datacenter versions 1.3.0 to 7.4.17, 7.13.0 to 7.13.7, 7.14.0 to 7.14.3, 7.15.0 to 7.15.2, 7.16.0 to 7.16.4, 7.17.0 to 7.17.4, and 7.18.0 to 7.18.1 contain a vulnerability known as an “OGNL injection” that could allow an unauthorized attacker to execute arbitrary code on the Confluence Server or Datacenter instance.
One of the top vulnerabilities, it can be exploited by sending malicious requests to the server, allowing the attacker to run any code they choose on the system. If this vulnerability exists in Atlassian Confluence, it could allow a hacker to gain unauthorized access to the system and execute the code of their choice. This vulnerability has a CVSS3 score of 9.8 out of 10.
- CVE Published: 06/03/2022
- Severity: Critical (As per CVSS 3.x)
- Affected Software: Atlassian Confluence Server
7. CVE-2021-21972 (VMware vSphere)
The vSphere Client (HTML5) in the vCenter Server plug-in has a vulnerability that allows for remote code execution. This vulnerability affects the vCenter Server for VMware versions 7.x before 7.0 U1c, 6.7 before 6.7 U3l, and 6.5 before 6.5 U3n, as well as VMware Cloud Foundation versions 4.x before 4.2 and 3.x before 3.10.1.2.
An insider threat or someone with access to port 443 on the network could exploit this vulnerability to gain root privileges and execute commands on the operating system that powers the vCenter server. This could potentially allow the attacker to use the vCenter server as a starting point to access the entire infrastructure. This vulnerability has a CVSS3 score of 9.8 out of 10.
- CVE Published: 02/24/2021
- Severity: Critical (As per CVSS 3.x)
- Affected Software: vCenter Server plugin
8. CVE-2022-0609 (Google Chrome Zero-Day)
Google’s threat analysis team has reported that a zero-day vulnerability in Chrome (CVE-2022-0609) is currently being actively exploited. This vulnerability, which affects all Chrome users regardless of their operating system, is located in the Chrome animations component and is a type of flaw called a “use-after-free” vulnerability.
A use-after-free (UAF) vulnerability that happens after the memory is freed, according to MITRE, can lead to a program using unexpected values, corrupting valid data, crashing, or executing code. A fix for the vulnerability was released in a later version of Chrome, but many users were exposed to the risk of exploitation until they updated their browsers. This vulnerability has a CVSS3 score of 8.8 out of 10.
- CVE Published: 04/04/2022
- Severity: High (As per CVSS 3.x)
- Affected Software: Google Chrome
9. CVE-2022-30190 (Follina)
One of many actively exploited Microsoft vulnerabilities in 2022 is CVE-2022-30190, also known as Follina. The Microsoft Support Diagnostics Tool (MSDT) is susceptible to the remote code execution (RCE) flaw known as Follin.
Hackers can use malicious Word documents to take advantage of the Follin vulnerability. The MSDT executable in this document is run using the Microsoft URL handler. This executable can run PowerShell commands, giving attackers access to the target system and enabling code execution. This vulnerability has a CVSS3 score of 7.8 out of 10.
- CVE Published: 06/01/2022
- Severity: High (As per CVSS 3.x)
- Affected Software: MSDT
10. CVE-2021-36942 (PetitPotam)
PetitPotam is a type of malware that exploits a vulnerability in the New Technology LAN Manager (NTLM) and the Windows Local Security Authority (LSA) to deceive a domain controller into authenticating to another server.
This vulnerability allows PetitPotam to use the Microsoft Encrypting File System Remote Protocol (MS-EFSRPC) to authenticate to another host using LSARPC on TCP port 445, which enables it to perform nearly any operation in a Windows domain. This includes distributing ransomware, creating malicious group policies, and more. This vulnerability has a CVSS3 score of 5.3 out of 10.
- CVE Published: 08/12/2021
- Severity: Medium (As per CVSS 3.x)
- Affected Software: vCenter Server plugin
Conclusion
It’s important to remember that vulnerabilities can often be exploited soon after they are discovered. Hence, it’s important to apply patches and security updates as soon as they become available to protect against potential exploitation.
To keep your business secure, it’s crucial to identify and fix potential vulnerabilities by regularly performing penetration testing. It’s also important to stay aware of the latest threats and take steps to protect yourself, as new vulnerabilities are constantly being discovered and exploited.
![Top 10 Exploited Vulnerabilities in 2024 [Updated]](https://cdn-blog.getastra.com/2022/12/Featured-Images-1.png)















