There is an inevitable element of risk in any enterprise. There is no way of avoiding it completely in the path of growth. What one needs is a way of understanding risk. You need to learn what the risk is, then identify the assets that might be exposed to it, carefully looking at and quantifying the risk, and finally allocating resources to mitigate it where it’s needed. In fact, sometimes you have to identify risk and leave it be without even attempting to control or remove it.
In this post, we will step into the risk assessment vs vulnerability assessment debate in the context of cyber security. We will learn a bit about risk management with our main focus on risk assessment and then we will discuss vulnerability assessment and risk assessment in complementary roles. The goal is to address any confusion you may have about the placement of the two processes under consideration in the larger scheme of things.
What Is Risk Assessment?
Risk assessment, in the context of information security, is the process of identifying, estimating, and prioritizing the risk to organizations, business processes, information assets, and individuals from certain uncertainties pertaining to the usage of information systems. It constitutes a major part of organizational risk management.
An organization usually has yearly or by-yearly risk assessment drives where they identify important assets that might be exposed to risk, list down the threats that might have an impact, determine the probability of certain threats materializing, and quantify the impact of such materialization, financial, reputational, or otherwise.
What are the different components of risk assessment?
A good risk assessment takes every asset belonging to an organization into account, determines its true value, and considers every probable risk factor with a potential impact. The end goal is to quantify the risks in order to prioritize as well as strategize the mitigation efforts. There are four components of a risk assessment.
Asset identification: This involves creating an inventory of all the network assets as well as physical assets of the organization under assessment. You also assign values to the assets based not only on the cost of the asset but also on the cost of a breach or the cost of fixing it.
Risk analysis: This is a little different from the risk analysis we conduct in the context of vulnerability assessment (we will discuss that too later in the article). Here, you identify all the risk factors that might impact your business and then qualify and quantify them based on the likelihood of their materialization, the frequency of it occurring, and the financial or reputational impact they may have upon the organization.
Risk evaluation: As we have stated earlier, no business can operate risk-free. Based on the industry, every organization sets an acceptable level of risk that it can tolerate. Risk evaluation is the process of mapping the results of the risk analysis against the risk tolerance criteria set by an organization for itself or by a governing body that regulates the risk acceptance policies for an entire vertical.
Cost assessment and resource allocation: Once you have a complete profile of risks to your business, you need to strategize the mitigation efforts. Mitigating risk can be expensive at times, and your budget might sometimes fail you. Once again, you will need to go back to the risk analysis matrix and figure out which risks you can tolerate, and which ones can potentially destroy your business.
The Risk Matrix and how it works
Each risk is evaluated based on two principal attributes – likelihood, and impact. The risk matrix helps you categorize the risks to your business by mapping them based on categories of likelihood and impact.
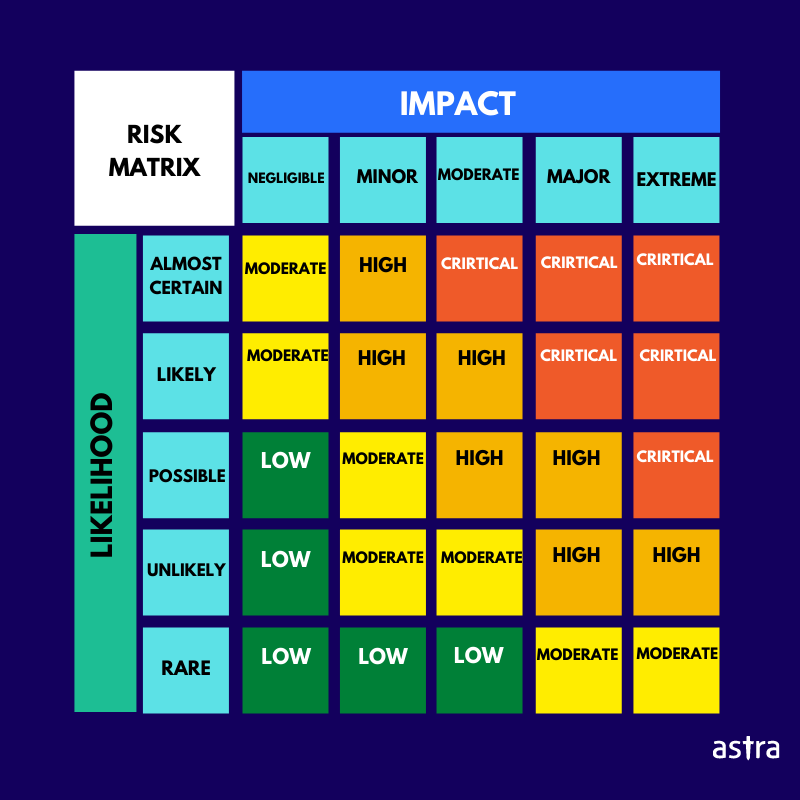
If you look at the image above, you will see a green box in the bottom-left corner with LOW written on it. It should contain the number of risks that are not only rare but also have a negligible impact on the business, hence they should attract low priority. Now, if you look at the red box in the top-right corner, that’s where the most critical as well as most probable risks lie. Those are the ones you should be most worried about. You can easily understand the rest of the matrix.
Why does a business need a periodic risk assessment?
As a business grows in complexity it incurs new forms of risks. Suppose you introduce a payment window into your web app, you will need to assess the risk it comes with from price manipulation attacks, or credit card hacks. Similarly, if you are running a high-performing marketing website, you must always take care of the risk of clickjacking attacks or SEO spam.
The risk landscape changes with your business goals, and a risk assessment plays a vital role in decision making.
What Is a Vulnerability Assessment?
A vulnerability assessment is a process of identifying and categorizing security vulnerabilities existing in your systems. It usually involves an automated tool that scans your assets for common vulnerabilities by referencing a vulnerability database. At the end of the scan, it creates a report where the vulnerabilities are listed, categorized by their severity. The vulnerability assessment report also includes suggestions for fixing the vulnerabilities.
Read also: Vulnerability Assessment: A Detailed Overview – Astra Security
What are the steps of a vulnerability assessment?
Before we talk about the steps of vulnerability assessment, let’s just clarify one thing – vulnerability scanning and vulnerability assessment are not the same. Vulnerability scanning is a quintessential part of the vulnerability assessment process. Anyway, let’s get back to the original discussion.
Asset discovery: The first step of the vulnerability assessment process is to identify all the network as well as physical assets that are to be assessed. With the increment of IoT devices, mobile applications, remote access to the company network, asset discovery is not as simple as it sounds. There is always a chance of missing out on a crucial piece.
Prioritization: Once you have found all the assets, it is important to narrow the focus down to the most important ones. If you are working with limited resources, this becomes a crucial step. Usually, the internet-facing assets and the customer-facing applications are prioritized for scanning.
Vulnerability scan: In this step, an automated vulnerability scanner is used to discover vulnerabilities across the systems. The scanner detects the security vulnerabilities, categorizes them according to their CVSS scores into low, medium, high, and critical severity vulnerabilities. It also recommends ways of fixing the issues.
Risk assessment and remediation: There is an element of risk assessment in the vulnerability assessment process as we mentioned earlier. The location, potential impact, and severity of a certain vulnerability prompt a risk score which in turn helps you decide whether to prioritize that particular vulnerability.
Once you pick the vulnerabilities for remediation, the developers can follow the recommendations of the scanner and fix the issues.
Rescan: A rescan is required to ensure that the vulnerabilities were taken care of.
Continuous scanning: New vulnerabilities appear every now and then even if you do not make any modifications to your software. Hence continuous scanning is a necessity to ensure the safety of your assets.
How Is a Vulnerability Different from a Risk?
Risk is a broad term that covers a wide range of business-related aspects. On one hand, it includes cyber threats, on the other hand, it covers natural disasters and pandemics. Cyber risk management constitutes a significant part of the overall risk management horizon, and vulnerability management is a part of the former.
A vulnerability is a mistake or a bug that may expose certain assets to attacks. A weak password is an example of a vulnerability, so is an encryption error, and an outdated firewall.
Risk refers to the exposition of an asset to harm, loss, or destruction. A vulnerability that provenly exists in a system and can cause loss or damage to assets or data, creates a risk. In theory, a risk is the product of a threat and a vulnerability.
Risk Assessment vs Vulnerability Assessment – The Resolution
Once again, we use phrases like risk assessment vs vulnerability assessment without hinting at any form of animosity between the two. Vulnerability assessment is a significant part of risk assessment. Security vulnerabilities constitute a vital segment of a company’s risk profile, and vulnerability assessment is a key method of identifying, categorizing, and prioritizing vulnerabilities. Vulnerability assessment is a complementary process to risk assessment and they are to be used in tandem.
How to pick a vulnerability assessment tool?
Vulnerability assessment is supposed to be a regular process to keep an eye out for any inconsistencies or anomalies in your web security. With the right tool, the process becomes easy and hassle-free. Here are some questions you should ask before choosing a vulnerability assessment tool.
- Does it come with a powerful scanner that covers all CVEs listed in OWASP top 10, SANS 25, and other popular vulnerability indexes?
- Does it have a continuous scanning feature for software updates?
- Can you integrate the scanner with your CI/CD?
- Does it produce a comprehensive report?
- Does it have positive user reviews and a significant client base?
- Does it help you with compliance reporting?
If you get affirmative answers to these questions about a certain tool, you can safely go ahead with it.
Astra’s Pentest for vulnerability assessment
Astra’s Pentest suite provides the users with an interactive dashboard that they can use for monitoring the vulnerabilities as they are found. In the same dashboard, a user can see the risk score assigned to each vulnerability which takes the CVSS score and the potential loss caused by the vulnerability into account. The dashboard also shows you a definitive figure of potential damages through the exploitation of a vulnerability.

Following features make Astra’s Pentest an unbeatable choice if you are conducting vulnerability assessments as a part of risk management. These aside, Astra’s Pentest comes with a host of features that are quite unique in its price range.
- 8000+ tests including all tests required for compliance with ISO 27001, SOC2, GDPR, and HIPAA
- Continuous scanning by virtue of CI/CD integration.
- Integration with Slack and Jira
- Detailed vulnerability scanning report with video POCs for remediation
- Zero false positives ensured by manual pentesters
You can discuss your security requirements with experts at Astra, and come out with the perfect plan for vulnerability assessment.
Conclusion
Hopefully, by now, you have found a resolution to the risk assessment vs vulnerability assessment debate. Both of the processes play a significant role in maintaining and improving security as well as business functionality. Cyber risk management is an extremely important undertaking in the context of today’s cyber threat landscape, and vulnerability assessment plays a pivotal role in its execution.
FAQs
1. What is a vulnerability assessment?
Vulnerability assessment is the process of detecting, categorizing, and prioritizing security vulnerabilities in a system.
2. How much does a vulnerability assessment cost?
The cost of vulnerability assessment is between $99 and $399 per month for web applications.
3. Is vulnerability scanning necessary for compliance with PCI-DSS?
Yes, vulnerability scanning is a requirement for PCI-DSS compliance.
4. Do we get free rescans after vulnerabilities are fixed?
Yes, you can avail free rescans after the vulnerabilities are fixed.
















