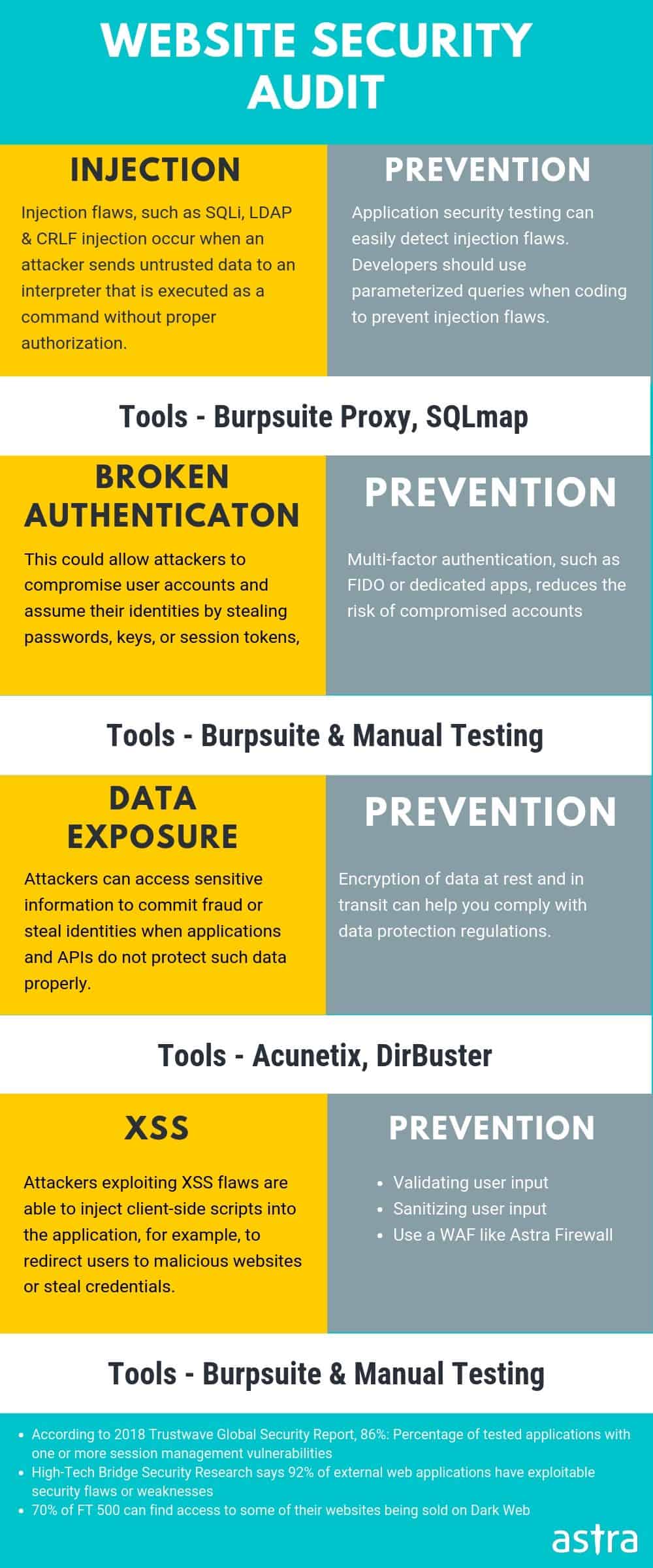
E-commerce has gained momentum within these last few years. As a result, multiple online platforms like Magento, Opencart, and Prestashop have sprung up. Prestashop has been gaining popularity globally, thanks to its open source nature. However, like any online store, the utmost priority for the customers is the Prestashop security. Multiple Prestashop security issues have been uncovered in recent years. According to the book PrestaShop Module Development,
Prestashop Security: Common Hacks in Prestashop
While setting up Prestashop is easy, much caution is needed to keep it secure. Online stores usually manage sensitive info like credit card details and there is a huge responsibility for businesses to deal with such sensitive data securely. Attackers are at play constantly to steal this data and sell on the dark web for dirt cheap prices. In order to keep Prestashop store secure, let’s take a look at the ways Prestashop security can be exploited.
SQL Injection in Prestashop
An SQLi vulnerability was exposed in Prestashop. This occurred due to the lack of input sanitization in one of its module. The module vulnerable was Responsive Mega Menu (Horizontal+Vertical+Dropdown). An SQLi could be injected through function calls in the code parameter. This was dubbed as CVE-2018-8824. Before this, the componentid_manifacturer was found prone to SQLi. Through the URLhttp://example.com/ajax/getSimilarManufacturer.php?id_manufacturer=3[SQL-injection]. This component was vulnerable to blind SQLi. By using SQLi, the attacker can:
- Read contents from the database.
- Find out the user login details and then log in as admin.
- Steal user credit card info in case it was stored locally.
- Conduct other attacks from the sensitive info gained from the database.
Cross-site Scripting in Prestashop
Multiple XSS flaws have been found in Prestashop this year. One vulnerability discovered at the beginning of the year was dubbed as CVE-2018-5681. However, it required the attacker to log in to the system first, in order to exploit it. The other more severe XSS vulnerability was in the Contact Form module. It was more severe as it was Persistent in nature. This vulnerability allowed to bypass theisCleanHtml() function. It could be bypassed using base64 encoding. Moreover, this can be used to inject HTML codes. Thus editing the display of messages.
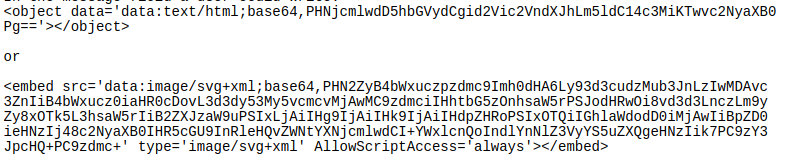
All the input provided in the image is in base64 format. Both, when decoded, would be<script>alert()</script>. Thus all the messages sent using Contact Form will be visible to the admin after logging in. So, using this, an attacker can:
- Firstly inject the malicious code in the messages.
- Load admin cookie stealing scripts from a malicious domain.
- After getting the cookie, the attacker can log in as admin.
- This opens the site to all kinds of further attacks.
- Moreover, the attacker can hook the admin’s browser and launch browser exploits.
Remote Code Execution in Prestashop
Prestashop suffered from an RCE vulnerability this year. The module responsible for it was Responsive Mega Menu Pro. The complete URL ishttp:///modules/bamegamenu/ajax_phpcode.php?code=echo exec(id);. Dubbed as CVE-2018-8823, this issue allowed attackers to run PHP code arbitrarily on the server. Using this the attacker could have:
- Run PHP commands on the server.
- Read/modify sensitive files.
- Tried to escalate privileges. After that, the attacker can now execute commands as an admin. Thus completing the system takeover!
Privilege Escalation in Prestashop
Prestashop suffered from a Privilege escalation issue which was dubbed as CVE-2018-13784. This issue was due to the mishandling of the cookie encryption. Prestashop used Blowfish/ECD or AES encryption which was vulnerable to padding attacks. An attacker could alter the contents of cookie to gain admin privileges. Thus, accessing the resources not intended for the attacker. Exploiting this the attacker can:
- Get hold of any customer session.
- Steal sensitive info such as customer information, orders, credit card info etc.
- Obtain access to the admin dashboard through CSRF or other attacks. Also, this can lead to remote code execution.
Prestashop Redirect Hack
Often malicious actors try to inject malicious redirect javascript code. Therefore, when the customers visit the site it typically redirects them to adult sites. Although at times it could be other sites selling products. Or maybe even harvesting clicks for the attacker. Especially the small stores are worst affected. Thus, a Prestashop redirect hack can:
- Result in the store getting blacklisted by search engines.
- Redirect up to 90 percent of user traffic.
- Loss of user trust in the store.
- The decrease in sales due to redirect malware.
- Turns your Prestashop store into a spam garage.
Related Guide – PrestaShop Hack and Malware Removal Guide
Admin Hack in Prestashop
Often Prestashop dashboard is hacked due to lapses in Prestashop security. The admin panel is one of the most sensitive areas of the store. It must be kept hidden from public access and with a safe password. However, when compromised it could lead to:
- Creating multiple new admin accounts previously unknown.
- Changes the user interface of the admin dashboard.
- Security plugins getting disabled paving way for more attacks.
- Hosting provider suspends the account for abuse.
- Admin area shows a blank page or file listing.
Weak Prestashop security can give away the admin dashboard to attackers. Sometimes the attacker might use backdoors for gaining persistence to the admin account. Therefore when it comes to Prestashop security, the admin dashboard is the most crucial resource. Hence the site admins must secure it following security practices.
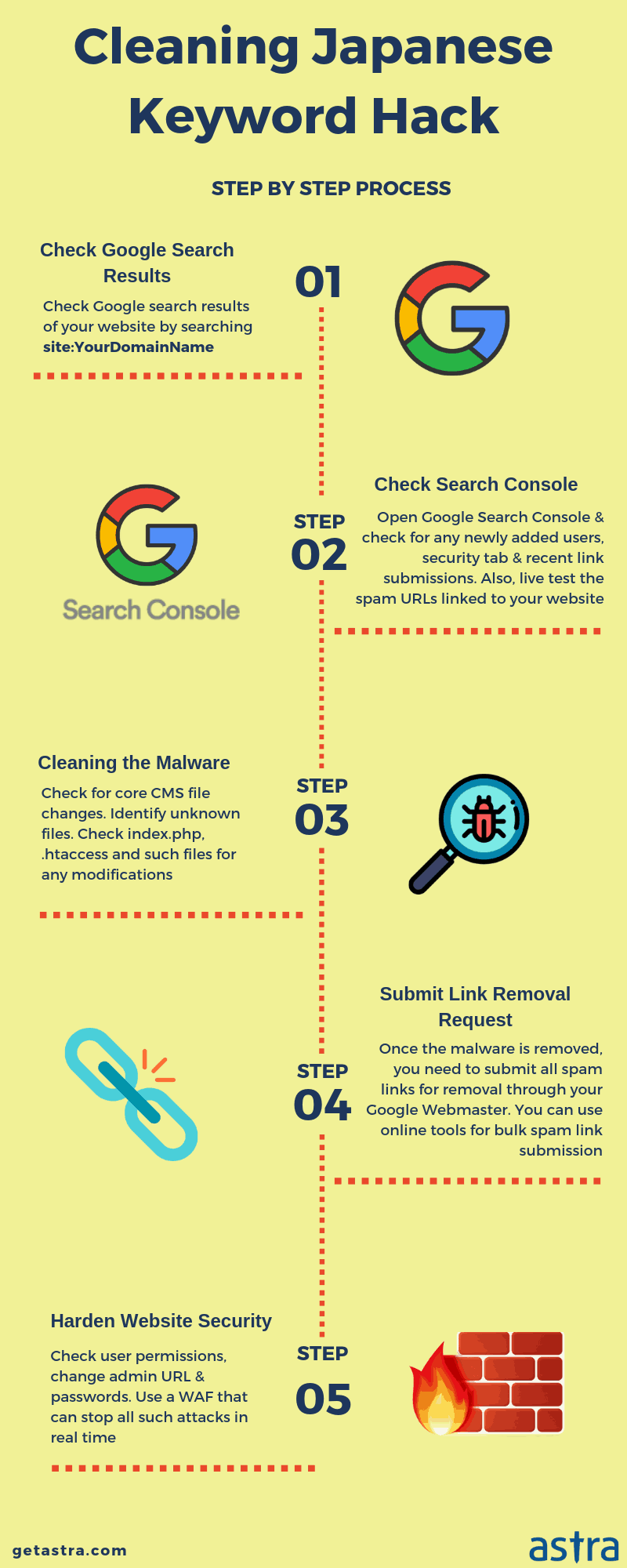
Google Keyword Hack in Prestashop
Sometimes the store may show pages or sell products it was originally not intended too. This is most likely the case of a spam injection. The attackers compromise the store and create fake pages. These pages may show adult products or contain content in some other language. When search engines like Google crawl the website for indexing, these pages get listed. Therefore affecting the search results of the site.
So when users search for a site on the internet, it shows and redirects them to the spam pages. However, search engines have malware filters. As a result, the store may get Blacklisted for spam content or malware. This warns the users each time they proceed on the site. Thus user traffic plunges and the sales drop to almost nil. Some of the typical infections of this kind are the Viagra Cialis hack and the infamous Japanese Keyword Hack. It has also been observed that attackers use cloaking to avoid detection. Therefore spam detection is a meticulous process and requires code inspection!
Credit card Hack in Prestashop
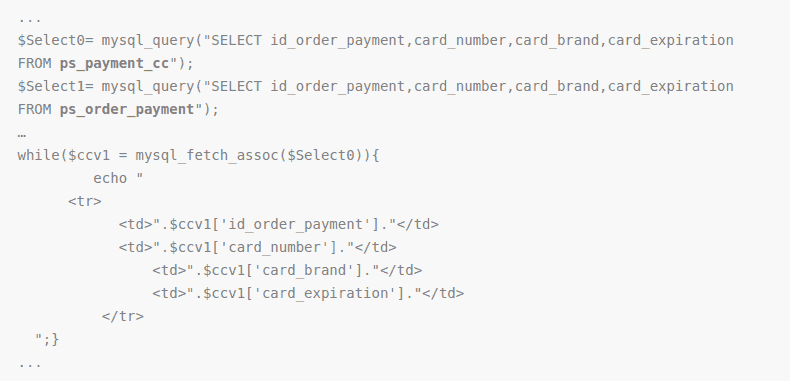
Sensitive transactions occur on the store every day. Some vendors opt to store the user credit card info while others don’t. Therefore the database becomes a ripe target for the attackers. Various credit card stealing malware and scripts are detected in the wild every day. Some scripts make a connection to the database to steal credit card info. The tableps_payment_cc contains sensitive columns likeid_order_payment,card_number,card_brand,card_expiration. The source code of one such script is given below.
As evident from the code, the script uses SQL queries. These queries extract credit card info from the database. Another well-known malware infection is the/vendor/composer/autoload_real.php file. However, malware and scripts are not used always. Sometimes the attacker tricks users into phishing attacks. Therefore the users should keep an eye on the suspecting pages!
To learn more about Credit Card Hijack in Prestashop, check our detailed blog.
Other Attacks
At times it is possible that the core Prestashop installation is secure but the server configurations are wrong. For instance,
Weak Credentials
Brute force attacks are quite common in the Prestashop stores. The prime aim of such attacks is to reveal default or weak credentials.
Open Ports
While installing and configuring the server, some ports may have been left open. These are an open invitation to hackers. Some search engines like shodan crawl the internet for such misconfigurations. Attackers can infect the store from these open ports. Therefore it is advised to block or filter ports.
DNS Misconfiguration
At times, the DNS servers may enable zone transfers. Or often some sub-domains may be unused. Attackers are constantly on the prowl for such vulnerabilities.
Outdated Modules
While getting a new module always ensure that it has a good community rating. Poorly coded modules can add backdoors to the store. Also, use reputed modules only. Moreover, if the installation is outdated, it is highly prone to attacks as exploits are publicly available.
Prestashop Security breached? Drop us a message on the chat widget and we’d be happy to assist you with your Prestashop website. Secure your Prestashop website now.
How to Secure my PrestaShop store?
There are certain methods to avoid the Prestashop store from getting hacked. These practices are easy and efficient. Though, the possibility of an attack on the Prestashop store cannot be totally averted. Yet it can be delayed by adopting certain mechanisms. Some of them are:
Prestashop Security: Use of SSL
Enabling SSL gives a significant boost to the Prestashop security. It is a standard protocol for ensuring that the communications between Prestashop store and the users are safe. SSL works using the elliptical curve cryptography where two unique key pairs are generated. This can help prevent man-in-the-middle attacks on Prestashop store. To boost the Prestashop security, admins can buy an SSL certificate and enable SSL on the Prestashop installation.
Prestashop Security: Strong Credentials
Ensure that the admin dashboard password is a secure one. Avoid using default or hard-coded credentials. Also, some common passwords like admin, password, qwerty etc should never be used. Moreover, keep separate passwords for FTP, cPanel, Dashboard etc. It is of the utmost importance for Prestashop security that a password should be very strong.
Prestashop Security: Hide core files with .htaccess
Ensure that no core files of Prestashop store are publically visible. Also, ban spam IPs. All this could be accomplished using the .htaccess file. Moreover, this file could help to force the use of HTTPS and prevent some of the script injection attacks. To hide core files, add the following code to your .htaccess file:
RewriteEngine on
RewriteCond %{REQUEST_FILENAME} !-d
RewriteCond %{REQUEST_FILENAME}.php -f
RewriteRule ^(.*)$ $1.php
# Return 404 if original request is .php
RewriteCond %{THE_REQUEST} "^[^ ]* .*?\.php[? ].*$"
RewriteRule .* - [L,R=404]If there is a difficulty in editing the file, consult an expert!
Prestashop Security: Set Preferences
The preferences settings on the dashboard can add more to the PrestaShop security. Cookies can help in managing users. Using a cookie makes it easy to track users and identify original users from fake ones. Cookies could also help detect fake logins. If the cookie mismatches with the IP it was issued to, it is likely to be an attacker. However, often times the IP changes dynamically, which should also be kept in mind.
Cookies can be enabled from the Preferences options. Or can be installed via a module. There are scores of free as well as paid PrestaShop GDPR and cookie bar modules that you can use here.
Furthermore, there is another Prestashop security feature called Increase Front Office security. It can be found in the option Preferences > General. This feature ensures that a unique session URL is assigned to each user. Thereby stopping privilege escalation attacks.
Change default admin URL
Everybody, including the hacker, knows the path to your store’s backend if you leave it unchanged to the original /en. Not changing your admin URL opens up the pandora’s box for you and your store becomes vulnerable to – Brute-force, code-execution, security bypass, and whatnot!
Hence, it is always safer to change your default URL. This would render your store’s backend inaccessible to anyone other than you.
Secure PrestaShop File/Folder Permission
PrestaShop files and folders need to be protected from arbitrary accessibility. The easiest way you can do this is by setting correct file and directory permissions to your store’s files. The recommended permission for PrestaShop store files is 644 and the same for folders is – 755.
To learn how to implement these files and folder permission on an actual PrestaShop store, follow our extensive guide on how to set PrestaShop file/folder permissions.
Prestashop Security: Install Prestashop Security Modules
There are certain plugins which can help in improving Prestashop security. These plugins can:
- Protects the store from known attacks.
- Lock access to the front office. Allowing only authorized users.
- Create unique keys for every purchase.
- Check if the orders were placed by bots.
- Added captcha for blocking bots.
- Block bad bots and Spam IPs.
Some effective PrestsShop security modules that can add to your website’s security are – re Captcha – Anti Spam – recaptcha – anti fake accounts Module, Official GDPR Compliance by PrestaShop (1.5 & 1.6) Module, Store fixer by Astra, Astra Firewall and Malware Scanner and so on.
Prestashop Security: Updates and Backup
Keeping the installation updated is the cheapest way to improve Prestashop security. Therefore, update to the latest stable version of Prestashop. Moreover, updates contain new Prestashop security improvements which can be verified from the changelogs. Also, ensure that your installation has a backup. The backup helps to restore files in case of a malware infection.
Prestashop Security: Prestashop Firewall and Antivirus
Investing in a good firewall comes a long way in securing your Prestashop store. It beefs up Prestashop security and blocks hackers. Firewalls monitor all the HTTP traffic going to a Prestashop store. Hence, any intrusion attempt towards the Prestashop security is easily dealt with. Moreover, the antivirus scans for any infected Prestashop installation files. The antivirus also scans for backdoors inside the Prestashop files. The days of using a physical firewall are obsolete. Hence, many businesses small or large, use firewall software. Out of the multiple solutions in the market today, Astra offers a complete package. Its firewall is economically viable and scalable for small businesses too. Get a demo now!
Prestashop Security: Prestashop Security Audit
As seen in the article, there are multiple ways to attacks your Prestashop store. More and more Prestashop security issues are discovered every year. So, won’t it be great if you could find Prestashop security loopholes before the attacker does? The solution to this is a comprehensive Prestashop security audit and pentesting. It can reveal multiple ways to compromise your Prestashop store. Security audits can reveal issues with the code that could lead to OWASP Top 10. Moreover, Prestashop security audit can find sensitive info leaks over the internet. A routine security audit means the user credit card info stays safe in the Prestashop store. Also, security audit includes the scanning of third-party plugins and reveals any backdoors.
Looking for a reliable web application software to secure your site against Prestashop attacks? Get in touch with Astra’s Web Security team to avail complete web security against all possible online threats.